Criminals launder up to 5% of global GDP annually, according to UN estimates. With the global GDP for 2024 estimated at $106.17 trillion, this equates to as much as $5.31 trillion in illicit funds infiltrating financial systems. The rise of real-time digital payments has further complicated efforts to combat money laundering, creating new vulnerabilities while offering convenience to consumers and businesses.
To fight back, strong anti-money laundering (AML) frameworks are essential. Transaction monitoring plays a key role, and regulators like FinCEN and the UK’s FCA enforce compliance with international AML standards.
What Is Transaction Monitoring in AML?
Transaction monitoring is the retrospective analysis of historical and current money movements to identify suspicious behavior that could indicate money laundering or financial crime.
Many financial institutions and regulated organizations use transaction monitoring software to detect placement, layering and integration of illicit funds. Monitoring flagged accounts surpassing risk thresholds are then routed to risk and compliance teams to explore further, verify the source of funds and prevent unwitting involvement in money laundering.
The most advanced AML transaction monitoring systems blend technology, data, and human insight. Machine learning detects patterns across millions of data points, while humans make informed decisions based on those insights. When paired with proprietary fraud and behavioral insights and a user-friendly interface, this approach gives compliance and risk teams the information they need to investigate with the full context for faster, more effective threat responses.
Why Is AML Transaction Monitoring Important?

Transaction monitoring is a key part of any anti-money laundering (AML) program. It helps financial institutions spot and prevent illegal activities like terrorist financing, human trafficking, corruption and arms trading.
Businesses that could be used for money laundering must follow strict regulations. Transaction monitoring plays a crucial role by offering the following benefits:
- Identifying suspicious activity: By analyzing transactions, financial institutions can detect unusual patterns that may signal money laundering or other financial crimes. If something looks out of the ordinary, it can be flagged for further review.
- Meeting compliance requirements: Regulators require financial institutions to have strong AML systems in place. Failing to monitor transactions properly can lead to hefty fines, reputational damage and financial losses.
- Preventing financial crime: Catching suspicious activity early allows institutions to act quickly and stop potential money laundering before it escalates. This not only protects the business but also helps safeguard the financial system as a whole.
- Managing risk: Transaction monitoring gives financial institutions valuable insights into customer behavior. Understanding these patterns helps businesses assess risks and make smarter decisions on resource allocation and risk management.
- Strengthening customer due diligence: Ongoing monitoring ensures businesses keep track of customer activity over time. This allows them to reassess risk levels and maintain compliance with evolving regulations.
- Building trust: A strong AML program reassures customers, regulators and the public that a financial institution is serious about preventing financial crime. This trust is essential for maintaining a good reputation and long-term success.
In short, transaction monitoring isn’t just about meeting regulations — it’s a critical tool for protecting businesses, customers and the entire financial system.
Learn how transaction monitoring works and discover the best software and tools to mitigate risks.
Read more
AML Transaction Monitoring System
To confront both functionality and efficiency in AML transaction monitoring, it is important to understand the key features that drive effective AML transaction monitoring programs.
- Real-time monitoring: Enables immediate detection of suspicious behavior, helping teams act faster and reduce exposure to financial crime — a major upgrade from legacy, batch-based systems.
- Behavioral data and fraud insights: Helps build a fuller customer risk profile by layering thousands of fraud signals, such as IP, device, and velocity data, alongside AML alerts. This is key to differentiating. between money laundering and other threats like account takeover
- Flexible rules & alert engine: Allows teams to configure precise, no-code rules that surface only relevant alerts — reducing false positives and alert fatigue while maintaining compliance accuracy.
- Customizable workflow triage: Supports automated alert routing based on SLA, workload, or risk type to ensure priority issues are addressed first and investigations progress efficiently.
- Accurate proprietary risk signals: Leverages directly sourced AML screening data from government lists— including sanctions, crime lists, PEPs, and more — so data is always up to date, alongside over 1,000 unique risk signals for high-confidence decisions
- Case management in one system: Enables cross-functional collaboration with audit-ready case files, investigator notes, document attachments, and direct escalation paths — eliminating reliance on spreadsheets and reducing investigation timelines
- Built-in regulatory reporting: Uses AI to auto-fill report details and write SAR narratives and file reports with regulators like FinCEN in one audit-ready system to improve accuracy and reduce time spent on regulatory reporting.
