IP address analysis is one of the oldest and most common methods used to detect fraudsters.
Check your IP fraud score here:
If looking up a phone number, please include its country code without plus signs, spaces or hyphens. By trying this tool, you’re agreeing to our Privacy Policy, General Terms of Service and Data Processing Agreement.
If you’re reading the words on this page, it’s thanks in part to an IP address. But unlike your home address, you probably have no reason to know it by heart.
And yet, this strange jumble of letters and numbers is, in fact, the key to automatic connection between any device and the Internet. This is true whether you visit a website, send or receive emails, use a chat room, and whether it’s from your phone, laptop or smart fridge.
What Is an IP Fraud Score?
An IP risk score can be used to help minimize the risk of bad actors entering your site. You can look at various settings and assign them points depending on a risk factor.
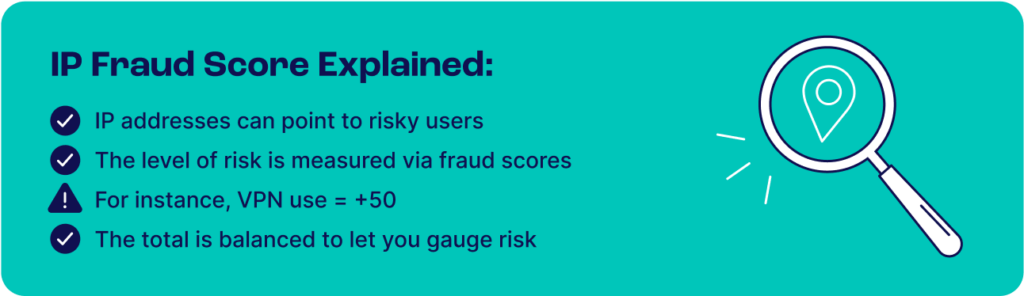
For instance, a VPN adds +1, an emulator adds +2, and so on. When all the points are calculated, you get an overall IP fraud score. IP reputation is another factor that impacts this score—IP addresses historically linked to bots or fraudsters will receive a higher risk score or may even be automatically blacklisted by your provider. Organizations typically use this solution at key stages like registration, login, or checkout to prevent malicious behavior such as account takeovers.
While an IP fraud score is a type of fraud score, the two shouldn’t be confused. The IP fraud score focuses specifically on internet protocol-related risk, whereas a general fraud score evaluates a broader set of user behaviors, including transactions and purchasing patterns. Watch the video below for a clear explanation of “What is a Fraud Score.”
How do IP Fraud Scores Work?
Once the points are added up, an automated system can decide whether the total score indicates a potential risk.
Here’s a simple example of how IP fraud scoring works:
- The IP address is from Russia. A rule says Russian IPs add +2 to the risk score.
- The ISP is residential. Another rule subtracts -1 from the score.
- A scan detects a suspicious SSH connection. This adds +5 to the score.
The total IP fraud score is 6 (2 – 1 + 5 = 6). Based on your system’s thresholds, this score might mark the user as high, medium, or low risk.
The main goal is to collect as much relevant data as possible to make the score more accurate and predict fraud more effectively.
What IP Data Is Important for an IP Fraud Score?
For IP fraud scoring to work, you need a system that can identify various IP parameters. Let’s break down some of the key types of IPs you should recognize.
Public vs. Private IP Addresses
If you think of an IP address as a physical postbox, a public IP lets you receive mail at your local sorting office. But the mail still needs to be sent to the right people in the city via Private addresses.
One point that often leads to confusion is that the term “private” doesn’t mean hidden. It simply refers to the fact that it links to a local network. It is indeed possible for anyone to find it.
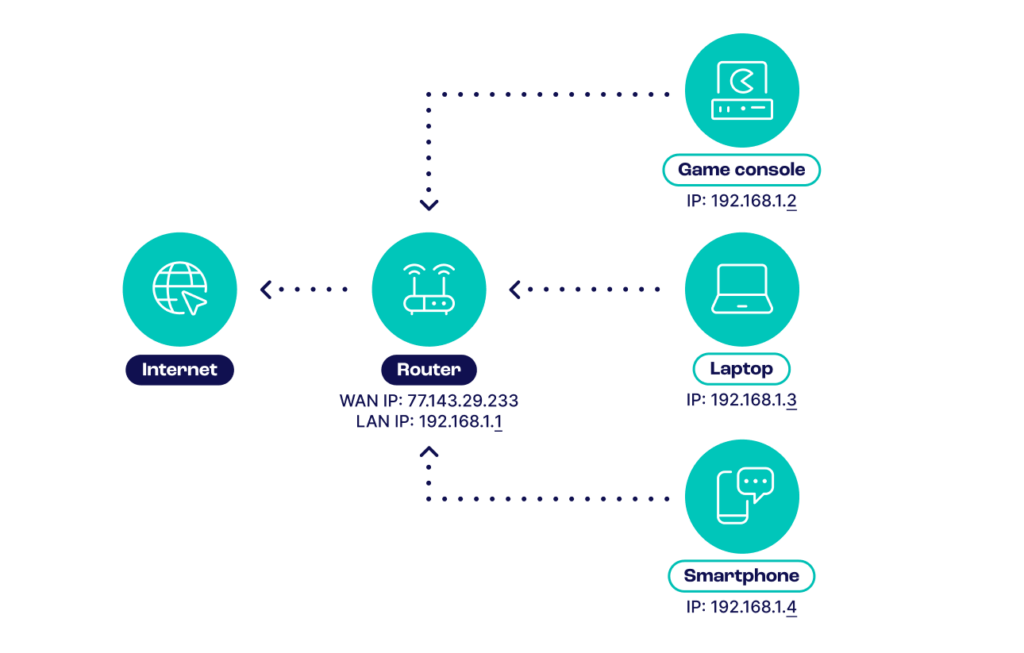
A public IP address is assigned to any device connecting to the Internet by an ISP (Internet Service Provider). It can be a phone or laptop, but also a web server or email server. It is impossible for a device to access a WAN (wide area network) like the Internet without one.
