According to estimates from the United Nations in 2020, 2% to 5% of global gross domestic profit (GDP) each year is laundered money. That means money laundering can account for anywhere between $800 billion and $2 trillion annually.
At the heart of this are illicit transactions that were not prevented at the time they were made. Thankfully, much of the answer to this corrupt financial activity boils down to organizations ensuring that they carry out an anti-money laundering process called Know Your Transaction (KYT).
Let’s look into KYT, how it works, and what it means for organizations.
What Is Know Your Transaction (KYT)?
KYT is an anti-money laundering (AML) and counter-terrorist financing (CTF) requirement. It involves organizations such as financial institutions logging, analyzing, and reporting their transactions. The goal is to try to detect fraudulent transactions and combat behavior associated with money laundering and other fincrime such as terrorist financing.
KYT fights financial fraud by arming organizations with the data needed to determine how to fight fincrime and other suspicious activities, the signs of which often lurk in each business’s transactions.
As an AML and CTF operation, Know Your Transaction complements the process of Know Your Customer (KYC) by focusing on which transactions people are making, as opposed to just who is making them.
While organizations and industries have different ways of carrying out KYT, the general actions it requires are listed in the following process:
- Data gathering: Collating a list of transactions
- Data analysis: Inspecting – often through transaction monitoring software – those transactions for suspicious activity
- Risk assessment: Gauging the data analysis results to determine the extent to which a transaction may be suspicious
- Reporting: Relaying the post-risk assessment data to the relevant AML/CTF authorities
Owing especially to its reliance on transaction monitoring software, KYT is a technological, data-driven, and altogether resource-intensive operation.
Part of staying compliant with KYT – and thus avoiding fines – involves assessing how effectively your organization has implemented the process. By monitoring it frequently for potential improvements and investing in real-time transaction monitoring, organizations can automate much of their KYT workload and even find ways to improve their return on investment (ROI) as a result.
Why Is KYT Important?
KYT helps organizations reduce their chances of being subjected to fines for failures in AML compliance. It also reduces the potential for financial exploitation by criminals, constraints on organizational resources, and the reputational damage that comes from being complicit in money laundering or terrorism.
Know Your Transaction can also help businesses improve their financial and overall operational performance thanks to its focus on income and outgoings. As KYT is a transaction monitoring, organizations that implement it may find ways to improve their ROI as a natural benefit during the process.
KYT is a regulatory compliance requirement. As such, it is part of an organization’s due diligence. Organizations that aren’t KYT-compliant may face legal penalties, financial losses, and reputational damage.
Transactions that can be linked to terrorist financing can be elevated from conventional AML due diligence to advanced AML due diligence. Depending on each organization’s risk tolerance, this may be where parties associated with the suspicious transaction are subjected to further security checks or trigger a more comprehensive manual review by risk teams.
Learn how SEON’s APIs work, their benefits, and how they can stop fraud at your company.
Ask an Expert
What Does KYT Mean for AML Compliance?
KYT is a staple part of both AML and CTF compliance because scrutinizing financial activity is a core way to prevent money laundering and terrorist financing. It achieves this through transaction and behavior monitoring, risk assessment, and alert generation.
Let’s take a closer look at the AML/CTF benefits offered by KYT:
- Transaction and behavior monitoring: KYT is a real-time process that focuses on financial activities. Suspiciously high transactions that occur within a dubiously fast timeframe can alert fraud prevention systems such as transaction monitoring software, which can flag these within a business’s KYT program to inform its AML/CTF reports.
- Risk assessment: KYT is informed by data sources such as politically exposed person (PEP) lists, high-risk jurisdiction lists, and negative media and sanctions lists. This insight helps organizations optimize the accuracy of their risk-scoring procedures, which enhances their compliance with AML and CTF regulations.
- Alert generation: While well-equipped organizations have systems of suspicious activity alerts, such as periodic transaction monitoring tools, many of these approaches do not work around the clock. Because KYT encourages the use of real-time systems for analyzing dubious transactions and behaviors, it is a key element of AML/CTF compliance. An AML/CTF report by the Financial Action Task Force (FATF) stresses the benefits of real-time threat monitoring systems to inform better communication, accountability, and auditability throughout the data-sharing processes between organizations and their compliance authorities.
