Historically, telecommunications companies have been slow to deploy risk operations departments. Losses were either absorbed or passed on to the repo business.
But telecom operators are increasingly inclined to meet their unique fraud challenges head-on.
Let’s examine them in detail here and see what kind of tools can help.
What Is Telecommunications Fraud?
Telecommunications fraud, also known as telco fraud or telecom fraud, includes any kind of activity designed to abuse and gain an advantage over telecommunications companies using deception (fraudulent practices).
This includes IRSF fraud (International Revenue Sharing Fraud), where fraudsters abuse premium phone rates, and interconnect bypass fraud, a form of arbitrage between operators’ call rates.
How Does Telecommunications Fraud Work?
Because telephony is the largest and oldest deployed network in the world, fraudsters have long developed tools and practices to exploit it to extract value. Revenues in 2023 are estimated at $498 billion – and it is still growing, at an expected rate of 2.08% year-on-year.
And while fraud attacks usually evolve quickly over time as companies squash them, telco fraud is unique as it’s often taken as a given. Its costs are absorbed by operators, who would rather not embark on integrating complex risk management systems into their architectures.
Adding to the challenge is the fact that telecom companies also break down their services to resell them to local networks and carriers – a £4/$5 billion industry in the UK alone.
As the technology to run your own mobile network becomes more widely available, large telecom operators are becoming targets of fraud indirectly, making it harder to identify.
Protect your business with SEON’s advanced real time fraud fighting tools to keep you and your customers secure
Ask an Expert
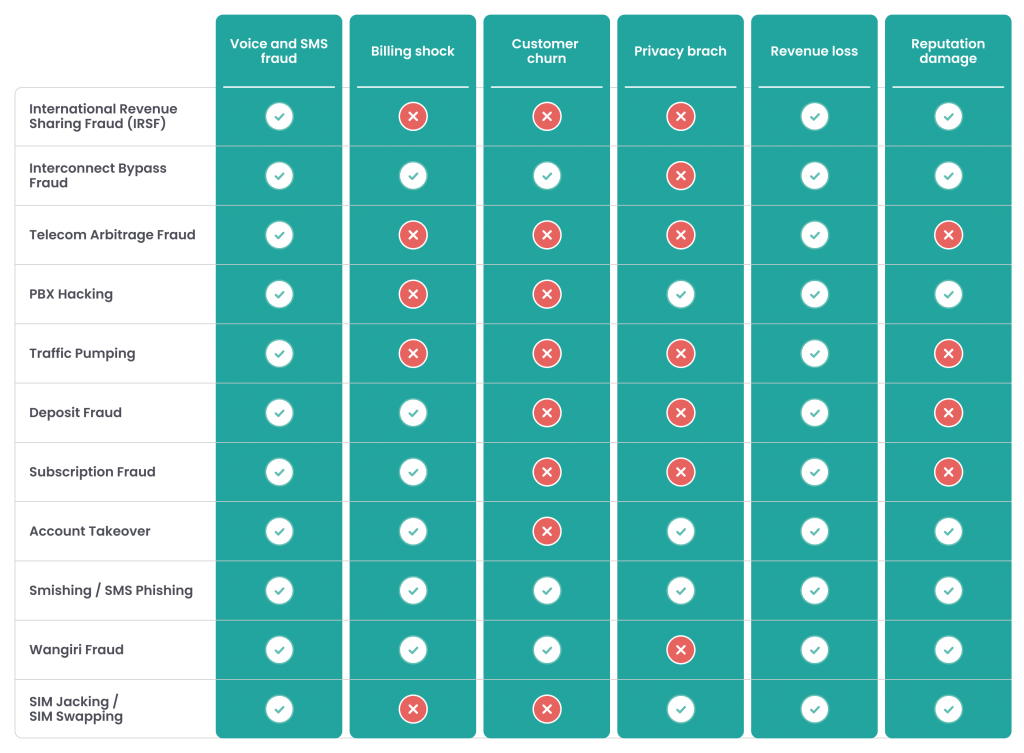
11 Types of Telecommunications Fraud
Let’s now look at the most common types of telco fraud attacks operators should know about.
