Credit card fraud is increasingly prevalent, with projections from the Nilson Report estimating losses could soar to an astonishing $38.5 billion by 2027. As the issue becomes increasingly pervasive, understanding how to detect credit card fraud and the reasons behind its prevalence is essential for consumers and businesses alike.
In this article, we will explore the mechanisms of credit card fraud detection and the various techniques employed to safeguard transactions.
What Is Credit Card Fraud Detection?
Credit card fraud detection encompasses a range of strategies and technologies aimed at preventing unauthorized purchases, whether online or in physical stores. The primary goal is to verify the cardholder’s identity and ensure the legitimacy of each transaction.
Various techniques are employed to authenticate cardholders, including multi-factor authentication (MFA), 3D Secure (3DS), biometric verification, and one-time passwords (OTP). These methods enhance security by requiring multiple forms of verification before approving a transaction. In addition to authentication, detecting credit card fraud often involves analyzing transaction anomalies. For instance, if a transaction originates from an IP address linked to a suspicious location or if a device displays an unusual configuration, these factors may trigger alerts.

Depending on the detection systems in place, businesses can assess cardholders’ identities and intent either in real time or retrospectively. This dual approach allows for proactive payment fraud prevention as well as thorough investigations of past activities.
How Does Credit Card Fraud Detection Work?
Credit card fraud detection uses advanced technologies, algorithms and data analysis to identify and prevent fraudulent transactions. Financial institutions utilize real-time machine learning models that recognize patterns and anomalies, such as sudden large purchases abroad or multiple transactions in a short period. These systems assess risk based on transaction history, location and user behavior, often halting suspicious transactions and contacting cardholders for verification.
In addition to machine learning, rule-based systems apply predefined criteria to flag potential fraud, ranging from simple conditions like exceeding spending limits to more complex correlations among various data points. To enhance security, financial institutions employ real-time monitoring and behavioral analytics to track cardholder activities continuously. Techniques such as biometric verification, tokenization, and multi-factor authentication further bolster defenses against fraud. By integrating these technologies, credit card companies can effectively detect and prevent fraudulent activities, protecting both cardholders and financial institutions.
With the fraud management industry set to reach USD 38.2 billion by 2025, explore our top fraud detection tools to protect your transactions effectively.
Read More
How Do Fraudsters Get Credit Card Numbers?
Acquiring credit card numbers online is surprisingly easy and inexpensive, with dedicated marketplaces on both the clearnet and darknet. Reports indicate that prices can be as low as $17 per card.
Here are some common methods through which these numbers become available:
- Theft: Criminals physically steal credit cards or gain access to them.
- Skimming and cloning: Fraudsters use devices known as skimmers to capture credit card details from legitimate card readers, allowing them to create unauthorized copies.
- Account takeover: A fraudster gains unauthorized access to a victim’s account linked to a credit card. The situation is often exacerbated if the account functions as an e-wallet (e.g., BNPL or cryptocurrency accounts).
- Phishing and social engineering: Scammers exploit human psychology to extract sensitive information through deceptive emails, SMS or fake online stores.
- Infiltrating legitimate online stores: Criminals inject malicious scripts into existing ecommerce websites, a technique known as online skimming, often utilizing sophisticated tools like MageCart.
How to Detect Credit Card Fraud
Detecting credit card fraud requires businesses to be vigilant in recognizing when card details may have been compromised. Various tools and techniques can help identify suspicious activities based on transaction behavior.

Card Security Features
Credit card networks have developed a number of security features designed to prevent fraudulent Credit card networks have implemented several security measures to prevent fraudulent purchases, including:
- Address Verification Service (AVS): This service verifies the cardholder’s identity by cross-referencing their registered address with the bank’s records.
- 3-D Secure (3DS): A security layer that prompts users to enter a code to complete a transaction, offered under different names by various card operators (e.g., Visa Secure, Mastercard SecureCode).
- CVV (Card Verification Value): A three-digit code on the card that confirms possession during a purchase.
While these features enhance security, they can also introduce friction into the purchasing process. For example, companies like Amazon may forgo CVV verification to streamline checkout and improve customer experience, relying instead on other security measures.
Risk Scoring
Risk scoring / fraud scoring is a common method for evaluating transaction risk. By applying heuristic rules, businesses can make informed decisions about whether to allow a payment. For instance, if an IP address differs from the shipping address, the risk score increases.
