Affiliate marketing is an inherently fast-growing industry. Astute Analytica forecasts a dramatic increase in revenue for the global affiliate marketing platform market: Following its value of $19,217.4 million in 2021, it’s predicted to grow at a CAGR of 7.9% and reach $36.9 million by 2030.
According to CHEQ, 2022 alone saw $35.7 billion of ad spend budget lost to fake and fraudulent web traffic. In fact, one in ten of the observed website visitors were found to be inauthentic – and one in fifty had outright malicious intent.
What Is Affiliate Fraud?
Affiliate fraud refers to any scheme that takes advantage of a company’s marketing partnership programs that offer compensation for sending traffic through gateways that lead to sales. This form of fraud can be performed by forcing bad traffic through the website that almost never results in a sale, or else using automated bots to trigger the affiliate payout reward.
Why Does Affiliate Fraud Happen?
Affiliate fraud is the product of inflated click-through rates (CTRs) that are used to manipulate exploitable software, such as pay-per-click (PPC) counters. Such software is used by organizations hiring affiliates who end up fraudulently manipulating the terms of their affiliation agreement with one or more technical machinations.
Here’s a look at five examples of the many ways that fraudulent affiliates can exploit CTR counters for illicit gain:
- Traffic laundering: one or more middlemen misguide website visitors with multiple deceptive tactics, such as fake and click-baity articles (with hidden ads embedded within them), social engineering emails, and redirects
- Bot attacks: when bots are used to “visit” target websites in an attempt to appear as legitimate human-made CTRs
- Identity theft: fraudsters pretending to be multiple people by visiting target webpages from real profiles – whose owners are both unwilling and unaware
- Ad stacking: multiple ads are stacked beneath one visible, surface advert, so any visitor making misguided and repeated clicks obliviously causes inflated CTRs
- Pixel stuffing: multiple, tiny ads are “stuffed” into pixels to trick CTR counters into tracking a highly exaggerated number of ad impressions
Types of Affiliate Marketing Fraud
Fraudsters have created a range of ways to turn affiliate schemes to their advantage. Let’s look at some of the most common.
- Duplicate content and shell websites: Malicious affiliates may simply clone the website of a high-performing, legitimate affiliate, then manipulate search engine optimization to divert traffic to their cloned site.
- URL hijacking: The fraudster buys domain names that are similar to a genuine website with an affiliate scheme. They register for the affiliate service then, when a user accidentally visits their URL instead of the genuine site, they trigger an event click for that user. The user either realizes their mistake and types in the correct URL or the scammer sets up an immediate redirect that takes the user to the correct site automatically. Either way, the affiliate fraudster gets paid as a result of triggering the event click.
- Click stuffing: As cost-per-click models are common among affiliate programs, fraudsters may use dedicated bots or click farmers to maximize the number of clicks through a specific link and collect the associated rewards.
- Click spoofing: Fraudsters can set up sites with affiliate links, then fire click-tracking events to those running the affiliate schemes for users who visit the fraudster’s site – even if the users themselves don’t click any affiliate links. Then, if the user goes on to make a purchase via any other route, the fraudster gets the credit even though the user didn’t click any of their links.
- Cookie stuffing: This also targets users who may not have clicked any affiliate links. The user visits the fraudster’s website, which uses automation to drop cookies on the user’s browser. Should the user go on to make a purchase from the affiliate scheme owner at a later date, the fraudster will get the credit for it.
- Hidden landing pages: Similar to cookie stuffing, hidden landing pages with affiliate links drop cookies on the user’s browser when they open. Again, the fraudster gets the undeserved credit should the user go on to make a purchase. Fraudsters can trigger these hidden landing pages to pop up when a user visits their site.
- Fake conversions: Affiliate programs often use cost-per models, such as cost-per-acquisition (CPA) or cost-per-click (CPC) but can be changed to reward affiliates who provide anything, such as leads, impressions, or app installs. These kinds of payout models can be exploited through either click farms or automated bots that can click links, fill out applications, and even make purchases with stolen credentials, all of which may trigger payouts to the fraudulent affiliate.
- Malware: Fraudsters can use malware to target online shoppers. They register for an affiliate scheme, then use malware to inject their affiliate codes into infected shoppers’ transaction processes, triggering payouts to the fraudster. Serving ads with infected code (known as malvertising) is one way that affiliate fraudsters can spread their malware. Those ads – purchased and served on other sites – can also infect the user’s machine with a click-generating virus, making it appear to the affiliate scheme operator that the fraudster has generated more clicks than they have.
A range of other types of affiliate fraud exist, from using stolen credentials to generate fake leads or make purchases to more complex schemes, meaning that any business that runs an affiliate scheme must be permanently on guard.
