What Is a Device Hash?
A device hash or hardware hash is a string of numbers and letters generated by a computer, phone, tablet or other device at the request of a piece of software, which contains information about the device and its user.
This information is akin to a device’s identity. It can include information about the local date and time, operating system version and type, hardware such as GPU, screen data, and more.
Each hardware configuration (but not each individual device) has a unique ID. This helps find connections between ostensibly different users, identifying and thwarting attempts at fraud, as well as provide other bits of useful information.
How Do Device Hashes Work?
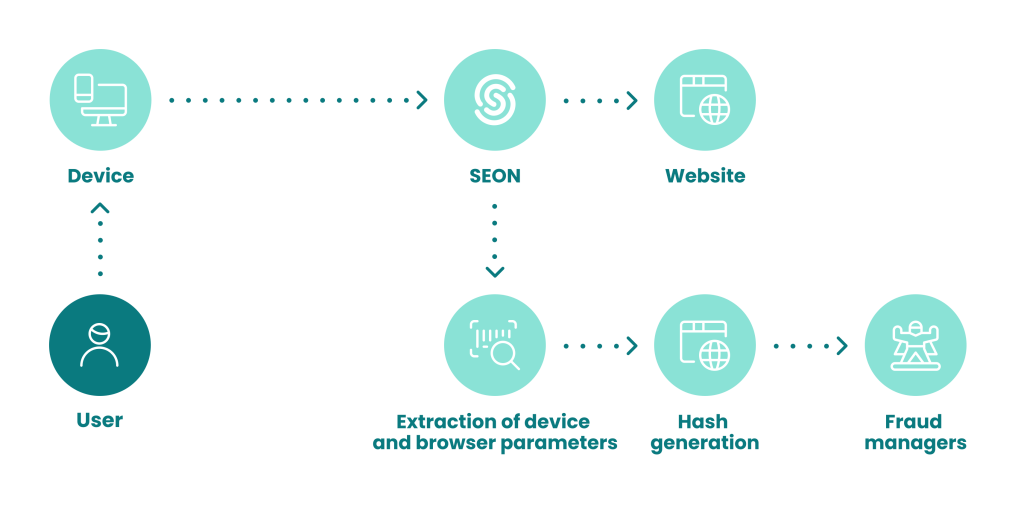
Device hashes largely work behind the scenes, when software requests one in order to be able to identify some basic information about the device, in a process called fingerprinting.
- When a user attempts an action online, a piece of code can ask their system for its device hash.
- The hash is generated from certain simple parameters about their hardware.
- The hash is submitted to the requester.
- The requester reads it to find useful information.
- The requester combines the device hash and other parameters, and compares it to a list of previously gathered hashes to reach conclusions about the user and their intentions.
It should be noted that efficient fingerprinting involves the exchange of several different types of hashes and information, not just a device hash.
When considered in tandem, these parameters will signpost useful information about how much of a risk a user could be, whether they are using spoofing software, if their hardware is adequate to run a web app or other software, and so on.
Are Device Hashes Unique?
Device hashes are as unique as the basic configuration of the device they correspond to. For systems such as mobile devices, this can be fairly common: two iPhone 7 devices running Safari will return the same device hash.
With PCs, a configuration is not as likely to be identical to others. Nevertheless, all device hashes, when analyzed together with all the other data sourced during the device fingerprinting process, will lead to fairly unique results that can be used to make certain deductions.
Device hashes do not contain any private or sensitive information about their users. Rather, they serve to show whether a computer, tablet or smartphone has visited a website, or attempted or taken another specific action before, and some general information about its hardware, which can include:
- MAC address
- battery health
- HTML5 canvas information
- time zone
- device time and date
- CPU details
- GPU information
- audio fingerprinting
- serial number
Can You Change a Device Hash?
For most people, there is no reason to want to change their device hash, as it does not reveal anything noteworthy about themselves or their setup. Moreover, digital fingerprinting typically involves requests for more than the device hash of a user, so changing the device hash does not amount to much.
In general terms, existing methods to change a device hash utilize a process called spoofing. These will usually replace the user’s device hash with the same one for all their users.
For example, FraudFox, AntiDetect and Multilogin will change users’ hashes, but will not adequately hide the fact they are using these tools to provide a false device hash.
How Do Device Hashes Help Fight Fraud?
Together with other data points and hashes, device hashes provide valuable information during fingerprinting, which helps flag users involved in nefarious activities.
In cybersecurity, fraud detection and adjacent fields, device or hardware hashes will show repeated, supposedly separate requests originating from the same device, which will then be treated as suspicious.
A simple example:
- A cybercriminal acquires a list of user credentials or stolen card details.
- They need to try each to find out which ones work. This can be manual or automatic but several (if not all) will be tested from the same device.
- The fraudster will try one set of credentials, and note the results.
- Before they try again, the fraudster will take certain steps to hide the fact it’s the same person trying more than a couple of cards, instead pretending to be a new, legitimate user/device – e.g. clear their browser cache, run a spoofing tool, or use a device emulator.
- They then try a new set of credentials.
- Steps 3 and 4 are repeated as needed.
Device fingerprinting can help stop these cybercriminals in their tracks, because it is a more advanced, composite technique that takes into account red flags generated by spoofing tools, compares IP address/device hash pairs, and so on.
By using device hashes, cookie hashes, browser hashes and other parameters, fingerprinting protocols can flag a user as high risk when they have made repetitive, suspicious requests, blocking their attempts at fraud.
Read how to leverage this key fraud prevention technique and how it’s used to protect businesses like yours globally.
Read More Here