1. International Revenue Sharing Fraud (IRSF)
International Revenue Sharing Fraud, or IRSF fraud, takes advantage of premium phone rates, which are then dialed unwittingly by users.
It is by far the biggest fraud challenge for telecom operators, costing the industry an estimated $4 to $7 billion a year according to Verdict. This is how it works:
- Bad agents sign up to lease a premium phone number.
- They break into a business’s phone systems and make calls to that number.
- The business pays as much as $1 a minute, 25% of which goes into the fraudster’s pockets.
Businesses may suddenly find themselves with astronomical phone bills for calls they do not recognize. The calls often happen outside of working hours and companies only realize they’ve been made when it’s time to foot the bill.
It doesn’t help that regulation is lacking in this area. Unlike with card payments, where the chargeback process can protect the person whose credit card was stolen, there is no such thing in the telephony world.
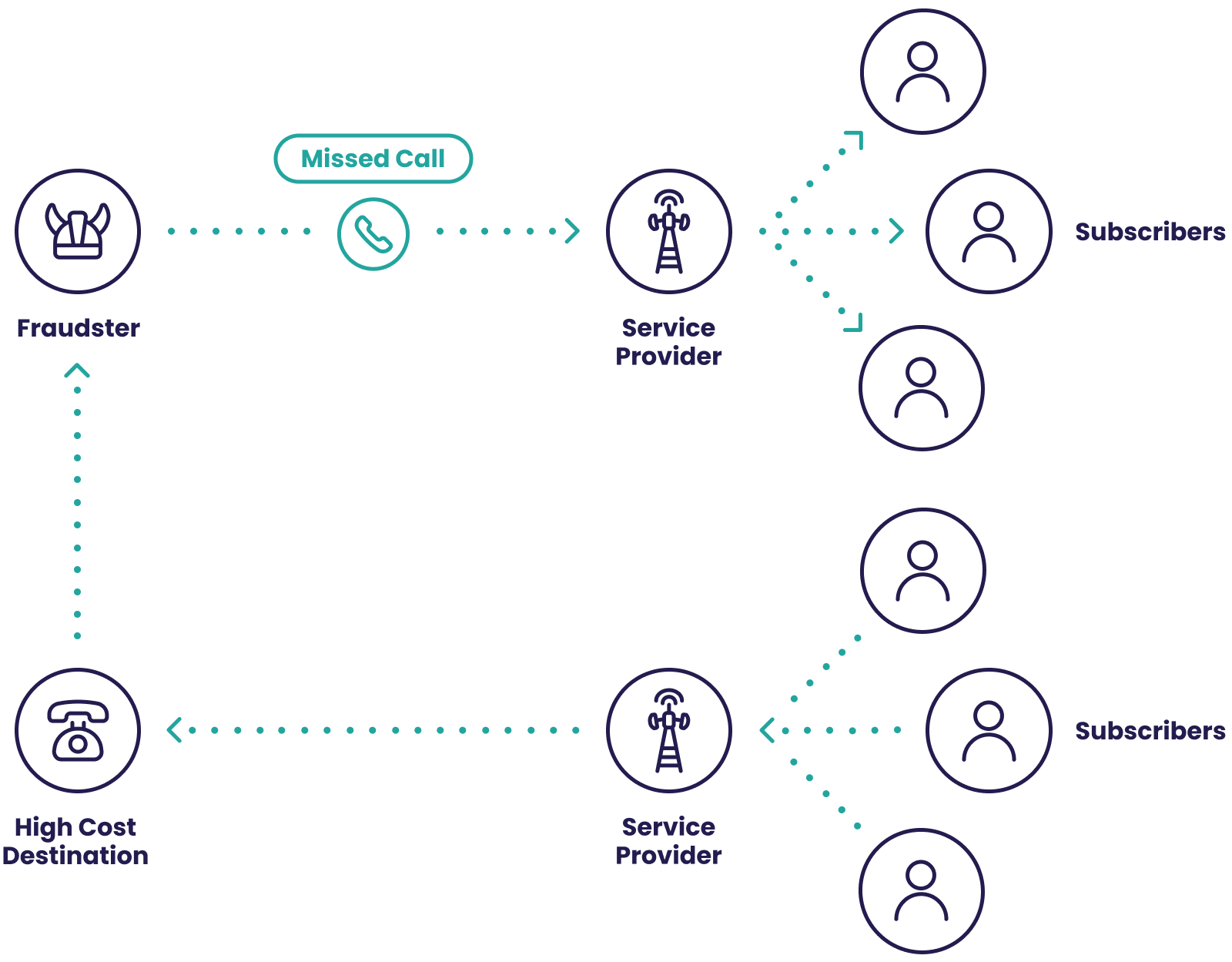
2. Wangiri Fraud
From the Japanese meaning “one and cut”, wangiri telecommunications fraud involves striking curiosity in customers by calling them, letting the phone ring once, and hanging up. The customer will often ring back, unwillingly calling an