The extent of account takeover (ATO) attack fraud cannot be understated. Figures show that in the United States, over 24 million households are affected, which is an estimated 22% of the adult population.
And on top of this, bank and other financial account takeover losses are nearly $12,000 per incident, on average.
As a bank or financial institution, how do you keep your organization and customers safe?
What Is a Bank Account Takeover?
Sometimes shortened to ATO, a bank account takeover attack is when a criminal gains access to and control of someone’s bank account. Usually, this is done after they have stolen the victim’s credentials, but it can as well be a result of brute force attacks, phishing, spear-phishing or any number of cybersecurity and fraud incidents.
In fact, sophisticated brute-force cracking tools and account checkers are available on dark marketplaces for as little as $4 – and sometimes even downloadable for free for those who know where to look.
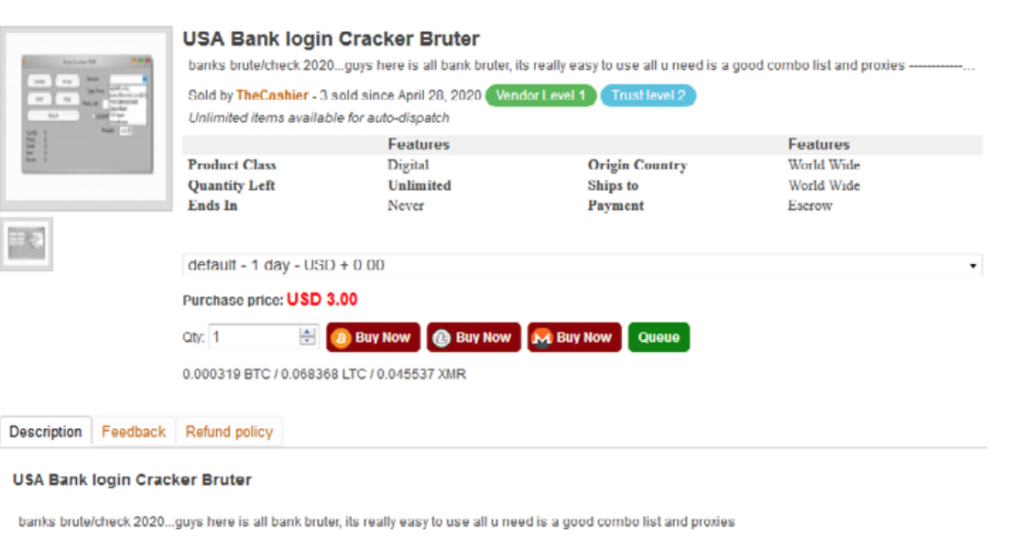
Such scripts and tools can make it more difficult to detect bank account takeover attacks compared to a criminal choosing the manual route.
Fraudsters and scammers have platforms and forums online where they discuss these techniques as well as mentor each other on how to achieve such takeovers.
Partner with SEON to block fraudsters from taking over your customer accounts with minimal friction – to enable growth and reach new heights in customer satisfaction.
Ask an Expert
Why Are ATOs a Growing Concern for Digital Banks?
In fact, ATO fraud has evolved beyond the typical phishing, renting and sharing methods of the past. Nowadays, ATO detection and prevention required more advanced methods, so, legacy prevention methods like CAPTCHA and 2FA are no longer sufficient.
On one hand, criminals now outsmart CAPTCHAs using human-assisted solving services or automated tools such as Anticaptcha and Buster.
They also use social engineering techniques and hijacking software to bypass the 2FA settings on online banking accounts – a worrying trend, considering many consumers believe multi-factor authentication to be sufficient protection.
Over 84% of financial institutions said they experienced ATOs in the past year, resulting in losses north of $12 billion.

What Do Fraudsters Do After a Bank Account Takeover?
Before we show you how to prevent account takeovers, let’s understand fraudsters better by examining what they do after successfully taking over bank accounts.
Account Draining
Once bad actors access a victim’s account, the go-to action in the vast majority of cases is to simply send the available funds elsewhere.
To avoid raising suspicion, they conduct multiple transfers, breaking the money into smaller sums (below official thresholds) that won’t trigger a review by the bank’s team. This is called smurfing.
