As a payment gateway company, you may think your main tools to flag fraudsters are the card and transaction data.
But there are more ways to detect identity theft. Let’s look at the best methods below.
Why Is Identity Theft a Problem for Payment Gateways?
The online payment ecosystem is complex and highly exploitable by fraudsters. They have no shortage of resources to find stolen card numbers and legitimate consumer fullz, which they use to pretend they are someone else and purchase goods and services.
This is a problem for a number of reasons:
- High chargeback rates: When fraudsters purchase anything online through your system, the legitimate cardholder may make a chargeback request. This is expensive and can strain your relationship with card operators.
- Manual review efforts: Monitoring every card transaction for high-risk payments is time-consuming and resource-intensive.
- SCA and PSD2 compliance: Failing to verify identities will cause you to be non-compliant with the latest payment directive requirements for your locale.
- Working with fraudulent merchants: Sometimes, the fraudsters are merely paying on your partnering merchants’ websites. Other times, the stores themselves may be set up by fraudsters, which needs to be flagged as soon as possible.
So, in essence, why should you block fraudulent identities as much as possible? For better business, smoother operations, and less legal risk in the long run.
Learn how payment gateway Barion automated fraud prevention with SEON to accelerate productivity and keep acquiring costs at bay.
View Case Study
How Do You Detect Identity Theft as a Payment Gateway?
When detecting payment gateway fraud, identity verification isn’t easy. No customer wants to be kept waiting for IDV when they just want their payment to go through.
Friction is the enemy of good business – which is why it’s often a balancing act between security and ease of use. But deploy the right tools and workflow and you’ll keep your bottom line safe, and customers and merchants happy at the same time.
Here are the kinds of tools you can leverage in order to highlight suspicious transactions:
- Card BIN lookup: You probably already check AVS (address verification service) and CVV (card verification value) for every payment card. But you should also look at the card type and issuing location. This will come in handy when we look at risk rules below. For example, gift card fraud is more likely to occur as gift card is more likely to be abused as it lacks some basic protection that debit and credit cards have.
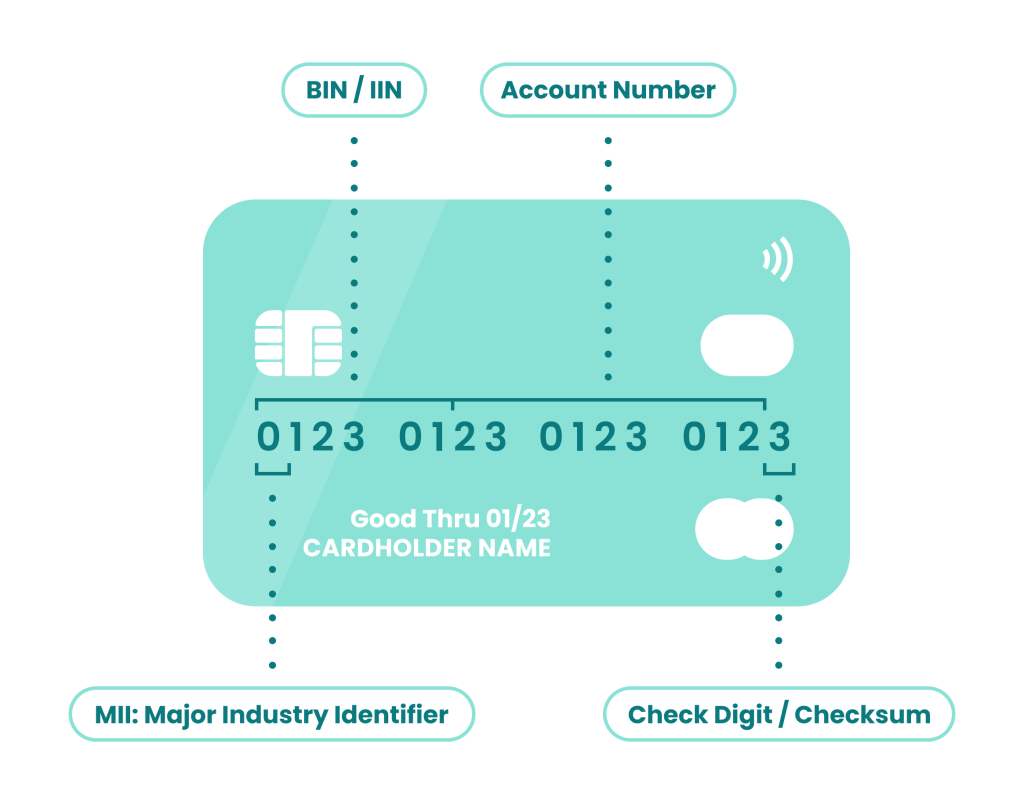
- Device data analysis: If you can gather information about the kind of computer, tablet or phone a customer is using to pay, you can highlight suspicious configurations. For instance, VPNs, anti-fingerprinting, and spoofing software should increase the risk that you’re about to process a bad payment.