A private address is assigned to a device on a local network (LAN). Multiple devices can communicate with each other, usually within the same building.
IP Addresses and Geolocation
Many users first realize that their IP addresses contain useful information after their first encounters with the concept of geolocation. This usually happens because of:
- Targeted ads: Digital marketers try to catch your attention by mentioning your local area in their adverts.
- Blocked content: Most commonly found on media streaming platforms, where copyrights aren’t universal.
However, IP geolocation is a complex process that is outsourced to specialists. The accuracy of the geolocation varies depending on which database they use. A famous database, P2Country, yields 95% accuracy. IP2Region (which can be as granular as city and area code), decreases to around 50 – 75% accuracy.
Public IP Address Features
For our purpose, which is to detect fraudsters, public addresses offer a lot more information than private ones. Here are important features that are helpful in IP fraud scoring:
- Public IP addresses are generated automatically: They are assigned by your ISP (Internet Service Provider), and you cannot control them. However, you may have the option to use a static address (which always remains the same), versus a dynamic public address, which is randomly selected with every new connection.
- Public IP addresses must be unique: There can never be two exact same public addresses.
- Every device needs an IP address to connect to the Internet: That includes your phone, tablet, PC, laptop, watch, or even smart fridge if it’s part of the IoT (the Internet of Things).
Note that the most valuable IP addresses for fraudsters are residential IP addresses, which can be sold or rented on specific marketplaces and via brokerage services.
Proxy Servers and SOCKS5
Finally, it’s important to understand the tools used to change or hide IP addresses. These include:
- HTTP proxies, which only reroute browser traffic
- SOCKS proxies, often used for other apps like games or streaming services
- Transparent proxies, typically set up by employers, parents, or organizations to monitor or restrict internet use
Proxy servers are quick, cheap, and easy to set up, which is why fraudsters use them to switch IP addresses during repeated attacks. This technique—known as IP spoofing—can be done in seconds using free tools like xroxy.com.
Fraudsters especially prefer SOCKS5 proxies, which are harder to get but help them appear as legitimate residential users.
And that brings us to the key function of IP lookup tools: detecting when an IP address has been tampered with.
How Users Hide Their IP Addresses
There are many reasons why someone would want to avoid spoofing detection. Circling back to our examples above, it could simply be to watch a video from a foreign country. It could be to improve their security via added encryption. And of course, it could be for malicious purposes.

Regardless of the why, let’s see how IP addresses are hidden:
- VPNs: Short for Virtual Private Networks. Increasingly popular tools, which tunnel all traffic from a device towards a server in another location. Different VPNs offer different kinds of IP addresses, such as static, dynamic, or shared.
- TOR: a system designed to maintain a user’s anonymity by masking IP addresses. Users download and run a free browser, which passes and encrypts traffic multiple times to hide the original IP address. However, an ISP or fraud detection tool will know if the user connected to TOR’s entry and exit nodes.
- Proxy servers: act as a middle man between a device and a visited website. TOR and VPNs are also considered proxies, even if they redirect all traffic coming from all software and device systems.
Proxies help fraudsters hide their IP addresses and stay anonymous. See how bad agents use them, and how our API flags them
Find out more
The Key Features of IP Analytics
Now that we understand how IPs work and a basic strategy of how people hide their addresses, let’s see what we can gather by analyzing them.
- Geolocation: As we’ve previously seen, a legitimate IP address should reveal where the user is based in the world. It is a basic feature, but still useful to see if it matches the card country or if the customer is travelling too fast.
- Internet Service Provider: Finding out who the ISP is can help us know if the IP is residential, from a normal residential connection, public library or web server/data center. The latter is particularly useful to know as they are often used by bots, VPN providers and TOR exit nodes.