Fraudsters often get away with this because they understand the loopholes in digital banking systems. Thankfully, you can use fraud prevention software to stay one step ahead of them.
SEON’s end-to-end platform comes with industry-specific presets, a whitebox machine learning module that learns from past activity, and fully customizable new rules, as well as risk scoring.
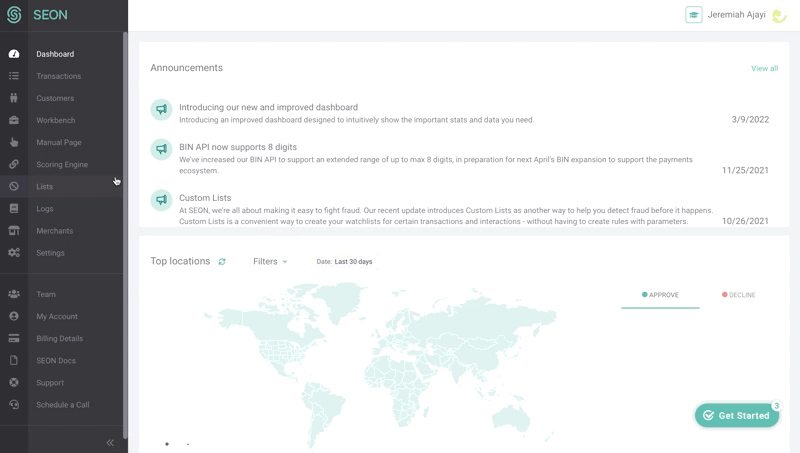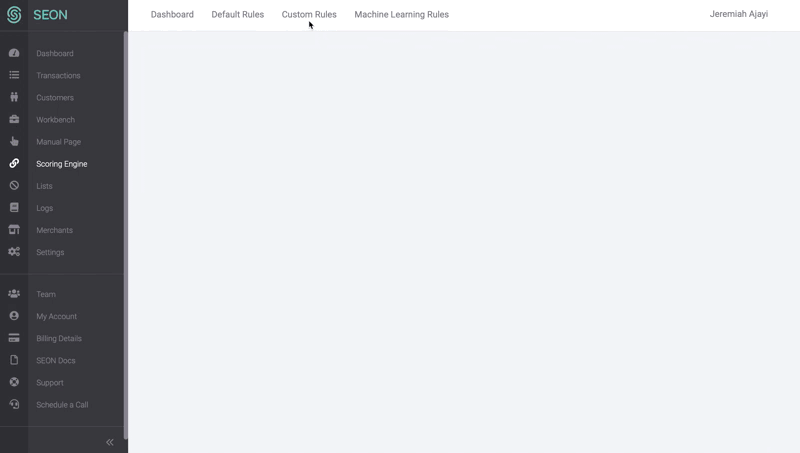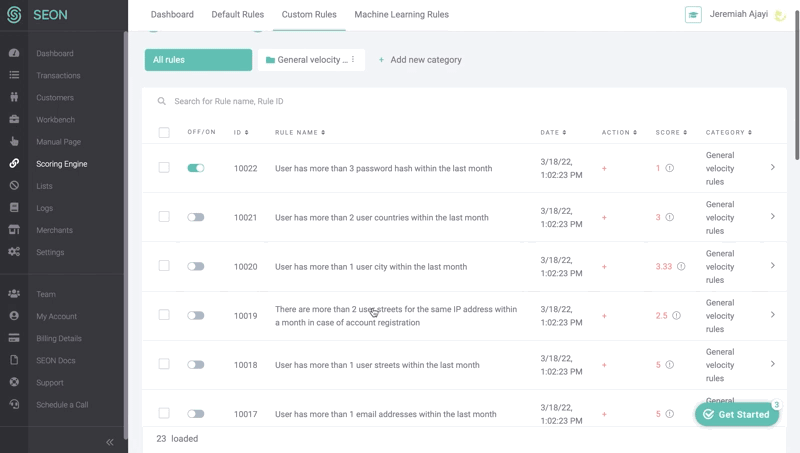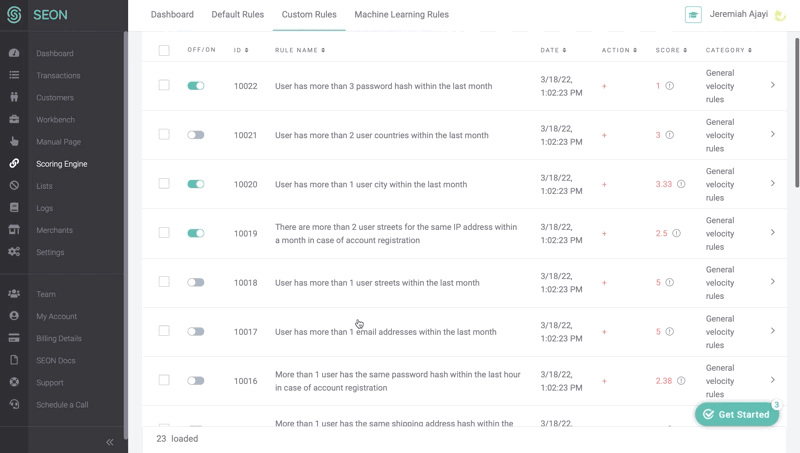
You can add new custom rules to catch such suspicious activity. The new rule we’re creating below will involve the manual review team any time a customer does more than 10 actions within 30 minutes – for example, more than 10 transfers.
