What Is an IP Address?
Short for Internet Protocol address, an IP address is a unique set of characters that identifies a device on a local network or the internet – much like the combination of characters in your house number and zip/postcode identify the unique address of your home.
IP addresses are fundamental to the smooth running of the internet, as well as intranets. They differentiate between different devices on a network, with each machine having its own unique identifier.
With so many devices in use, there are billions of IP addresses already in existence. Thankfully, there are 340 trillion trillion trillion IPv6 addresses available.
As well as identifying each device through the location information they contain, IP addresses also make each device available for communication.
What Is Internet Protocol?
Internet Protocol (IP) lays down rules for the way in which information is passed via a local network and the internet. It defines the format of the data being sent, establishing a standardized network layer communications protocol. This means different devices can communicate with one another.
IP was first invented in 1973, in IPv1, an experimental version. In fact, that decade saw the most revisions, getting us to September 1978, when the first description of the currently-used IPv4 was published.
IP Address Types
There are several types of IP address, including network addresses and website IP addresses. These include public, private, static, and dynamic IP addresses, along with shared IP addresses and dedicated IP addresses for websites.
Here are some key groupings of IP address types:
| Public vs private IP address | Defined by whether it is indicating the presence of a device on a local network or the wider internet. Online devices normally have both a public and a private IP address. |
| Static vs dynamic IP address | Defined by whether this public IP address is the same or changes over time. This is defined by the ISP. Static IPs can be only public IP addresses. All private IP addresses are dynamic. |
| Shared vs dedicated IP address | Is this IP address ever shared by any other devices or individuals? This is relevant to websites, servers, etc. |
Public IP Addresses
Your internet service provider (ISP) provides a public IP address to your router. The address covers your entire network. Any device outside your network will use your public IP address to communicate with your network.
Public IP addresses along with private IP addresses are often referred to as consumer IP addresses.
Private IP Addresses
Within your network, each of your devices has a private IP address, which your router assigns. That means every laptop, smartphone, tablet and so on has its own unique private IP address, along with any smart devices or Bluetooth devices one may have (TVs, Wi-Fi printers, smart speakers, etc.).
Each device having its own private IP address means that your router can recognize, differentiate between and communicate with everything on the network.
Static IP Addresses
There are two forms of public IP address: dynamic IP addresses and static IP addresses.
Static IP addresses are fixed – they don’t change. You can use a static IP address for a server, to ensure that other devices can consistently find it. This is essential for any websites and email addresses hosted on that server.
Dynamic IP Addresses
Dynamic IP addresses do change, regularly and often. An ISP’s Dynamic Host Configuration Protocol (DHCP) server assigns the dynamic IP addresses temporarily, assigning one to a device each time it connects to the internet. The dynamic address expires after a set amount of time. It then goes back into a pool of IP addresses that the ISP owns, ready for reassignment to another device in future.
There are financial, practical and security benefits for ISPs who use dynamic IP addresses. The ISP can save money (and hassle), as it doesn’t have to deal with moving IP addresses when people move house or businesses change premises.
From a security perspective, a dynamic IP address makes it harder for someone to hack into a network.
Shared IP Address
In addition to the types of IP addresses detailed above, there are also two types of website IP addresses that businesses can buy as part of their web hosting: shared IP addresses and dedicated IP addresses.
A shared IP address is precisely what the name implies – it is shared by multiple websites, devices or individuals, which are hosted on the same server. If we’re talking about a website, this type of IP address is best suited to small websites with a low volume of traffic.
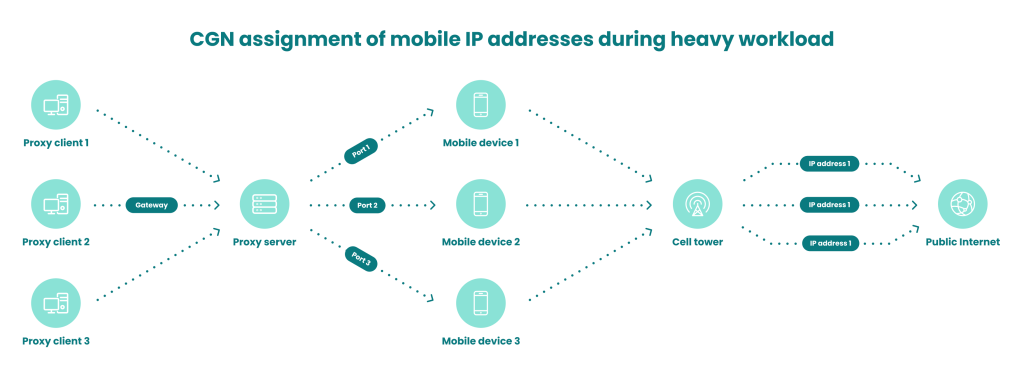
Another example of shared IP address is seen at times of high workload on a mobile network. The mobile ISP will then assign the same IP address to several different subscribers at the same time. This is why mobile proxy connections are preferred by cybercriminals. Because they can’t be banned, for fear of insulting legitimate customers.
