Identity theft is a pain point for any vertical – but especially neobanks. Without the proper precautions in place, many illicit individuals can remotely set up a neobanking account with fake credentials that go undetected.
In fact, neobanking sees fraudulent attacks that double that of credit card companies, according to Unit21, with neobanks encountering a 0.30% fraud rate compared to the historical average of 0.15% seen in credit card companies.
Let’s look into how fraud, particularly identity theft, impacts neobanks and banking institutions, and what can be done to combat it.
Why Is Identity Theft a Problem for Neobanking?
Identity theft happens in numerous ways but the goal is always the same: to leverage real people’s data for nefarious deeds.
Fraudsters and criminals who rely on stolen identities can then target banks and neobanks in the following ways:
- opening bank accounts under someone else’s name – therefore committing a specific example of identity theft fraud known as synthetic identity fraud
- taking out credit loans that they have no interest in repaying
- laundering money without linking transactions to their real-life identities
While flagging fake IDs is a key part of the KYC process, it becomes a lot more challenging when you’re dealing with a real person who is unaware their data has been stolen.
This is especially true if the fraudsters are sophisticated enough to create a digital footprint that matches the person’s ID or to create a synthetic ID profile – a core strategy deployed when fraudsters open bank accounts.
The identity theft that fuels synthetic IDs comes from standard cybersecurity failures, such as data breaches, phishing, or fake job ads. However, there is also a growing market for “rent-an-ID” services, which see desperate punters sell their identities in exchange for a quick payment.
In short, bank account fraudsters have no shortage of options when it comes to identity theft. This makes it harder for banking institutions to separate criminals from legitimate users – especially if they want to acquire more customers online with as little friction as possible.
How Do You Detect Identity Theft in Neobanking and Banking?
Just like with every other industry, detecting stolen identities should start at the onboarding stage in neobanking and banking. In short, SEON can function as a frictionless pre-KYC filter to instantly assess the kind of customer you’re dealing with and raise any red flags.
While the traditional KYC process can help you flag suspicious IDs using identity verification software or document validation checks, there’s a lot of benefit to sourcing alternative data at the pre-KYC stage.
This is the best time to tackle the following three questions, which SEON investigates without introducing any friction to the customer’s journey:
- Is the user connecting with a suspicious configuration (such as an emulator, VPN, or Tor)?
- Are they employing suspicious tools commonly used by fraudsters (e.g. eSIM cards and disposable email address domains)?
- Do they have an online presence (such as social media profiles, accounts on popular platforms, and various subscriptions)?
Equipped with the answers to these questions, you can block obvious fraudsters right away. Not only will this help you keep your neobank free from fraud, but it can also save you money and time otherwise spent on doing fully-fledged KYC verification and compliance checks on individuals who are clear threats to your organization.
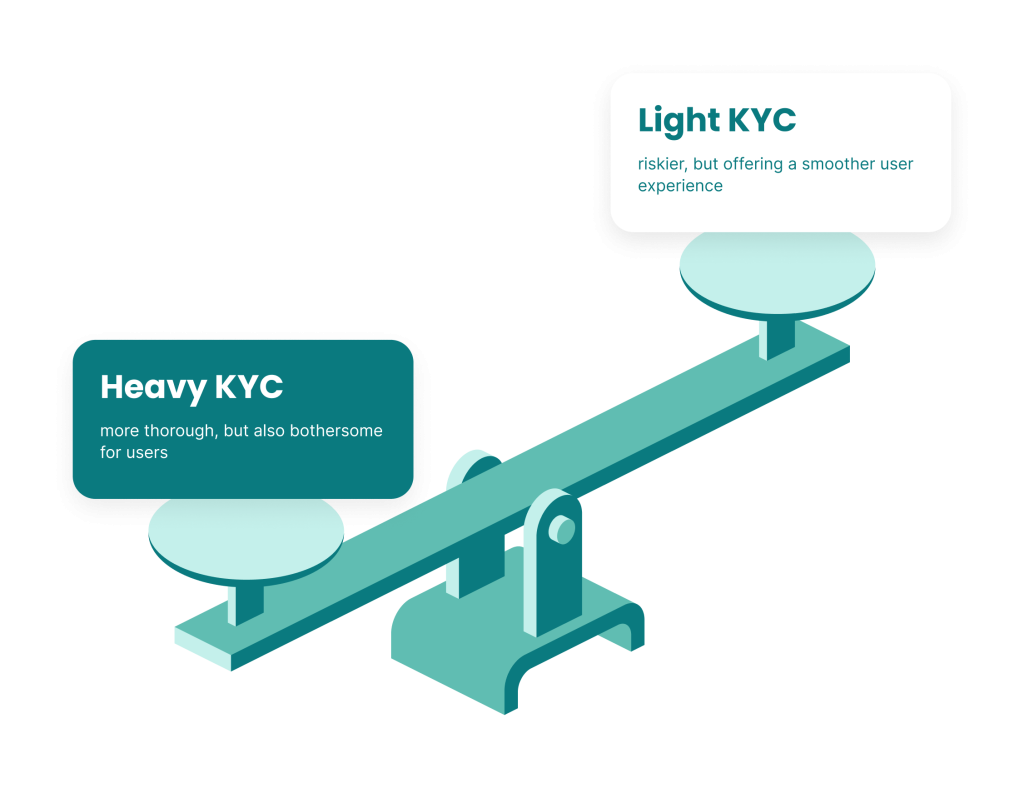
Think of the score resulting from such a pre-KYC check as a traffic-lights system, allowing you to funnel customers who are confirmed to be legitimate through just the minimum (light) KYC checks required by law – keeping them happy and satisfied.
