Fraudsters and cybercriminals have no trouble impersonating other users to steal their accounts, make purchases, and exploit your business.
Let’s see how to stop them with risk-based authentication.
What Is Risk-Based Authentication (RBA)?
Risk-based authentication (RBA) uses scores to determine whether someone should be able to perform an action on your platform or not. This may be a login or a transaction, among others.
The scores are calculated based on risk rules that analyze various factors. For instance, connecting to the site from a blacklisted device or IP address adds to a user’s risk score, which could mean they get blocked.
The key goal of risk-based authentication is twofold:
- to block suspicious users
- to allow legitimate users access to online services without unnecessary obstacles
But it’s not always black or white: Visitors deemed risky should be asked for extra authentication proof, such as passphrases, 2FA codes, or extra ID documents. This means fewer false positives while keeping the risk low.
Why Deploy Risk-Based Authentication?
Taking risk into account when approving user actions, risk-based authentication has become increasingly important in recent years, as rates of ID fraud, transaction fraud, and account takeovers continue to skyrocket. Intellicheck, for instance, reports a 282% surge in account takeovers between 2019 and 2020 alone.
Risk-based authentication isn’t foolproof, and it needs to be deployed with care to be worthwhile. However, it has many benefits worth considering.
Reduce Fraud and Improve Compliance
Companies are increasingly forced to strengthen their fraud prevention measures through proper risk monitoring. In simple terms, RBA is all about ensuring you’re dealing with the right person, whether they are initiating a purchase or logging in to an account.
At the signup stage, you must also check whether you are onboarding a real person. At the bare minimum, you must verify an ID and link it to a name and address.
In certain industries, this falls under the umbrella of KYC verification checks, also known as know your customer checks. These are heavily regulated processes, which means that failing to authenticate a user could result in regulatory fines.
You may also want to authenticate users at the withdrawal or transaction stage to meet AML requirements. Anti-money laundering (AML) rules state that you must verify the identity of users for certain actions, which is exactly what a risk-based authentication tool can help you with.
Ultimately, risk-based authentication helps filter out suspicious users, including those whose profiles are obviously built on falsified, stolen, or made-up information.
Protect Legitimate Users
The second reason to deploy risk-based authentication is to protect existing user accounts. Presumably, you’ve verified identities at the signup stage. What’s left to do is ensure the right people access their accounts later.
If someone gains access to an account without authorization, it’s called an account takeover, or ATO.
By comparing the data you have collected at signup with that of the login, you should be able to get a good idea if it’s the same person. For instance, a sudden change of IP address could increase the IP Fraud score. You should then ask for extra proof.
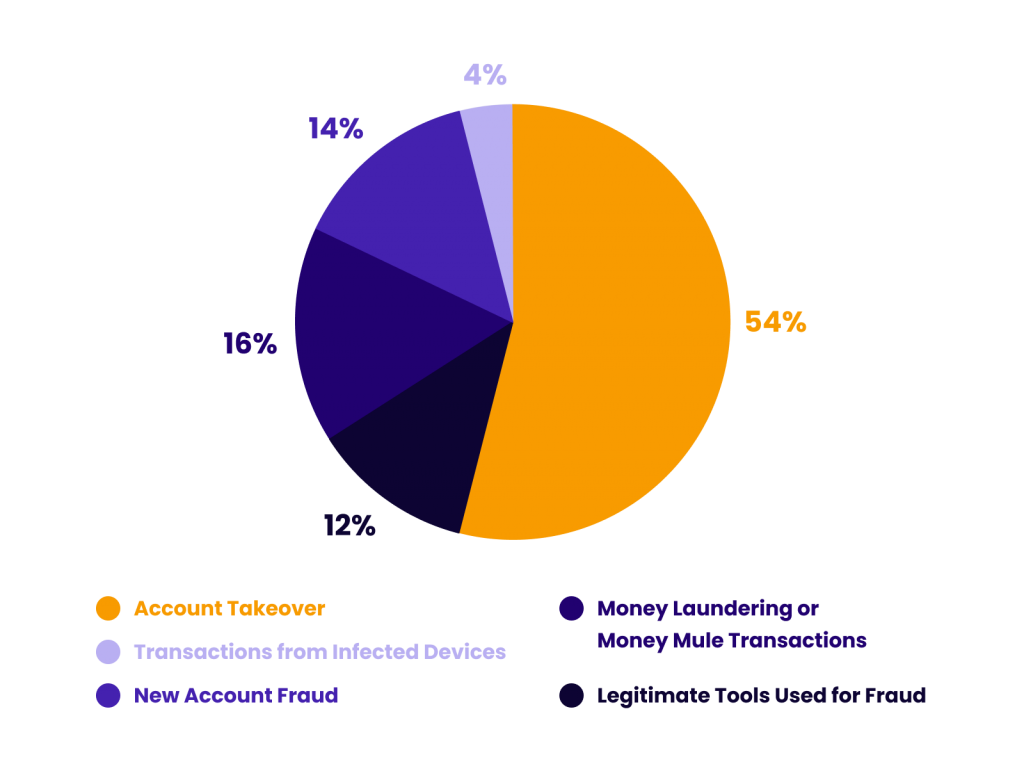
Research by Kaspersky suggests that 54% of all fraudulent online attacks in the finance industry are attempts to log into someone’s account without authorization, as you can see in the pie chart below, along with other findings.