expensive premium number that the fraudsters control.According to the latest data that exists, wangiri scams cost the economy a significant $2.23 billion a year. This type of telecommuncations fraud sits at number two of the top fraud methods reported in 2021, while the CFCA survey has also noted a year-on-year increase.An SMS variant of this also exists, where fraudsters send a message prompting customers to call back a certain number, or even text it. The typical red flags for this kind of telecommunications fraud are spikes in traffic to high-cost destinations, which telcos should be able to monitor with their internal systemThe key here is to know that, as a business, you should keep an eye on which numbers are automatically dialed. This isn’t only for telcos, by the way: Any company where phone calls are an important part of finding leads or customer service could do well to deploy a simple reverse phone lookup tool to protect themselves whenever someone is asked to dial back an unknown number.
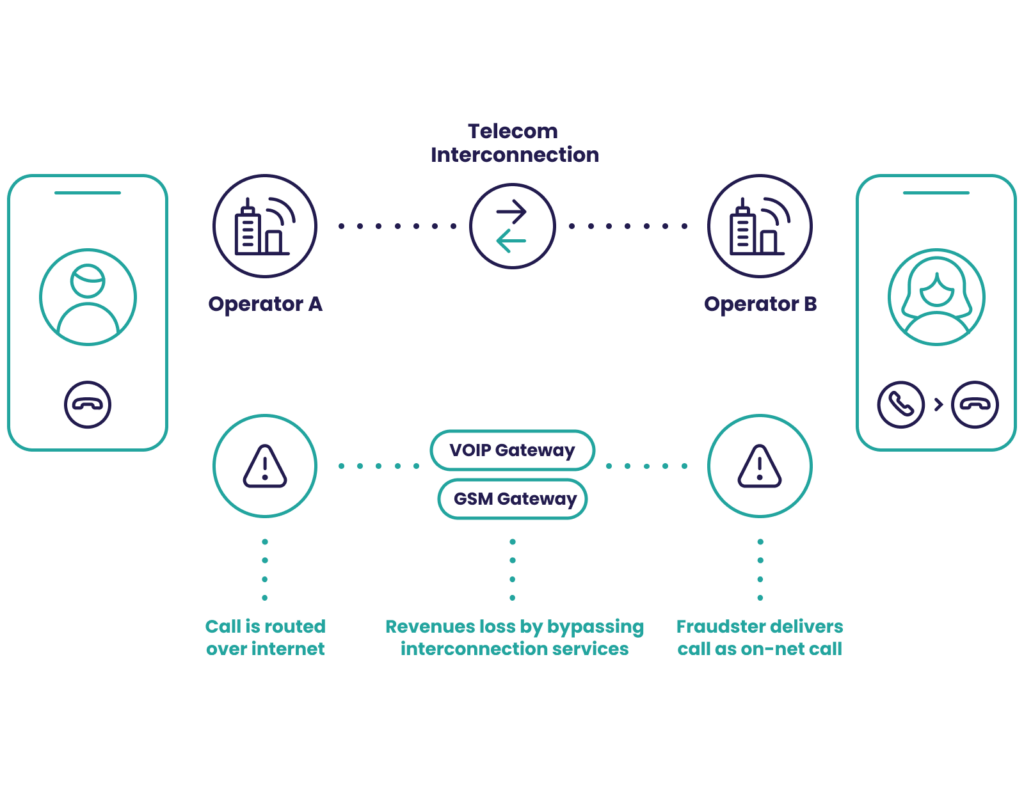
3. Interconnect Bypass Fraud
Interconnect bypass fraud, also known as SIM box fraud, takes advantage of something called a termination rate to make cheaper phone calls. It is estimated by CFCA to cost telecom operators $3.11 billion in lost revenue per year.
