Just as your physical fingerprints are utterly unique combinations of loops, whorls, and arches, the web browser you use to connect to websites leaves its own distinct impression. However, instead of double loops and tented arches, browsers have personal markers like screen resolution, stored WebGL, and graphics card configurations. Just like hand-based fingerprints, these browser fingerprints can be tracked as they move around the world, regardless of how many cookies are cleared (or eaten).
Naturally, customers approaching your online marketplace can’t have their identity verified by taking their fingerprints and, frankly, doing so would probably be an overstep for, say, buying groceries. However, assessing the likelihood of risk in a browser fingerprint is much faster, and less invasive.
How do browser fingerprints work, and how do they improve your businesses operations and secure your bottom line? SEON explores.
What Is Browser Fingerprinting?
Quietly assessing the unique configuration of web browsers that connect to a web domain is a process called device fingerprinting. Naturally, the fingerprint being scrutinized is made up of more than simply the web browsing program, such as the installed languages, operating system, plugins, and in-browser time zone, among others.

Together, the sum of these attributes forms a highly — though not perfectly — unique identifier that can be used to both verify a returning user, as well as identify suspicious setups associated with fraud. For instance, browser fingerprinting may be able to detect when users rely on emulators or spoofing tools, which should increase your suspicions about their intentions on your website.
Most browser fingerprints will turn out to be unique, and two users with the same fingerprint will almost certainly be the same user on the same device. However, there is an unlikely possibility that multiple users connecting via mobile may have the exact same browser fingerprint, owing to the fact that people are less likely to make granular adjustments to their mobile browser settings. For this reason, device fingerprints shouldn’t be used as an identifying tool in a vacuum, and should be paired with other identifying data from the user to form a more reliable, holistic profile.
The last point to note is that browser fingerprinting is a somewhat contentious practice, which is why a number of privacy-advocacy groups have developed anti-tracking and anti-fingerprinting techniques and tools, though browser fingerprinting tools like SEON can detect these as well.
Which Data Is Collected?
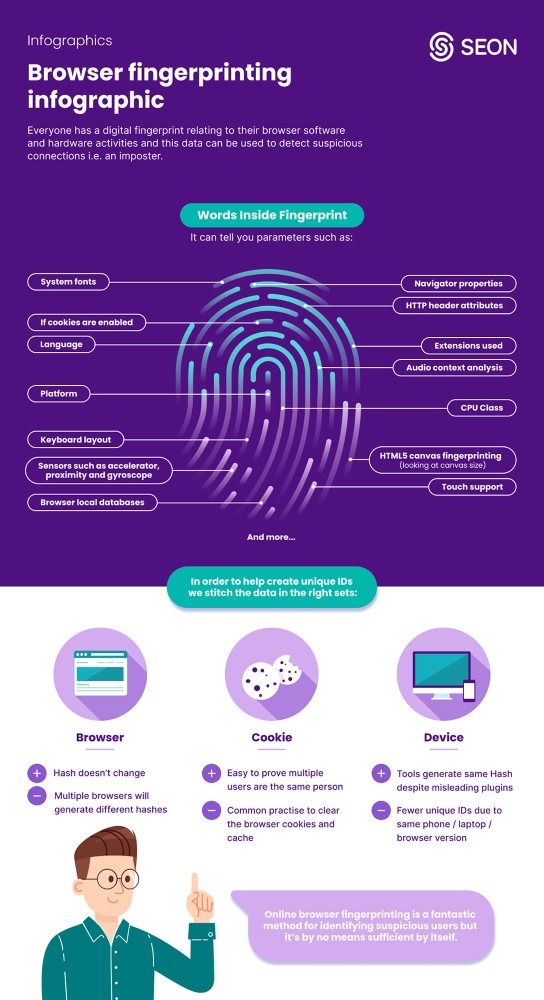
Browser fingerprinting tools gather user data relating to users’ software and hardware configurations, including:
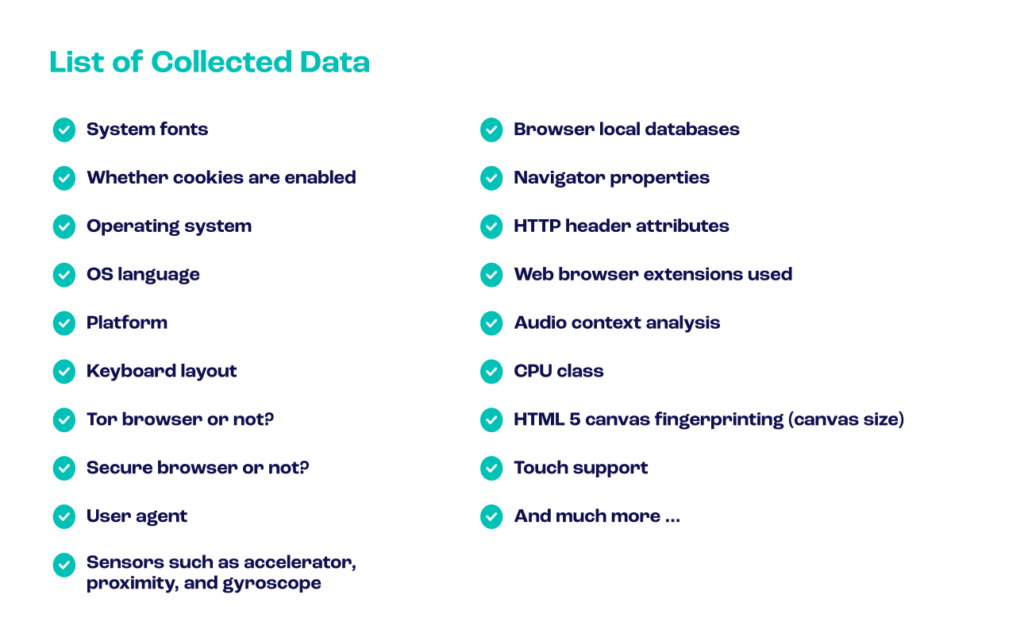
The above shows just how many parameters are taken into account to create a browser fingerprint.
Examples of Browser Fingerprinting
Browser fingerprinting in action is a quiet process, with software collating attributes of the connecting browser setup and developing them into a single identifying hash. This hash is informed by potentially dozens to hundreds of characteristics of a given browser.
