What Is Business Email Compromise?
Business email compromise (BEC) is a type of fraud where a criminal, posing as a legitimate contact, manages to get the login credentials of an official business email address, leading to account takeovers (ATO), the exploitation of company resources through impersonation, and breaches of sensitive corporate data. The victim whose account becomes compromised may believe they are handing over their login information for a legitimate, urgent reason. These kinds of attacks can lead to extremely damaging data breaches of sensitive or financial information, or can be directly used to attempt to steal money under the guise of valid business processes.
The process BEC that maliciously targets login credentials is most often a form of phishing. As they happen online, they fall within the legal definition of wire fraud, per US legislation, and this form of fraud is on the rise as fraudsters become more adept at deception and coercion. In a 2022 survey of major financial institutions, LexisNexis reported that 71% of all fintechs had experienced a successful BEC attack. Staff up and down the ladder are vulnerable to BEC, necessitating terms like CEO fraud to refer to email compromises at the executive level. This is a particularly realistic vulnerability if all staff are not made aware of pervasive BEC tactics, and without any form of email verification software.
As an exercise, try SEON’s free email lookup tool below to see what information can be associated with a single email address, and what enriched data points might be red flags if a sudden unexpected discrepancy were to arise.
Check your IP fraud score here:
If looking up a phone number, please include its country code without plus signs, spaces or hyphens. By trying this tool, you’re agreeing to our Privacy Policy, General Terms of Service and Data Processing Agreement.
How Does Business Email Compromise Work?
BEC works by convincing an employee to disclose information that leads to their email account being accessed by an unauthorized party. From there, a fraudster may impersonate that employee, requesting payments or confidential information, or using that account to gain further access into the company’s sensitive data infrastructure. Fraudsters use openly available information from the internet, along with data gained through phishing tactics to achieve this. This can include spoofing lookalike email accounts, phishing, or malware hidden in innocuous business documents that get downloaded. In some cases, harvested login credentials may simply be put on sale on the dark web.
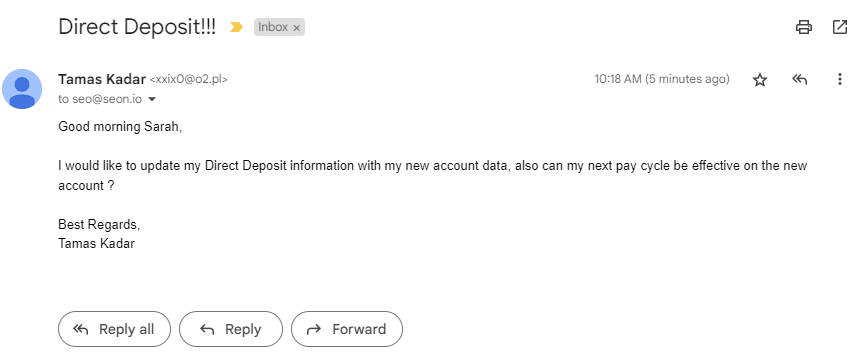
Fraudsters may pose as a legitimate business contact – usually a senior executive or a known supplier – to play on the employee’s trust. They then will often use a sense of urgency to talk the employee into making a fast payment that bypasses normal protocols, potentially introducing an element of confidentiality to explain why the usual procedures can’t be followed and might even promise a promotion or bonus.
In other cases, access to an email account with high privileges might be enough to gain access to other parts of the company’s network, resulting in huge data breaches. This is often a greater risk than an impersonating fraudster making off with company funds, as it can lead to huge reputational damage that erodes customer trust, and ultimately ROI.
Use our free guide to learn how to verify the authenticity of emails, helping you avoid falling victim to fraudulent emails from phishing scams.
Read More
How Is BEC Conducted?
There are different stages to a business email compromise attack, but they generally involve gathering intel, making contact, and then sending a request, sometimes accompanied by additional promises, coercion or other social engineering attack techniques.
- Fraudsters put time and effort into learning about a company, its processes, its contacts, and its staff before attempting to carry out BEC fraud.
- Once they have built up sufficient knowledge, they approach the organization by phone or email, usually targeting a specific individual. They may take over a legitimate email account to do so or spoof an address that looks very similar to a genuine one.
- The fraudster might pose as a senior executive within the company or as a legitimate contact from a trusted supplier or partner organization. In either case, they will inform the target employee that they need an urgent payment to be made, request access to a particular part of the network, or else continue the BEC chain and ask for someone else’s login credentials.
- They will likely advise the employee that there is an element of confidentiality related to the request and that it needs to be made in a hurry.
- One key element of BEC fraud is that the fraudster will tell the victim to bypass normal company procedures. They will provide a plausible-sounding explanation as to why this is the case, then rush the employee to fulfill their request for money or data.
- The employee, believing they are in contact with a genuine individual whom they trust, often fulfills the request before realizing anything is wrong, or else being intimidated by the impersonated authority.
How Common Is BEC?
Business email compromise attacks are increasingly common. According to Beazley’s Q3 2022 Cyber Snapshot, there were almost as many business email compromise incidents in the first nine months of 2022 as there were during the whole of 2021.
Professional services and associations reported the most BEC incidents during the first nine months of 2022, followed by financial institutions and healthcare organizations. The education sector also saw a sharp rise in BEC incidents between 2021 and 2022.
How Are Compromised Accounts Used?
Fraudsters can use compromised email accounts to access company information. Through a combination of pressure and persuasion, they can convince employees to reveal confidential information and, ultimately, to make one or more payments to the fraudster’s bank account.
Fraudsters can also use compromised email accounts to access information about a company’s contacts. They can use this as part of their BEC fraud attempts at one company, then move on to do the same at another business, using the information they have gleaned as part of the first BEC attack.
Partner with SEON to reduce fraud in your business with unique social data points, intelligent reporting, real-time data enrichment, machine learning, and advanced APIs.
Ask an Expert
How to Stop Business Email Compromise Attacks
For companies, successful prevention of BECs involves a combination of awareness training, having efficient procedures in place, and utilizing suitable software and tools that will flag suspicious activity or provide additional contextual information about email addresses, individuals, etc.
BEC attacks are effective because the fraudster has taken the time to learn about the business, meaning they can effectively pose as a legitimate contact. They do their homework and can be extremely convincing.
There are several measures that companies can take to protect against business email compromise fraud. Knowledge sharing plays a key role in implementing anti-fraud measures, so companies should ensure they are up-to-date with the latest risks, understand which risks most apply to them, and train employees regularly to be aware of the dangers. The importance of always adhering to company procedures should be emphasized as part of this work.