Reduce Friction and Improve Customer Loyalty
Risk-based authentication helps catch bad agents, but it also allows good users through hassle-free. A low risk score doesn’t necessarily prove that the users are who they say they are, but it can certainly help you remove friction from their journey.
In concrete terms, removing friction could look like allowing a user to sign up with no document verification or to log into an account without 2FA. It’s up to you to set the appropriate thresholds based on your risk appetite, as well as any legal requirements.
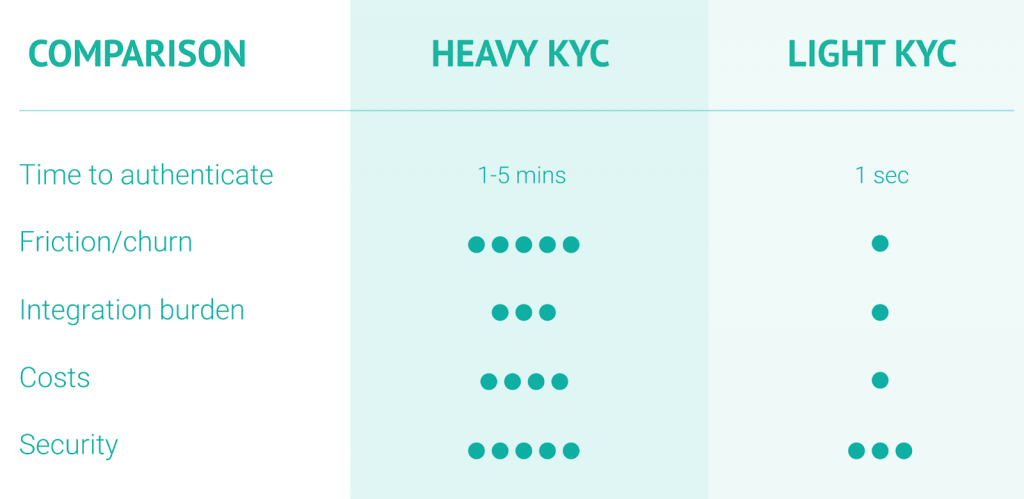
Either way, the result is that you can create a smoother user experience, which has many competitive advantages in today’s always-on economy. At SEON, we call the process dynamic friction, as it allows you to choose between light and heavy KYC based on those early signals.
Automate and Scale
Finally, the key advantage of risk-based authentication is that it’s performed automatically. You can set and tweak rules that take care of the filtering. Risky users are blocked while low-risk users are approved. If they fall within a grey area, you can also perform a manual review.
Having a manual review team is highly recommended; human intelligence and insights can confirm your suspicions. It’s also important to regularly adjust your risk scores, as fraudsters are quick to adapt and find workarounds.
However, risk-based authentication can certainly alleviate the load on your risk management team, so they can dedicate more time and resources to fine-tuning the system and reviewing medium-risk cases. All the rest is taken care of by the risk scoring.
How to Implement Risk Based Authentication
To take advantage of the benefits of RBA, you will need a way to monitor and calculate risk, as well as a mechanism to automate approval or rejection.
This takes the form of risk management software, with end-to-end platforms as well as solutions that stack available on the market.
In the case of SEON, the powerful risk scoring engine makes use of device fingerprinting, velocity checks, and IP analysis, to assess who this customer is and whether they’ve been seen before.
But it’s the data enrichment module that brings in unique, valuable insight that makes it very difficult to fool. Engaging in what is also known as digital footprint analysis, it takes a simple point the user has provided us with, such as their email address or phone number, and enriches it with information from 90+ online platforms and social media to show us who they really are.
