Fraudsters are just as tech-savvy as they are lazy. How can they multiply attacks to target your business? Through the use of bots.
Thankfully, bot detection is easier than you might first think.
What Is Bot Detection?
Bot detection is any process designed to identify the presence of bot traffic on a website, server, network, etc. It is made to detect individual bots and scripts, as well as botnets comprised of several bots, which can be in the thousands. The idea is to be able to tell human traffic from bot traffic.
In general terms, you may want to block your average bot. But they’re not all malicious bots – but there are also useful bots out there that you will certainly want to allow, such as Google’s spiders, which index web pages.
In the context of fraud detection, bot traffic always has a negative connotation, as fraudsters will attempt to use bots in order to automate and scale their attempts against a business or organization.
The Importance of Bot Detection for Businesses
As a business, your goal is to ensure web traffic comes from legitimate users, so you’ll want to detect bots and block their access to all or certain parts of your infrastructure. This is because fraudsters rely on bots to automate actions such as taking over user accounts, making payments with stolen credit cards, or digital onboarding with fake identity details.
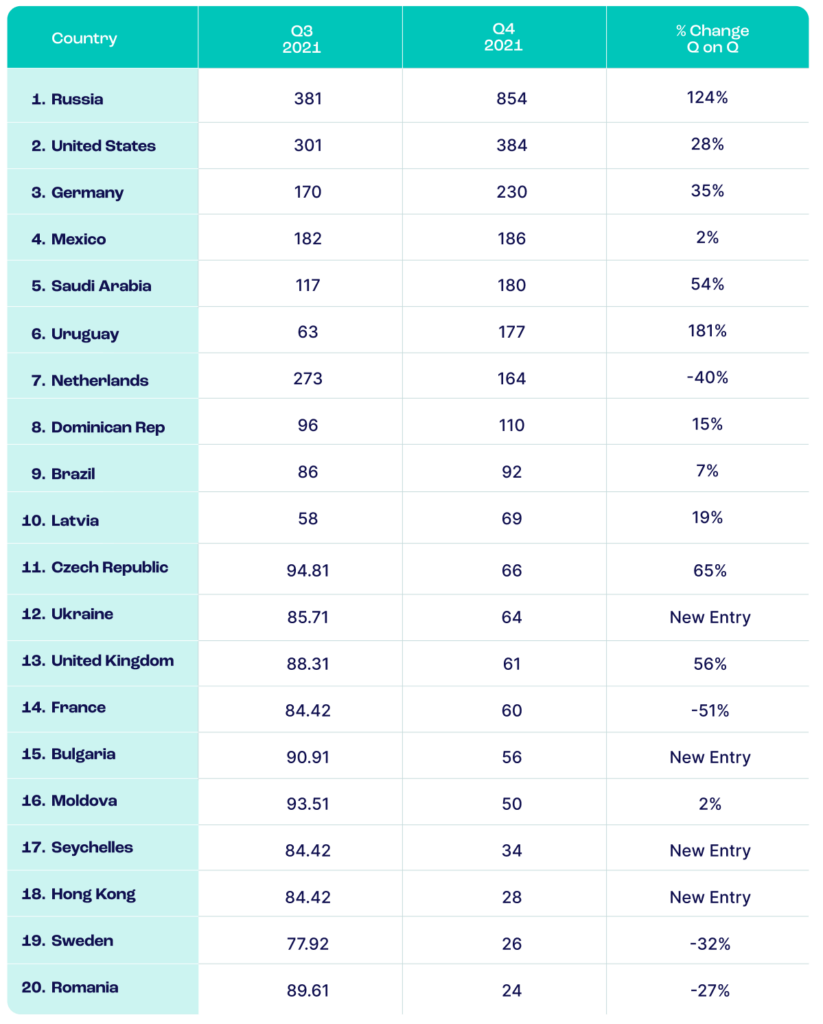
To make matters worse, bot attacks are on the rise globally. Cybersecurity firm Spamhaus identified a 23% increase in botnet traffic in Q4 2021 compared with the previous quarter.