- Open port scan: All proxies tend to have at least one open port, and so do computers functioning as servers. By performing a scan, we can measure how risky the situation appears to be. For instance, some proxy providers resell hacked SSH connections, where port 22 is usually open. A proxy detection service or proxy detection API can help.
- Spam checklist scan: There are two useful lists called DNSBL (Domain Name System Blackhole List) and RBL (Real-time Blackhole List), which catalogue IP addresses used for email spamming. If these IP addresses appear in the results of our search, we can suspect the user is fraudulent.
So with these few features, we can already tell a lot about a user based on their IP address. Where they are based, what kind of network setup they use to connect online, and whether they appear suspicious or not.
Velocity Rules for IP Usage
So what should you do if you find a suspicious user’s IP address connecting to your system? You could simply block it straight away, but adding that address to an IP blacklist doesn’t make sense. This is because IP addresses are mostly dynamic, and multiple users could eventually end up sharing them, so you’d end up blocking valid customers.
This is why you can’t just look at the IP address itself, but also their usage via velocity rules. These algorithms look at the patterns and changes of IP address usage over time, which helps anti-fraud intelligence.
Enhancing IP Score Checks with APIs
As we’ve seen, understanding IP addresses and getting a report is fast, affordable, and easy to perform. But it’s in no way flawless. While it can indicate suspicious behavior, it cannot point to fraud with 100% certainty.
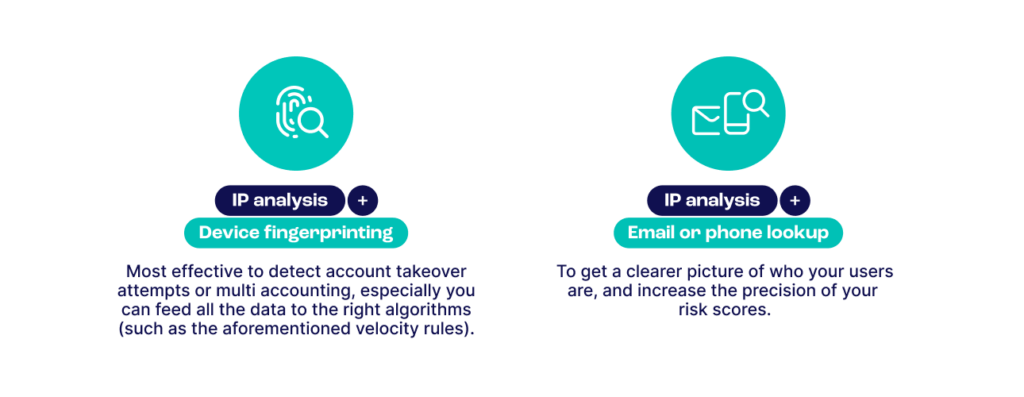
This is, in fact, one of the shortcomings of the tech: it’s only useful as part of a complete fraud detection tool. When you search for risk, you need as much data as possible. And here, you’ll need:
The Benefits of IP Analysis Against Fraud
As we’ve seen, IP addresses contain a multitude of valuable parameters that help us calculate risk. It’s not the only reason to rely on IP analysis against fraud. Here is why you should deploy that type of tool today:
- Lightweight checks: IP analysis is invisible to the end user. All the checks happen behind the scenes, without slowing down the user journey.
- Real-time results: checking most IP parameters is nearly instantaneous, which also helps create a frictionless experience without sacrificing safety.
- Affordable: IP analysis is one of the most cost-effective ways to filter out bad agents.
As for the types of fraud you can detect with IP analyis, they include bot traffic, bonus abuse, multi-accounting, payment fraud, and more.
Prevent IP Fraud Risk with SEON
Breaking down the features of IP addresses for risk scoring is fast, affordable, and delivers results in real time. This is exactly what SEON’s IP lookup module offers in an affordable, easy-to-use package.

However, IP data is only one piece of the puzzle. For a complete solution against all kinds of fraud, from bot attacks to bonus abuse and chargeback fraud, we recommend combining IP fraud scoring with reverse email lookup, user and device fingerprinting, and more.
To learn more about how SEON can protect your online business, ask an expert by clicking the link below.
SEON is a powerful end-to-end solution that gives you complete control over the rules that affect your users’ fraud scores, with granular reporting.
Ask an Expert
Frequently Asked Questions
There are two types of IP scores. One of them is called an IP reputation score. Service providers use it to determine if your emails should pass spam filters. In fraud prevention, your IP risk score can determine if a system labels you as fraudulent or not,
Any improper use of the IP address of a server is considered IP abuse. This includes spamming, phishing attempts, DDoS or malware attacks.
An IP score rating helps businesses determine whether an IP address is risky or not. While there is no standard for how the scores are calculated, a higher score tends to point towards a risky IP.
IP analysis can be performed manually by taking certain parameters, such as an IP address, and checking it against public databases. However, most businesses automate the process using IP lookup and IP risk-scoring tools