What Are Velocity Checks?
In fraud prevention, velocity checks look at various different factors which might not be suspicious in isolation but become suspicious when they’ve taken place within a certain timeframe.
A simple example:
A single user attempting to pay with one or two frozen credit cards is nothing unusual. They might have forgotten, or someone they share the account with might have blocked them.
However, a single user attempting to pay with five different frozen credit cards within ten minutes is highly suspicious, as even someone in dire straits would likely stop once they realize one or two of their cards have been frozen or canceled.
On the contrary, a criminal attempting to find which of their stolen credit cards work (a process called card testing) is very likely to do just that, repeatedly.
The element of time is key for velocity checks. Using the previous example, five failed attempts with frozen cards from the same IP address within a year are nowhere near as suspicious as five such attempts from the same IP within ten minutes.
What Are Velocity Rules?
A velocity rule or filter is any combination of data points and timeframes used in velocity checking in order to evaluate a user’s behavior and flag it, where needed.
Essentially, they are conditional if-statements linked to timeframes, of the form:
If A happens within B time, then do C.
This is a simplistic breakdown. Real-world applications are normally much more complicated.
For example:
If more than A instances of B behavior occur while C is active and D present, all within E time and from F location, then add +5 to this user’s risk score.
Though such combinations can seem tricky to wrap one’s head around, that is because they are so specific to each organization that is applying them, their industry and their individual needs.
Fraud analysts will already know, or be able to figure out, the pain points in each situation and within the context of each type of attempt at illegitimate behavior.
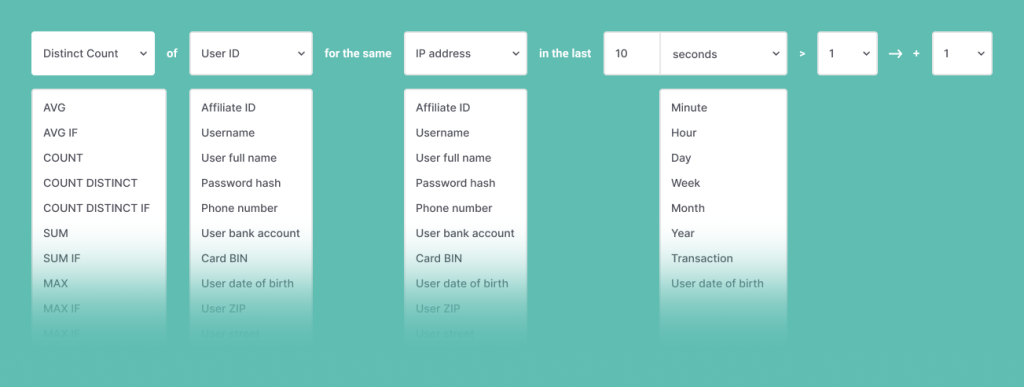
Data points discoverable via device hashes, browser hashes and other means which are taken into account in velocity checks can be any of the following:
- email address
- geolocation
- IP address
- browser and version
- card hash
- device name
- device language
- installed plugins
- and more…
One or more of these data points will be considered within a specific timeframe, from seconds to hours, days, weeks or even years – all according to the specific concern and specific type of fraud we want to detect and block.
As one last example, we can instruct a system to look for this velocity rule:
More than 15 failed attempts to log in to more than 7 different accounts on a website, all from the same device ID, within less than 10 minutes.And when it identifies it, to ban that device for 24 hours.
How Do Velocity Checks Work?
Fraud detection platforms that offer velocity checks follow certain steps:
- Identify relevant data points.
There are several ways to look into historical data and discern which behaviors are indicative of fraudulent activity in each setting (including machine learning). - Create a velocity rule.
This can be any combination of data points and timeframes, informed by the conclusions reached in step 1. - Apply the velocity rule.
The platform starts running constant velocity checks to assess users’ behavior. - Whenever the conditions set out in a velocity check are satisfied, a pre-set result is triggered.
For example,- Blocking a user from continuing a transaction via transaction monitoring
- Assigning a higher risk score to the user
- Asking the user to re-enter their password
…and so on.
- From there, data analysts can amend, add to or delete these rules as needed.
What Is Velocity Checking for Credit Cards?
Payment card velocity checking rules are linked to the use of credit cards over time, flagging behaviors considered suspicious.
They can count how many times a credit card has been used within a certain time period, how many different credit cards a certain IP has attempted within an hour, or even trigger specific spend limits for instance.
What Is a Velocity IP Check?
Velocity IP checks prevent fraud by looking at how many actions, transactions or attempts at actions have been submitted from a specific IP address over time – usually, a short amount of time.
When creating such a velocity rule, we take into consideration what is considered normal user behavior and compare it to what fraudsters have been doing or are likely to do in the same environment, as part of a coordinated attempt to stop them in their tracks.
How to Use Velocity Checks and Velocity Rules for Fraud Detection
In fraud detection, velocity checking allows us to identify previously concealed connections between users and actions, or even combinations of users and actions, by bringing the element of time into the equation.
This means we don’t just rely on the data points themselves to tell us what a user is likely up to, but those data points as observed within the context of time.
The data points can come from device fingerprinting, canvas fingerprinting and other sources, and they’re given a new dimension through velocity checking.
There are virtually infinite numbers of combinations that one could come up with to create rules and filters for velocity checks. This is why, for effective fraud detection, it is essential to consider exactly which fraud checks are valuable in each situation, for each business or for each action.
Some platforms offer pre-set suggestions per client industry. An airplane ticket aggregator will have different concerns than a cryptocurrency exchange platform.
The latter is part of an industry that tends to attract money launderers, so the velocity checks implemented will look for specific kinds of transactions done within specific timeframes, flagging anything suspicious for manual review.
Why Are Velocity Checks Important?
Velocity checking in the context of fighting fraud allows for:
- A deeper understanding of user and fraudster behavior
- Improved fingerprinting
- Better detection of fraud rings
- Improved grasp of threats and threat trends
- More precise and efficient fraud detection
- Prevention of more elaborate types of fraud
- Deterring fraudsters making use of more advanced tech
Velocity rules can help detect threats such as:
- account takeover fraud
- poker bot farm use
- high-risk users old and new
- identity morphing, synthetic identity fraud
- chargeback fraud
- bonus abuse in iGaming
- card testing
- eSports fraud
- …and more
Velocity checks are customizable and, when used optimally, they are tailor-made to each organization’s needs, helping fraud analysts to learn more about user and fraudster behavior as well as to weaponize this knowledge in the fight against fraud.
For organizations frequently targeted by fraudsters, a multi-layered approach that includes velocity checks is ideal.