Your neobank, challenger bank, or traditional financial institution has all the right KYC validations in place. And, still, fraudsters manage to open bank accounts.
How do they do it? And, more to the point, how do you stop them? Let’s find out.
1. They Create Synthetic Identities
The first step for a fraudster is to fool your KYC checks.
It used to be easy enough with stolen identities. But banks became wise to the tactic, and identity verification software got better at flagging IDs that appeared on data breaches.
This is why fraudsters currently rely a lot on synthetic identities. Put simply, these are identities stitched together using real people’s data and made-up data.
A common example of a synthetic identity would include a real name and date of birth but a stolen social security number.
This would be hard for a KYC system to detect because social security numbers couldn’t always be checked electronically. And while the Social Security Administration launched an electronic verification service in 2020, synthetic IDs still remain a problem.
The stolen IDs tend to come from the usual sources: data breaches, phishing, and even the ID records of children, unbanked or homeless people, the deceased, or incarcerated individuals. Fake job ads and online scams are also a good source of phishing IDs.
These are all people with “thin credit files” or non-existent credit history. Their records won’t be flagged by ID verification systems because they’ve never appeared anywhere else.
Fraudsters also increasingly rely on “rent-an-ID” service, where people desperate for a quick payment actually lend their details in exchange for cash.
As for the made-up data, there is no shortage of services fraudsters can use to create fake IDs in seconds. Sophisticated fraudsters will even go as far as creating deepfakes to fool video selfie ID verification services.
Solution for Spotting Synthetic Identities?
2. They Purchase Pre-Created Accounts
The dark web is full of options for fraudsters who need a quick, pre-opened account. In fact, fraudsters have become so brazen with neobanks and challenger banks, that they might even find some on clearnet marketplaces.
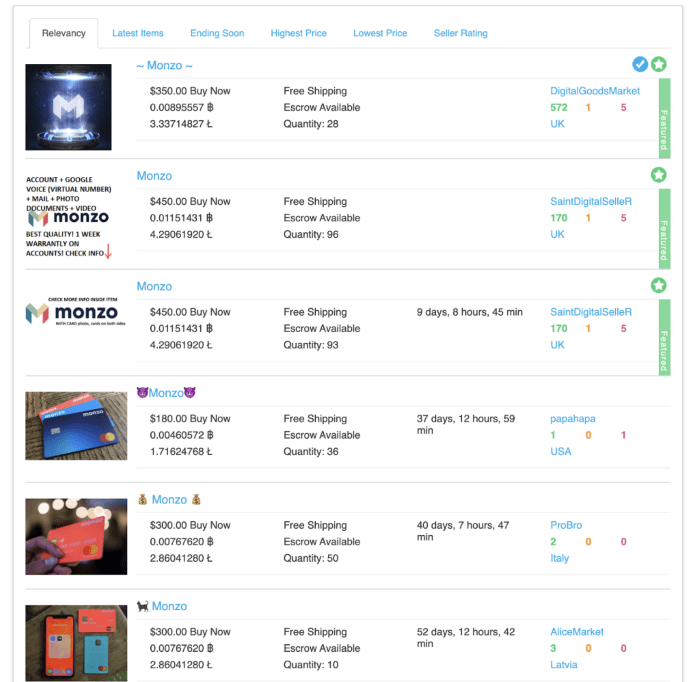
These packages can be hit and miss for fraudsters. With the right synthetic ID fraud detection systems in place, you’ll have no problem realizing that the login details have exchanged hands.
But it’s the sheer volume of these accounts that makes them challenging for neobanks. Fraudsters only need one to slip through the cracks. And when you’re trying to grow as fast as possible by onboarding thousands of daily users, it can be hard to stay on top of risk management.
Solution for Blocking Pre-Bought Accounts?
Unfortunately, fraudster marketplaces are like the mythical hydra – cut one head and two more grow back. So not much you can do from that side. However, spotting when an account is passed to another user is possible using device fingerprinting and IP lookup tools.
3. They Spoof Their Configurations
Fraudsters understand the basics of risk detection. The oldest trick in the book, the ability to change your IP address to make it look like you’re connecting as someone else, doesn’t cut it anymore.
But in this game of cat and mouse, fraudsters have leveraged technological tools designed to completely make it appear as if they are someone else online.
This is particularly damaging for neobanks and branchless banks, where the only information you have is digital.
So how do fraudsters hide their online selves in order to open more fraudulent bank accounts? Here are examples:
- VPNs, proxies, and Tor: A fairly standard technique for hiding your IP address.
