Gift cards are often seen as impersonal and a last-minute gift idea. But the fact of the matter is that both businesses and customers love them and the convenience and flexibility they involve.
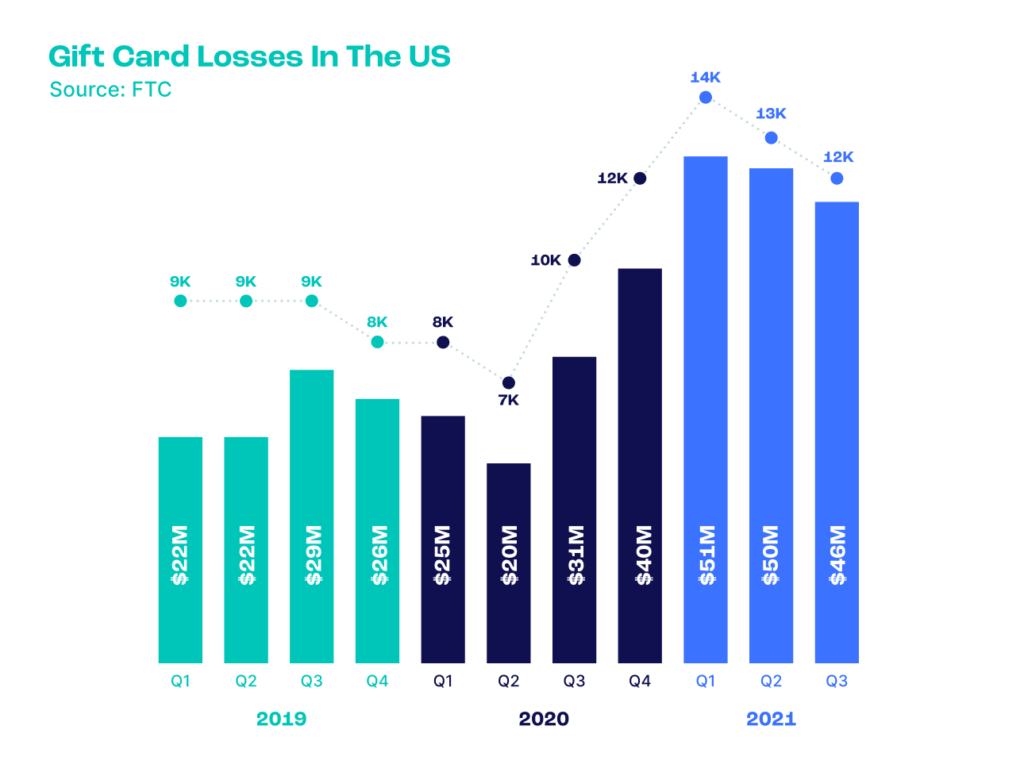
Gift card sales are projected to hit $510M by 2025, according to MagePlaza.
Unfortunately, bad agents also love how easy it is to use gift cards for fraud, scams, and other nefarious deeds. Today’s post will break down how it works and how better risk operations (RiskOps) can improve your online store’s gift card fraud prevention.
What Is Gift Card Fraud?
Gift card fraud applies to both the B2B (business-to-business) and B2C (business-to-consumer) spaces. For example, the former may involve organizations targeting other organizations with gift card scams, and the latter may involve organizations – or, rather, ostensible organizations – targeting consumers.
Also, when a fraudster commits gift card fraud to achieve a financial benefit or other personal gain, the overall process may be called a gift card scam.
You can prepare yourself against gift card fraud and gift card scams by remembering this important fact: Outside of the traditional, intended purposes of gift cards, any requests to make gift card transactions should be treated as suspicious.
This is because no organization or individual should ever ask to receive a gift card or gift card credit as a replacement for a normal transaction.
How Does Gift Card Fraud Work?
There are many different ways gift cards are used in the context of fraud. Gift card fraud can take place in a variety of ways including cloning, theft, account takeover, or exploiting errors on the merchant side.
Fraudsters can use a gift card to easily convert it into either money or merchandise, or make smaller individual transactions using a method that, in some cases, is practically untraceable. For example, certain complex fraud schemes set up phony subscriptions and applications to launder money via Google Play store vouchers.
Why Is Gift Card Fraud So Successful?
- Gift cards are anonymous: Unlike credit cards, there is no real-life identity attached to gift cards.
- They are easy to trade: There is a huge world of gift card traders and marketplaces.
- They are frictionless: Paying with a gift card is as simple as entering numbers into a field. It’s fast and easy – much more so than debit and credit cards.
- They work both online and in-store: Gift cards can be swiped, but their code also works online. Essentially, you only need the code to use the balance, which makes them very susceptible to fraudulent attacks using automated software or cloning.