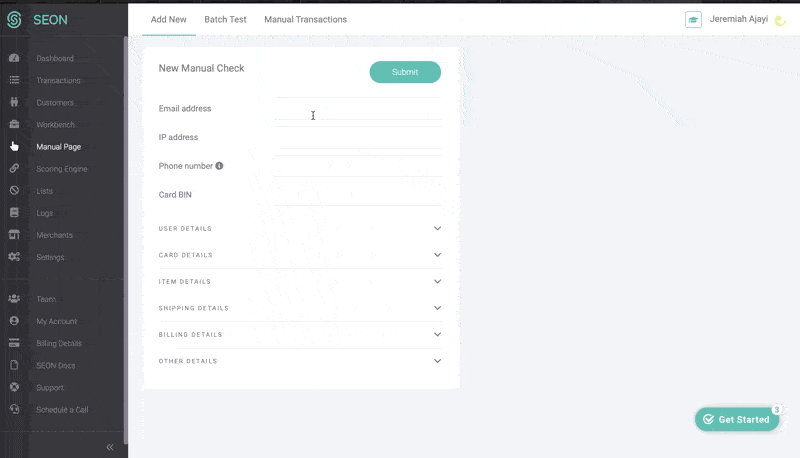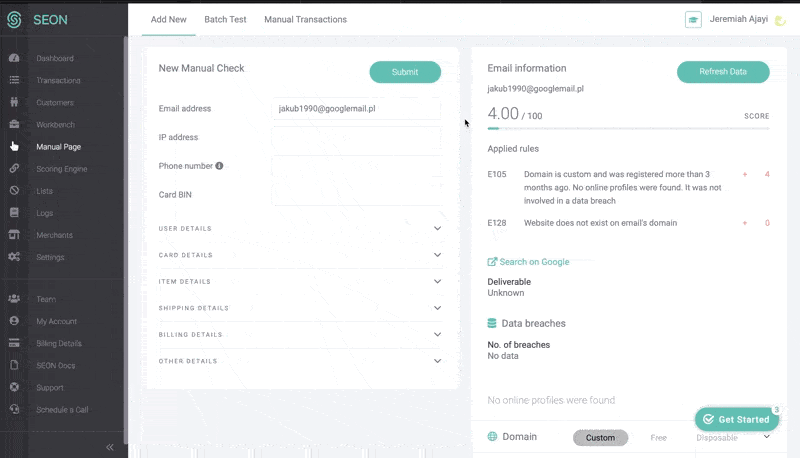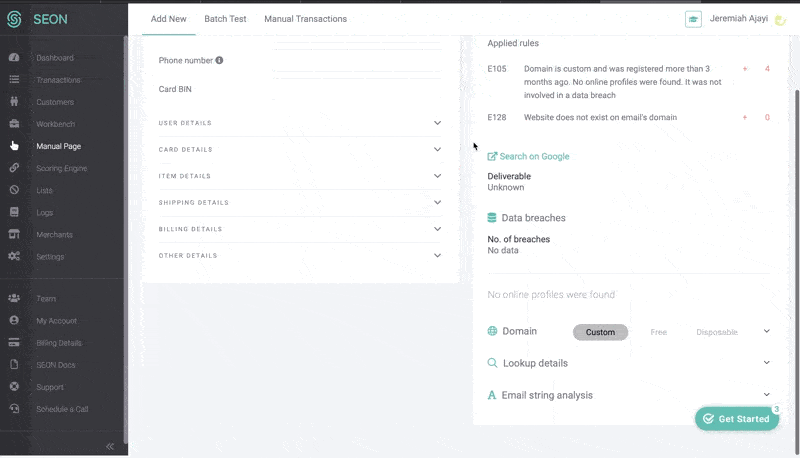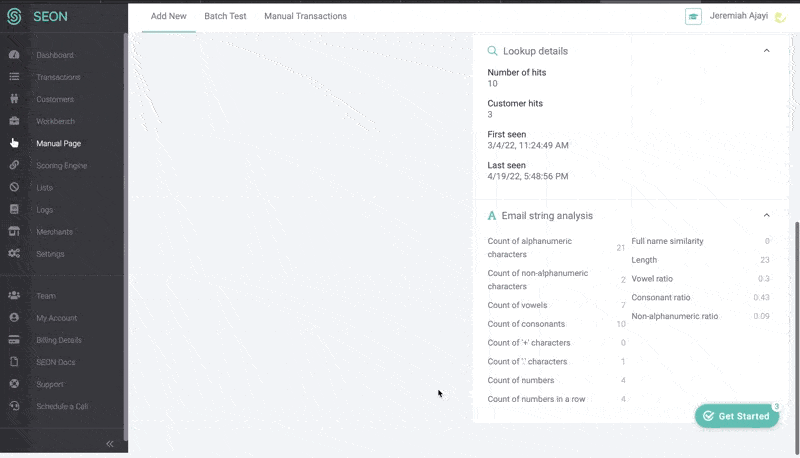
This amps up the accuracy and efficiency in catching high risk customers – and from there the system will implement the steps defined by the merchant, which are set according to their needs and risk appetite.