Dedicated IP Address
A dedicated IP address is one that your web host assigns as unique to you, your website or server. It is not shared with anyone else.
In the case of websites, this can deliver several advantages. It means you can more easily obtain an SSL certificate to run your own File Transfer Protocol (FTP) server. It also means you won’t be implicated in any poor behavior by any other sites sharing your IP address (so you can avoid being unfairly blacklisted).
A dedicated IP address is also handy if you’re transferring your domain, as you can access your website using its IP address while the transfer is underway.
What Are the Different IP Address Versions?
There are two IP address formats currently coexisting: IP version 4 (IPv4) and IP version 6 (IPv6). The development of IPv6 began in 1994, due to the future exhaustion of the number of IPv4 addresses (there are 4,294,967,296 IPv4 addresses available).
IPv6 was ratified as the Internet Standard on July 14, 2017. Though it has been established as the successor of IPv4, IPv4 addresses remain the most common format at present.
IPv4
IPv4 addresses use a 32-bit (232) address space and take the format X.X.X.X
Each X can have a decimal value between 0 and 255. Here’s an example of an IPv4 address:
172.16.254.1IPv6
IPv6 addresses use a 128-bit (2128) address space and hexadecimal notations. They are separated by colons rather than periods, and have eight groups of 16 bits. Here’s an example of an IPv6 address:
2001:0db8:85a3:0000:0000:8a2e:0370:7334What Can You Learn from an IP Address?
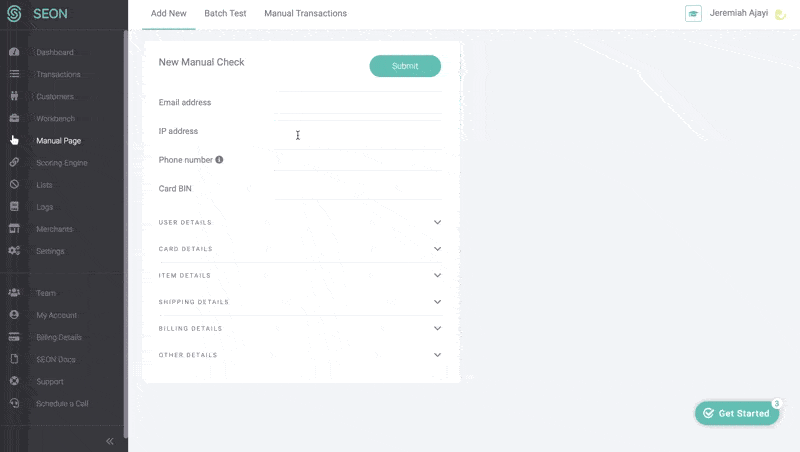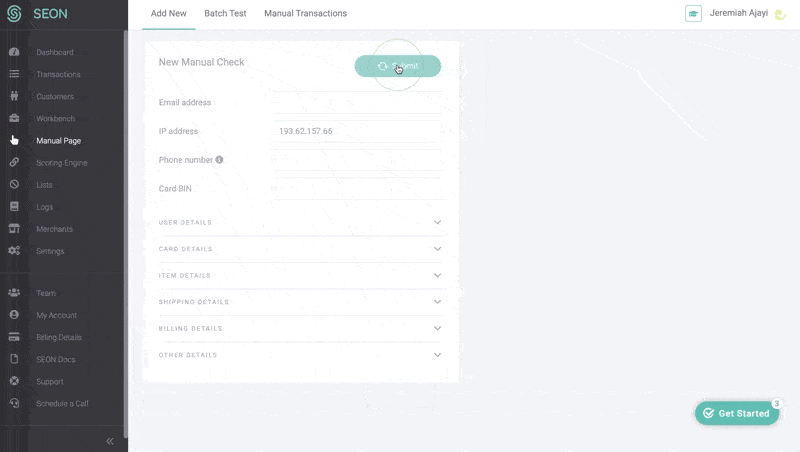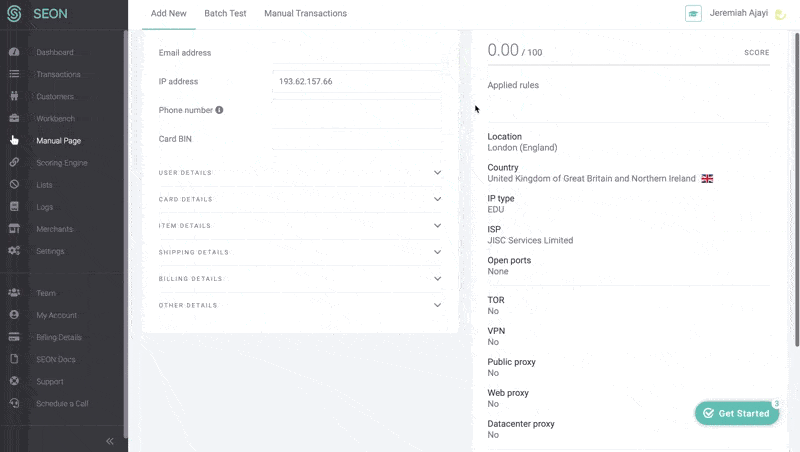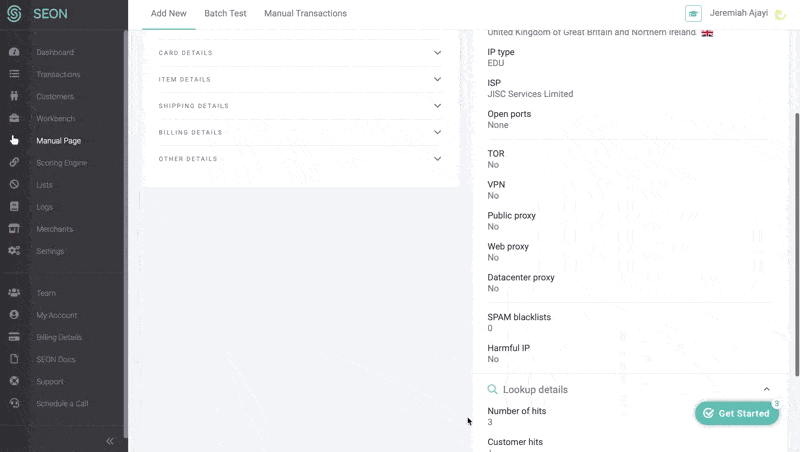
If you want to find out more about an IP address, you can use an IP lookup tool.
IP addresses can reveal all sorts of information, including the name of your ISP and its rough geographic location (city, zip code, or area code – though the accuracy of the location varies from ISP to ISP). What an IP address won’t reveal is your name and address.
For the purposes of fraud prevention, IP addresses help provide valuable data points to inform someone’s risk profile, including whether they are trying to spoof their location in order to appear to be someone they’re not.
You can test this out by entering any public IP address below. SEON’s data enrichment will return a complete profile of everything one could learn from it:
Check your IP fraud score here:
If looking up a phone number, please include its country code without plus signs, spaces or hyphens. By trying this tool, you’re agreeing to our Privacy Policy, General Terms of Service and Data Processing Agreement.
The score that a fraud prevention module calculates based on someone’s IP is called the IP fraud score. Fraud analysts consult this and other parameters to decide how much of a risk a user could be posing.
