According to a worldwide survey, 65% of organizations experience at least one spear-phishing attack every year and one increasingly popular method is known as the CEO scam or CEO fraud.
Let’s take a closer look at what this entails and how you can help your employees – and yourself – to prevent it.
What Is CEO Fraud?
In simple words, CEO fraud is a social engineering attack where a criminal pretends to be a company’s CEO and approaches employees in an attempt to gain money, information or access to its systems.
In fact, it doesn’t even have to be the CEO in particular. Any member of upper management in a company is fair game to these fraudsters – the CFO, for example, or the COO.
What makes it a social engineering attack is the fact the fraudster assumes the identity of a person of authority that the victim would do their best not to disappoint or even question – and this is exactly why it can be so effective.
Because it usually targets specific individual employees, having gathered some information about them, CEO fraud is also said to constitute a type of spear-phishing attack. We should note, however, that some would clarify it’s technically only spear phishing when conducted via phishing means.
No matter the individual parameters though, in the heart of it, a CEO scam is whenever someone takes on the identity of a high-ranking official in a company, so they can more easily access funds, data, or physical premises.
How Common Is CEO Fraud?
CEO fraud is a niche type of attack, but it is becoming increasingly common around the world.
What’s more, new remote and hybrid working arrangement trends mean less physical proximity between employees and can result in fewer and fewer employees having any interaction with upper management – becoming more fertile ground for CEO-type fraud.
UK Finance is one of the organizations that have been tracking the frequency of this type of attack in recent years. Just in the UK, there were 603 CEO scam incidents in 2018, 676 in 2019, 837 in 2020, and 207 in the first half of 2021.
Their findings are also indicative of how much companies can lose from successful attacks, as well as how difficult it is to recover the money.
For example, 2020 saw UK companies lose £10.4/$14.06 million to CEO fraud. And the victims of these 837 separate incidents were only able to recover 37.5% of the funds that were stolen – £3.9/$5.27 million.
Meanwhile, according to an FBI public service announcement, business email compromise attacks, including some CEO fraud attacks, were a $5.3 billion business in 2017 – a figure expected to have risen.
How Does CEO Fraud Work?
The mechanisms of CEO fraud always involve convincing a company’s employees that the fraudster is “the boss” – the CEO or someone equally high ranking. There are various ways to try to do so.
The fraudster will also attempt to create a sense of urgency, so that the victim doesn’t have time to stop and think, double-check with other team members, look up the CEO’s actual email, and so on.
Usually, the message from the fake CEO will be accompanied by a request for a cash transfer out of the company’s accounts to a supposedly new account the employee isn’t familiar with, but they can also ask for sensitive information, company secrets, passwords, or even physical access to the premises.
Depending on how it is conducted, CEO fraud can be more or less risky for the attacker.
Tools Used in CEO Fraud
Tricks and technology employed by bad actors in conducting CEO fraud include:
- OSINT research: They will look up information about the individual they will impersonate, to appear more convincing. LinkedIn is a valuable resource for them, as are official websites.
- Domain spoofing: Often, they’ll use tools to make their email address and/or email message look like it originates from inside the company, although it doesn’t.
- Deepfakes: It is also possible to use audio deepfake technology to mimic the CEO’s real voice, calling the employee on the phone or leaving a phone message. The employee is less likely to find this suspicious or risky, compared to an email or text message.
- Social engineering: Social engineering tricks such as creating a sense of urgency, giving off an air of authority, and applying pressure to make the victim act without thinking, thus more likely to fall for the scam.
- Phishing and whaling techniques: CEO scams borrow several techniques and elements of phishing and spear-phishing attacks. As for whaling, it targets high-ranking employees in particular. It tends to depend on their particular goal: a fraudster who wants funds will try to scam someone in finance – or, if they want access to systems, it might be a low ranking member of CS.
- Proxies and/or VPNs: Location spoofing tools can sometimes help the attacker appear to the system and/or employees like they’re in the building, bypassing some security checks.