Money Laundering
Criminals who profit from trafficking, terrorism, or other illegal exploits are always on the lookout for money-laundering opportunities. And stolen accounts can help them immensely, because they’ve already passed through a series of due diligence checks.
Once in a victim’s account, fraudsters deposit dirty money so they can do multiple transfers in a seemingly legitimate manner. They ensure all these go unnoticed by the victim by changing the account preferences.
That way, they can receive illegal deposits or make transfers without the victim receiving any notification whatsoever.
However, you can defend against this outcome by implementing specific AML measures and using effective fraud prevention as well as AML software.
Credit Applications
Fraudsters are eager to enjoy credit access, which they can take advantage of by taking out loans and never paying them back.
They translate that desire into reality by accessing customers’ (particularly those with good credit scores) bank accounts and racking up debt in the victim’s name without their awareness.
Initially, fraudsters repay the debt so they can increase their credit limit. And once they achieve their desired credit limit, they abandon the account, leaving the victim to bear the costs.
However, because SEON provides an alternative, modern method of sourcing data for credit scoring, it can shed light on the true intentions of the person who has applied for a loan.
This is partly done through robust device fingerprinting and velocity checks, but it is SEON’S unique data enrichment modules that can provide even more value for lenders, as they reveal an applicant’s digital footprint.
It is outcomes like this that motivated Sun Finance to adopt SEON. They were struggling to fend off account takeovers and wanted a risk prevention workflow that could improve their verification processes without refusing valid applications due to false positives.
Eventually, they chose SEON’s social media profiling, which made risk underwriting for loan disbursement substantially safer.
How to Safeguard Your Customers’ Accounts from Fraudsters
If you don’t guard against account takeovers, financial services risk losing as much as 8.3% of its annual revenue. Even worse, you might lose customers’ trust, an element EY Global Research confirmed cyberattacks often destroy.
Protecting your bank from the damage of ATO means having anti-fraud defenses such as using banking fraud prevention software that identify patterns and take action to prevent incidents from escalating.
SEON comes pre-built as an end-to-end fraud prevention tool or can be integrated into your existing stack, allowing you to detect account takeover attempts through various capabilities, namely:
IP Address Analysis & Enrichment
The limited availability of data is a crucial challenge in fighting ATO fraud. With SEON, you can gain more data points from the information you know for a fact is true.
The data enrichment module that can help fend off ATO attacks is the IP Module, which takes the known information of a person’s public IP address and enriches it to see whether it truly follows known patterns observed to be part of this customer’s normal activities and behavior.
