In this article, data privacy and web tracking expert Gabor Gulyas shows us how fraudsters use browser spoofing to hide on your website.
If you go to the website WhatIsMyBrowser.com, chances are you’ll get fairly accurate results. It will show your IP address, location, and of course, the name of your web browser.
You may not know it, but most websites perform a similar analysis in order to learn more about their users. This is useful because it can help companies tailor specific services, or detect unusual behavior (like someone suddenly logging in from another country with another device).
And of course, it helps us spot fraudsters who want to hide their device configurations. This is mostly done with browser spoofing techniques, and today I’ll show you some examples of how they do it, along with some good detection methods.
What Is Browser Spoofing?
Fraudster use browser spoofing to manipulate their browser to make it seem as if they are using a different browser configuration which they would use regularly, for example, to make it seems as if they’re from a different country.
Fraudsters use this to bypass basic security checks and match the browser’s profile to the identity that you’re trying to use, for example, if they are looking to make purchases with a US card a fraudster would spoof their browser to match the language settings and timezone.
How Browser Spoofing Works
Since many fraudsters are looking to access accounts that are located in other countries, browser spoofing allows them to match up key factors like language, timezone, and other geolocation-based data.
By manipulating the HTTP Header messages, your browser sends off a request to a website so it appears to be from a different browser.
Websites run and render differently in different browsers so mismatches can trigger fraud prevention systems; fraudsters will often use browser spoofing as it’s more effective than just a VPN or proxy.
Sophisticated device fingerprinting yields hundreds of data points related to someone’s device, browser and activity, allowing you to identify and prevent fraud better.
Learn more
3 Examples of Browser Spoofing & How to Spot Browser Spoofing
Changing Browser Agent On Chrome
A browser’s user agent string (UA or UAS) is needed to connect a browser with the website. There are different values and formats for different browsers, but the important thing is that the string must be sent via HTTP for each request header.
In simple terms, anytime you click on a website, the UA is checked by the server to ensure communication is possible. These user agents can tell us quite a lot, including information about the OS too.
For instance, you could find out that you’re dealing with the Google Chrome browser (version 70) from this UAS example:
- Mozilla /5.0 (Windows NT 10.0; Win64; x64)
- AppleWebKit /537.36 (KHTML, like Gecko)
- Chrome /70.0.3538.77
- Safari /537.36
Chrome UA Spoofer
You can use a Chrome UA Spoofer in the form of a Chrome extension that lets you change the “look” of your browser.
Interestingly, you’ll see that this extension is developed by Google itself. That’s because it’s a useful developer tool for those who need to test websites seen from different devices.
Once you’ve installed the extension, this is how easy it is to spoof the string of your browser with a quick one-feature app.
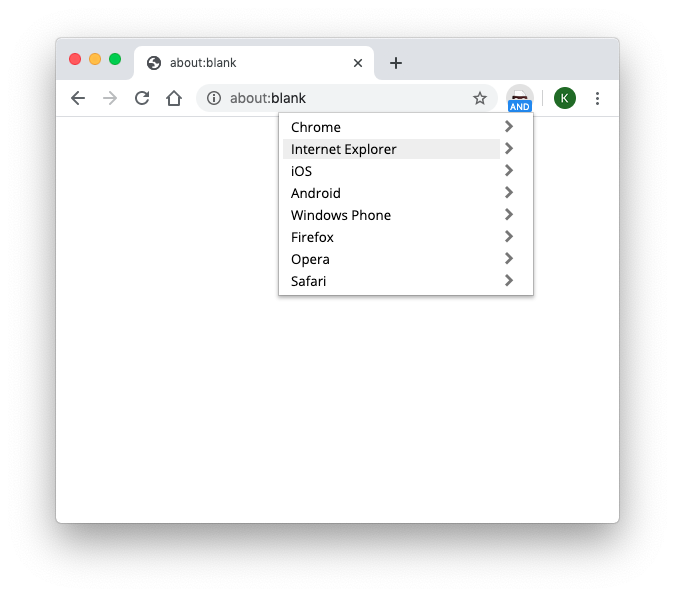
Simply search and scroll down to, say, the now antique Internet Explorer, and you’re set! Checking whatismybrowser.com will show that you are indeed using Internet Explorer to connect.
Purpose-Built Browsers
Certain browsers have been developed to such as Tor or Selenium to mask browser fingerprints based
For example, Tor defaults each user to have the same fingerprint, which minimizes targeted advertising and privacy concerns but also helps fraudsters remain anonymous to basic anti-fraud defenses.
To combat Tor, you can easily run an IP test and if this matches with a known Tor exit node, then you can block this traffic. To track Selenium usage, you can uncover evidence of the technology behind it (WebDriver) through JavaScript.
Is User Agent Spoofing Malicious?