Meanwhile, those customers deemed to be suspicious but not necessarily bad actors can go through a heavy KYC process that scrutinizes their identity very closely – so that you are only onboarding real people while reducing the chances of them experiencing false positive rejections.
Partner with SEON to reduce fraud rates in your business without friction – with real-time data enrichment and advanced APIs.
Ask an Expert
Top 3 Tips to Detect Stolen IDs in Neobanking
Let’s now look at three things to focus on when attempting to protect your neobank from fraudsters with stolen IDs: digital profiling, machine learning, and activity monitoring.
#1: Use Digital Profiling to Determine who has no Social Media Presence
At the time of digital onboarding, every customer will provide a phone number or email address. Good news for risk managers: This can be enough to identify suspicious applications that most certainly point to a fraudster.
Using these to check 90+ social signals, this gives you an idea of whether that person has an online presence or not thanks to the comprehensive profiles created by SEON’s digital profiling and data enrichment capabilities.
ID thieves might have a name, address and in some cases personally identifiable information (PII), but they will rarely have the full set of data related to the person. While a phone number and email address is easy enough to falsify, it is incredibly hard to make them link back to the real person’s digital footprint.
For example, it is easy to sign up for a new email handle that uses the victim’s full name but incredibly difficult to convincingly recreate that email account’s online presence on social media, web platforms, apps, and so on.
The below screengrab gallery shows SEON’s digital profiling capabilities in action:
As shown above, SEON can check IP addresses, email addresses, and/or phone numbers to determine what, if any, internet presence an account owner has. After all: The lower the account subscriptions, the more suspicious the individual.
This digital profiling capability is crucial to keeping the fraudsters away from your neobank before they can make it through the digital onboarding stage.
#2: Utilize SEON’s Machine Learning to Innovate Your Rule Making
SEON ensures your account monitoring stages are automated thanks to its machine learning rules that identify suspicious patterns and inform you of suggested rules that will help you protect your neobank from fraudsters.
Let’s take a look at the below screenshot gallery that shows SEON’s machine learning in action:
As the above widget shows, SEON is able to detect suspicious activity and provide you with suggested rules accordingly. This allows you to enjoy the benefits of automation while also allowing you to tailor SEON’s fraud prevention capabilities to your own risk appetite.
In the example shown above, SEON has detected that there are recurring instances of a billing address hash that is associated with fraud. The user then has the opportunity to flag or block any such instances of that billing address, and this allows you to crack down on such activity.
After all, while fraudsters may attempt to exploit your neobank with identity theft, they may not cover their tracks based on the location of the transactions they make. Using SEON’s machine learning-based rules gives you the opportunity to act fast whenever it detects such illicit activity.
#3: Use SEON’s Activity Monitoring to Spot Suspicious Device and Browser Configurations
Understanding how users connect to your online banking website or app can reveal enlightening clues about who they are. A device and browser fingerprinting tool will uncover important technical data relating to their configuration of software and hardware.