- Single API for easy integration: Consolidates fraud detection, AML screening, transaction monitoring, and reporting through a single API — reducing integration overhead and ensuring data consistency across compliance workflows
How to Set Up Transaction Monitoring in AML
To set up AML transaction monitoring, the first step is to customize rules and alert triggers based on the regulatory requirements you must adhere to. Note that various regulatory agencies may have different requirements you must adjust for and accommodate.
For example, setting up rules that monitor for:
- Large transactions: Monitoring transactions above a certain threshold to identify potentially high-risk activity.
- Unusual patterns: Detecting abnormal transaction patterns or behaviors that deviate from a customer’s normal activity.
- Structuring or smurfing: Identifying multiple smaller transactions designed to evade reporting thresholds.
- Rapid movement of funds: Detecting swift movement or velocity of funds between accounts, or if outflows rise over a certain amount, may suggest illicit activity.
- High-risk countries: Flagging transactions involving countries known for money laundering or terrorism financing.
- Politically Exposed Persons (PEPs): Monitoring transactions involving individuals with political influence to prevent corruption or bribery.
- Sanctions Screening: Checking transactions against government-issued sanctions lists to identify dealings with restricted entities.
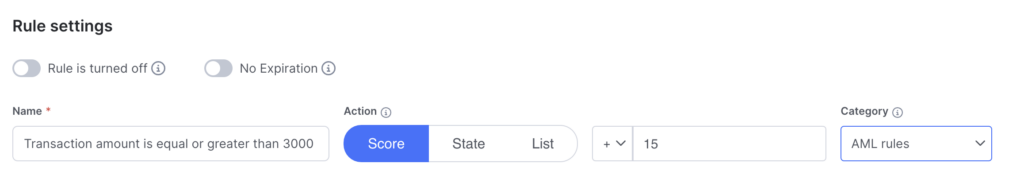
Setting Up AML Transaction Thresholds
You’ll need to set up a rule to ensure that transactions over a certain threshold are logged and monitored.
To do so, use the “compare” parameter and the operator “greater or equal to.” The demonstration value is $3,000, the most recent US banking AML requirement. Every time this setting is met, the rule will trigger. Note that you can manage currencies in settings and change each currency at the rule level.
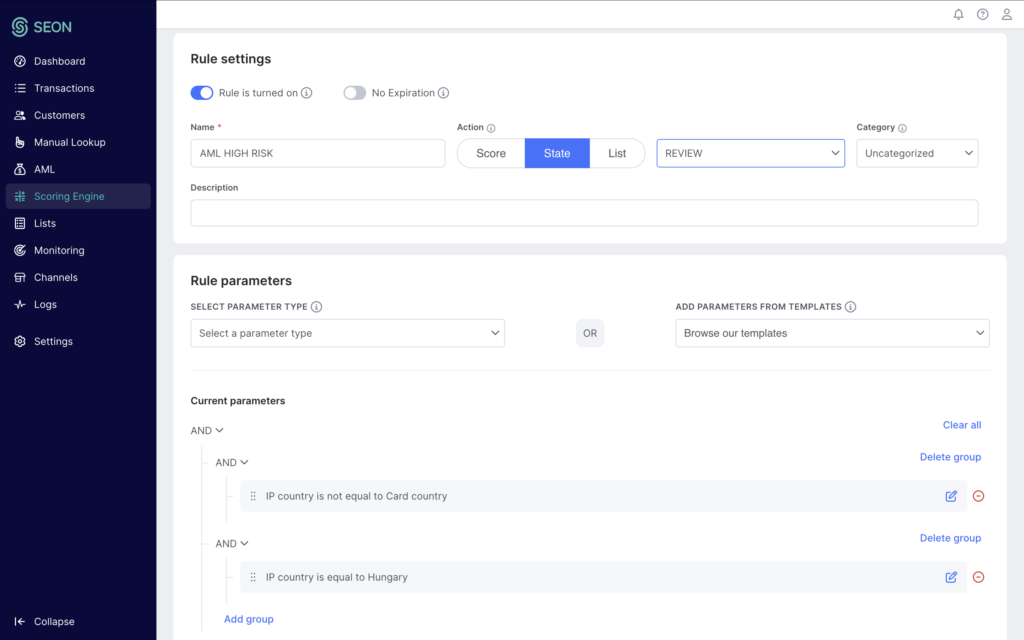
Setting Up a Rule for High-Risk Countries
To set up a rule using high-risk countries, you’ll want to:
- Define the high-risk countries by creating a custom list titled “High-Risk Countries.”
- Examine IP addresses and complete data for the IP country, adding those found on the international sanctions lists. Notice that SEON uses the country code.