Here is a list of where this automated traffic comes from:
Explore a demo with us today and find out how we can help you together.
Ask an Expert
Bot Detection Techniques
Common bot detection techniques for finding and stopping bot traffic include:
· flagging suspicious tools that enable bots
· using privacy-focused browsers
· using software and apps specifically designed to detect bots
Bot detection techniques vary in their efficacy. As such, if you’re keen to protect your business from the negative consequences of bot traffic, it’s a good idea to use a combination of approaches. Let’s take a look at some of these:
- Device fingerprinting: This technique allows the software to gather non-identifiable information about each visitor’s software and hardware, in order to flag up any use of suspicious tools and software that could hint at a bot or script. Look for software where you can customize the risk rules and risk scoring so that you can fine tune this bot detection method to your unique business setting.
- Device hashes: In the case of bots set up to commit multi-accounting abuse, creating and comparing device hashes will allow you to identify returning users and bots, even if they attempt to pass off as different people. This can stop bots in their tracks, preventing them from setting up multiple accounts (for example to commit bonus abuse on iGaming sites).
- Real-time monitoring: It’s important for high-risk organizations to continually monitor traffic rather than do so periodically. After all, if your aim is to stop bad bots harming your business, you need to catch them as soon as they try to carry out their malicious actions, not after they’ve done so.
- Firewalls and blocklists: Depending on the needs, infrastructure, and risk appetite of your business, you may find that a Web Application Firewall (WAF) or Access Control List (ACL) is sufficient. This will observe and filter traffic, blocking unknown users, including bots, to provide protection from session hijacking, cross site scripting, SQL injections, and the like. However, while WAFs can work well for blocking known, familiar threats, they are insufficient for keeping up with more evolved, advanced bots.
- CAPTCHAs: For bots set up to automate the creation of multiple accounts, including for bonus abuse and other pain points, sometimes the addition of a CAPTCHA “prove that you’re human” step to onboarding is enough to stop them. At least, it used to be… nowadays, bots can connect to CAPTCHA farm APIs that solve CAPTCHA challenges in seconds. CAPTCHAs also create friction for genuine users, meaning they are far from ideal for many businesses.
- Two-factor authentication (2FA) and multi-factor authentication (MFA): To mitigate the risk of bot-enabled account takeovers, you can encourage or force users to use multi-factor authentication for greater security than old-school username/password combinations can provide. Of course, MFA won’t protect you from other types of bot attack, such as distributed denial-of-service attacks, so you’ll need other defenses in place to counter those.
The best strategy is to implement a range of bot detection techniques to ensure your business is well protected.
Why Is Bot Detection So Difficult?
When it comes to the detection of basic bots, adding a few rudimentary technical hurdles will work. For instance, CAPTCHA is known to reduce bot-driven form submissions by 88%.
Things get more challenging when you deal with bots designed to replicate human behavior.
Referral fraudsters, for instance, utilize sophisticated automation designed to trigger rewards an starting affiliate fraud.
This is an example of what this kind of bot can do:
- A fraudster signs up for a pay-per-lead program
- They launch bots to automatically click on the link
- Automatically fill in all the details using synthetic or made-up user data
- Deposit money using a stolen credit card number
- Trigger the signup reward
- Change the IP and device settings, and repeat
As you can imagine, complex sequences of events are harder to detect than simple fraud attacks – especially if they’re designed to pass off as a human.
That is, of course, unless you have the right bot detection tool at your disposal.
How Does SEON Help With Bot Detection
SEON is a full end-to-end risk mitigation platform that enables fraud detection and bot mitigation through powerful APIs, machine learning and custom rules.
Uniquely, it also harnesses the power of data enrichment, gathering information from 90+ social media and online sources in real-time to learn more about users. Specifically:
- IP lookup: Does the user connect using a VPN or proxy? While this is not enough for a user to be marked as a bot, hiding connection details is enough to flag a potential risk to fraud and risk managers. IP lookup can also show if a connection is a long way from the user’s shipping address – another red flag.