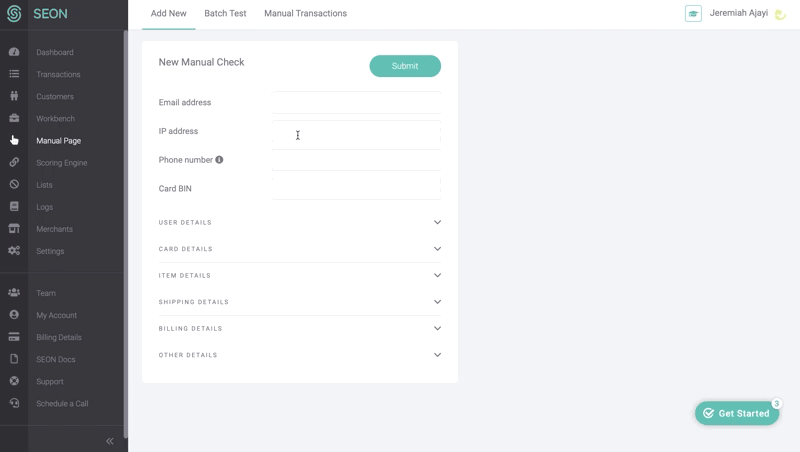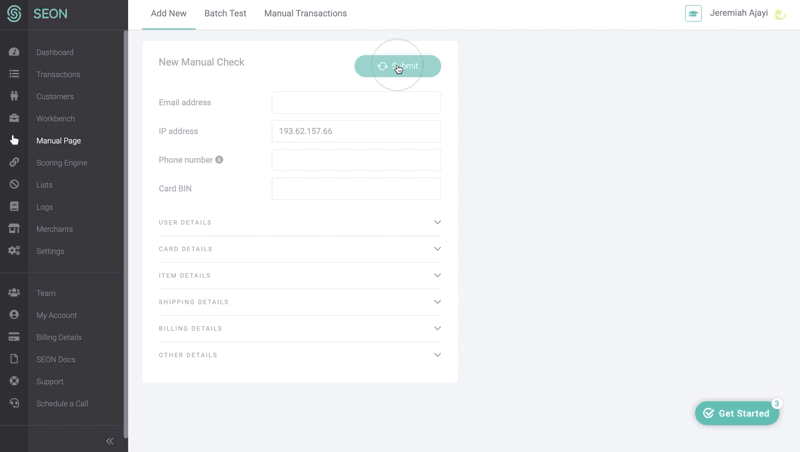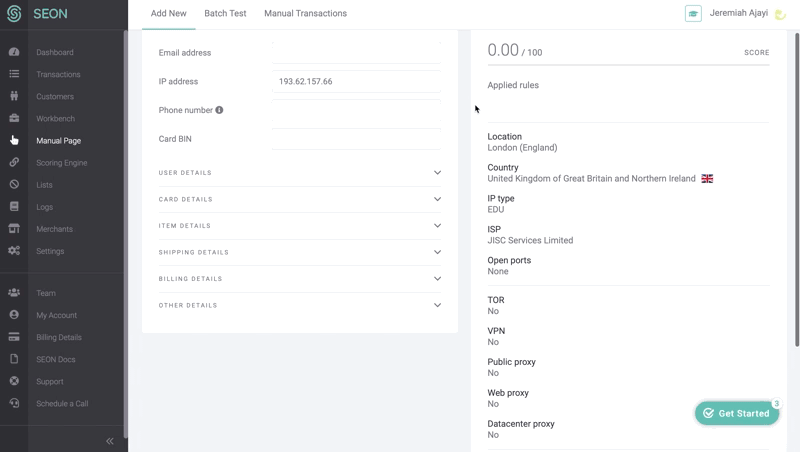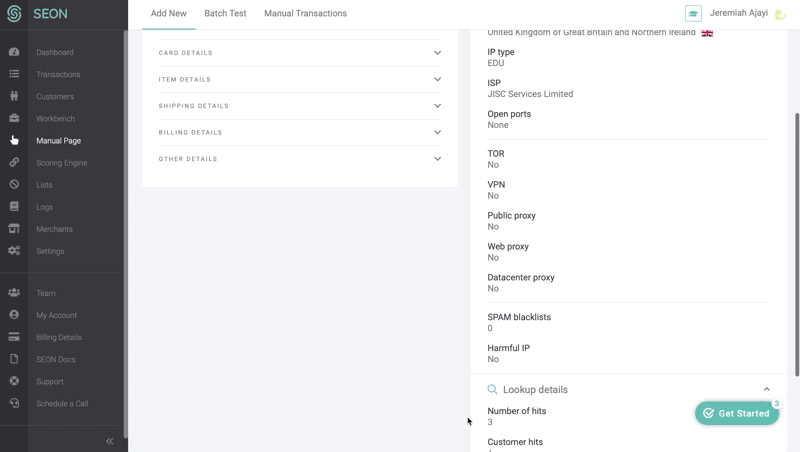
When trying to take over their victims’ accounts, fraudsters mask their locations via VPNs, Tor or proxy servers. Using data enrichment, SEON lets you unmask them.