- SecOps tools: The usual software and apps from fraudsters’ toolbox, which help them hide their real-world identity, for their own security.
Examples of CEO Scams
Let’s look now at different modes of attack by fraudsters conducting CEO scams.
CEO-Impersonating Fraudster Attacks SEON
In December 2021, one of SEON’s own employees was approached by a scammer impersonating SEON’s CEO, Tamas Kadar!
A SEON employee received an SMS message from a new number. It claimed to be from Tamas.
When the employee responded, the scammer asked him to buy some gift cards and send him the codes “for a presentation” “at a conference” where he claimed to be.
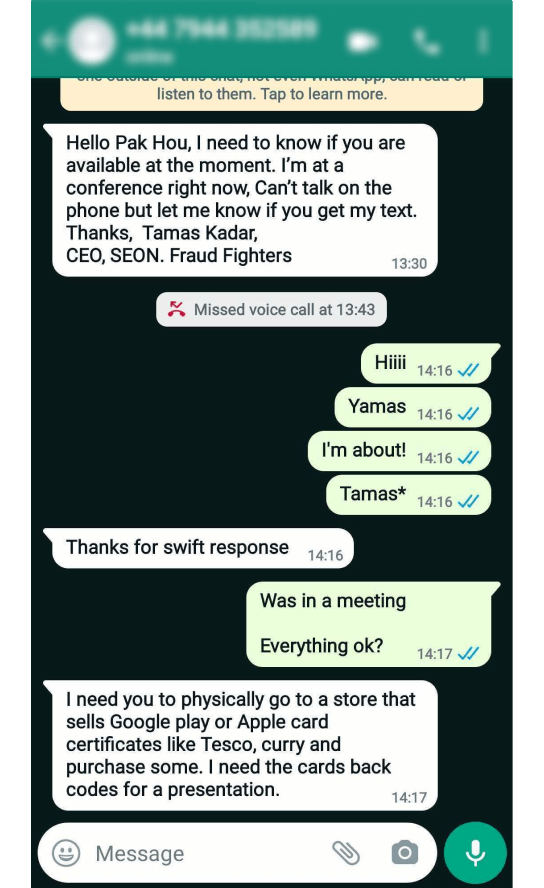
If our team member had done this, the scammer would have defrauded him through gift cards – which are much more difficult to both track and recover compared to a regular credit or debit card.
But he could smell a rat…
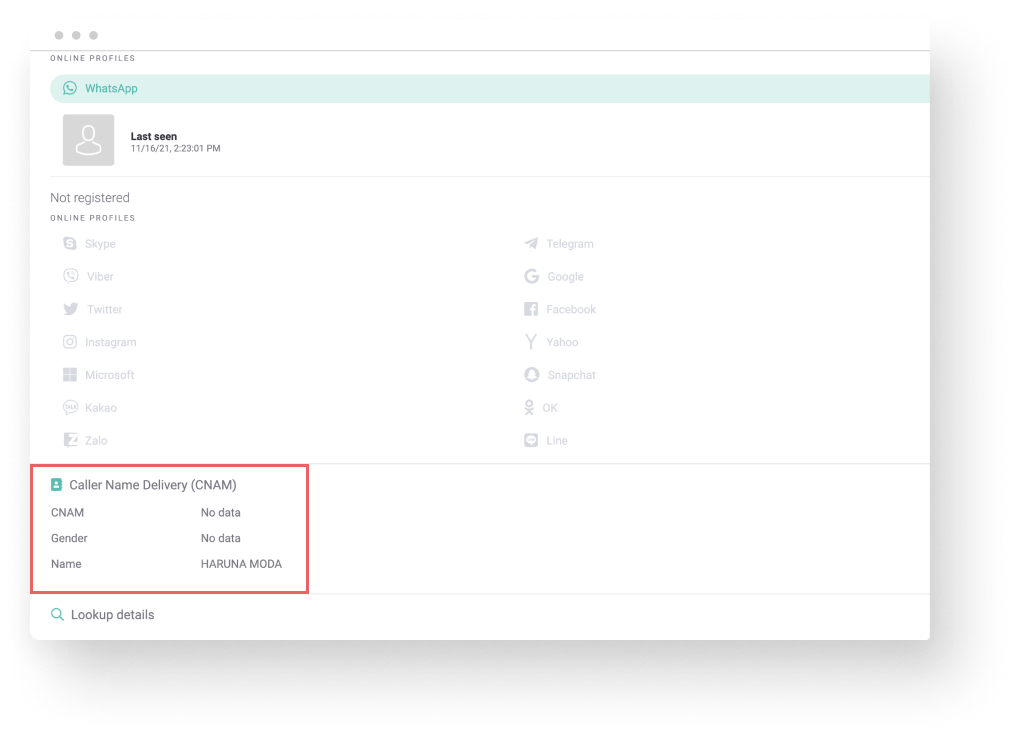
He alerted the team and we even used our SEON phone lookup to find out the name of the scammer who owns this number.
