The demand for transaction monitoring software is increasing rapidly. According to Allied Market Research, the market value of such systems will reach $25,419.40 million by 2026 – which would make it see an almost 219% increase from when it was valued at $7,957.14 million in 2018.
We look at how it works for businesses along with the best tools for the job.
What Is Transaction Monitoring Software?
Transaction monitoring software is a tool used by financial institutions to automatically detect and flag suspicious transactions, including high-value cash deposits and unusual account activity. It is an essential component of the Anti-Money Laundering (AML) framework, which helps institutions comply with regulations set by government bodies and international organizations. By identifying these red flags, the software helps prevent fraud and illegal activities, thereby protecting both the institution and its customers.
Key Features To Look For in Transaction Monitoring Software
A transaction monitoring software must be powerful enough to help you meet compliance regulations, and flexible enough to be updated regularly. Let’s explore the key features here:
- Risk scoring: At the core of every transaction monitoring tool is rule management, which is designed to trigger alerts based on your risk management strategy. However, the best software lets you calculate a risk score, which is more flexible by allowing you to determine whether the transaction must be automatically accepted, declined, or sent for manual review.
- Custom rules: Compliance requirements change regularly, which is why it’s crucial to be able to update your rules manually, without having to rely on developers. Make sure your transaction monitoring software lets you easily create, edit, and update rules.
- Real-time alerts: Transaction monitoring tools must flag suspicious user actions as soon as possible. The results should be delivered within milliseconds for two reasons. First, it helps with compliance. Secondly, it also removes friction and frustration for legitimate customers.
- Sandbox testing: You will want to test your risk rules using live data, but also based on your historical data. This is why it’s important to be able to test transaction monitoring software in sandbox mode, to ensure you have the lowest number of false positives and negatives.
Other useful features may include AI or ML analysis, which can offer suggestions to improve your risk rules based on your own data, or the automated creation of reports such as suspicious activity reports (SARs).
The 6 Best Transaction Monitoring Software and Tools
Disclaimer: Everything you’ll read in this article was gleaned from online research, including user reviews. We did not have time to manually test every tool. This article was last updated in Q1 2024. Please feel free to contact us to request an update/correction.
SEON – Transaction Monitoring Software Tailored to your Business
SEON provides end-to-end fraud prevention and detection, enhancing AML compliance thanks to its advanced AML API. This API conducts extensive checks, including PEP (Politically Exposed Persons) and relative lists, criminal watchlists, sanctions, blacklists, and more.
The platform stands out for its adaptability, enabling users to swiftly establish custom risk rules, incorporate industry-specific default rules for automated transaction monitoring, and define their own thresholds for identifying high-risk activities.

Read reviews of SEON Fraud Fighters on G2
SEON’s AI-driven risk scoring, machine learning rule recommendations and seamless integration with various risk management tools make it a comprehensive anti-fraud solution that combines digital footprinting, email, phone and IP analysis, device fingerprinting and more with AML for fraud protection and seamless KYC.
It provides a no-code environment for creating custom rules to monitor transactions, aligning with your specific risk appetite and business requirements. Users can explore its features through a free trial before opting for one of the flexible purchasing plans with monthly contracts.
Learn more about SEON’s capabilities
With SEON:
- Screen transactions with easy-to-use rules
- Lock down suspicious activity with machine learning
- Improve compliance with AML screening
- Utilize transaction monitoring services
Speed up and automate your AML screening, monitor transactions in real time with easy-to-create rules and lock down suspicious activity with machine learning.
Ask an Expert
Unit21
Unit21 is a platform that provides no-code tools and services for risk and compliance teams. Unit21 helps protect businesses against adversaries through a simple API and dashboard for detecting and managing money laundering, fraud, and other sophisticated risks across multiple industries. It is built with state-of-the-art security practices by security experts who have defended large systems against hackers.
