For some companies, identity validation and identity verification are merely useful. For others, they’re a mandatory part of their KYC process. But there’s more than one way to get the most from your checks.
In this post, we’ll cover the basics, and we will demonstrate why some methods are more effective than others.
What Is Identity Verification and Validation?
Identity verification and validation both refer to the process during which your company confirms a user’s identity. It ensures the identification process is valid, that there is a real person behind an action, and that they are who they say they are.
It is particularly important in the context of fraud prevention, where flagging false identities is often the best way to reduce damage to your organization.
How Do Businesses Confirm Identities?
This is what every business should put in place to confirm identities, in these three steps:
- Identification: gather and log user data at any time
- Identity verification: confirm that the data is valid, not stolen or fake
- Identity authentication: ensure the verified data is consistent every time the user reappears on your site
Identity authentication always happens after verification. While ID validation typically only needs to be checked once, customer authentication may be necessary multiple times, for instance, if a user logs in from a previously unknown device or location.
Why Is Identity Verification Important?
Verifying a person’s identity is vital to prove that there is a real person behind the transaction/process. Fraudsters create fake profiles before abusing your business, whether they want to default on an online loan, create multiple accounts to abuse your promo system, or trigger affiliate rewards.
Simply put, fraudsters and criminals do their best not to tie their activities to real-world identities but more importantly, ID verification is increasingly a regulatory and compliance issue.
While this has long been the case in the world of banking and financial institutions, we’re seeing a more pressing need to perform identity-based authentication in a variety of verticals. This includes online stores, OTAs and payment gateways, to name but a few.
An example includes SCA (strong customer authentication) from the PSD2 directive, or the Patriot Act in the US, which states the minimum requirements for an identity verification software.
“(2) MINIMUM REQUIREMENTS —The regulations shall, at a minimum, require financial institutions to implement, and customers (after being given adequate notice) to comply with, reasonable procedures for—
US Patriot Act Section 326
(A) verifying the identity of any person seeking to open an account to the extent reasonable and practicable;
(B) maintaining records of the information used to verify a person’s identity, including name, address, and other identifying information.”
Partner with SEON to reduce fraud rates in your business with real time data enrichment and advanced APIs
Book a Meeting
Benefits of an Efficient Identity Verification Process
Confirming an identity is the cornerstone of risk management. The more a customer appears legitimate, the less likely they are to commit fraud or cybercrime on your site.
An efficient identity verification process at the login stage results in the same benefits but also improves the chances of catching ATO attacks when fraudsters log into legitimate users’ accounts.
Then there are the large fines issued for lack of KYC compliance or AML (anti-money laundering) screening.
Identity Verification vs Authentication
Identity verification and authentication are often used interchangeably. However, the verification part usually happens at signup, when you encounter the user for the first time. Authentication tends to refer to a returning user, whose identity needs to be confirmed before they can log into their account.
How Do You Authenticate Someone?
There are many trusted solutions available to authenticate a user. You can do so via secure document verification, biometrics, or multi-factor authentication. These methods serve as identifying a user and approving or declining the action depending on the quality of the data sources results.

How to Use Identity Verification in Your Business
The key point to understand is that it’s generally more affordable and easier to scale when you outsource these services to a third-party company. The maintenance is taken care of off-site, which may make life easier for your developers, but may cause data privacy concerns.
There are broadly four solutions you can deploy for eKYC or Customer Due Diligence (CDD) at your company, but not all of them are created equal.
Now let’s see which solutions work, which solutions don’t, and let’s try to understand why.

Document and Video Verification
Customers are prompted to submit high-quality images or videos of their real ID documents. These may include driver’s licenses, passports, identity cards, residency permits, or voter ID cards.
Most of the time, a selfie ID must also be submitted alongside other verification documents.
Images are then authenticated through a global network of document verification services.
- Friction: high. It is a serious obstacle to those who expect a quick user onboarding process or fast transaction.
- Efficiency: mixed. On the one hand, some customers may feel safer when their online identity is verified, but fraudsters have no problem fooling the process. They can use a plethora of services that create photoshopped selfies. There are many Stolen ID scans also on the dark web. Note that deep fake technology is also making it easier for fraudsters to create videos without someone’s consent.

Biometrics
Biometrics are body measurements that should point to a user’s unique features. These include fingerprints, face ID, and voice recognition.
From a legal perspective, many countries have yet to adopt biometrics identification as valid, but it’s increasingly becoming commonplace. India, New Zealand, Australia, and Pakistan, for instance, now accept biometrics for both identity-based security and identity verification methods.
- Friction: low. Scanning your fingerprint or Iris is much faster than submitting documents or using a password.
- Efficiency: mixed. There can be legal issues, and data privacy is a concern for some users. A false positive (or inaccurate result) can also be frustrating for users and cause spikes in your customer insult rate.

2FA and OTPs
2FA, or 2 Factor Authentication and OTP (One Time Password) are both forms of multi-factor user authentication which confirm user identities by linking them with more than one device.
- Friction: medium-high. Most of us are already familiar with failed 2FA attempts and struggling to gather the right device at the right time. It’s not always fast or easy.
- Efficiency: mixed. The rise of SIM-swapping attacks, which sees fraudsters gain possession of a user’s phone messages, is seriously hampering the efficiency of 2FA.

