On top of this, financial criminals who carry out layering may use multiple payment methods, banks, and intermediaries to complicate the financial process further, and thus obscure the paper trail.
Fortunately, there are AML (anti-money laundering) precautions that can help people and organizations combat layering. So, let’s dive into some things you need to know about layering money laundering.
What Does Layering Mean in Money Laundering?
Layering in money laundering is the process wherein a money laundering operation passes their illicit money through enough transactions that the paper trail leading back to both the origin of the money, as well as their own identities, becomes as difficult to trace as possible.

Layering attempts are most effective when the nature of the laundered money changes across the multiple transactional processes. For example, money laundering transactions made with US dollars will be harder to detect if they are later transferred to UK pounds and then to Japanese Yen.
Post-Layering and AML Processes
The post-layering process refers to the period of time after the actual layering has taken place, when the criminals are executing a plan to get the “cleaned” money back into the economy, and their pockets. AML processes, such as the following, are there to lessen the chance of post-layering transactions being successful:
- Transaction monitoring
- Customer due diligence (CDD) and enhanced due diligence (EDD)
- KYC verification
- the suspicious activity report (SAR) process
Taking stock of the above, the process of exchanging post-layered money is combated by AML processes that monitor transactions, verify the legitimacy of customers, and utilize the SAR filing process, tightening overall security by requiring parties to report potentially suspicious transactions and individuals.
How Does Layering in Money Laundering Work?
Layering in money laundering is when money launderers complete many different transactions to the point that their malicious operations become overwhelmingly complex to trace. It is the second stage of three core stages in money laundering: placement, layering, and integration.
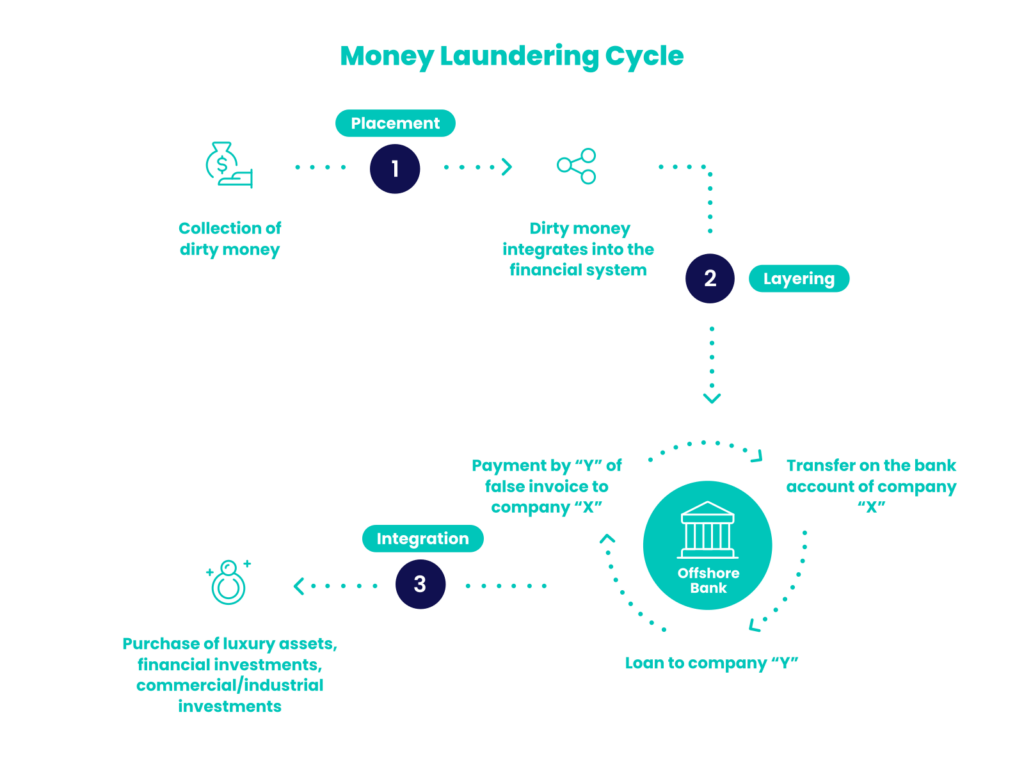
Here’s a breakdown of the three-stage process before we look further into what makes layering an unfortunately successful tactic for money launderers. And, while there are far more involved money laundering operations (such as those involving international trading), we’ll use a relatively simple example here that refers to a money launderer operating in a casino.