SEON’s anti-fraud tools are designed to detect suspicious usage and uncover hidden fraudsters
Ask an Expert
Examples of Gift Card Fraud
Here are five examples of gift card fraud. Please note that there are technical differences between gift cards, prepaid cards and vouchers, but we’ll be using all three terms interchangeably here, as they have very similar uses in the context of fraud.
1. Gift Card Chargeback
The most common gift card fraud type is also the most obvious: Fraudsters purchase them with stolen credit cards. By the time the merchant that issued the gift cards receives a chargeback request from the legitimate cardholder, it’s too late to cancel or void it.
Another variation sees a fraudster purchase an item from your store with a stolen credit card. They return it and ask for a refund on a gift card so they can extract the money from the original card and store it on a gift card that isn’t traceable. They can then purchase items with the gift card or simply resell it on a classifieds site.
2. Pay with Gift Card Scam
In this scenario, a victim receives a phone call, email or SMS prompting them to pay for a service. It’s usually urgent and usually something official-sounding, such as a utility bill, bank charge or postal delivery fee. The fraudsters instruct the victim to purchase a gift card from their nearest retailer. They are asked to read the digit code over the phone or to send it. Because gift cards are more difficult to trace than bank transfers, this method is more likely to work in the fraudster’s favor.
3. Gift Card Number Generator or Leak
This is probably one of the most complex and technically challenging forms of attacks on our list. It involves fraudsters who manage to hack into the company’s network (or use social engineering attacks and phishing) to access the software that generates the shop’s gift card numbers and create some for their own use. In other scenarios, these hackers simply leak the gift card numbers, as seen with the Australian retailer Woolworths in 2015, when AUD 1.3 million/USD 1 million’s worth of gift cards was made available on the dark web.
4. Brute Force Bots
Gift card numbers are easier to crack than credit card numbers because they’re not tied to a specific address or identity. So it’s no surprise that fraudsters and cybercriminals have built software that will simply try all the possible combinations on online stores’ checkout forms.
You’ll notice that many retailers now refuse to tell you on their website how much balance there is on your gift card. They prefer sending a message via SMS or email, almost like 2FA for gift cards. This is done specifically to avoid giving away the balance information to such bots.
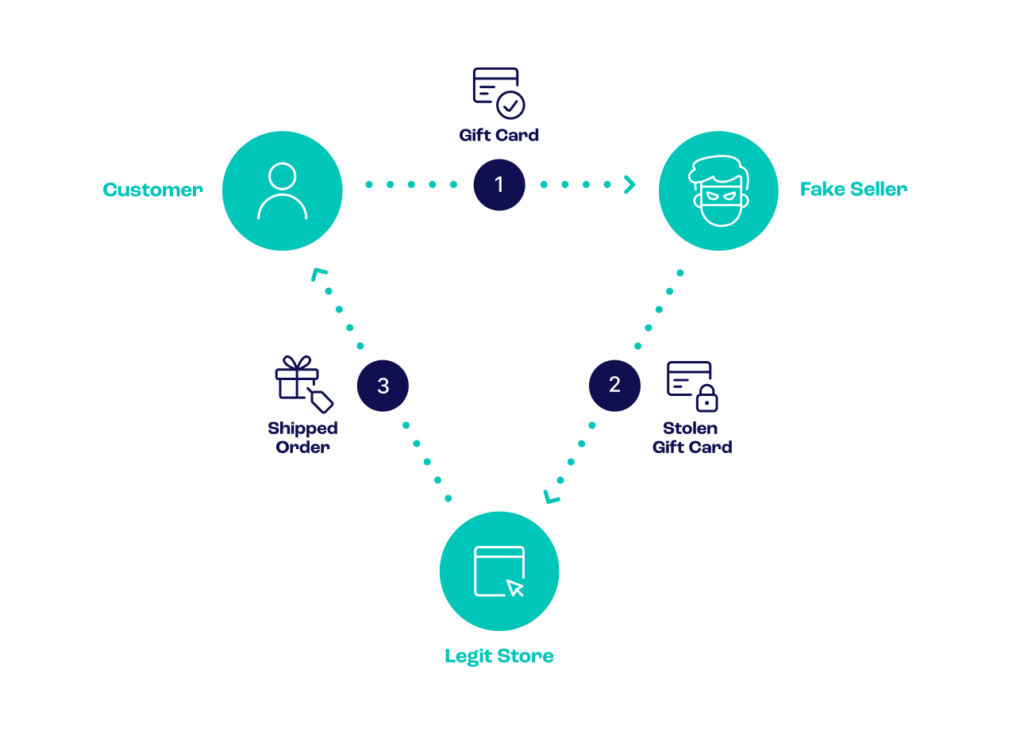
5. Triangulation Gift Card Scam
We’ve already covered triangulation fraud in our article on ecommerce fraud detection and prevention. The same principles apply to gift cards. In short, a fraudster sets up a seller account on a website such as eBay or Etsy, and accepts gift card payments. When you place an order, they purchase the same item from another store using a stolen credit card, and arrange for the order to be shipped to you. They pocket the gift card balance, or simply use it to make another payment elsewhere.
