Fraud Detection API: How It Works & Key Benefits for Your Business


by Tamas Kadar
IP address analysis is one of the oldest and most common methods used to detect fraudsters.
Check your IP fraud score here:
If you’re reading the words on this page, it’s thanks in part to an IP address. But unlike your home address, you probably have no reason to know it by heart.
And yet, this strange jumble of letters and numbers is, in fact, the key to automatic connection between any device and the Internet. This is true whether you visit a website, send or receive emails, use a chat room, and whether it’s from your phone, laptop or smart fridge.
An IP risk score can be used to help minimize the risk of bad actors entering your site. You can look at various settings and assign them points depending on a risk factor.

For instance, a VPN adds +1. An emulator adds +2, and so on. When all the points have been calculated, you get an overall IP fraud score.
IP reputation is another factor that impacts the overall score: IP addresses that have been historically connected to bots or fraudsters will have a higher risk score or might be blacklisted automatically by your provider.
Typically organizations use this solution at registration, login, or the buying stage, to stop potential malicious behavior (such as an account takeover).
While an IP fraud score is a type of fraud score, the two should not be confused with another: The former is specific to internet protocols whereas the latter is a more general overview of the fraud risk level of a user’s activities such as their transactions and purchasing behavior – watch below a video that explains “What is a Fraud Score”.
IP fraud scores work by taking data relating to a user’s IP address and feeding that data through risk rules. Each risk rule adds or subtracts points from the fraud score. When all the points have been tallied, an automated system can decide whether the score indicates risk or not.
Here is an example of IP fraud scoring:
The total IP fraud score for this user is 6 (2-1+ 5=6). Your anti-fraud system can then decide whether this score makes the user high, medium, or low risk, based on your own thresholds.
The goal, of course, is to gather as much data as possible to increase the precision of the score in order to predict risk accurately.
For IP fraud scoring to work, you need a system that can identify various IP parameters. Let’s break down some of the key types of IPs you should recognize.
If you think of an IP address as a physical postbox, a public IP lets you receive mail at your local sorting office. But the mail still needs to be sent to the right people in the city via Private addresses.
One point that often leads to confusion is that the term “private” doesn’t mean hidden. It simply refers to the fact that it links to a local network. It is indeed possible for anyone to find it.
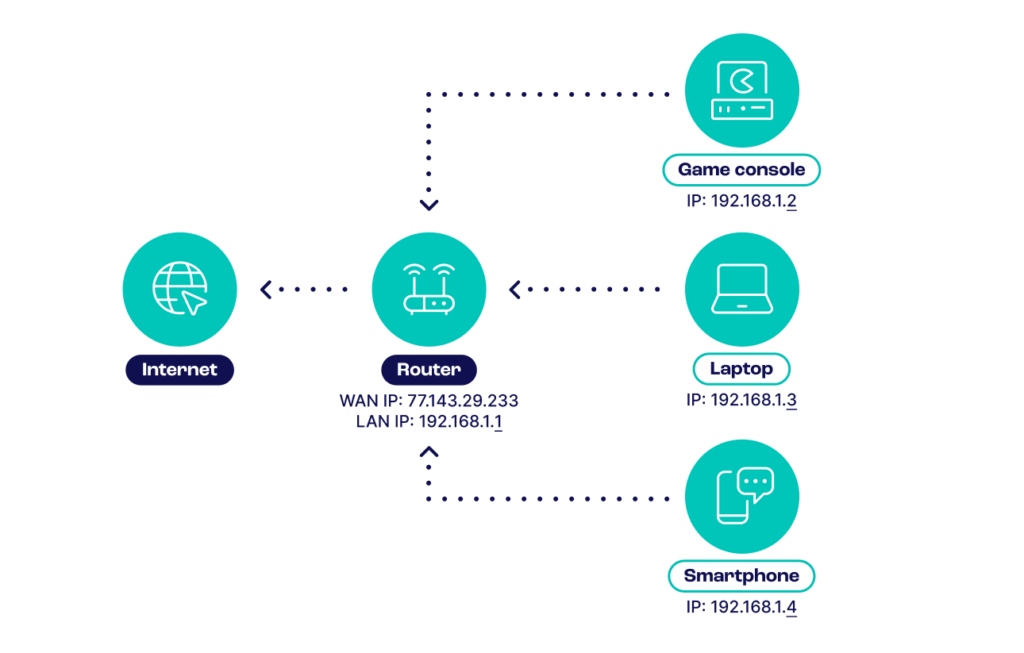
A public IP address is assigned to any device connecting to the Internet by an ISP (Internet Service Provider). It can be a phone or laptop, but also a web server or email server. It is impossible for a device to access a WAN (wide area network) like the Internet without one.
A private address is assigned to a device on a local network (LAN). Multiple devices can communicate with each other, usually within the same building.
Many users first realize that their IP addresses contain useful information after their first encounters with the concept of geolocation. This usually happens because of:
However, IP geolocation is a complex process that is outsourced to specialists. The accuracy of the geolocation varies depending on which database they use. A famous database, P2Country, yields 95% accuracy. IP2Region (which can be as granular as city and area code), decreases to around 50 – 75% accuracy.
For our purpose, which is to detect fraudsters, public addresses offer a lot more information than private ones. Here are important features that are helpful in IP fraud scoring:
Note that the most valuable IP addresses for fraudsters are residential IP addresses, which can be sold or rented on specific marketplaces and via brokerage services.
Last but not least, it helps to understand features designed to change an IP address. These include:
Proxy servers are easy, cheap, and fast to set up, which is why fraudsters rely on them to quickly change IP addresses during multiple attacks. This is called IP spoofing, and anyone can do it in seconds with free services such as xroxy.com.
Fraudsters favor SOCKS5 proxies, which are more complex to acquire but improve their chances of passing off as innocent residential users.
brings us to the most important part of IP lookup tools: understanding when the address has been manipulated.
There are many reasons why someone would want to avoid spoofing detection. Circling back to our examples above, it could simply be to watch a video from a foreign country. It could be to improve their security via added encryption. And of course, it could be for malicious purposes.