- Placement is when the ill-gotten money is first placed in what can be loosely defined as the legitimate economy – the economy that is free from immediate suspicion. The placement step can be executed in many ways, but for the sake of this example, picture the money launderer first giving their dirty money to a cashier at a casino in exchange for gambling chips.
- Layering is when the money launderer attempts to complicate, and therefore obscure, their connection to the initial placement of the dirty money. So, in this context, they’d then try to throw any potential watchful eyes off the scent by paying a small amount of money on gambling machines, poker tables, and so on, so that their willingness to risk losing their money may appear legitimate. But here’s what is perhaps the most important part: When this pantomime is over, the money launderer then returns, still with the vast majority of the chips they started with, and then has those leftover chips exchanged to traditional money. The money launderer has now covered their illegal activity under the veil of various layers.
- Integration is when the dirty money has been successfully placed and layered – and therefore ultimately laundered – because it is now in a state where it can be used in the legitimate economy in a way that is free from suspicion. The money, in other words, has been “cleaned” and can ultimately be spent on everyday things, just as any law-abiding citizen enjoys doing.
To make stage 2 a functional part of the operation, layering attempts are most effective when the nature of the laundered money changes throughout the multi-transactional process. For example, money launderers starting with ill-gotten US dollars will be harder to detect if they are broken into smaller amounts, exchanged into Great British Pounds and then BitCoin, then split, rejoined, and mixed.
In fact, some forms of money muling and forex fraud are some of the approaches that money launderers may use to further complicate their layering methods. Money launderers entice unwitting people into their operations by offering essentially free money.
On top of this, financial criminals will certainly be using multiple payment methods, banks, and intermediaries to add further levels of complexity to tracing the source of the money, or the identities of the criminals.
Methods of Layering in Money Laundering
As layering in money laundering can refer to any action that adds additional complexity to the paper trail, there are many possible, sometimes very simple methods.

Below, we’ll focus here on layered money laundering examples that involve complex transactions, shell companies, asset investments, and accomplices, which are:
- Complex transactions: The use of various approaches – which may include forex trading, international transfers, and of course, generally frequent and fluctuating payment amounts – to obscure the illegality of the original funds.
- Shell companies: The use of “organizations” that merely exist as a front for the illicit exchanges stemming from laundered money.
- Asset investments: The use of seemingly legitimate investments in assets such as high-value artwork or real estate can help large sums of laundered money to be concealed or spread across multiple ownerships.
- Accomplices: The use of criminal helping hands, such as corrupt bankers, to knowingly store and exchange laundered money to further obfuscate the nature of the ill-gotten funds. These accomplices could also be unwitting or unwilling, unaware they’re part of a larger money laundering operation.
These unwitting accomplices, many of whom may have been actively recruited through social media with the promise of free money, may find themselves acting as money mules. They will be asked to hold a certain amount of currency in their personal account before transferring onward to yet another account sometime later, and make a premium in return.
Such individuals are completely unaware of their involvement as layers in a money laundering scheme, and this further impedes the authorities’ attempts to trace money launderers and gather witness testimonies against them.
Variants of Money Laundering
Among the many variants of money laundering are structuring (aka smurfing), currency exchanges, bank capture, shell company schemes, and both trade-based and gambling-based money. Let’s take a look at each of them:
- Structuring (aka smurfing): “Structuring” transactions into small payments and other miniscule exchanges (like the Smurfs moving tiny packages around) to reduce the chances of detection from authorities.
- Currency exchanges: Transferring the nature of the illicit funds, especially in the knowledge that currency values constantly fluctuate.
- Bank capture: Gaining and exploiting partial or even full control over the operations of a bank – often offshore and in a jurisdiction that has limited AML measures – with the aim to launder money under the guise of a legitimate system of payment processing, whether it’s in terms of storing, exchanging, investing, or otherwise.
- Shell company schemes: Utilizing shell companies, i.e. organizations that exist in name only (although shell companies can be legitimate, especially those that are transparent about why they’re shell companies in the first place) so that transactions can be made under the cover of one or more registered businesses.