A velocity rule scores transaction behavior by looking at data points within a certain time frame. For instance, it might block an account after multiple failed password attempts within a short time frame.
Risk scoring systems can be either transparent (whitebox) or opaque (blackbox), depending on whether risk managers customize the rules or rely on preset algorithms. Organizations with dedicated resources may prefer whitebox systems for greater flexibility, while those with limited capabilities might opt for out-of-the-box solutions.
To learn more about risk rules and best practices, read our guide on card-not-present fraud prevention.
Digital Footprint Analysis
Confirming a user’s online identity without adding friction is crucial for preventing fraudulent transactions. Digital footprint analysis serves as an invisible security layer that gathers additional information from single data points, such as:
- Digital and social checks: Assessing whether contact information corresponds with registered social and digital accounts.
- IP analysis: Checking for connections from VPNs or suspicious proxies.
- BIN lookup: Verifying if the payment card type aligns with expected usage patterns.
- Device intelligence: Analyzing information about the devices used to access your platform and identifying, for instance, whether the user has previously accessed the site from the same device.
This approach allows businesses to build comprehensive user profiles without requesting extra information, feeding valuable data into risk-scoring systems to better assess potential fraud. Digital footprint analysis can also provide crucial evidence in disputes over chargebacks or instances of friendly fraud.
How SEON Does Credit Card Fraud Detection
SEON’s fraud detection software offers a comprehensive suite of features designed to enhance credit card fraud detection by providing critical insights into payments, cardholders and alternative data sources such as social and digital profiles and device information.
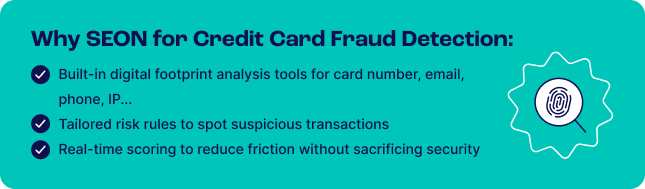
Key features include:
- Card BIN lookup: This feature verifies the card’s validity, identifies the issuing bank, and determines its country of origin, helping to assess the risk associated with a transaction.
- Digital footprint analysis: You can check the shopper’s online presence simply by entering their email address or phone number. A lack of digital footprint may warrant further investigation.
- IP analysis: SEON analyzes how customers connect to your checkout process, flagging harmful IP addresses, VPNs, Tor usage or suspicious DNS activities.
- Custom and industry-specific risk rules: SEON comes pre-loaded with default risk rules tailored for various sectors, such as online retail and BNPL services. In addition, custom rules help automate and finetune risk assessment so it fits each business’s specific needs.
- Integration flexibility: You can enhance your existing systems with additional data intelligence, connect via API for full automation or use plugins for platforms like Shopify.
SEON’s solutions aim to empower businesses to combat credit card fraud and minimize chargebacks without compromising security or customer experience during payment acceptance.
SEON’s customizable risk scoring, digital footprint analysis and machine learning capabilities help businesses reduce fraud by up to 99%.
Ask an Expert
FAQ
Fraud prevention software should be able to detect credit card fraud instantly. It will use a combination of risk rules to flag a transaction and prevent it before it happens. If you detect credit card fraud, you will need to initiate a chargeback request. The chargeback may take up to 120 days to be settled.
Theoretically, you can trace credit card fraud. In practice, however, it is very unlikely that the fraudster will be prosecuted – unless they are caught as part of a large-scale anti-fraud operation.
If your business processed a fraudulent credit card transaction, you are legally forced to repay the sum to the cardholder. You may also dispute the chargeback process, which may be a long and costly process.
Credit card fraud happens when a fraudster gets hold of someone else’s credit card details and makes a purchase with it. This is clear fraud, where the goal is to not pay for a good or service and still receive it.
Note that there is also another type of credit card fraud that happens when the cardholder is being dishonest. In that scenario, the payment looks legitimate, but the cardholder has already decided to return the item or ask for a refund.
Sources
- Juniper Research: Online Payment Fraud
- The Guardian: Stolen credit card details available for £1 each online
- Nilson Report: Card Fraud Losses Dip to $28.58 Billion
- Magecart: A Deep Dive Into Magecart