Digital Footprint Analysis
The concept of digital footprint for identity proofing differs drastically from the aforementioned methods. Your customers have digital lives, and they need to submit information on your site to onboard, log in or process a transaction.
Why not extract as much information as possible behind the scenes to confirm their identity? While this was a common practice as part of the OSINT (Open Source Intelligence) method, it’s a resource-heavy and time-consuming task when done manually, and it doesn’t scale either. This is why SEON decided to automate it, bringing reliable digital footprint results through data enrichment.
This allows you to gather social media data linked to the email address and phone number. This is a powerful identity verification tool that lets you gather data points such as social media profiles, including bio, avatar, and date are last seen on the platform.
Digital Identity Verification Done Right
When it comes to identity verification, the more data you have, the better. But it’s always a balancing act between gathering information and adding too much friction.
A slow onboarding process, too many obstacles during a transaction, or an astringent authentication system can increase customer churn, and send your users towards competitors.
The answer is automation through solutions such as:
- Phone number analysis lets you see if the phone number is valid, in the right country, and use virtual sim card detection.
- With IP analysis you can track identify spoofing attempts from proxies, VPNs and Tor usage, among others as well as see if the geolocation changes suddenly.
- Device fingerprinting detects users who rely on emulators and change their devices too often as they could be considered high risk – especially during the login identity authentication process.
- Reverse email address lookup which lets you check whether the domain is valid, if it’s from a low-friction provider, or if the name appears suspicious. Learn more in our guide on email check tools here.
SEON believes that digital footprint analysis and reverse social media lookup offer the best of both worlds for your identity-checking process, allowing you to make informed decisions, meet legal requirements, and support a smooth customer journey at the same time.
SEON’s Identity Verification Solution
SEON’s solution can help with identification, identity verification, and identity authentication for organizations in different sectors as a frictionless alternative to traditional methods.
It works behind the scenes, leveraging information that the customer provides either willingly (such as their email or phone number) or by virtue of being on the website (IP address, device information, browser cache, etc) to compose their digital footprint and ensure they are who they say they are.
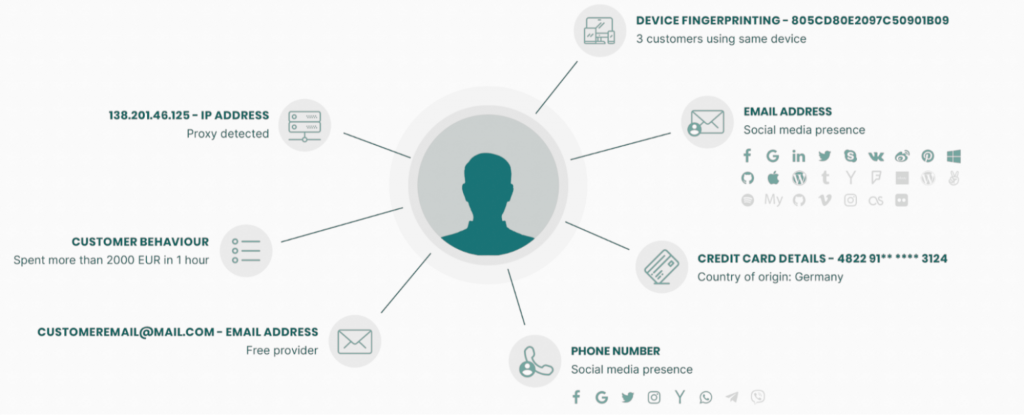
Because SEON gathers 90+ social and online signals using data enrichment, the results are much more trustworthy than conventional methods. Fraudsters will often sign up for new email accounts to match their stolen or synthetic IDs, but they will not take the time to set up an extensive, convincing digital footprint for this persona, as findings have shown.
In effect, this means that an email account set up by a fraudster will not have much social media presence. What’s more, they are very unlikely to have appeared on data leaks or have accounts on websites such as TripAdvisor and Github. On the contrary, most legitimate users will have a data trail linked to their email address.
This can then be combined with more data points, such as geolocation, and velocity and behavior checks to help with both verification and authentication.
Importantly, SEON’s solution can work alongside other methods as an API or deployed on its own as an end-to-end system.
SEON’s social media lookup tool checks 90+ social media networks and messenger apps to identify fraudsters
Ask an Expert
FAQ
Online identity verification is done by checking ID documents, using biometrics authentication, or looking at a user’s digital footprint. The key is to combine as many sources as possible to be sure you are dealing with the right person – without adding too many verification steps in the customer journey (friction).
An identity verification service takes your user data and tries to match it with databases to confirm someone’s identity. The original data can be a name and address or an ID document. Some ID proofing services look at an email address or phone number and enrich that data via digital footprint analysis.
Most identity verification software is cloud-based and operates under the SaaS model. Examples include SEON, Ondato, and Trulioo.
You might also be interested in reading about
SEON: Identity Proofing: What is it & How can it Prevent Fraud?
SEON: How Email Risk Assessment Can Help Your Business
Learn more about:
Digital Footprinting | Browser Fingerprinting | Device Fingerprinting | Fraud Detection with Machine Learning & AI