Protect your business with SEON’s advanced real time fraud fighting tools to keep your business secure
Ask an Expert
3 Ways to Detect Affiliate Fraud
If affiliate fraudsters are targeting your business, you want a three-pronged approach to check the quality of your marketing partner. Ideally, your fraud prevention solution should be able to deliver the following tools:
Monitor the Traffic
The first step is to keep track of traffic quality. Make sure your system allows you to log affiliate IDs, and that you get an accurate view of how many of the users they bring. You should also know how many of their visitors go through the conversion stage successfully.
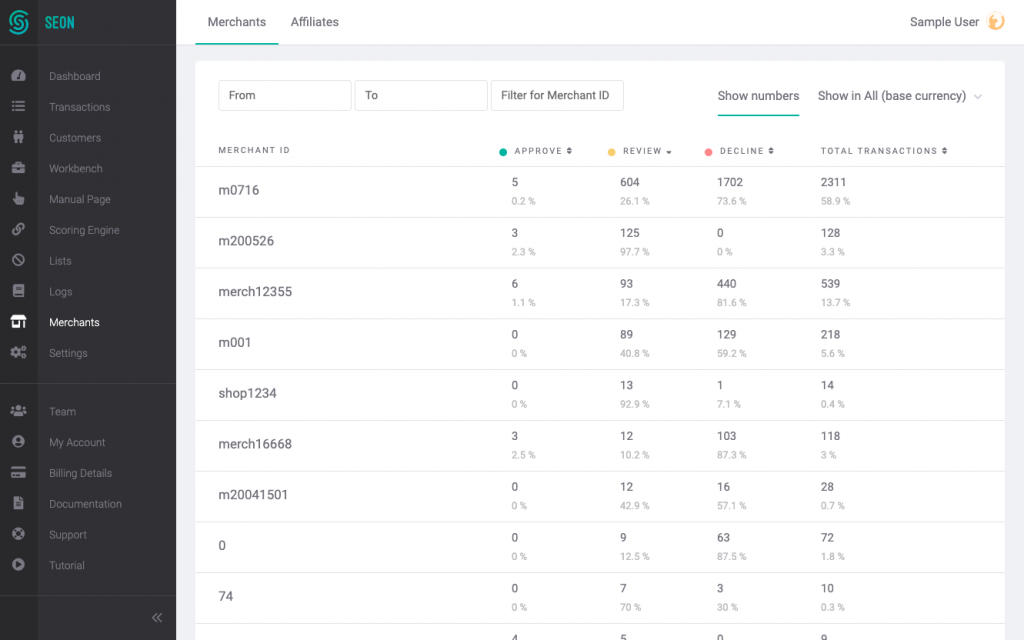
In the screenshot above, we can clearly see that each merchant (or affiliate) brings in users whose transactions are approved, reviewed, or declined. These three results can of course be automated by your fraud prevention system.
But the key point is that after logging every conversion for a while, you’ll have enough data to start separating good affiliates from bad ones.
But what if you want to block fraudulent traffic before it enters your system? You can look at device fingerprinting.
Enable Device Fingerprinting
Each user that lands on your conversion page will arrive with some data. We call it a digital footprint, and it includes the configuration of their software and hardware.
With a device fingerprinting module on your site, you can create IDs for these configurations, and see when anything looks suspicious. For instance:
- Has this exact configuration already been found on your site? There is a possibility you could be dealing with a fraudster trying to fool your system with multi-accounting.
- Does the device point to an emulator like FraudFox, Kameleo, Linken Sphere, MultiLogin or AntiDetect? These are tools favoured by fraudsters who use bots to abuse affiliate programs on a mass scale.
Combined with other data enrichment tools, you will be able to build a pretty complete profile of your users – all in real-time.
Note that device fingerprinting is also a fantastic tool for curbing bonus abuse, for instance in the gambling world, or even to reduce chargeback rates and manual reviews.
Behavior Analysis
In fraud detection, the behavior is tracked via a series of risk rules. Every time the user data is checked against the rule, a risk score increases or decreases.
The most obvious example would be a standard IP analysis. Is the user’s IP address pointing to the same location as the cardholder’s address? But you can of course get much more sophisticated with the rules:
- How many connection attempts did they make per hour?
- How fast did they complete the fields on your signup form?
- What was the average time it took them between landing on your conversion page and going to checkout?
When it comes to risk rules, the sky’s the limit, and this is where having a talented team of fraud managers can make all the difference. Provided, of course, that your fraud management solution allows you to create risk rules manually – or to get suggestions from a machine learning engine.
