What Is Triangulation Fraud?
Triangulation fraud involves a legitimate buyer, an unsuspecting seller and a fraudster who intercepts the transaction, damaging both parties.
The fraudster poses as a seller offering a great deal and leads the buyer to a fake storefront. After the customer pays for the product, the fraudster uses a previously stolen credit card to fulfill the order from a legitimate merchant and then ships the product to the customer. While the buyer receives the product, the real cardholder might see the unauthorized transaction and issue a chargeback.
The online merchant takes the brunt of the attack — they lose both the money and the product, doubling their losses.
Having a credit card fraud detection system in place is essential for survival in today’s ecommerce landscape.
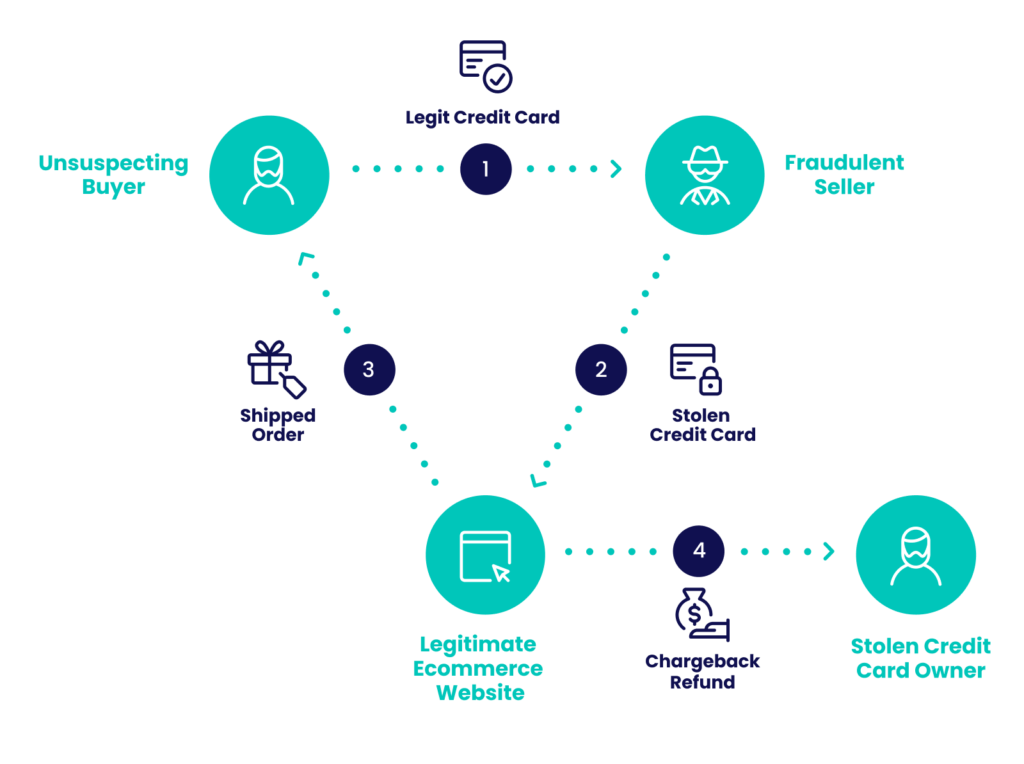
How Does Modern Triangulation Fraud Look Like?
Triangulation fraud is a form of card-not-present (CNP) fraud that can involve up to five affected parties depending on the circumstances of the transaction.
- The fraudster posing as a real ecommerce storefront or a reputable seller profile.
- The unsuspecting buyer taking advantage of the unrealistically good price.
- A legitimate seller with an online storefront — usually large enough to have a fully automated checkout and delivery infrastructure.
- A person whose credit card information was stolen previously.
- And if applicable, a marketplace such as Amazon, eBay or Shopify.
Learn how card not present fraud can affect your business, how chargebacks affect you, and how to tackle it all.
Protect Yourself
How Does Triangulation Fraud Work in Ecommerce?
The scam starts with a fake online store identical to a legitimate seller website, or one that posts items on marketplaces like eBay, Amazon and Shopify (or even social media sites) using a fake seller profile.
Then, the fraudster lays in wait — probably not very long — for a digital customer looking for the best deal on that product. When they stumble upon the product at a price point that seems too good to be true, the following ensues:
- The customer pays the fraudster posing as a reseller for the product.
- The fraudster pockets the money from the customer.
- The fraudster places the customer’s order with the actual, original retailer, using stolen credit card details.
- The retailer fills the order, charging the stolen credit card and delivering to the original customer.
- The customer receives their order, unaware they were an unwitting money mule.
- The real cardholder discovers the fraudulent charge on their card and files a chargeback with their card issuer.
- The retailer has to refund the money but has no recourse to reclaim their product.
How Dangerous Is Triangulation Fraud?
Triangulation fraud not only affects the retailers who lose out on both the goods and the money but also undermines the trust in online transactions. As the prevalence of stolen credit card information grows, this type of fraud becomes more widespread, especially on platforms with high transaction volumes like eBay, Amazon and smaller marketplaces.
Fraudsters who decide to execute this kind of scam will often think of it as a victimless crime — the credit card holder gets their money back, and a major company has been defrauded of an amount of money that it won’t mind losing.
The victims of credit card theft are often elderly, not tech-savvy people who often don’t understand the situation or know of any recourse to combat it — for instance, the chargeback option they have.
Triangulation Fraud Red Flags
Triangulation fraud can be hard to spot, particularly without specialized security software in place. When a triangulation scheme is set up, every actor present in the scam may initially appear legitimate. There will be a real customer, a real credit card and a real order of real products. However, there are always telltale signs.
For online retailers:
- Conflicting shipping and billing addresses.
- Multiple accounts named in a similar pattern or with similar passwords.
- Falsified contact details (e.g. email address or phone number).
For marketplaces:
- Brand new seller account with no reviews or ratings.
- The seller recently deleted their account and registered a new one with the same email address.
- Multiple adverts for one item or brand.
- Unusually low prices for valuable items.
- The seller cannot be contacted or uses a fake email address or phone number.
How To Stop Triangulation Fraud
As with any kind of digital fraud, knowing as much about your customer as possible is essential, but having good security in place with minimal friction and false positives is a delicate balance.
Deploying a suitable fraud prevention solution will first allow businesses to gather information on fraudsters using:
- Digital footprint analysis: Businesses can analyze users’ online presence and the validity of their email and IP addresses to detect fraud. While criminals may have stolen credit card details, they often struggle to replicate the realistic digital profiles typical of genuine shoppers.
- Device intelligence: By examining how users connect to a website, taking into consideration things like the presence of a VPN or an unusual hardware setup, companies can identify common fraudster patterns and defend themselves.
- Velocity and behavior checks: By identifying recurring patterns in user behavior examining their actions throughout a give timeframe, businesses can spot multi-accounting attempts and catch criminals who are running several such fraud schemes simultaneously.
With a security suite that has the correct tools, businesses should be able to spot and stop fraudsters attempting triangulation fraud.
From there, depending on the results, a dedicated fraud team can review the gathered data to determine if a customer is legitimate and manually sign off on them, with only a modicum of added friction.It can also help to enable fraud prevention machine learning tools that suggest new, bespoke risk rules based on the needs of individual companies and streamline the approval process.