- Risk scoring: Since manual reviews are out of the question in this case, tailoring your risk strategy to automatically score every transaction is the key to managing risk. High-risk users should be immediately blocked. Medium-risk users could be asked for extra verification. Low-risk payments should go through with as little friction as possible – which helps deliver excellent service to customers and merchants.
- Machine learning: Payment gateways process a huge volume of transactions compared to the average online store. You can make this into an advantage. Gather as much transaction data as possible and feed it through a machine learning fraud detection system to get surprisingly insightful results about invisible fraud trends – for instance, in the form of risk rule suggestions.
Top 3 Custom Rules for Payment Gateways to Detect Identity Thieves
Let’s now explore in detail the kind of risk rules you could deploy to spot bad transactions before it’s too late.
#1: Card and IP in Different Countries
We’ve mentioned card BIN lookups above, and a great data point these can return is the location of the issuer. This isn’t foolproof (people do travel), but should give us a general idea of who the buyer is.
Now, combined with another data point relating to geolocation, an IP address, we can start painting a clearer picture. Is the person really traveling? Or is it such an unlikely combination that you should start raising red flags?

In the example above, you see a customer who is apparently located in Russia but paying with a US card. Once again, it isn’t enough information to block the payment. But it should certainly raise the risk score on your end.
Depending on the presence of additional causes for concern, such a rule can tip the scales toward identifying that fraudster.
#2: Browser Is Spoofing Data
Device information is a powerful tool for payment gateways. It works behind the scenes in real-time, costs no extra time to gather and can reveal important data points to flag risky payments.
Let’s take a look at the example below. This payment is made via a suspicious browser profile that’s also at least five years old, and appears to be spoofing connection data. More damning, the cookies aren’t enabled from the user’s side.
This is an example of several fraud rules coming together to paint a clearer picture. In this case, that there is a lot of cause for concern.
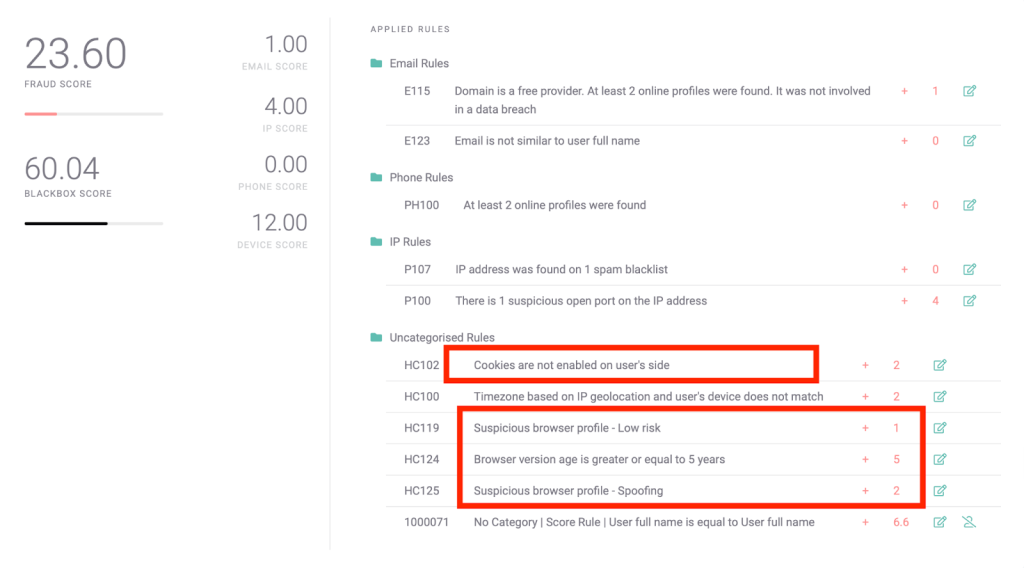
Should you accept the payment? Well, the answer might vary depending on your risk appetite.