- Email address lookup: Is the email address from a free provider? Is it registered to any social media accounts?
- Phone number lookup: Does the phone number point to a virtual SIM card? Is it registered to WhatsApp, Viber, or any other mobile-first platforms?
- Bank Identification Number (BIN) card lookup: Is the card type consistent with what you’d expect? A prepaid US card for a customer in Greece, for example, could raise suspicions.
SEON also uses device fingerprinting to show exactly how users connect to your site. This is especially good for highlighting emulators and virtual machines for better bot management.
Device fingerprinting examines installed plugins, web browser version, browser window size, screen resolution, language used and more, then automatically creates a device hash.
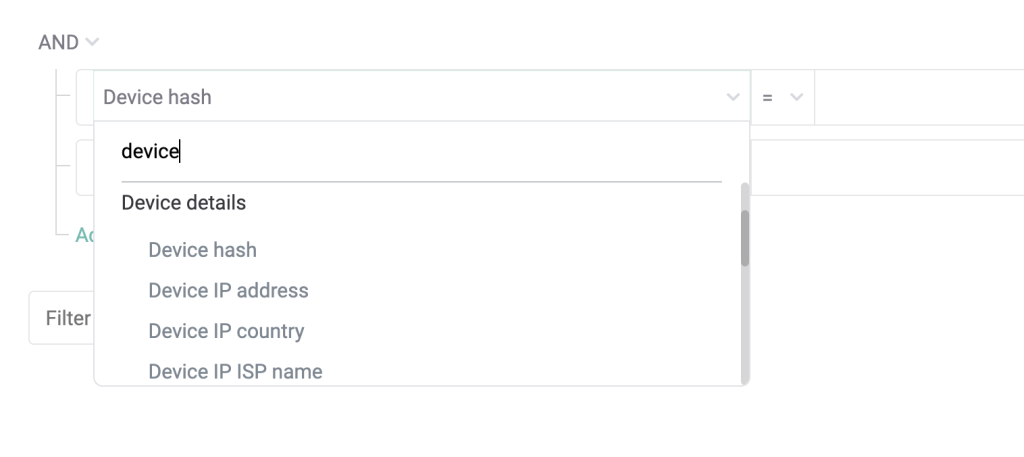
The device hash can be used along with velocity rules, or velocity checks, to allow you to monitor user actions over time and understand user behavior through data.
If a new user pops up, adds a product to their cart, checks out, then enters three different credit card numbers within a minute, velocity checks can flag this as suspicious.
SEON can also spot suspicious connections between users and transactions. The fact that fraudsters reuse bots to perform the same action multiple times means there will be patterns in the data.

SEON Fraud and Customer Success Manager Conner Keele showed how such data can be used to detect bots when he spotted 700 fraudulent iGaming accounts in one hour. Conner noticed several hundred users signing up from the same internet service provider, all using outlook.com email addresses in the same format ([email protected]) and all using the same security question. By filtering through the data points, Conner realized he was looking at a fraud ring using bots to sign up and claim rewards (a practice known as bonus abuse).
The key to good bot detection is to combine all of the above in order to model what good or suspicious behavior looks like in the unique context of your business.
Join us for a demo to discuss your needs and see how SEON’s powerful engine can help.
Ask an Expert
FAQs for Bot Detection
Bot detection starts with gathering data about your user’s behavior and connection. By looking at whether they connect with proxies, VPNs, or Tor, you can increase suspicions. Emulators and virtual machines should also raise red flags. Then you need to compare such data and user actions with others to spot patterns.
An IP address isn’t usually enough to let you know if you’re dealing with a bot or not. However, you can assess whether it points to a VPN, proxy or Tor browser. This can help you raise red flags, depending on the user’s behavior.
The easiest way to block bots is to enable CAPTCHAs. However, it won’t stop the more sophisticated bots. To block those, you need to enable a combination of data enrichment (to learn more about how they connect to your site) and velocity rules (to understand their online behavior).
Sources