Most developers rely on it to check how websites look from different devices. Some users change theirs for security reasons (for instance when using a VPN), but even certain browsers identify as others. For instance, the default Android web browser identifies itself as Safari to make compatibility easier.
Try it out for yourself! Install the extension in a Chrome browser and hide yourself as if it was another one. Then, check below if your Chrome browser can be still detected or not:
Other Advanced Spoofing Extensions
There are other tricks that fraudsters can use to change the way their browsers appear with a range of alternative extensions available at their disposal to attack your business.
One of them is the Trace extension, which includes an impressive list of protective features:
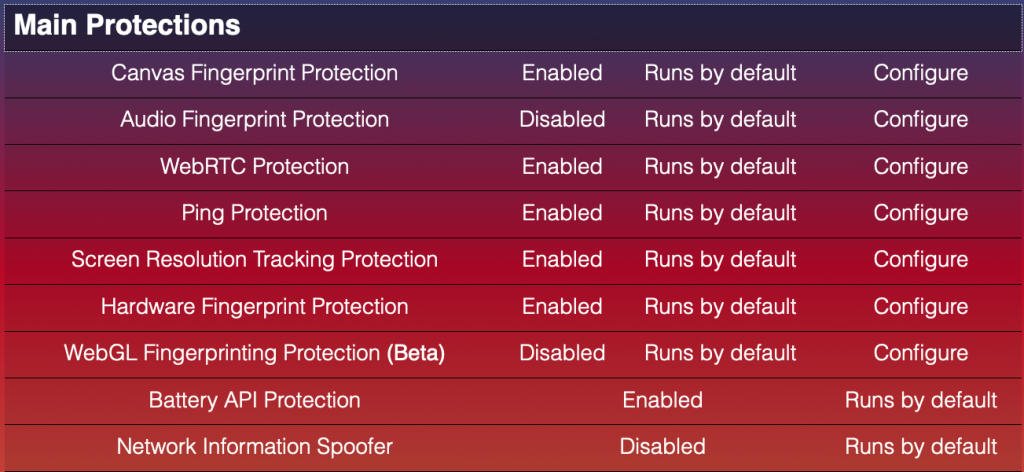
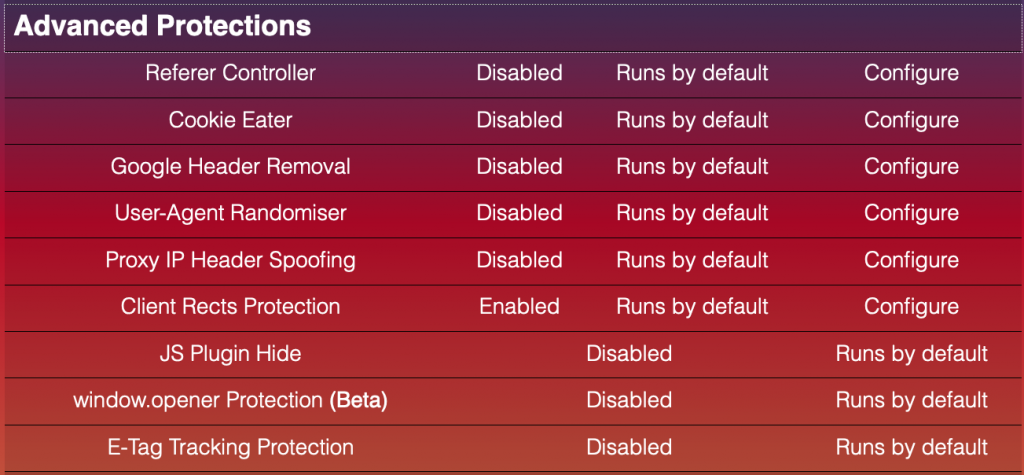
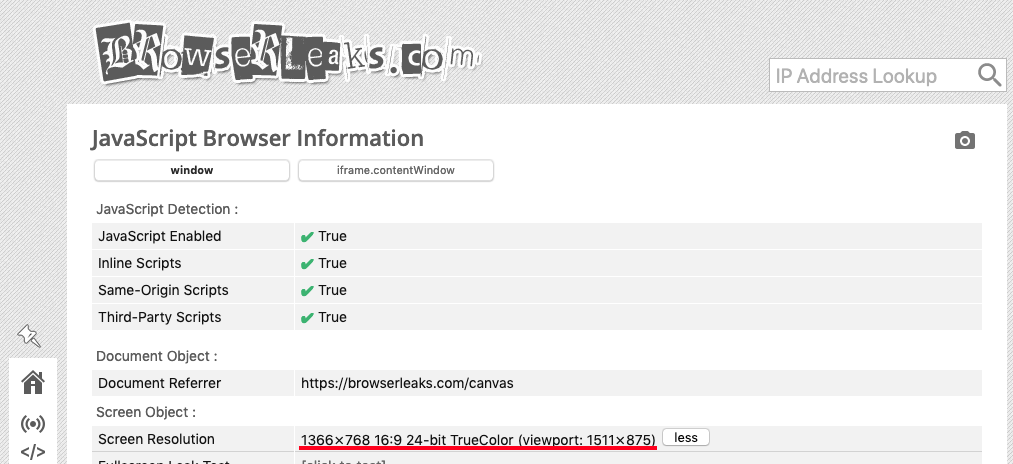
While it’s certainly a lot of spoofed parameters, they are not indetectable to the right system. For instance, one that can look at the screen size would understand that it’s smaller than the actual visible part of the windows — a strong indicator that something is suspicious. You can also see it in the example below.