Called manually or via API, the results of the IP data enrichment module will reveal whether the individual is indeed located where they claim to be, whether the area seems to align with what they’ve shared about themselves, and other important data points.
Of course, questions of whether this person appears to be using spoofing software are also taken into account, resulting in an overall IP fraud score.
Depending on how high this is, you can choose to review or outright block the request.
Velocity Checks
Before fraudsters successfully take over an account, they often have to test different usernames and passwords.
The result of this trial and error method? Several failed login attempts before eventual success. Though the fraudster will attempt to conceal this, these login attempts can be linked to their browser or IP address.
Simply having a limit of a handful of failed logins or requiring further verification is one way to stop fraudsters in their tracks. You can also call the SEON fraud API to confirm all successful logins are from the right users.
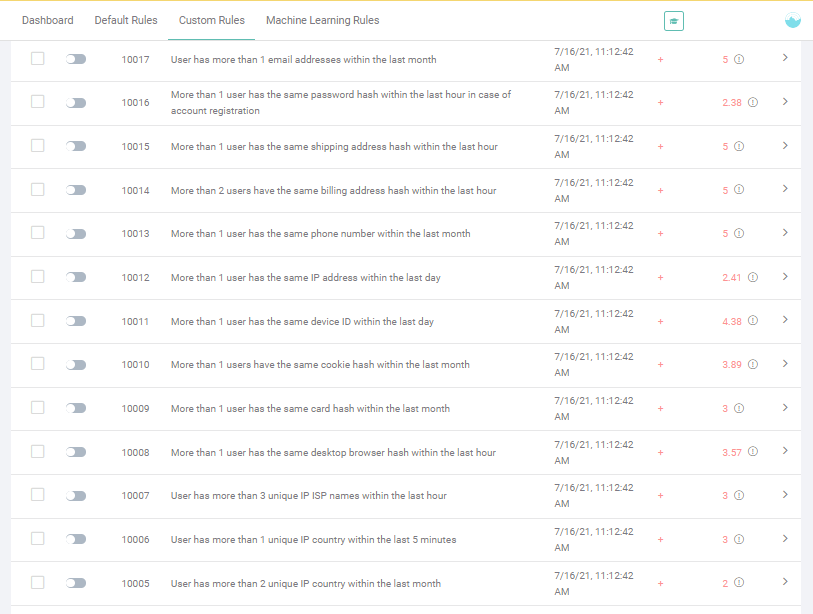
Here, you can see a sample of what velocity check rules look like on the SEON Admin Panel.
Fraud points will be added to the risk score of each user who demonstrates behavior such as more than three ISPs within an hour, or more than one country (based on their IP) within an hour.
These add up, together with other factors – so the higher someone’s risk score is, the more likely they are to be a fraudster.
Device Fingerprinting
In stopping account takeover attacks, a sophisticated device fingerprinting module is key.
SEON device fingerprinting will flag suspicious devices, hardware combinations and setups that point to someone using spoofing software instead of a real device to access an account.
Integrate SEON’s code into your platform via Javascript, iOS SDK, or Android SDK. This code integration collects the following parameters about users:

Then, you can leverage the information revealed by those parameters by defining higher score penalties for unusual setups:

In the screen above from SEON’s Scoring Engine, a disposable phone number will add 10 points to someone’s risk score. However, you can easily edit this score to make it higher or lower, based on your needs or risk appetite. You can do the same with every aspect of the scoring.
This way, you can detect fraudsters who are using OPSEC tools, as well as otherwise unnoticeable large-scale attempts by bots.
Partner with SEON to reduce fraud rates in your business, with real time data enrichment, machine learning and advanced APIs.
Ask an Expert
Machine Learning
On top of the aforementioned features, SEON’s algorithm learns from previous transactions, data, and feedback.