Gift Card Fraud Prevention
If your store offers gift cards, there are a number of ways to prevent them being exploited by fraudsters. Let’s go over some of the best techniques, which include risk management strategies, specialist software, and even IT and cybersecurity techniques.
Run User Fingerprinting Tools
Understanding whether you are dealing with a legitimate customer or a fraudster is the key to prevent gift card fraud. And the best way to identify both is to look at their alternative data, which is also known as user fingerprinting.
The idea is to extract as many data points as possible in order to flag suspicious users. The data may include:
- Device data: such as their combination of software and hardware
- Email and phone data: which can reveal temporary and disposable email addresses or virtual SIM cards, for instance.
- IP address: letting you flag harmful IPs, VPNs and other high-risk connections.
All the data can be checked manually, or ideally fed through the risk rules of a fraud management solution, which can calculate how risky the user action is, whether it’s the purchase of a gift card or its activation.
Leverage BIN Lookups
Another form of user profiling focuses on the payment data. This is where a card BIN lookup can be a powerful tool, to identify whether the payment seems legitimate or suspicious.
A BIN lookup can reveal the issuing bank’s location, for instance, which can be checked against the IP address or shipping address in order to spot obvious fraud cases.
Deploy Card Activation Limits
Fraudsters employ hit-and-run tactics, rushing to pay with gift cards before exiting your store and disappearing without a trace. There are two ways you can fight against these tactics, namely by adding activation delays to the gift cards, and introducing limits on how many cards can be bought by the same account.
The former strategy is designed to slow down the process between a gift card purchase and activation, which should give you enough time to spot a chargeback scam. The second is about spotting bots and automated scripts that focus on gift card purchases.
Use a Gift Card Tracker
While there are online databases designed to track prepaid, gift and virtual cards, it’s probably wise to have an internal system for tracking the gift cards that are valid at your store. The idea is to ensure there are no duplicates, or that not one customer redeems a suspiciously high number of them.
If you use a fraud prevention system, you could create a custom field that looks specifically at data associated with the gift card numbers you’ve distributed. Some fraud prevention tools also allow you to track custom fields to look for suspicious duplicates. You can use that to your advantage by generating a hash for every card and receiving alerts if they’re used twice.
Monitor Gift Card Trading Sites
It’s worth checking online gift card trading marketplaces regularly to see if they hold any that relate to your store. It can be a simple but effective part of your risk management strategy to anticipate fraud, especially if you’ve seen seasonal spikes.
In some cases, you may find that certain marketplaces do not actually allow the sell of gift cards, which could be in your favor. You can contact them to block the listings and ensure no fraudsters access them.
How Does Gift Card Fraud Affect Ecommerce Businesses?
Gift card fraud causes ecommerce businesses to lose revenue, inventory, and even customer trust. You also have to take into account the hours and resources deployed to identify the exploit and fix it, either by upgrading your security or updating your risk management software.
But by far the most damaging consequence of gift card fraud on online stores is that it may increase your chargeback rate. Remember that card operators monitor this metric closely, and that too many fraudulent attempts on your store may tip it over the recommended 1% chargeback rate.
If the above happens, you could be asked to pay more for each credit card transaction, which can have a terrible impact on your bottom line, especially if profits are already razor thin on your online sales.
Lastly, if your customers have been targeted by gift card fraud, the best course will always be to first consult authorities on the matter. And always read their terms and instructions carefully, because different organizations have different methods of suspected fraud reporting and acting on them will increase your chances of experiencing a smooth and effective anti-fraud process.
SEON offers a complete set of fraud fighting tools that grow with your business
Ask an Expert
Frequently Asked Questions
As an ecommerce brand, it is a good idea to educate your customers on gift card fraud, especially if you’ve noticed an increase in attempts. This could be as simple as writing an informative blog article, email newsletter or social media post with a handful of general tips and best practices.
Unfortunately, there’s not much to do from the business side. You could contact a local police department but the best thing to do is to log as much information as possible related to the scammer and blacklist it.
They should consult the authorities and other experts – all of which must be specific to their jurisdiction – and report the matter with as much evidence and other information as possible.
The US-based FTC (Financial Trade Commission), for example, offers advice to anyone who has been targeted by gift fraud, but this is far from the only authority. Also remember that retailers, especially the retailers that the given gift card belongs to, will be able to offer further advice as they should have a record of their transactions and how they work.
You might also be interested in…
- SEON: Credit Card Fraud Detection: The Complete Guide
- SEON: Payment Fraud Prevention & Detection
- SEON: 5 Steps to Better Transaction Fraud Detection
Learn more about:
Data Enrichment | Browser Fingerprinting | Device Fingerprinting | Fraud Detection API