- Trade-based money laundering: Disguising illicit activities by carrying out ostensible business exchanges, especially through price misrepresentation tactics such as over-invoicing and/or under-invoicing.
- Gambling-based money laundering: Obscuring illegal transactions by placing ostensible bets and wagers and exploiting certain transactional activities that are specific to the targeted and/or complicit casinos – with chip walking being a common example, namely when criminals “clean” their money by buying a great many chips, running through the motions of a brief and conservative gamble, and then cashing out the vast majority of their chips leftover.
Of course, even this long list can only represent a tiny minority of the countless variants of money laundering that financial criminals have in their arsenal.
And yet, still, the methods are likely to diversify even more with time.
These examples can at least provide an idea of how present money laundering can be, and how difficult it is to catch when so many opportunities exist. The options available mark the plethora of opportunities that criminals have to layer their illicit funds.
Compare leading solutions to strengthen compliance, streamline risk assessments, and improve accuracy.
View top AML tools here
How SEON Can Help Combat Layering in Money Laundering
Just as SEON is there to fight fraud with its end to end fraud detection services, it’s also there to fight money laundering, even its very tricky aspect of layering. Though the methods may change and diversify all the time, the persistent key to fighting financial crime is knowing both what and who to look out for.

SEON offers a complete toolkit that your risk and compliance teams can use to cover both their legal due diligence, as well as fighting the fraud that money launderers bring with them. In terms of AML regulations, SEON provides sanctions screening software against most of the world’s crime and watch lists, and allows for the continuous monitoring for suspicious transactions which fall within the AML transaction monitoring perimeter. At the manual review stage, data points resulting from advanced API lookups and device fingerprinting allow your organization to make the most informed call possible on whether or not to trust individual customers. These unique identifiers also inform the automated risk assessment process, reviewing if user profiles show signs of automation or account takeover that can be associated with money laundering or scaled fraud attacks.
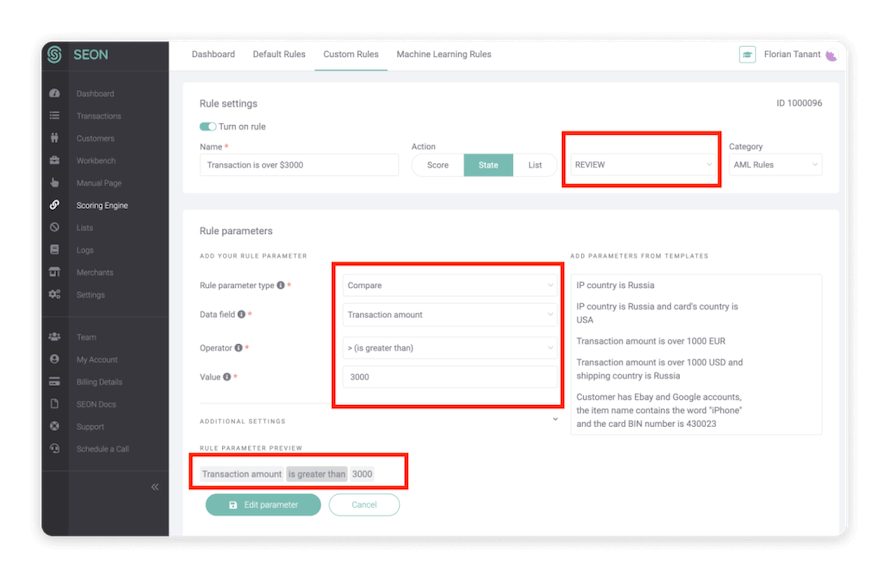
As can be seen in this screenshot, SEON offers a great degree of customization in how you can act on, for example, dubious transactions, failed AML checks, and suspiciously low social media presences. In this case, a custom AML rule has been set up to detect transactions that legally necessitate the filing of an SAR. Note that, with just a few clicks, these rules can be added to and adjusted depending on individual risk appetites or changing legislation.
When you know the legal and risk-based perimeters your company wants to stay inside, SEON’s whitebox machine learning algorithms mean that you can implement changes to your risk strategy seamlessly, and then interpret the resulting risk determinations transparently.
Ultimately, it is this level of software engagement and adaptability that will help you effectively pit SEON’s tools against layering money laundering.