SAS
SAS provides business analytics software and services and is the largest independent vendor in the business intelligence market. It helps organizations anticipate business opportunities, empower action and drive impact. SAS takes a unique hybrid approach to transaction monitoring, combining advanced analytics, AI and machine learning with traditional detection methods to uncover suspicious events. The SAS approach includes the latest advances in graph analytics, social network analysis, anomaly detection and text analytics.
Actico
Actico calls its suite of products a digital decisioning platform, and it’s easy to see why it is becoming a leader in the world of transaction monitoring software. You get all the expected key features, but also a specific Money Laundering Detection System (MDLS), credit scoring tools, etc.
While it is a powerful and complete solution for compliance, it is worth noting that Actico offers little when it comes to traditional fraud prevention and identity verification, which means you’ll need an extra solution to meet KYC or PSD2, among others.
iComply
Also known as iComplyKYC, this company covers compliance in 240+ countries and supports 4,000 document types for identity verification. But when it comes to anti-money laundering compliance, it is just as impressive, allowing you to automate screening thanks to its access to exclusive global databases.
The transaction monitoring tools are limited, however, only allowing you to focus on individuals rather than the transaction amount, for instance. Still, it is a robust AML solution that can meet part of your transaction monitoring requirements.
Dow Jones
Dow Jones is an information services company that creates and distributes engaging content and other products and services. Dow Jones offers advanced screening and monitoring services that allow you to automatically track and identify risks with powerful, continuous screening and monitoring of entities and individuals against structured and unstructured data.
Why Is Transaction Monitoring Software Important?
Transaction monitoring software is important because it helps in:
- Detecting fraud and risk in real time, a key feature of transaction monitoring software. By leveraging machine learning, it can quickly identify fraudulent and money laundering activities. AI-generated insights improve the precision and efficiency of detection rules, which can be customized to meet a business’s specific risk tolerance and fraud prevention needs.
- Optimizing risk management, another significant benefit. The software accurately evaluates risk by linking digital footprints, device intelligence, and transaction history. This reduces false positives and improves detection accuracy through custom rules engines, while AI-driven insights automate risk assessments, lowering manual review workloads and costs.
- Upholding compliance in a simplified way by ensuring regulatory adherence with real-time AML screening and monitoring. Advanced velocity rules swiftly detect suspicious behaviors, and transactions are screened against sanctions and watchlists to prevent illegal activities, helping businesses maintain compliance effortlessly.
Ultimately, transaction monitoring renders your organization’s incoming and outgoing payments safer while also helping you achieve compliance while becoming more efficient, trustworthy, and respectable.

How to Deploy Better a Transaction Monitoring Tool
Transaction monitoring software can be part of your AML and fraud solutions, a fully automated on-premise installation, or an outsourced third-party solution you deploy as part of a multi-layer approach to risk management.
Regardless of your approach, here are a few tips on the best practices.
- Combine transaction and customer monitoring: Transaction monitoring should examine both inbound and outbound data, as well as the identities of those sending or receiving money. This overlaps with customer due diligence (CDD) and know your customer (KYC) processes. Accurate identity verification, using ID verification software, is crucial for spotting discrepancies in account activity and enhancing overall compliance within your AML strategy.
- Compare user account activities: Customer behavior varies widely depending on the financial services offered. Neobanks and challenger banks, for example, must be vigilant against fraudsters using accounts for illegal money transfers. To maximize efficiency, understand typical user behavior by comparing account data points. Ensure your transaction monitoring software supports custom rules, risk labels, and alert priorities. This aligns with expert recommendations to tailor AML responses to specific company risks.
- Monitor transaction velocity: Your transaction monitoring system should include the option to set velocity rules. A velocity rule is designed to identify suspicious activity based on a rapid movement of funds. However, your limits need to take into account outliers or regular large deposits such as a paycheck.

