KYC verification is notorious for being time-consuming, costly and frustrating for customers — yet it remains surprisingly easy for fraudsters to bypass. This friction in the onboarding process often leads to higher churn rates and demands significant resources to manage effectively.
For banks, the average annual cost of Know Your Customer (KYC) checks is estimated at $60 million, driven by the need for comprehensive verification, continuous monitoring, and adherence to regulatory compliance. The process itself includes three key components: Customer Identification Program (CIP), Customer Due Diligence (CDD) and ongoing monitoring.
What Is KYC Verification?
KYC verification is the process of confirming a customer’s identity to ensure they are who they claim to be. It is a key part of Know Your Customer (KYC) regulations, helping businesses comply with legal requirements and prevent fraud.
By verifying personally identifiable information (PII) against official documents like passports or driver’s licenses, KYC verification helps businesses prevent fraud, money laundering, and other financial crimes. Many organizations also use biometric checks or database cross-references to enhance security during customer onboarding.
How Does KYC Verification Work?

To complete KYC verification, businesses must follow these key steps:
- Collect customer details – Request essential information like name, address, and date of birth.
- Obtain official ID documents – Ask for government-issued identification (e.g., passport, driver’s license).
- Cross-check information – Compare the provided details with the ID documents to ensure they match.
Cross-Checking Methods
The verification process can vary depending on automation levels:
- Automated checks – Some organizations use identity verification (IDV) software to scan and extract details from ID documents.
- Manual review – Others prefer human oversight, where documents are checked visually for inconsistencies.
- Hybrid approach – Combining software detection and human verification improves accuracy and helps spot tampered documents.
KYC verification is complete when the organization confirms the applicant’s eligibility and approves them for onboarding.
SEON uses email, phone, and IP data from onboarding to build a digital footprint, detecting fraudsters before KYC.
Ask an Expert
Why Is KYC Verification Important?
The KYC process is essential for businesses to maintain compliance and prevent fraud. In 2024 alone, over $3.2 billion in KYC and AML fines were issued in the banking sector, highlighting the high cost of non-compliance. Here are the key benefits of KYC verification:
- Avoid heavy fines – Non-compliance can lead to massive penalties and legal troubles.
- Reduce fraud – Verifying users helps block fraudsters and protects your platform.
- Protect consumers – Preventing criminals from accessing your services reduces identity theft and scams.
- Maintain business reputation – Compliance prevents PR disasters and builds trust with customers and regulators.
By using KYC software and authentication checks, businesses make it harder for criminals to operate, discouraging fraudulent activity before it even starts.
3 Components for a Successful KYC Verification
A successful KYC verification process involves three key steps: a customer identification program (CIP), customer due diligence and ongoing monitoring.
1. Customer Identification Program (CIP)
The CIP requirement stems from the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) Act of 2001. The Act’s goal is to deter and punish terrorist acts in the US and globally, including by strengthening anti-money laundering measures.
For financial institutions, this means verifying the identity of account holders. An individual can open an account with basic details (name, date of birth, address, and identification number). The financial institution must then verify those details, for example by checking the individual’s identity documents and/or looking them up on public databases, consumer reporting agencies, and similar.
2. Customer Due Diligence
The next step of the KYC verification process concerns assessing the customer’s trustworthiness. At the simplified due diligence end of the scale, it may be sufficient to verify the customer’s identity and location. Enhanced due diligence takes this further, including checking blacklists, watchlists and lists of politically exposed persons (PEPs).
Customer due diligence can also delve into an individual’s occupation, the types of transactions they make, their expected activity patterns, and more. The goal is for the financial institution to understand the particular risks associated with that individual while keeping detailed records of the checks undertaken.
3. Ongoing Monitoring
A successful KYC verification process is not a one-time activity. Monitoring must continue throughout a customer’s time with the financial institution in question. Ongoing monitoring flags changes in activity patterns: these could include unusual cross-border payments, higher-value transactions, changing payment methods, a higher volume of transactions and/or the addition of the account holder to a sanction list. The financial institution may need to file a Suspicious Activity Report if an account holder’s behavior changes sufficiently to warrant this.
Best Features for KYC Verification Processes
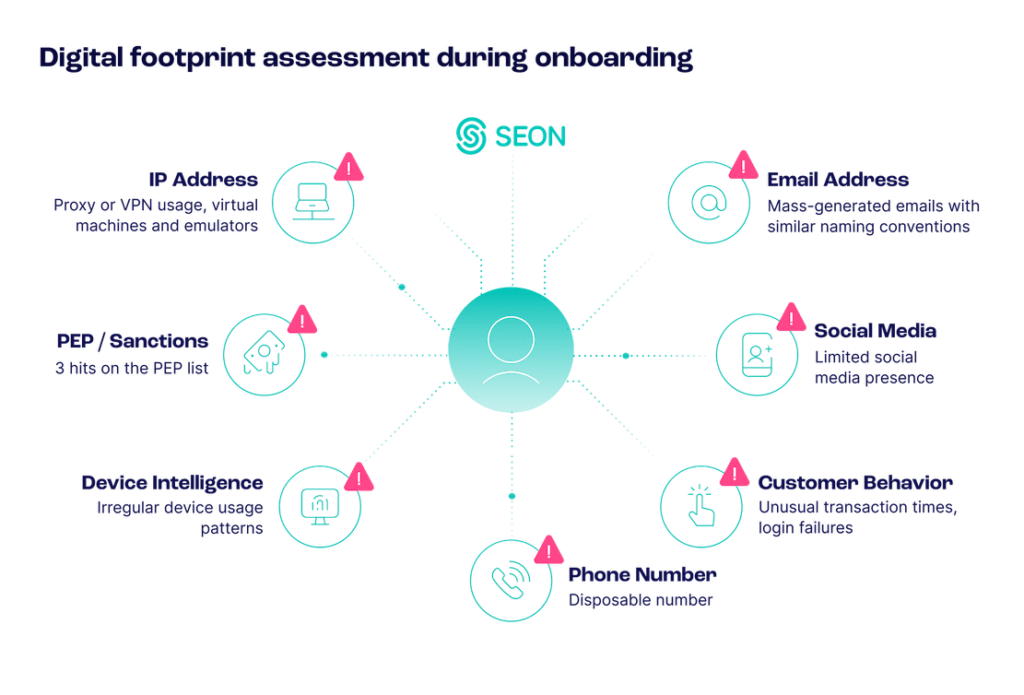
Digital Footprint Analysis
Digital footprint analysis starts with gathering key data points, such as email address, IP address and phone number. SEON then uses this data to build a detailed profile, drawing from over 200 signals from social media and online sources to assess whether a user behaves like a legitimate customer.