But if you’re walking a tightrope to reduce chargebacks as much as possible, then you have every reason to block the payment.
#3: Larger Than Average Transaction Amount
You can also set up a rule that flags any payment that’s suspiciously high. This is a rule you should deploy after careful planning and research. You must have a good understanding of what an average transaction looks like with specific merchants.
However, flagging unusually large transactions for closer scrutiny is helpful when dealing with online fraud.
If a fraudster has hit the jackpot and found a card that hasn’t been blocked yet, they’ll want to maximize their profits. In many cases, that means buying as much as possible, as quickly as possible, and sending it to a drop address.
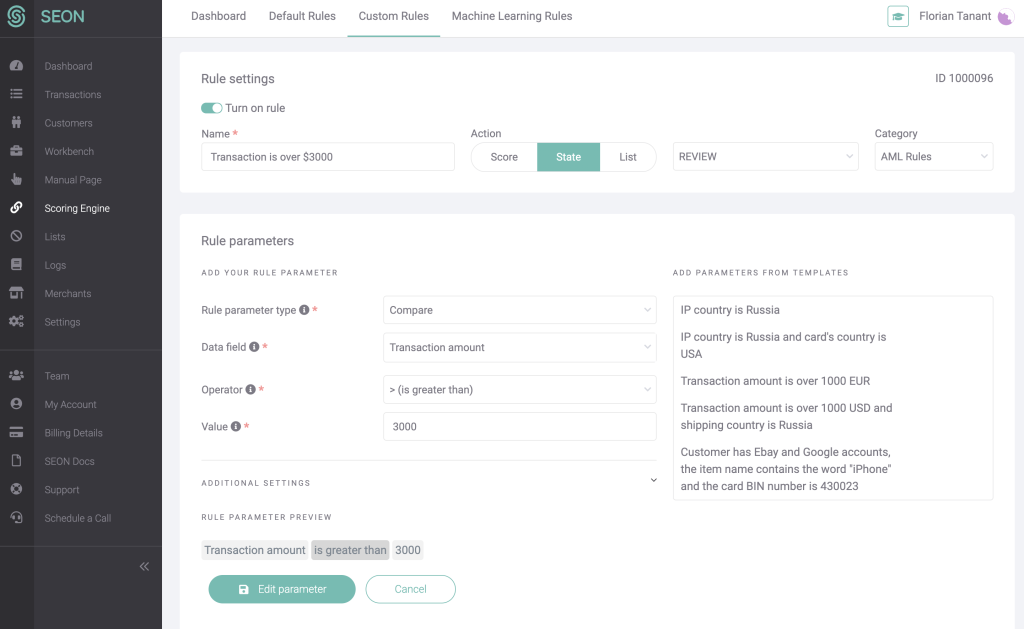
It’s worth noting that a similar rule can be applied to detect unusually low transactions.
Fraudsters will often perform card testing with small purchases to see which of their long lists of acquired card details are still “live”. So you have a lot to benefit from monitoring very small transactions, under $1, very closely.
Partner with SEON to reduce fraud rates in your business with real-time data enrichment, whitebox machine learning, and advanced APIs.
Ask an Expert
How SEON Helps Payment Gateways Detect Identity Theft
For payment gateways, stolen identities usually mean stolen credit cards and chargebacks. This is precisely why SEON is designed to give you complete flexibility, including:
- Powerful data enrichment modules: Learn as much about the cardholders as possible, in record time. You can gather real-time intel starting with their device, card, email, phone number and even IP address – often uniquely in the industry.
- Custom risk scoring: Calculate how risky a payment is based on your own risk appetite and factors like IP fraud scoring etc. SEON helps you deploy a traffic-lights system to automatically block high-risk payments, allow low-risk payments, and manually review medium-risk payments. We call this dynamic friction and it ensures you keep customer churn low.
- Machine learning suggestions: Do you have a ton of historical payment data? Want to deploy more accurate risk rules? Let our machine learning engine extract insights from your previous chargebacks to suggest better fraud-fighting strategies.
All of the above is available for free, with some limitations – or via pay-per-API call contracts for the full functionality. For more information about how SEON can help your payment gateway, book a demo with one of our team today.