To understand it, let’s look at a scenario with two operators in different countries:
- A customer of Operator A calls a customer of Operator B.
- Operator A charges its customer a fee per minute.
- Operator B charges Operator A a fee for providing the call to its customer.
That last charge, where the call terminates, is the termination rate. These rates vary wildly depending on the contracts between the two operators. Some of them are expensive, others are close to 0.
This is where a fraudulent operator comes into the picture. They reroute these international calls using a SIM box or GSM gateway, effectively hijacking the connection to achieve cheaper termination rates. They are essentially making long-distance calls much cheaper, but the caller pays the same price – so the fraudster telco pockets the difference.
This also impacts telecom customer satisfaction because more often than not, the quality of these calls will be inferior to standard international calls.
4 Telecom Arbitrage Fraud
Arbitrage is the general practice of capitalizing on price differences. In the telco world, these differences appear in the long-distance rates between countries.
Just like with international bypass fraud, it can lower the international cost for customers, but also open the door to fraudulent companies who insert themselves between operators. They claim to connect directly from country A to B, whereas, in fact, they go through a cheaper rate country to connect the call.
5. PBX Hacking
PBX hacking allows fraudsters to take control of phone lines by exploiting unsecured phone networks.
A PBX (private branch exchange) is a private phone network that connects to external networks. It’s what allows companies to share lines and to reduce the number of numbers needed in an office, for instance.
Because a lot of these PBX are IP-based, they can be an easy target for hackers. They will log into the system and use it to their advantage – for instance for instances of IRSF fraud mentioned above. This is a cybersecurity and IT issue that can be avoided with better internal controls and password security.
6. Traffic Pumping
Traffic pumping, also known as access stimulation, is a practice where unscrupulous local exchanges cook the numbers of calls to their networks to benefit from compensation fees set up by the US FCC.
Under the Telecommunications Act of 1996, big telcos such as Sprint, Verizon, and AT&T have to pay fees to rural carriers – so these carriers do everything in their power to boost the number of calls to get larger payouts.
7. Deposit Fraud
Essentially a type of credit card fraud, deposit fraud targets telecom operators’ online stores using stolen credit card numbers. Fraudsters usually purchase prepaid SIMs, but the same technique applies to devices (smartphones, routers, etc.).
The problem, of course, is that online telecom stores are responsible for refunding the fees in the form of chargebacks. You could, of course, rely on your payment processor to reduce these rates or deploy chargeback-guarantee fraud prevention tools, but this does make your company vulnerable to high rates of false positives – where legitimate customers are prevented from making a purchase.
There’s also a growing threat in the form of 5G proxy networks, a practice that’s been booming in recent years, both for legitimate business and residential use cases.
Unfortunately, fraudsters also purchase SIM cards and USB dongles en masse to create their own residential mobile network. While services like Proxidize claim to cut costs and offer higher speeds, they also allow fraudsters to launch more attacks by generating and controlling IP addresses.
8. Subscription Fraud
Subscription fraud in the telephony world sees criminals sign up for contracts using stolen IDs and stolen credit card numbers.