The next technology fraudsters can use are privacy-orientated browsers. Tails, which is favored by darknet users for its built-in access to Tor, is designed to work on an external hard drive so that all the information can be hidden or manipulated. It even comes with MAC address spoofing, which hides the serial number of your network interface and most of the information that could identify you on a network.
What Is The Future Of Browser Spoofing Detection?
One interesting technique is the one designed by the anti-abuse team at Google. Codenamed Picasso, it’s a lightweight tool that works on the following assumption: every device has unique traits that cannot be cloned or simulated, and can, therefore, be identified by how it renders graphics.
If that’s true, then a graphical challenge could be designed to test the device, which is then compared to a genuine result.
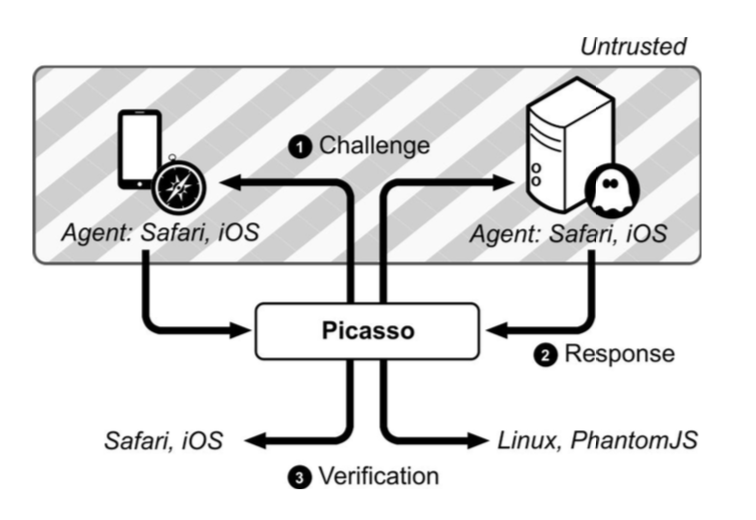
The challenges do need to be randomized, which can be costly and take substantial effort and resources to set up. You also need several genuine references to each software and hardware stack combination, relating to the device hardware, OS and web browser. Moreover, the system needs to be up to date for every combination of these three parameters.

How SEON Detects Browser Spoofing
SEON offers businesses a number of tools designed to detect suspicious usage. Our IP Analysis module, for instance, can let you know a range of parameters including:
- ISP
- geolocation
- IP Type
- open ports
- spam checklists
- browser and proxy information
- VPN usage
With SEON, we are working together on their browser fingerprinting tool, which can be integrated into web and mobile apps via JavaScript. This nifty code can reveal hundreds of data points about the combinations of software and hardware of users, which can then be fed through risk rules to calculate how suspicious a connection is.
For more information about IP risk scores, or device fingerprinting and what they can do for your organization, contact SEON today!
SEON’s anti-fraud tools are designed to detect suspicious usage and uncover hidden fraudsters
Ask an Expert
Frequently Asked Questions:
The most common form of user agent spoofing – that is, changing the HTTP header data that identifies the connecting user to appear as a different user – is certainly for testing and developing webpages. Backend and frontend web devs will spoof their UA to make sure the website behaves the way they want it to from different angles, such as unique devices and locations. Malicious users may make use of tor browsers to mask and change their apparent location for the purpose of, say, using stolen credit card credentials and masking their location to that of the victim’s to avoid detection.
As there are plenty of legitimate uses for browser spoofing – indeed, a popular tool for spoofing was developed by Google – it is not illegal by itself. However, browser spoofing is often a component of many instances of online fraud, which are illegal and punishable by law.
You might also be interested in reading about:
- SEON: Device Spoofing: How it Works?
- SEON: Cross Browser Fingerprinting
- SEON: Man in the Middle Attack
Learn more about:
Browser Fingerprinting | Device Fingerprinting | Device Intelligence | Fraud Detection with Machine Learning & AI
External Sources:
- Gulyás, Gábor György, PhD: About Me
- Tails: Portable operating system that protects against surveillance and censorship
- Tails: MAC address anonymization