What Is Spear-Phishing?
Spear-phishing is a type of phishing attack that impersonates a trusted entity and specifically targets a particular individual or company, in order to seem more convincing. It’s most commonly associated with emails being sent to selected targets, in an attempt to convince them to take actions such as:
- reveal personal or business-sensitive information
- log into fake or compromised websites
- install malicious software
- grant the attacker access to organizational infrastructure
- carry out other actions that further the objectives of the sender
Although spear-phishing is commonly associated with email communication, it can also happen via phone, social media, instant messaging and other methods – in which cases there is overlap with terms such as vishing, smishing, and so on.
Symantec estimates that 65% of known online crime groups use spear-phishing as part of their techniques, making it the most popular avenue of attack for cybercriminals.
A fact that often shocks small business owners is that they’re a particular target for spear-phishing attacks. Studies show that SMEs are three times more likely to be targets for spear-phishing than their larger counterparts.
This is because fraudsters are aware that smaller companies are less likely to have the resources – as well as the cyber awareness – to mitigate against such attacks.
Find out how phishing can compromise your business emails and what you can do to stay safe.
Read More
How Does Spear-Phishing Work?
A typical spear-phishing attack works in a series of steps that include reconnaissance, attack, social engineering techniques, next steps and replication.
- The fraudster will gather intelligence on their target. For example, they may research publicly available (OSINT) information to find the name of a CEO or a financial director. They may find out their email address, who they bank with, who their clients are, or any other pertinent information that can help to make their spear-phishing attempt compelling and convincing.
- The fraudster will attempt to contact the target and influence their behavior using social engineering. Techniques can include impersonating the IT department in an attempt to make a user reveal a password or install malicious software. Hackers may even pose as the CEO and request that a member of the finance department process an “urgent” payment or attempt to make the recipient worry about their job security or the health of the company.
- Cybercriminals may complement their phishing attempts with various techniques that can make them more convincing. For example, they may spoof an email address to appear to be another member or staff, or use deepfake technology to mimic upper management in a voice memo.
- Based on the exact design of the scheme, the fraudster may use information they’ve gained to perpetuate other criminal activities. For example, they may use a password acquired via spear-phishing to gain access to a corporate network, steal data, launch a ransomware attack, or start a broader phishing attack targeting a larger number of individuals.
- When a spear-phishing attempt proves successful, the attacker may often try to replicate the scam or target the same individual for more information or a larger financial payout.
Tools and technologies that criminals can employ to assist with spear-phishing include:
- social engineering techniques such as creating a sense of urgency
- deepfakes emulating the voice and appearance of other people
- spoofing techniques
- fake social media accounts
- business email compromise (BEC)
- lists of compromised credentials and fullz purchased from other fraudsters
Why Is Spear-Phishing Dangerous?
The dangers of spear-phishing include theft of funds and sensitive information from the company as well as reputational damage.
It’s an attack that requires relatively little effort, though it is by definition more difficult to carry out than general phishing, which is a numbers game. Spear-phishing is efficient because it exploits a lack of cyber awareness among individuals.
It’s also a type of cybercrime that allows fraudsters to constantly evolve and refine their methods, finding increasingly innovative and convincing ways to trick people into revealing information.
Spear-phishing is also on the increase. Over 80% of businesses say they have witnessed an increase in the frequency of phishing emails in recent years.
What Are the Consequences of Spear-Phishing?
Spear-phishing can have severe consequences both for businesses and individuals, which include stealing funds and sensitive information, as well as corporate espionage and sabotage.
Depending on the severity of the attack, the individual found to have implicitly allowed this may experience repercussions, including dismissal.
Frequently, the eventual aim of a spear-phishing attack is financial gain for the fraudster. They may aim to gain access to a finance or payroll system so that they can directly reroute outgoing payments.
Spear-phishing attacks can also cause reputational damage to the businesses they target, and embarrassment and distress to the specific staff member(s) involved.