- Compliance with due diligence: AML regulations require organizations to carry out both customer due diligence (CDD) and enhanced due diligence (EDD) based on the level of suspicion related to each customer. These due diligence processes become better informed the more a business knows about its transactions through its KYT processes.
KYT requires ongoing training and research on topics that surround AML/CTF and their regulations. This employee engagement is another way that KYT helps businesses stay compliant with AML regulations.
How KYT Works
KYT works by organizations using both their technology and their workforce to record, analyze, and (whenever suspicious activities arise) report the transactions they deal with.
The actions required to undertake KYT checks are industry-, jurisdiction-, and organization-specific. The process is proving an increasingly technological one, with modern systems such as transaction monitoring software, risk assessment, and behavioral analysis tools improving its efficiency and efficacy.
That said, whether an organization carries out its data generation on a periodic or real-time basis, humans oversee much of the process, especially to reduce the chances of false positive fraud risk alerts.
With the combination of technology and human intervention in mind, let’s now check out an overview of the KYT process:
- Gather and analyze transactional data to determine a risk score. Having determined the sums involved in the transactions, as well as their purposes and the parties involved in them, use data analytics to determine a risk score.
- Continue to monitor the transactional data and act on any alerts that arise. It’s during this process that alerts are made based on the organization’s risk criteria and risk appetite. For example, financial institutions can do blacklist checks on the parties making the payments at this initial transaction monitoring stage.
- Approve the transactions deemed legitimate and escalate the ones that are suspicious. While innocent transactions can proceed without further intervention, suspicious ones are flagged for review.
- Investigate the flagged transactions and notify the given financial authority when required. Determine the origin, purpose, and nature of each suspicious transaction. For example, which parties were involved in it, and are any of them involved in organized crime? Reject any flagged transactions that continue to appear illegitimate at this point and file them in a suspicious activity report (SAR) for the attention of the organization’s given financial authority.
By following these steps, an organization will comply with its AML/CFT regulations and ensure a successful KYT process.
Benefits of KYT
Aside from the obvious benefits of AML compliance and risk management, KYT helps organizations to be data-driven, profitable, secure, and equipped to support financial audits – and even law enforcement.
Let’s take a closer look at the operational and law enforcement benefits of KYT:
- It’s data-driven, better equipping your business to record and gain insights about its financial activities.
- It’s largely automated, thanks to the fact that KYT requires software to record and process transactions automatically. This reduces the demand on your workforce for manual processes.
- It helps risk-scoring processes by assessing the level of suspicion in each transaction. Because it’s a risk-scoring process in itself, KYT can determine high-risk transactions that will help you gauge the risk associated with the customers making them. KYT often goes hand-in-hand with KYC, after all.
- It improves ROI by helping organizations flag suspicious financial activities and individuals and take action accordingly.
- It’s both a deterrent and weapon against criminals – and not just white-collar criminals either: KYT is focused on counter-terrorist financing in addition to anti-money laundering.
- It can assist law enforcement investigations. As suspicious transactions can be heavily associated with organized crime, a routine process of transaction analysis and monitoring helps bolster the evidence-gathering process.
Aside from being an AML requirement, KYT is highly beneficial to any organization wishing to optimize its operations and strengthen its safety, reputation, and return on investment.
Partner with SEON to reduce fraud rates in your business with real-time data enrichment, machine learning, and advanced APIs.
Ask an Expert
Challenges of KYT
Know Your Transaction processes can introduce friction and carry the risk of both false positives and false negatives. KYT also involves the processing, recording, and transferring of sensitive information, which puts demands on organizations in terms of how they safeguard their customers’ data.
Let’s take a closer look at these challenges:
- KYT can lead to customer insult rates based on the high level of friction that it can require – especially at those unfortunate times when it leads to customers being rejected due to a false positive fraud check.
- KYT can lead organizations into a false sense of security when the process inadvertently draws false negative fraud checks, ultimately allowing financial criminals to deal with an organization that mistakenly trusts its less scrupulous customers.
- While the difficulties of maintaining data protection are of course a necessity, it is important to remember that KYT is highly data-driven. This means it can be difficult for organizations to balance carrying out necessary data precautions for KYT with minimizing the friction its demands for enhanced due diligence checks cause when the need arises.