Phone contracts are harder for fraudsters to purchase than items because they involve a form of KYC verification. That is to say, you need to verify the user’s identity before they can subscribe.
Fraudsters love high-end smartphones they can acquire through contracts. It’s a simple case of submitting fake IDs, jailbreaking the device, and reselling it on second-hand markets. By the time the repo company comes, it realizes the person does not exist.
So how do they pass the KYC checks? That’s barely an inconvenience for identity fraud experts. They have a large pool of stolen identities to choose from, acquired via phishing techniques, bought on the dark web, or rented out from ID mules.
It should be noted that in-store purchases tend to have a higher risk rate than shipping. While fraudsters have plenty of options for acquiring drop addresses (where they receive items not tied to their real identities), it’s much easier for them to walk in and pick up the devices in person.
9. Account Takeover
Telecom companies who offer online user accounts can be victims of ATO fraud, where fraudsters find the login and password details of other users and sign in in their place. Account takeovers cost companies a total of $1.62 billion in the last reported year, according to the CFCA report.
If your online store lets users create accounts, chances are fraudsters are ready to steal them – regardless of what you sell. It is expensive, as Javelin estimates it costs a business an average of $263 to recover a user’s account, not to mention how it can damage your business reputation.
The point is that you need to have systems in place to authenticate user logins to ensure you are indeed allowing the right people into your store.
10. Smishing/SMS Phishing
Smishing, also known as SMS phishing, is the practice of sending mass SMS in order to obtain personal information from the person who receives the messages.
Mass spam campaigns are the bane of customers’ and telcos’ existence. This is why SMS phishing rings have become adept at avoiding detection. They’ve been known to use software to confirm the numbers they target are mobiles and not landlines (so telcos don’t notice red flags), create auto-shops to resell the stolen details, and even provide their own hosting services to host phishing sites and marketplaces.
The volume of social engineering attacks that take the form of smishing skyrocketed by more than 328% in 2020 and while telco operators don’t always take the fall for it, they should feel uncomfortable knowing that they are accidentally complicit in the practice (and it potentially affects their reputation, too). It is concerning that according to ProofPoint data from 2022, year-on-year awareness of smishing dropped to 23%.
A simple system for monitoring signups and transactions coming from the B2B service should be enough to ensure your telco company isn’t helping a smishing business.
11. SIM Jacking and SIM Swapping
Also known as SIM swapping, SIM jacking sees fraudsters take control of a person’s SMS messages and phone calls by switching a phone number to another they are in control of.
As more and more companies, such as banks, use OTP (one-time passwords) and 2FA (2-factor verification) delivered in the format of text messages or phone calls, fraudsters are attempting to take control of people’s phone numbers in order to intercept them.
The fraudster will contact the telco’s customer service and ask to transfer their number to a new SIM, which they control. When the procedure is complete, they can receive all the OTPs and SMS verifications needed to hijack customer accounts, from social media to fintech apps.
Telco operators have become much better at mitigating this kind of risk in the last few years, simply by deploying their own multi-factor authentication (MFA) systems to confirm if the user legitimately requested a number change.
What Is Telecommunications Fraud Detection and Prevention?
Telecommunications fraud detection and prevention encompasses a wide array of strategies and techniques aimed at curtailing illicit activities that exploit telecom operators. This form of fraud can significantly undermine the financial stability of telecom companies and erode customer trust. To combat this, the industry has developed a set of best practices.
The cornerstone of effective fraud prevention in telecommunications involves the real-time monitoring of calls to identify unusual traffic patterns or suspicious behavior. This proactive surveillance is essential in spotting potential fraud as it happens, allowing for immediate intervention. However, monitoring alone is not sufficient. It must be integrated with advanced call-routing technologies that can dynamically respond to threats by rerouting or blocking fraudulent calls.
Effective telecommunications fraud prevention targets three critical areas:
- Vetting and filtering out bad resellers: Ensuring that those who resell telecom services are legitimate and do not facilitate fraud is crucial.