For instance, doing so could take the form of automatically banning the IP of any users caught with a risk rating higher than 60, or letting through anyone with a risk score lower than 10. For the rest, we can implement the aforementioned strategy of dynamic friction.
Examples of RBA Using Risk Scores
Let’s now look at concrete examples of risk-based authentication. In this scenario, a new user is purchasing an item from an online store. There are two key data points the system uses to calculate the score: IP address and email address.
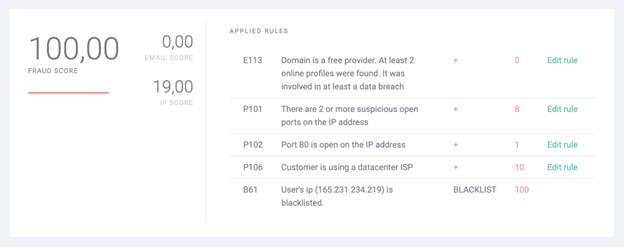
The high fraud score above lets us know we’re dealing with a risky user. We have enough red flags to block the transaction, even before we start analyzing the card data – for instance with a BIN lookup. Clearly, their purchase should not go through.
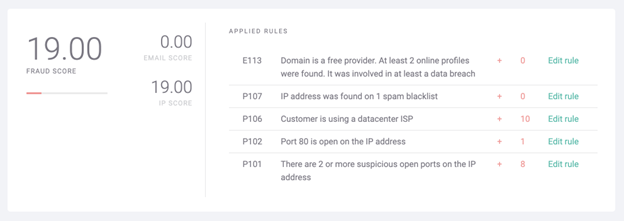
The low to medium fraud score above should arouse suspicions. It’s not a definite case of fraud but it would be a good reason to alert the manual verification team. You could also trigger an additional verification step, for instance by asking for a CVV number at the final checkout stage or requiring a one-time password (OTP).
You can read more about how fraud scores are calculated here.
How SEON Does Risk-Based Authentication and Dynamic Friction
At SEON, our key objective is to let you mitigate risk however it makes sense for your business. We empower fraud analysts, risk managers, and manual review teams to get as much information as possible about users.
This is done via data enrichment techniques such as:
- Reverse social media lookup: SEON is the only risk-based authentication tool to check 90+ social and online signals for proof of an online footprint.
- Phone and email analysis: Based on our internal reports, 80% of fraudsters use throwaway emails and phone numbers that aren’t linked to any other services. This can be spotted using reverse email and phone lookup tools.
- Device fingerprinting: We offer one of the most powerful device detection systems, looking at hundreds of parameters to spot emulators, VPNs, proxies, and Tor usage, among others.
Moreover, our machine-learning system will even suggest better rules for authentication, which you can test in a sandbox environment with historical data.
All of the above is available via seamless integration and a true SaaS model with a 30-day trial and a cancel-anytime contract.
Risk based authentication is a powerful tool and should form the backbone of your transaction monitoring. This is crucial for your AML fraud detection efforts, no matter if you’re a bank, fintech or other mandated business.
Find Out How
FAQ
Risk-based authentication, or RBA, works by scoring user data points in order to measure how risky their actions are. Different parameters such as IP address, the device used, and more are broken down into parameters, which are fed through risk rules. The rules help calculate a score to let you know if the action is risky or not.
With risk-based authentication, you can automatically approve or block a user action based on how risky it is. For instance, you can stop a transaction from someone with a high risk score, who may be a fraudster.
You can also remove obstacles such as 2FA or OTP for users who appear legitimate. Medium risk users can be asked for more information, or have their details manually reviewed by an agent.
Risk-based authentication allows companies to reduce the costs of fraud and risk management, so they can allocate more resources to manual review. It can also help protect user accounts from account takeovers. Ultimately, it helps reduce fraud rates, which has positive benefits for business growth, compliance, and user trust.
Sources
- Intellicheck: 5 Account Takeover Statistics
- Kaspersky: Kaspersky research shows sharp increase of account takeover incidents in 2020