While Know Your Transaction is indeed data-intensive and comes with both friction and the potential for inaccuracies in its security checks, it bears repeating that it remains a highly effective method of combatting money laundering and other fincrimes.
KYT vs KYC
Know Your Transaction is different to Know Your Customer. The former is about identifying suspicious financial activity; the latter is about identifying suspicious individuals and behaviors. KYT and KYC are both mandatory anti-money laundering and counter-terrorist financing processes that are becoming increasingly automated and data-driven.
KYC takes place at the initial stage of a customer onboarding process, and the level of friction involved depends on how low- or high-risk the individual is. Meanwhile, KYT takes place after a customer has already been onboarded and whether the transaction is successful depends on the nature of both the individual and the transaction itself.
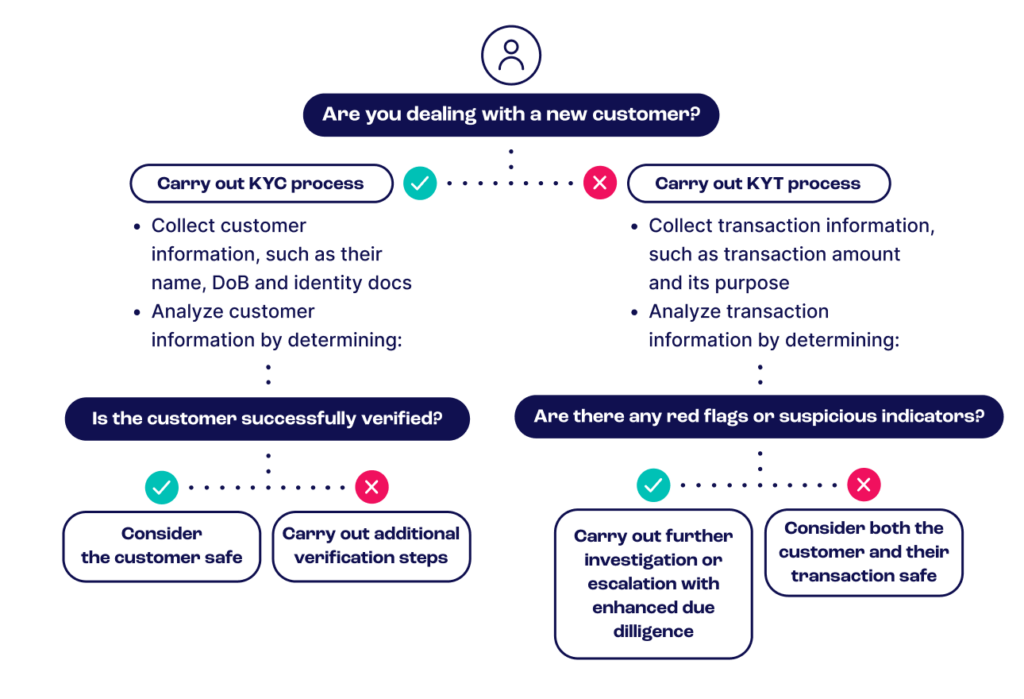
How SEON Can Help with KYT
SEON provides risk management teams with the digital tools they need to comply with AML and CTF regulations and determine risk based on such factors as IP geolocation and transaction attributes.
Suspicious payments can be thwarted before you even have to do a KYT check – as reflected in the animation below:
It’s still perfectly possible that some of your legitimate customers will have rightfully passed the initial round of risk assessment, despite being flagged as potentially high-risk. This can owe to factors such as their presence in politically exposed person lists and negative media coverage. Such accounts are especially likely to be subjected to account takeover (ATO) attacks, meaning while these customers pass the onboarding stage, the account activities themselves should not pass the KYT stage.
Thankfully, SEON can combat ATOs through its IP geolocation and transaction monitoring capabilities. These solutions allow you to set rules that boil down to such criteria as “Flag transactions made from high-risk locations” and “Reject transactions that are 200% higher in value than customer’s previous payments”.
You can also learn how SEON helps you spot would-be money laundering transactions with its AML screening API, which factors in PEP checks, sanctions lists, and much more – all to help your organization become as safe, profitable, and AML- and CTF-compliant as possible.
Sources