- Protecting business revenue: This not only involves detecting and preventing fraud but also creating robust systems that make it increasingly difficult for fraudsters to succeed.
- Authenticating users and customers: It’s vital that customers are precisely who they claim to be. Digital footprinting, device fingerprinting, and machine learning are powerful tools that help verify identities and assess risk.
By utilizing digital footprinting and device intelligence alongside machine learning-based suggestions, SEON enhances the capability of telecom operators to verify identities and manage risks effectively. This technology stack is particularly effective in ensuring that users are genuine, thereby preventing fraud in a critical area of concern.
What to Look Out for in Telecommunications Fraud in 2024 and Beyond
Telecommunications fraud is continually evolving, with recent trends highlighting a rise in sophisticated attack vectors:
- Virtual SIM Cards (eSIMs): Despite their enhanced security features, such as being difficult to clone, eSIMs are still vulnerable to malware and social engineering attacks.
- Social Engineering Attacks: The pandemic has escalated the frequency and sophistication of phishing attacks, including SMS and call-based phishing, utilizing advanced techniques like deepfake technology and targeting specific individuals through CEO fraud and spear-phishing.
- Combined Attacks: Notable incidents of SIM swapping have been linked to groups like “Scattered Spider,” who have impersonated telecom staff to access systems and execute SIM swaps for financial gain.
- AI-Enabled Telecom Fraud: With AI and machine learning increasingly used in fraud prevention, fraudsters are also leveraging these technologies to refine their tactics, such as creating more convincing smishing messages.
- Fake and Synthetic IDs: Fraudsters are exploiting advanced methods to obtain ID documents, either through phishing or services that rent out IDs. Detecting synthetic ID fraud is becoming increasingly complex as these IDs often contain legitimate elements.
These trends underscore the dynamic nature of telecom fraud and the need for continuous advancements in fraud detection and prevention strategies.
Solutions for Telecommunications Fraud
Fraudsters are adept at evading identification. They will use stolen IDs and card numbers and deploy every possible tactic possible to hide their real-life identities and intentions. This is true whether your telecommunications business is dealing with an online store customer or a local carrier.
With SEON, you can learn as much as possible about who you’re dealing with, with as little friction as possible.
In the context of telecommunications fraud prevention, that means deploying frictionless, invisible, and efficient tools to aggregate info without disturbing the customer experience of your telco business customers.
The results? Smoother business operations, and reduced rates of account takeover, transaction fraud, and ID fraud – all thanks to a powerful machine-learning-driven engine and full risk management control.
Partner with SEON to reduce fraud rates in your business with real time data enrichment and advanced APIs
Ask an Expert
Telecommunications Fraud FAQ
The most costly fraud attacks for telecommunication companies include IRSF (international revenue share fraud), bypass fraud, and traffic pumping.
Fraudulent attacks such as account takeover, transaction fraud, and subscription fraud targeting telecommunications operators can be detected with real-time monitoring, digital footprinting and data enrichment. This allows companies to learn more about users in order to accept or decline their actions, such as a payment or login.
You might also be interested in reading about:
Learn more about:
Digital Footprinting | Device Fingerprinting | Fraud Detection API | Fraud Detection with Machine Learning & AI
Sources used for this article:
- Telephony Report 2020: Telephony Report 2020
- IBISWorld: Telecommunications Resellers in the UK – Market Research Report
- ZDNet: Phone fraudsters are stealing billions each year through a scheme known as IRSF
- Javelin: Identity Fraud Hits Record High with 15.4 Million U.S. Victims in 2016
- Proofpoint: Mobile Phishing Increases More Than 300% as 2020 Chaos Continues
- Infosys BPM Podcast: Emerging Telecom Fraud Trends
- Dark Reading: Cybercriminals Target Telecom Provider Networks
- Proofpoint: Proofpoint’s 2022 State of the Phish Report
- Statista: Telephony Worldwide
- Verdict: Telecom Fraud – the battle continues
- CFCA: Fraud Loss Survey 2021