Regardless of the why, let’s see how IP addresses are hidden:
Proxies help fraudsters hide their IP addresses and stay anonymous. See how bad agents use them, and how our API flags them
Find out more
Now that we understand how IPs work and a basic strategy of how people hide their addresses, let’s see what we can gather by analyzing them.
So with these few features, we can already tell a lot about a user based on their IP address. Where they are based, what kind of network setup they use to connect online, and whether they appear suspicious or not.
So what should you do if you find a suspicious user’s IP address connecting to your system? You could simply block it straight away, but adding that address to an IP blacklist doesn’t make sense. This is because IP addresses are mostly dynamic, and multiple users could eventually end up sharing them, so you’d end up blocking valid customers.
This is why you can’t just look at the IP address itself, but also their usage via velocity rules. These algorithms look at the patterns and changes of IP address usage over time, which helps anti-fraud intelligence.
As we’ve seen, understanding IP addresses and getting a report is fast, affordable, and easy to perform. But it’s in no way flawless. While it can indicate suspicious behavior, it cannot point to fraud with 100% certainty.
This is, in fact, one of the shortcomings of the tech: it’s only useful as part of a complete fraud detection tool. When you search for risk, you need as much data as possible. And here, you’ll need:

As we’ve seen, IP addresses contain a multitude of valuable parameters that help us calculate risk. It’s not the only reason to rely on IP analysis against fraud. Here is why you should deploy that type of tool today:
As for the types of fraud you can detect with IP analyis, they include bot traffic, bonus abuse, multi-accounting, payment fraud, and more.
Breaking down the features of IP addresses for risk scoring is fast, affordable, and delivers results in real time. This is exactly what SEON’s IP lookup module offers in an affordable, easy-to-use package.

However, IP data is only one piece of the puzzle. For a complete solution against all kinds of fraud, from bot attacks to bonus abuse and chargeback fraud, we recommend combining IP fraud scoring with reverse email lookup, user and device fingerprinting, and more.
To learn more about how SEON can protect your online business, ask an expert by clicking the link below.
SEON is a powerful end-to-end solution that gives you complete control over the rules that affect your users’ fraud scores, with granular reporting.
Ask an Expert
There are two types of IP scores. One of them is called an IP reputation score. Service providers use it to determine if your emails should pass spam filters. In fraud prevention, your IP risk score can determine if a system labels you as fraudulent or not,
Any improper use of the IP address of a server is considered IP abuse. This includes spamming, phishing attempts, DDoS or malware attacks.
An IP score rating helps businesses determine whether an IP address is risky or not. While there is no standard for how the scores are calculated, a higher score tends to point towards a risky IP.
IP analysis can be performed manually by taking certain parameters, such as an IP address, and checking it against public databases. However, most businesses automate the process using IP lookup and IP risk-scoring tools
Showing all with `` tag




Click here
Tamás Kádár is the Chief Executive Officer and co-founder of SEON. His mission to create a fraud-free world began after he founded the CEE’s first crypto exchange in 2017 and found it under constant attack. The solution he built now reduces fraud for 5,000+ companies worldwide, including global leaders such as KLM, Avis, and Patreon. In his spare time, he’s devouring data visualizations and injuring himself while doing basic DIY around his London pad.
The top stories of the month delivered straight to your inbox