- Create your rule and title it “IP country is AML HIGH RISK.”
This rule checks if a user’s IP is on the list of high-risk countries and, if so, will create a REVIEW alert that you can choose to automatically APPROVE or DECLINE the user’s transaction based on your risk appetite.
If it’s sent for manual review, your AML compliance team can check the transaction details for more information – or log the details to submit a Suspicious Activity Report (SAR).
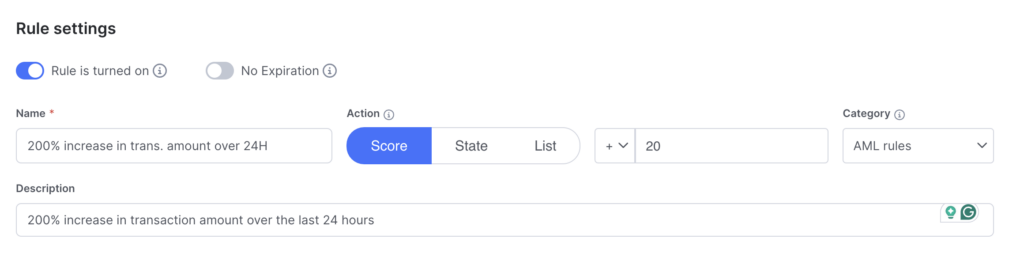
Setting Up Velocity Rules for Suspicious Transaction Behavior
Slightly more complex, velocity rules are designed to alert your team when a user suddenly increases their normal transaction volumes.
The velocity rule showcased here:
- Aggregates the amount of all transactions over 24 hours
- Looks for an increase in spending over 200%
Here is what it looks like on the dashboard when turning on the rule, setting parameters and once the rule has been triggered.
Transaction Monitoring: Key Takeaways
In AML, transaction monitoring is essential for safeguarding financial institutions and companies from being exploited for money laundering, ensuring compliance with regulations, and maintaining financial integrity. As fraudsters increasingly leverage advanced technologies and real-time digital payments, proactive oversight through transaction monitoring becomes crucial in detecting and preventing illicit activities.
Tools like SEON’s AML transaction monitoring empower your anti-fraud and money laundering prevention strategy by providing access to hundreds of user identity and transaction data points. These insights enable the creation of customized, flexible, and powerful rules to mitigate AML risks while also protecting against other types of fraud.
Automate AML: pre-KYC screening, checks, monitoring, alerts, and reporting — all in one real-time solution aligned with your SLAs.
Speak with an Expert
Related Articles of Transaction Monitoring Across Industries
- Digital Banking: Transaction Monitoring in Digital Banking
- Payments: Transaction Monitoring for Fraud and Payments
- iGaming: Transaction Monitoring in iGaming
- Retail: Transaction Monitoring in Online Retail
- Forex: Transaction Monitoring in Forex Trading
- Crypto: Transaction Monitoring in the Crypto Space
Frequently Asked Questions
AML transaction monitoring is a key part of national and international anti-money laundering strategy, which forces companies to examine transactions over a certain threshold. The transactions must be linked to someone’s identity to reduce the risk of money laundering.
Global AML regulations, such as the FATF Recommendations, the EU AML Directives, and the U.S. Bank Secrecy Act, require financial institutions to monitor transactions for suspicious activity. Failure to implement effective monitoring can result in significant penalties, including multimillion-dollar fines, regulatory sanctions and even criminal liability for compliance failures. Regulators like FinCEN, the European Banking Authority and the UK’s FCA actively enforce these obligations worldwide.
For banks and other fintech organizations, this works by having software monitor all transactions and flag all those that exceed a certain threshold for investigation, which often involves manual review. Additionally, the system ascertains that customers are not on PEP or sanctions lists. If anything seems suspicious after this, the bank ought to file a suspicious activity report (SAR).
The main challenges in the transaction monitoring process include high false positives that waste time and resources, constantly evolving fraud tactics that outpace static systems, complex and changing regulations across regions, and the need to balance strong security with a smooth customer experience. To overcome these, businesses must adopt automated, adaptive, and risk-based approaches for more accurate and efficient monitoring.
Payment screening is the process of vetting payments against watchlists before they enter the system, aiming to stop suspicious activity upfront. Transaction monitoring, on the other hand, is the process of continuously analyzing payments for unusual patterns that could signal financial crimes.
Sources
- UNODC: Money Laundering portal
- United Nations: Money Laundering
- Trading Economics: World Full Year GDP Growth