What Is Tor?
Generally speaking, Tor is a privacy tool used to communicate online anonymously. It stands for The Onion Router and works to hide your IP and location, making less known about you than conventional browsing methods.
Specifically, Tor is a communication protocol that uses a network of relays to stop others from tracking you. The “onion” metaphor is used to indicate the layers upon layers of encryption applied, rendering it difficult to determine who you are and track your online activities.
Effectively, this means that website admins and other internet users cannot find out information about who and where you are, and what you have been up to online.
This extra protection is used by people looking to hide their tracks on the world wide web and the internet in general – anyone from activists living under authoritarian regimes to petty criminals or even terrorists, as well as law-abiding individuals for whom privacy is a priority concern.
Tor is also frequently used to access what is sometimes called the dark web, including Tor hidden services, which are sometimes linked to illegal activity, although not necessarily so.
Most fraudsters working online are likely to be Tor users because they are trying their best to cover their tracks. But it is important to note that being a Tor user does not mean one has something to hide.

Who Created Tor and Who Runs Tor?
The Tor communication protocol was created by the United States Naval Research Laboratory as a way to protect US intelligence communications on the internet. Tor reached its alpha version in September of 2002, while it was released under a free license in 2004 for the benefit of online privacy and free speech around the world.
It is open source and free software that has been maintained by The Tor Project, Inc. – a nonprofit based in Seattle, WA, since 2006.
Today, their mission, according to an official statement from August 2015, focuses on supporting human rights and freedoms, promoting privacy and anonymity and advancing scientific understanding.
How Does Tor Work?
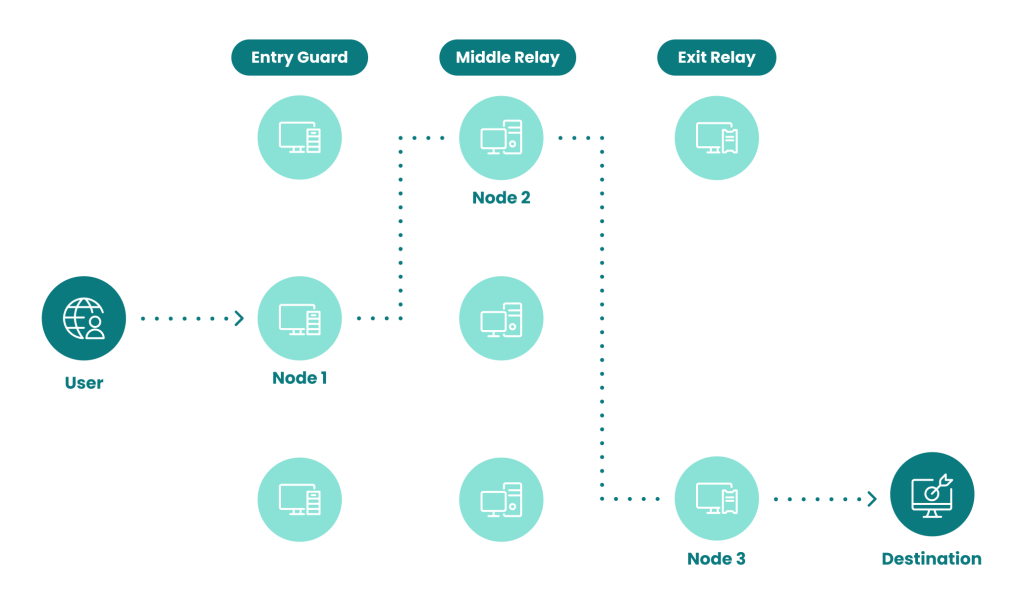
The Tor protocol uses three layers of encryption to provide anonymity, stripped or added each time the message hops to a new node. At one end, the message is unreadable. At the other, the sender is unknown.
- The user who wants to send the message runs the Tor client.
- The Tor client obtains a list of active Tor nodes for it to use.
- The message is encrypted 3 times by the Tor client.
- The message leaves the Tor user’s computer for node 1 (the entry node).
- Using a key it has already received, node 1 strips one layer of encryption.
- Node 1 sends the message to node 2 (the middle node).
- Node 2 strips one more layer of encryption.
- Node 2 forwards the message to node 3 (the exit node).
- Node 3 strips the final layer of encryption. The message is now unencrypted, but the node does not know who sent it.
- Node 3 forwards the message to the recipient server, which does not need to be running Tor.
Note that this path changes all the time. The next time the user wants to send a message, their client will choose a different set of three nodes.
None of the nodes has access to any information that could harm the user, as they either don’t know who the user is and/or what the message is, because it is still encrypted.
However, after passing through node 3, the message is no longer encrypted and can be read by anyone who intercepts it (unless there’s additional protection). The person who
intercepts and reads the message after the exit will not, however, know who sent it. Instead, they are likely to know that the sender has used Tor.
Because of the multiple steps from relay node to relay node, Tor means slightly slower communications – but those who choose to use it certainly don’t mind sacrificing speed for a boost in anonymity.
What Is Onion Routing?
Tor is an implementation of the onion routing concept, which bounces around connections between different routers in order to hide the identity of a user who is sending a message or accessing a server.