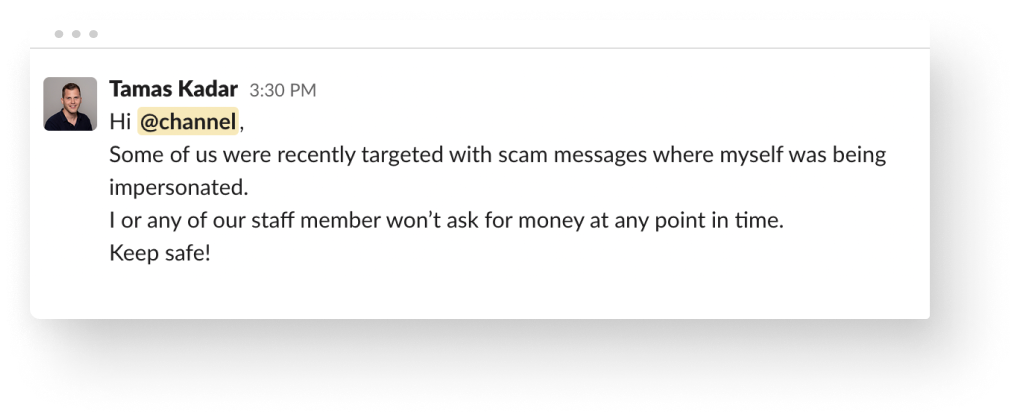
Tamas also sent a brief heads-up to the team!
Fraudsters, we applaud your ambition but did you really think a fraud-fighting company would ever fall for your CEO scam?!
The Urgent Email – A Classic
- The scammer creates an email address under the name of the CEO, on a domain that looks like but is not identical to the company domain. – e.g. [email protected] instead of [email protected]
2. Scammer sends an email to a low-ranking employee with access to finance. It reads:
“Hi Paula,
I’m in a meeting with our supplier Westgate and they’re saying we’re very late with a couple of invoices from two months ago?? Why did this happen? They’re one of our best clients! They’re irate.
I said we were experiencing software problems but they’re not happy at all. They’re threatening to leave us. Please, if you’re still at the office make the transfer now and I’ll look into what happened first thing Monday. They need to see the payment right away so I can calm them down.
Their new account is XXXXXXX. Thank you Paula you’re a lifesaver! I won’t forget this!”
- The employee, Paula in this case, scrambles to help. She makes the transfer within minutes, instead of checking the accounts or asking for more information.
- The transfer goes through to the scammer, who takes off with the money.
Other Modes of Attack
The above are very typical examples that involve some of the most common aspects of CEO fraud:
- creating a sense of urgency and risk
- making the victim believe they’re saving the company
- requesting money
However, we should note that it doesn’t always look like this. There are different techniques out there, and fraudsters are always trying out new methods too.
For instance, they might manage to get actual access to the CEO’s email inbox and might contact you from there, or they may even use a deepfake of the CEO’s voice to become even more convincing.