How Do Criminals Hide Their IP Address?
Methods and tools that mask someone’s physical and IP address are a key part of OPSEC for fraudsters and other online criminals. These can include:
- Tor
- VPN
- mobile proxies
- residential proxies, though criminals prefer mobile proxies
- privacy-focused tools that ultimately include some of the above
Each of these has its own benefits and shortcomings, though the idea is always the same: to falsify your IP in order to look like you’re someone you’re not – or at the very least that you’re not who you are.
Reasons for this include attempts at multi-accounting, where the fraudster is pretending to be various different people, as well as pretending to be situated somewhere else because, for example, that is where someone you are impersonating would be.
However, sophisticated fraud prevention software is able to detect these methods through IP address analysis, and IP address enrichment. Utilizing velocity checks and other comparisons, tools can tell when something seems off, pinpointing discrepancies between someone’s stated and real location.

Why Protect Your IP Address?
Protecting your IP address can stop your online activity being tracked. It can hide part of what you do online from certain parties, such as targeted ad networks. Protecting your IP address can also sometimes prevent the authorities from tracking you, or even criminals.
Another reason to mask your IP address is to dodge geo-restrictions. Some individuals use this to access TV series, sports shows and online games – all content that is not officially available in their locale.
But there are ways in which criminals may abuse someone’s IP address. If targetting a company, they could deploy a DDoS (distributed denial of service) attack to flood its servers.
With private individuals, a criminal could trick them into installing malware that reroutes the criminals’ own IP through the victim’s, helping the criminal appear to be somewhere legitimate, though they are not.
How to Protect Your IP Address
Anyone who wants to protect their IP address can do so using free or paid software to ensure that it remains private or pseudo-anonymous.
You can use a proxy, Tor, or a VPN to achieve this. Note that proxy detection techniques mean that anyone who knows how to look will be able to tell you are hiding your IP.
At the end of the day, fraudsters make use of many of the same tools, scripts and applications that privacy-minded but legitimate individuals would.
The question for companies – and the challenge for fraud prevention vendors – is not just how you can identify the use of such tools but how you can tell who is who, so you can block the bad actors and continue to let good customers through without interrupting their UX.