This analysis reveals valuable insights, such as a user’s number of online profiles and whether they’ve been involved in data breaches. A genuine user typically has five to six online profiles, while fraudsters often have minimal online presence, making them easier to flag for further scrutiny or outright blocking.
By analyzing these digital footprints, businesses can identify fraudsters early in the onboarding process, improving fraud prevention while ensuring a smooth customer experience.
Device Intelligence
Device intelligence goes beyond basic device identification by analyzing key data points across both desktop and mobile devices. It examines user behaviors, hardware and software configurations and real-time interactions to detect fraud patterns. With device intelligence, you can monitor:
- Whether a user has connected previously under a different username
- If the user’s actual location matches their stated one
- Suspicious device setups that may indicate spoofing attempts
- Use of common fraudster tools like Tor or mobile proxies
By leveraging thousands of real-time data points, such as device hashes, geolocation, network configurations and user preferences, device intelligence provides proactive fraud detection, ensuring secure online transactions and interactions.
How to Save on KYC Costs with Pre-KYC Checks
KYC checks can be expensive, with identity verification vendors charging anywhere from $13 to $130 per customer. These costs can quickly add up.
These costs can be significantly reduced by stopping fraudsters before they reach KYC verification. SEON’s solution, for instance, is implemented at signup and it acts as a traffic light system that filters out bad users early, ensuring that only legitimate customers make it to KYC.
In addition to saving on KYC costs, this proactive approach helps reduce fraud across your platform, making it much harder for fraudsters and money launderers to gain access to your products.
Learn how BNPL leader Mokka used SEON to reduce fraud by 65% and cut KYC costs by 6%.
Learn More
How SEON Can Augment Your KYC Verification
KYC risk assessment requirements are standard across your industry, but implementing them efficiently is key. SEON optimizes your KYC process, providing you with a competitive edge while ensuring a seamless experience for legitimate customers. Here’s how SEON can transform your KYC verification:
- Reduces KYC costs
- Operates seamlessly in the background
- Filters out and automatically flags fraudulent users
- Gathers valuable user insights
- Works even with limited data
- Detects stolen, fake and synthetic IDs
- Verifies users without 3DS/SCA reliance
- Identifies suspicious user connections
- Speeds up the digital onboarding process while maintaining a smooth journey for good users
This also lays the foundation for expanding financial services capabilities. For example, loan providers seeking to implement alternative credit scoring through digital ID profiling no longer need to rely on traditional financial data. Instead, they can leverage digital footprint analysis to build their scoring models, bypassing the need for information from banks and financial institutions.
SEON enables you to onboard legitimate users quickly, applying minimal KYC checks while blocking fraudsters and requesting additional documentation only from suspicious users. Our solutions have empowered leading digital banks and fintechs to scale efficiently, serving more customers without compromising safety or compliance. By filtering out bad users pre-KYC, triggering exceptions for 3DS checks, reducing transaction fraud and minimizing defaults, SEON provides a secure, seamless experience from start to finish.
SEON’s flexible solution integrates with KYC, saving time, cutting costs, and enhancing security.
Ask an Expert
More About KYC Risk Checks Based on Industry
- SEON: KYC in Cryto
- SEON: KYC in Online Lending
- SEON: KYC in Banking
- SEON: KYC in iGaming
- SEON: KYC in Forex
Frequently Asked Questions
A KYC journey can vary depending on the context but typically will consist of ID card verification, video verification, document verification, and biometric verification.
The answer should be a resounding no – not if they are going to be rejected! If you can filter out junk users, bad leads, and obvious fraudsters, you’re saving on costs and resources before the checks even begin. So even if your company is mandated by law to conduct KYC on everyone, you can avoid doing so when it’s an obvious fraudster, by applying simple pre-KYC profiling to block them before they reach KYC.
The easiest way to understand the difference between KYC and AML is by thinking about the goals of each:
KYC is introduced at onboarding, when a new customer is about to sign up, and it has to do with verifying who this person is. On a practical level, this could involve document verification checks or biometrics.
AML are measures taken continuously by a financial or related organization to prevent money laundering. They have to do with securing that the funds brought in by the customer have a known, legitimate source. AML involves actions such as flagging unusual transactions and/or those over a certain amount, and filing suspicious activity reports with the authorities.
Sources
- Accenture: Banking Consumer Study: Making digital more human
- World Bank: The Global Findex Database
- Merchant Machine: The Countries Most Reliant on Cash In 2021
- CNBC: 25% of US households are either unbanked or underbanked
You might also be interested in reading about:
Learn more about:
Browser Fingerprinting | Device Fingerprinting | Fraud Detection API | Fraud Detection with Machine Learning & AI