Real-Life Examples of Spear-Phishing
Real-life examples of spear-phishing include CEO fraud, malicious emails and larger-scale attacks. Let’s take a closer look.
CEO Fraud & Finance Department Fraud
A common spear-phishing attack experienced by businesses of all sizes is CEO fraud, which often – but not always – targets finance departments.
The fraudster will determine the name of the CEO and the name of a member of finance staff who is able to process payments. This often requires no more than a phone call to the company, with the hacker posing as a legitimate supplier.
An email is then sent to the member of finance staff, purporting to be from the CEO. The fraudster may even use email spoofing software to make it appear to come from the CEO’s regular email address. They introduce urgency and stress – saying that this payment must be made today, or that there was a mistake that the company may suffer from unless remediated as soon as possible.
Keen to please the boss, the employee makes the payment.
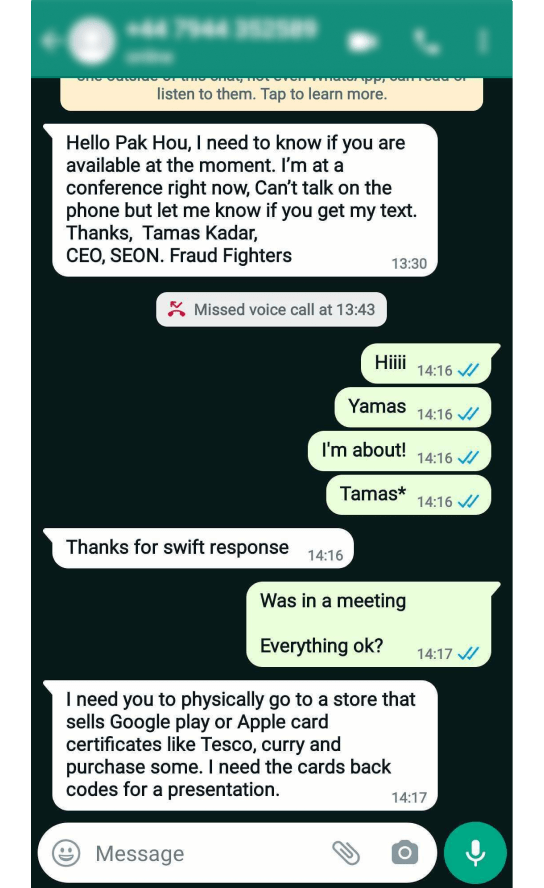
Emails with Malicious Links
Another way to target employees with spear-phishing is to gather enough information to send a convincing email that appears to come from a genuine contact or colleague. Within the email, the fraudster may include links to compromised or spoofed websites, or malicious attachments.
Similar techniques are used in broader and less targeted phishing attacks. When spear-phishing is involved, criminals make the effort to gather intelligence that increases the likelihood of convincing the victims that they’re receiving legitimate communications.
Large-Scale Spear Phishing Attacks
Spear-phishing is also used to target representatives of much larger companies and organizations, with messages being sent en masse.
In the high-profile hack of the US Democratic National Committee in 2016, criminals gained access to 60,000 private emails as a result of spear-phishing. It’s believed that a simple typo declaring a phishing email as “legitimate” instead of “illegitimate” played a part in the success of the scheme.
Another example involved an individual hacker posing as a Taiwanese hardware supplier to Google and Facebook. He sent out invoices to the tech giants totaling over $120 million over a period of three years, until he was caught and jailed.
Partner with SEON to reduce fraud in your business with real time data enrichment, machine learning, and advanced APIs.
Ask an Expert
How to Prevent Spear-Phishing
There are various technical solutions that help to prevent spear-phishing, such as anti-spam tools designed to flag or reroute phishing emails.
However, there is an ongoing cat-and-mouse game between fraud fighters and criminals, who constantly work to evade detection.
With this in mind, the most crucial way to protect against spear-phishing is cyber awareness. Employees should be trained to detect suspicious emails, phone calls and social media messages, and know to only reveal sensitive information when they are absolutely certain about who they’re interacting with.