So what does an identity thief’s connection look like? In all likelihood, it’s going to be spoofed, controlled or manipulated. They will rely on emulators, anti-fingerprinting browsers, or even privacy-focused operating systems.
Here are examples of rules this may trigger:
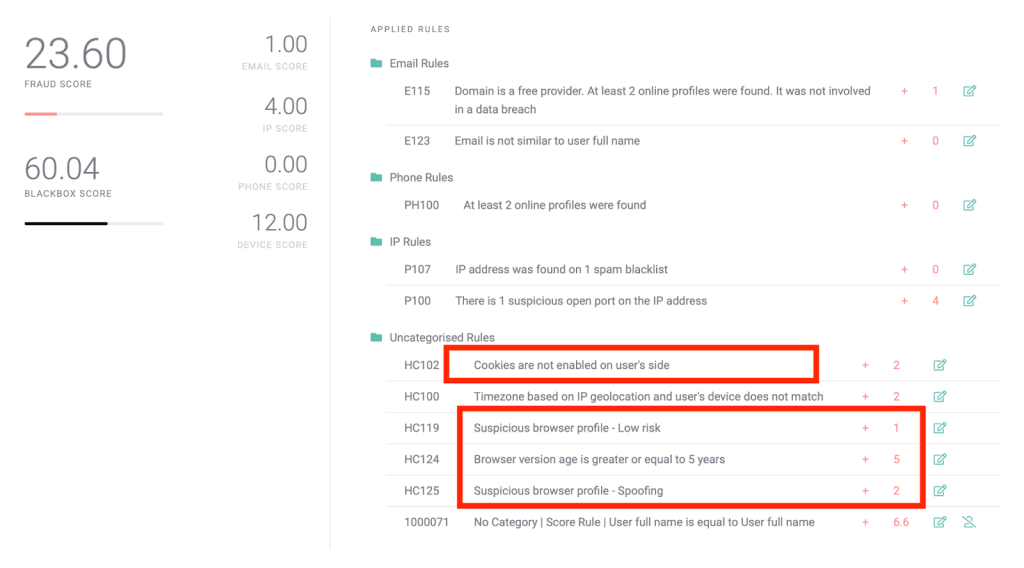
As the above screenshot shows, an individual’s browser is raising a few red flags. Its version points to a five-year-old product, which is unrealistic for an everyday user, and there is also a sign of a browser spoofing attempt.
Of course, this doesn’t necessarily point to identity theft, but the likelihood that you’re dealing with an imposter increases drastically if they’re relying on these tools which SEON can detect. Put simply, SEON helps you tackle the question: Why would they be trying to hide who they are?
By doing so, the solution allows you to better protect your neobank from identity theft by flagging those users who appear to be hiding who they are and what they’re doing.
How SEON Helps Protect Your Neobank from Identity Theft
SEON combats identity theft through its digital profiling, machine learning, and activity monitoring capabilities. To spot identity thieves, you need to find a dubious social media presence, spot suspicious patterns with automation, and find software and hardware configurations that reflect an individual with something to hide.
Accordingly, SEON is equipped to help you identify those fraudsters who have created a fake neobanking profile and account – but who haven’t covered their tracks by ensuring their social media presence, account activity, and web browsing equipment appear convincing.
Partner with SEON to reduce fraud rates in your neobank and catch identity theft without false positives and with no friction.
Ask an Expert
FAQ
Identity theft happens when criminals or fraudsters acquire important pieces of a legal identity, such as a full name, address, and copy of an ID document, and try to use it to open a bank account or access a financial product offered by a bank.
Criminals have developed different techniques for financial identity theft, medical identity theft, synthetic identity theft, and even child identity theft. They then use these to try to defraud banks.
You may be a victim of identity theft if you notice unexplained bank charges or withdrawals, receive letters from credit card providers you did not apply with, or notice errors on your credit report.
Sources
- McAfee: A Guide to Identity Theft Statistics for 2022
Related Case Studies in Banking
- FairMoney Onboards Better Neobank Customers Thanks To Digital & Social Footprint Check
- Leading Challenger Bank Eradicates Bonus Abuse Thanks to SEON’s Email Module