- Double-check IBANs: International Bank Account Numbers, or IBANs, used to be a reliable way to link identities to banks. You can still go to a website like IBAN.com to check, validate and find bank information based on one of these numbers. In the age of neobanks like Wise, Revolut, and Monzo, IBAN monitoring can lead to false positives since these banks use sponsor banks for IBANs. Consider this discrepancy when automating monitoring with geolocation and sanctioned country rules.
- Log data for retroactive analysis: Documentation and record-keeping are imperative, and not just for real-time screening and reporting. Your transaction monitoring system should also give you access to past data, to reassess previous transactions based on new insight and information.
Ultimately, post-analysis can also be useful to feed data to an AI-driven system, which could update its algorithms in order to suggest more effective risk rules when assessing future transactions.
Stop new fraud trends and enable your growth with SEON’s real-time data enrichment, whitebox machine learning, and advanced APIs.
Ask an Expert
The Challenges of Deploying Tools for Transaction Monitoring
Transaction monitoring software is a legal requirement, but it tends to divide companies and risk management teams when it comes to its effectiveness. This is partly due to the following reasons:
- Added expense: Transaction monitoring tools can be either deployed on-premise or be outsourced. Either way, it is expensive to integrate, monitor and update.
- Resource-intensive: Software helps you process a lot more data as you scale, but you still need a fully-staffed risk management team to manually verify alerts and to produce reports.
- Time-consuming: The large number of alerts to monitor can require a tremendous amount of time and effort from the compliance department.
How SEON’s Software Does Transaction Monitoring
At SEON, we’ve put together all the fraud prevention tools you need for identity verification, transaction monitoring, and user authentication.

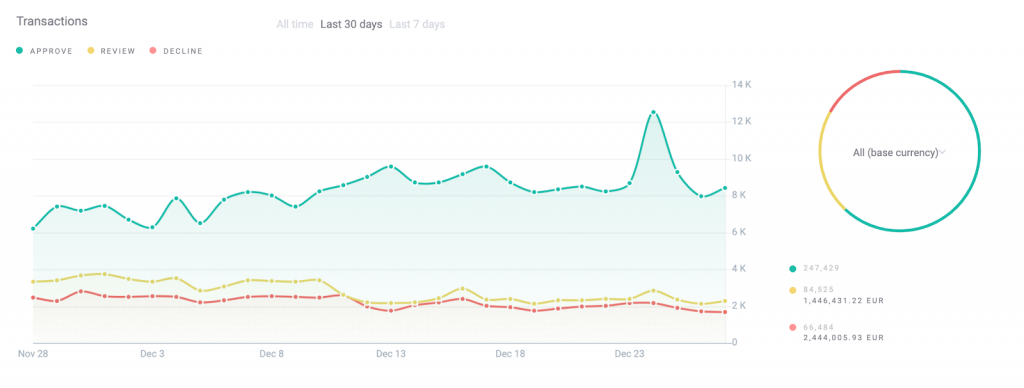
Our powerful system focuses on helping you understand user behavior via customizable rules. You have complete control over customization to adapt the system to your risk appetite, whether it’s to create new rules or accept suggestions from our machine learning engine. See below an example of us in action:
Our goal? To give you access to an extra layer of hidden data to complete your AML compliance efforts, with complete control over the pricing.
FAQs
Transaction monitoring software automates the detection of suspicious transactions in real-time, essential for AML and transaction fraud detection. It collects and normalizes data, applies rules to identify suspicious activity, and uses advanced analytics to detect anomalies. The system generates alerts for flagged transactions, which AML analysts review and investigate. Confirmed suspicious transactions are reported to regulatory authorities. The software is continuously updated to adapt to new threats and regulatory changes.
Transaction monitoring helps block money-laundering attempts and other illegal activities. A financial institution that fails to meet AML requirements will have to pay hefty fines.
Companies can monitor their users’ transactions manually or build in-house tools. However, a growing number of companies choose transaction monitoring software. These third-party tools integrate with your system and monitor withdrawals, transactions and payments, including real-time alerts if they go over certain AML thresholds.