How Affiliate Fraud Impacts Businesses
Affiliate fraud can significantly impact businesses, leading to a range of detrimental consequences. When an organization inadvertently enters into a fraudulent affiliate agreement, it can experience:
- disrupted web analytics due to bots
- misused tracking cookies
- and other technical challenges.
These disruptions distort data, making it difficult for businesses to understand their audience’s behavior and preferences. As a result, valuable marketing dollars are wasted on campaigns that yield little to no genuine return on investment, affecting the organization’s overall financial health.
Moreover, measuring and interpreting key performance indicators (KPIs) for ad campaigns becomes challenging, hindering the optimization of marketing strategies. Without reliable data, businesses struggle to make informed decisions, leading to further inefficiencies and potential revenue loss.
Beyond these immediate issues, the long-term consequences of affiliate fraud can be even more severe.
How Affiliate Fraud Damages iGaming Companies
Affiliate fraud poses an especially severe threat to the iGaming industry. The ramifications are extensive and can deeply affect iGaming operations.
- Financial Losses: One of the most direct impacts of affiliate fraud is financial loss. Fraudsters manipulate affiliate systems using bots, fake accounts, and other methods to generate illegitimate clicks and conversions. This means iGaming companies end up paying for fake traffic that never converts into real customers.
- Operational Strain: Affiliate fraud places a heavy burden on company operations. Detecting and mitigating fraud requires significant effort and resources. Teams must sift through vast amounts of data to identify suspicious activities, detracting from other critical business functions.
- Reputation and Compliance Risks: Engaging with fraudulent affiliates can severely damage an iGaming company’s reputation. Customers expect a secure and fair gaming environment, and any association with fraud can lead to a loss of trust. Additionally, fraudulent activities can lead to regulatory scrutiny and fines, especially concerning compliance with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations. Noncompliance with these regulations can result in hefty penalties and further tarnish the company’s reputation??.
- Promo Abuse and Additional Fraud: iGaming companies often use promotions and bonuses to attract new players. However, these incentives can also be targeted by fraudsters. Promo abuse involves exploiting signup bonuses and other offers through fake accounts and manipulated referrals. This not only results in financial loss but also undermines the effectiveness of marketing strategies designed to attract genuine players?.
Affiliate fraud inflicts multifaceted damage on iGaming companies, affecting their finances, operations, reputation, and compliance status. Addressing these challenges requires comprehensive fraud prevention strategies, including advanced monitoring systems and stringent affiliate vetting processes?.
An Example of Affiliate Marketing Fraud
The iGaming industry is susceptible to affiliate fraud because it relies on affiliate marketing more than many other types of businesses. However, many other industries also face the risk of affiliate marketing fraud. An example of this type of fraud in action looks like this:
- Fraudsters sign up to your referral program.
- They purchase stolen ID data on the dark web.
- Bots automate the signup process on your site, using stolen IDs and multi-accounting.
- Sophisticated bots can even replicate human behavior (browsing, transactions, etc).
- Fraudsters get a referral fee because everything looks legitimate, while you are left with bad users.
The use of bots means that fraudsters can carry out affiliate marketing fraud such as the above example rapidly and at scale.
How Can SEON Help in Affiliate Fraud Detection
Cutting through the noise is harder than ever for marketers, and things are made more complicated by fraudulent affiliates. The thing is, affiliate marketing is more important than ever for modern online businesses. We live in the age of comparison websites, YouTube influencers, and heightened customer expectations for sourcing engaging content.
The good news, however, is that affiliate fraud software solutions are faster, easier, and more affordable than ever.
Using a simple combination of decent traffic monitoring, device fingerprinting, and tailored risk rules such as SEON’s solution, you should be on your way to flag bad partnerships and focus on the best ones that can really help grow your business.
SEON’s anti-fraud tools are designed to detect suspicious usage and uncover hidden fraudsters
Ask an Expert
FAQs
According to Juniper, advertisers’ total loss to fraud will rise to $100 billion by 2023.
To detect fraudulent affiliates, you must log the quality of the traffic they bring to your website. It’s important to keep track of your conversion rates, but also of the typical user behavior. Monitoring data points relating to user behavior allows you to flag suspicious traffic that comes with affiliate fraud.
You might also be interested in reading about:
Sources:
- AWin: MoneySupermarket Insurance
- TripAdvisor: What is the Tripadvisor Affiliate Program?
- Influencer Marketing Hub: How to Spot Fake Instagram Followers
- Astute Analytica: Affiliate Marketing Platform Market – Industry Dynamics, Market Size, And Opportunity Forecast To 2031
- CHEQ: Examining the State of Fake Traffic in 2023