One more real world example is French cinema company Pathé, which lost a reported $21 million to CEO fraud in 2018. The Managing Director and CFO were also fired over the ensuing scandal.
In most cases, businesses are not obliged to disclose this information and like to keep it down low as not to appear untrustworthy or even attract more scammers so it is important to stay vigilant, use the right tools, and train employees in how to deal with these.
How to Prevent CEO Fraud
Efficient CEO fraud prevention and mitigation require the combined efforts of both employees and the cybersecurity/IT department. Let’s look at staff training and software separately.
Tools to Spot and Stop CEO Scams
- Reverse email lookup and reverse phone lookup modules: Whether you’re doing it manually with SEON’s browser extension or automatically enriching communication via an API, reverse lookup can give you detailed information about who this email address and phone number belongs to, and whether it looks legitimate. For example, you’d expect your company’s real CEO to have some level of professional presence online – e.g. a Twitter and a LinkedIn account.
- MFA/2FA and biometrics: Setting up multi-factor authentication for access to the company’s digital infrastructure is a good basic security step, and means management’s actual email accounts will be safer. Take heed though, as this does not provide complete certainty. New techniques are bound to allow attackers to intercept some one time passwords and biometrics checks.
- IP analysis: Depending on your digital infrastructure, certain attacks can be flagged or automatically blocked through IP analysis algorithms.
- Identity verification: Subject to the way the victim has been contacted, verification algorithms can look into the communications.
- End-to-end fraud software: Comprehensive anti-fraud platforms such as SEON’s tend to address some of the modes of attack of CEO fraud out-of-the-box. Also, keep in mind that other products in your tech stack might have some relevant functionality. For example, many email providers will add warnings whenever an email originates from outside of your organization.
Best Practices for Employees
As with all social engineering and social engineering-adjacent attacks, it is also important to train the staff, who are your best line of defense. If no employee will fall for it, the CEO fraud attack will always fail.
As they say, you are only as strong as your weakest link = and here this link is your less careful and/or knowledgeable employee.
Commonly cited rules of thumb include:
- Stop and think: Would this person contact me at this hour? Is what they’re asking for reasonable? Why are they asking me and not someone closer to them?
- Verify their identity: This can be as simple as calling the CEO on their company-registered phone number, or checking with a supervisor.
- Read carefully: When contacted via written message, look carefully at the text, and the sender information. Is the domain the company’s own? Does the email signature look as it’s supposed to? And so on.
- Cross-reference: Try to cross-reference with existing information. Are there any records of any meeting with this supplier on the calendar? Did any invoices actually go unpaid last month? Etc.
- When in doubt, ask: Raising a question with IT is the best mode of action if something feels off. Better yet, ask in your team/company group chat, if you use one. More senior members will be able to advise. Even if it was indeed the CEO, the company will thank you for being vigilant and careful.
FAQ
Also known as email account compromise, the terms BEC and EAC scam are often used interchangeably with CEO fraud, although there technically can be some small differences. It is also the FBI’s preferred terminology, so you’ll see it often.
It certainly is still a popular means of attack against companies, their funds and their internal data. With new fraud technology, CEO scam methods evolve, but the central idea and goals are similar.
Most often, money – in the fraud of wire transfers, gift cards or even company credit card information. But they might also be trying to get business intel to sell to competitors, or access to your IT systems to then conduct other schemes.
SEON’s data enrichment module can be set to look up email addresses and phone numbers automatically. Employees can also conduct searches manually. Meanwhile, our fingerprinting, IP and other modes of analysis will also help catch fraudsters pretending to be upper management.
Book a call with one of our customer support team members so we can talk about addressing your particular concerns.
Sources
- Proofpoint: 2021 State of the Phish Report
- Internet Crime Complaint Center: The 5 Billion Dollar Scam
- FBI.gov: Business Emal Compromise
- Variety: Pathe Loses More Than $21 Million in Internet Scam