Based on this, it will propose new rules that are calculated to work for your specific needs to block ATOs and other harmful attacks.
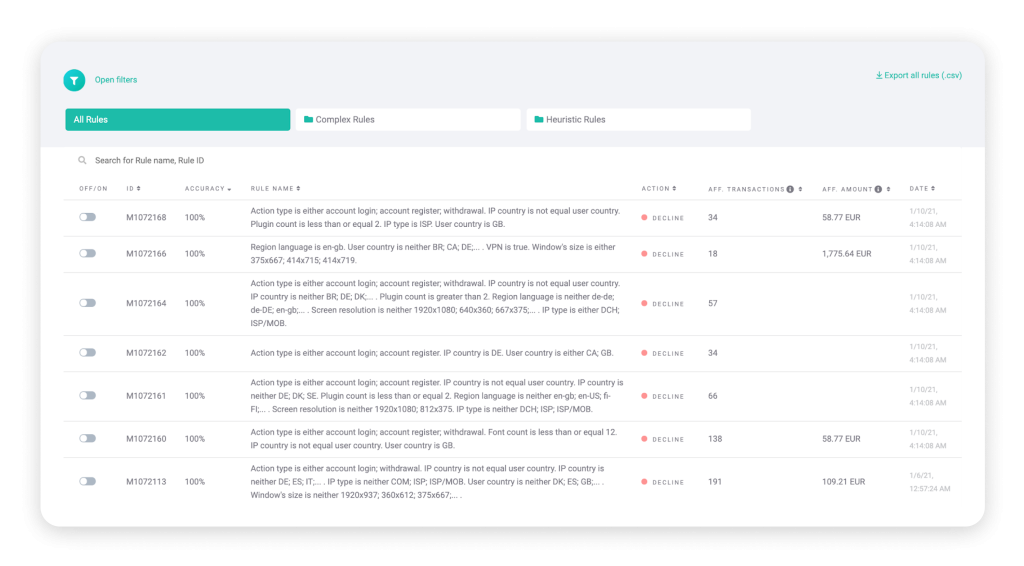
You get to control if you want to activate the proposed rules or not, and you can also see exactly what each rule will be (a whitebox setting) and what confidence rating the AI is giving it, before you even activate it.
More Ways to Keep Bank Customer Accounts Safe
Additional ideas to ramp up security include:
Keep customers informed: The work of fraud prevention becomes much easier when customers themselves are proactive about protecting their PII. Enlighten customers on the dangers of using weak passwords or sharing personal information with others. Keep them in the loop about fraudsters’ methods, showing them relatable scenarios.
Stay aware of credential stuffing tools: Be on the lookout for the development of OpenBullet, Sentry MBA, and other credential stuffing tools. More importantly, study how your security solutions measure against those tools’ evolving capabilities – or check in with your fraud solutions provider for new insights.
Discourage or block bad passwords: During digital onboarding and registration, don’t just ask customers to set complicated passwords but actively check if users’ credentials have been leaked. You can checks this using Pwned Passwords2 or K-Anonymity, and can set your onboarding software to block customers from using these leaked passwords on your portals.

How to Prevent Account Takeovers with SEON
In 2020 alone, ATOs accounted for 54% of all fraudulent transactions.
With fraudsters becoming smarter and fintech-related legislation opening up the way for innovation – which unfortunately brings opportunity for fraud – there has never been a more critical time to upgrade your strategies.
Through the combination of SEON’s data enrichment, device fingerprinting and both blackbox and whitebox ML, you can easily spot takeover attempts and block them before they succeed.
All the while, the fraud prevention modules will also protect your customers and funds from dozens of other types of pain points, including identity theft in banking and AML issues for banks and neobanks.
You might also be interested in:
Sources
- Security.org: Account Takeover 2021 Annual Report: Prevalence, Awareness and Prevention
- Globe Newswire: New Report from Aberdeen Group Reveals Serious Impact of Credential Stuffing and Account Takeover Attacks on the Financial Services Industry
- Digital Shadow: From Exposure to Takeover
- EY Global Research: Cybercrime – What does the most damage, losing data or trust?
- Kaspersky: Share of account takeover incidents increased by 20 percentage points compared to 2019
- BAI: Fraud fighters secure digital banking’s weakest links