In onion routing, already encrypted traffic moves from node to node, with each node removing one of the layers of encryption, each with a different key. The message is encrypted several times, so each node can’t read it – except for the exit node, which can finally read the message and act on it.
When it has reached the exit node, the message is now unencrypted, and then sent to the server, but nobody knows who has sent it. Each node only knows the key assigned to it, as well as the address of the previous and next node. Nothing else.
So, the Tor protocol is one implementation of onion routing as a concept – but not the only way to do it. It is estimated to be the most popular, however, with approximately 2-2.5 million relay users every day in 2021, mainly from the USA (22.17% from January 1 to October 1, 2021), Russia (14.86%) and then Germany (7.68%).
What Are Tor Hidden Services?
Onion services, also known as hidden services, are anonymous websites and other services that are set up to only receive connections through Tor. Their IP and location are completely unknown, including to the Tor network.
They were first introduced in 2003 and have changed names from “hidden” to “onion” services since. Some of these have historically been online black markets such as the notorious Silk Road and others, pornography websites, message boards that allow unsavory and/or illegal topics, or tech tools that themselves provide additional privacy.
However, there are also onion services run by some of the most reputable news organizations in the world, such as the BBC and the New York Times, for various reasons including to enable anonymous evidence drops, and supporting whistleblowers.
Are Tor and the Tor Browser the Same?
The Tor Browser is a web browser that comes equipped with Tor and other anonymizer tools. Using it, one can browse the web with more anonymity.
It’s arguably the easiest and most accessible way to run one’s communications through Tor as a network.
Tor Browser is a convenient way to run Tor. However, you do not need the Tor Browser to use the Tor network. Tor Browser is developed and maintained by The Tor Project, with the first release all the way back in 2008.
How Do Fraudsters Use Tor?
Even novice criminals are likely to use Tor to hide their tracks. For example, to do some of the below:
- To buy drugs, illegal firearms and criminal services on marketplaces
- To buy stolen goods, or goods bought using stolen credentials
- To carry out device or browser spoofing and hide one’s tracks
- To sell one’s fraudulent services directly or via marketplaces
- To commit account takeover attacks
- To commit loan fraud
- For general operational security (OPSEC) purposes in order to keep one’s criminal and real identity completely separate
Because Tor is a tool cybercriminals use, every company and organization that is targeted by them would be wise to take it into consideration when evaluating whether a transaction or user is legitimate.
Is Using Tor Illegal?
No, using Tor is not illegal. Neither is it only used by criminals. However, the anonymity that the Tor network provides has led it to become a useful tool in fraudsters’ arsenal, just like a VPN or mobile proxy might be.
So, not all Tor users are criminals, but almost all online criminals go through Tor.
How to Protect from Tor-Related Fraud
Key in the efforts to fight fraud that is enabled by the Tor network or committed via onion routing is the anonymous result returned by Tor to fingerprinting requests.
Yes, Tor does increase one’s privacy greatly. But advanced anti-fraud solutions will identify whether someone is using Tor during their IP address analysis and browser fingerprinting user profiling routines.
This is because Tor users look very much alike, as if they have put on the same mask, returning almost identical browser hashes. The Tor Browser will reveal itself when the tool matches the user’s IP with a known Tor exit node, which acts like a proxy following decryption.
You can try out SEON’s IP lookup module below. Just enter someone’s IP.
For a company’s anti-fraud efforts, what is important is not exactly who this person is but rather whether they are using Tor. This is a red flag for risk scoring, and will raise suspicions and trigger manual reviews when the ruleset for fraud scoring followed is efficient.
It should also be noted that Tor does not hide the identity of the sender. It focuses on encrypting the message instead.
People have been identified for criminal activity through Tor when the police identified said messages as sent through Tor and then looked at a list of who used Tor in a specific area at the time the message was sent.
For example, such an incident happened at Harvard University in 2013 with a fake bomb threat, and the sender was caught because they were identified as having used Tor at that time, from the university’s campus.
An Example of Defense against Tor-Related Fraud
As a quick case study, let’s take, for example, an eshop running a risk management tool.
A cybercriminal is trying to access it through Tor, planning to use stolen fullz to create a new account, buy items and then later attempt to return empty boxes, thus pocketing the refund. Or any attempt at fraud that runs through Tor, really.
Experienced fraudsters trying to run such a scam will take various steps to conceal their identity and appear legitimate. However, advanced anti-fraud tools take dozens, often hundreds, of data points into consideration, to do with how the user and device are currently acting, as well as their cookies and cache (how they have acted in the past). Much of this is concealed by Tor, but the fact they are using Tor is still flagged.
In tandem with the additional data points, Tor use will result in high risk scores that will set off alarm bells and trigger appropriate protocols. The fraudster’s attempt at either creating the account or buying the items will thus be blocked and flagged for manual review. Simply put, modern anti-fraud solutions are well aware of the particularities of Tor and what fraudsters utilize it for, and therefore take all this into account when safeguarding a company.
We did an investigation of our own to get a better understanding of how fraudsters use the dark web. Today, we can leverage fraudsters’ own tools and techniques against them.
Read the Investigation
Sources
- Tor Metrics
- The Verge: FBI agents tracked Harvard bomb threats despite Tor