Confused about KYC regulations and how you can improve your checks to please regulators and protect your business?
Today we’ll give you a handy five-point checklist to use and share some tips too.
How to Create a KYC Checklist
Creating a KYC checklist may be a daunting task, but it can be straightforward if you spend a bit of time thinking about your goals first. Below is food for thought:

#1: Check Global KYC Differences
The first thing to understand about KYC is that it varies from one country to another.
Sure, the basics tend to be the same, as KYC checks will include:
- getting someone’s full name
- asking for their residential address and date of birth
- confirming the above information with valid documents
Where things get tricky is when it comes to reduced or enhanced due diligence. Are there any obligations to use transaction monitoring software? Are there high-level requirements around beneficial ownership? And which ID documents are acceptable?
There is unfortunately no general answer to these questions. Each country has minor differences in regulations, which can make KYC and AML a logistical nightmare.
However, a great place to start is to check PWC’s global guide to KYC and AML here. You can also look at MangoPay’s list of acceptable ID documents for KYC here.
#2: Think About Cultural KYC Differences Too
Did you know that in Italy, 70% of customers use a paper ID to pass KYC? The documents also vary greatly from one municipality to another.
If you decide to automate KYC with, say, live video software, you might find that you frustrate your users more than anything else. The rates of false positives will be high, which will create churn, whether your customers are trying to open a bank account or use a BNPL service.
Similarly, data from 27 countries show significant differences in when users complete KYC checks. Signups after 10pm generally tend to be rare, but Spanish users, for instance, will happily register for a new service around 11pm.
The key is to ensure your checklist can take all kinds of customers into account.
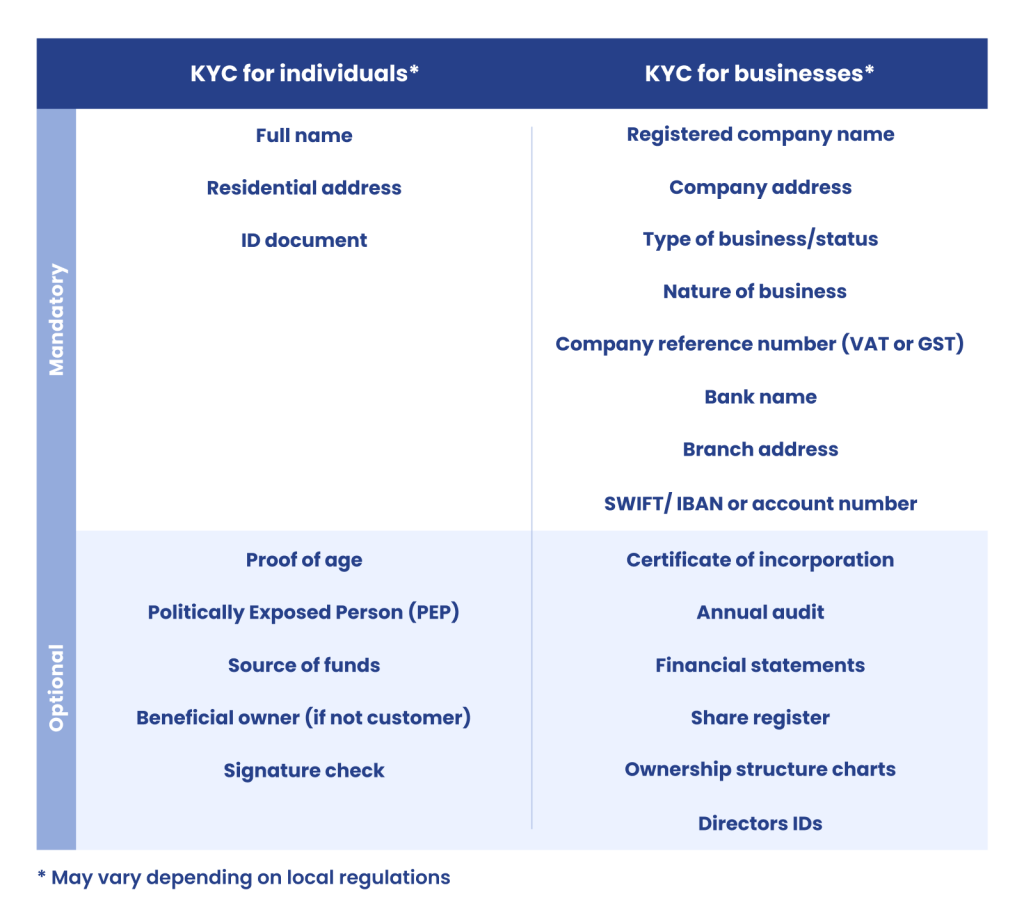
Differentiate Between KYC Checks for Individuals and Businesses
Business and individual KYC have the same goal (to learn who you’re dealing with) but go about it in different ways. Here are two examples that should work for most KYC checks in Western countries.
#3: Download Our KYC Checklist Form for New User Onboarding
You can see it includes a list of the steps you can take to meet KYC requirements. We’ve also added an onboarding checklist and risk assessment checklist.
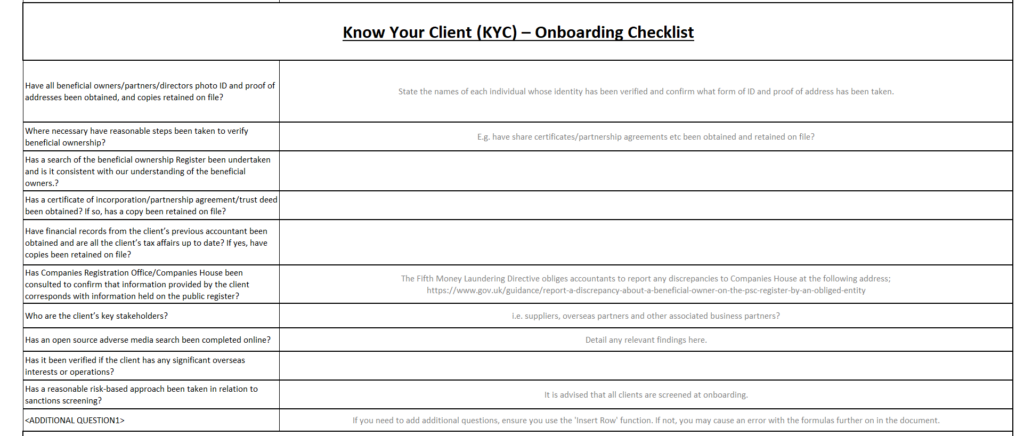
While you may need to adapt the steps based on your unique business needs and legal requirements, it’s a great place to start.
Click here to download the form, adapted from an original template by Acca Global.
#4: Automate Your KYC With the Right Software
More and more companies decide to forego KYC checklists altogether in favor of outsourcing the process.
KYC software is increasingly effective, affordable, and easy to connect to your online system (usually via API).
There are plenty of other benefits:
- Saves time on manual KYC checks
- Scales your volume of checks as your business expands
- Speeds up the process for your users
- Combines KYC with AML features
However, be aware that not all KYC software is created equal. While some focus on video identity verification, others, for instance, take the approach of verifying identities in real-time through digital footprint analysis.
You can learn more about this on our list of the best KYC software here.
#5: Consider Other Steps to Augment Your KYC Process
The KYC process can vary greatly depending on whether you’re going for simplified due diligence or advanced due diligence. If you want to go the extra mile, here’s what you can do:

Write a Customer Acceptance Policy (CAP)
The goal of a Customer Acceptance Policy, or CAP, is simply to demonstrate to regulators that you have put a KYC procedure in place.
CAPs tend to be more common in the world of financial services than, say, ecommerce, but it’s nevertheless good practice to show that you have put in the effort to understand who you’re doing business with.
Creating a Customer Identification Program (CIP)
On paper, a Customer Identification Program, or CIP, may look very similar to a CAP and other KYC checks.
The CIP, however, also establishes how long you’ll be keeping the data associated with the new account opening. There is also a stronger emphasis on KYC verification – not just gathering it.
Deploy Account Monitoring
What if you put all the right steps in place to ensure the account creation is done by a legitimate user but someone else uses it?
This may not strictly be a KYC issue, but is just as important for online businesses to ensure the customer remains in control of their account.
In risk management, ceding control of an account to a third party (usually a fraudster) is called account takeover.
The good news, however, is that the same tools you use for KYC can also help you protect accounts in the long run.
Integrate Frictionless Pre-KYC Checks
Whether you perform manual KYC checks or outsource them to a third-party vendor, the truth is that they are expensive. They are costly either in terms of resources, or actual monetary value.
The solution? You could deploy pre-KYC checks to filter out junk users before verifying their identities, for instance by using SEON.
Identifying obviously fraudulent users with fake email addresses, wrong phone numbers, or photoshopped IDs can help you save a lot on KYC checks – not to mention avoid all kinds of troubles if these fraudsters pass them.
How SEON Does Frictionless KYC
At SEON, we believe that identity verification tools need to evolve in the age of deepfakes, Photoshop, and massive data breaches.
This is why we focus on helping you understand who your users are, based on what their digital data says about them.

Here are some concrete examples:
- Was the email address created recently with a free domain provider? This should increase your suspicions.
- Is the phone number from a virtual SIM card? Red flag.
- Does the user appear to be hiding their connection settings? High likelihood of fraud.
These are precisely the kind of users who should not go through KYC checks! And the goal of identifying them early on, before KYC, is simple:
- Saves you expensive KYC checks
- Reduces fraud to 0%
- Protects your business – and users, in the long run
To learn more about how SEON helps expose digital data, read all about device fingerprinting, email profiling, and IP lookup on our website.
Frequently Asked Questions
A KYC checklist is a best-practice framework for internal compliance teams to follow to help their organizations steer clear of violating safety mandates. These mandates are subject to frequent change, as do the resources that need to be referenced as part of KYC due diligence, so keeping an updated process checklist is essential.
Sources
- Fourthline: Glocal KYC: Not all EU countries are created equal
- Acca Global: Client Risk Assessment Tool