- Socks5 proxies: A more advanced form of spoofing that emulates a residential proxy.
- Emulators and virtual machines: Software designed to automatically change your IP, but also a MAC address and even the browser and OS environment. Examples include Nox of VMWare.

You can read more about advanced spoofing techniques in our post on device fingerprinting.
Solution for Spotting Spoofed Configurations?
A good device or browser fingerprinting tool will be able to alert you of suspicious software or hardware configurations.
4. They Enlist Money Mules
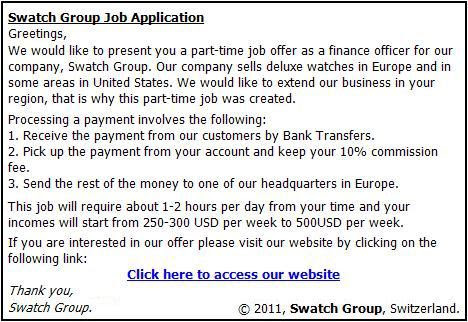
An example of a money mule advert, gathered by the Aston University of Birmingham
Fraudsters who can’t open fraudulent bank accounts themselves have another option: paying other people to do it.
They will simply place ads asking to use other people’s accounts (for a fee). In some cases, they will guide them through the account opening process, ensuring they can take control over the login details.
In the money laundering world, the people who lend their accounts in that way are referred to as money mules.
The practice of splitting large sums of money into multiple accounts, called smurfing, allows fraudsters and criminals to hide money obtained illegally. The goal is always to launder it – or make it enter the legitimate financial system.
Solution for Spotting Money Mules?
Spotting fraudsters’ accomplices can be one of the most challenging tasks for banks and neobanks. However, it is entirely possible to establish what is considered normal vs suspicious behavior using a combination of risk rules (more on behavior analysis below).
You can read more about AML fraud detection here.
5. They Imitate Good Customer Behavior – Until They Don’t
Once they’ve created a bank account, fraudsters understand they need to lay low for a while. They will often attempt to imitate the behavior of a legitimate customer in order to avoid suspicion and detection.
If your bank offers loans, fraudulent borrowers will be on their best behavior during the early stages. Sophisticated fraudsters often repay their initial loans and gradually upgrade their credit limit, until they decide to default on a big repayment (also known as bust-out fraud).
This kind of behavior is particularly challenging to identify. Online lenders tend to encourage users to increase their purchasing limits, which is where this kind of fraud happens. However, a machine learning system could potentially identify patterns over time.
Solution for Spotting Suspicious Behavior?
In risk management, the closest thing you have to agent monitoring is called velocity rules. These are risk rules that look at data and events over a specific period of time. For instance, a regular increase in a loan application, or monthly repayments from a suspicious source of funds.
Machine learning systems can also identify patterns over time – even if they appear legitimate to the naked eye.
You can learn more about velocity rules and behavior analysis in our post on transaction monitoring software.
How to Stop Fraudsters From Opening Bank Accounts: Key Takeaways
As long as banks have managed people’s money, fraudsters have attempted to open accounts with them. In the digital age, where neobanks and challenger banks see friction as a competitive disadvantage, opening a fraudulent bank account is easier than ever.
Luckily, there are effective tools you can deploy to mitigate risk by:
- Looking at alternative data at the onboarding stage
- Detecting users’ real configurations of software and hardware
- Monitoring transactions in real-time
- Understanding user behavior with risk velocity rules
- Deploying machine learning systems to identify patterns over time
These are exactly the kind of features that SEON offers banks and digital banks – all available as a full end-to-end fraud detection solution, or as modular APIs to augment your current risk tech stack.
Frequently Asked Questions
Unfortunately, if your identity is stolen, including personal identifying information, or a copy of a government-issued ID, it is possible that a fraudster might be able to open an account in your name and use it for nefarious purposes. This is especially true of bank accounts that exist solely online, where stolen digital identities are more easily used to sign up.
If a fraudster is armed with your stolen personal information, including your name, address, sensitive data like social security numbers, AND they have hacked into your email account, it is possible that they can access your account and drain it of funds, or potentially open an account impersonating you. This is especially true if no form of multi-factor authentication exists that sends an alert to your mobile device when someone attempts to access your bank account from an unknown location.
Application fraud is the most common, and potentially the least malicious form of loan fraud. It may include lying about assets to get better terms on a loan, but can range in severity to impersonating another person to take out a loan with no intention of repaying it.
Though the bank will ultimately be liable for unauthorized payments made from a hacked account, you should report fraudulent transactions as soon as possible to mitigate further damage and inconvenience.