In the sense that the goal of browser fingerprinting is to develop a unique identifying profile of a given user, no particular attribute is more important than another. That being said, there are certainly some attributes which are more closely associated with fraud than others, for example connecting via a browser that is designed specifically to circumvent existing fraud prevention platforms.
Other examples of data points within a browser fingerprint which often have a closer association with fraud include:
- Installed plugins, especially anti-fingerprinting extensions like AdBlocker Ultimate and Canvas Blocker.
- Unexpected browser version age can be associated with fraud, as some fraudsters will be exploiting security loopholes in browser versions that have since been patched.
- Unpopular screen resolutions, such as ones that appear too small in an un-modern way, may be indicative of multi-accounting from a single device, with a fraudster emulating multiple devices at once on the same physical screen.
- These unusual screen resolutions may be facilitated by a Virtual Machine (VM) environment, which will appear as an attribute in a browser fingerprint.
As well, particularly unusual configurations that may include the above should potentially be assigned a higher risk score. Though some users may just have particular preferences, very unusual configurations may turn out to be associated with bot attacks, with a single browser on a single machine orchestrating many profiles at once. Many browser fingerprinting tools allow for such rule customization, including SEON.
How Does Browser Fingerprinting Work?
Typically, browser fingerprinting is facilitated through a snippet of JavaScript code that gathers the data that is an inherent part of the connection process.

This data includes data openly shared as a requirement for connection, like user-agent strings and HTTP headers, which contains data about the browser type, version, and installed operating system. Installed browser plugins, which may be relinquishing other data points about the user on their own, also make themselves visible. JavaScript code can additionally pull data on screen settings, time zones, and languages.
Together, these data points all inform a holistic profile of a given user — their browser fingerprint. This fingerprint is anonymized by assigning it a hash, which effectively removes any identifying personal data from the profile while still providing a unique identifier. The generate has doesn’t change as long as the user connects on the same device, even if cookie caches are cleared. Any changes that browser fingerprinting software detects often begs manual review, to make sure the same user just happens to be connecting from a new device, and is not an instance of account takeover (ATO).
At SEON, beyond ATO detection, browser fingerprints are leveraged in different ways which have different fraud-fighting applications.
Browser Hash
Browser hashing generates an ID by looking at all browser fingerprint data points such as the user agent, operating system, windows, screen, font settings and more.
- Pros: The hash doesn’t change even if the user clears their cache and cookies or uses incognito mode.
- Cons: Multiple browsers (e.g. Edge, Chrome, and Firefox) on the same computer will generate different hashes. Even a browser update will force the creation of a new hash.
Cookie Hash
A new ID is created with each browser session.
- Pros: Easy to prove multiple users are the same person if they share the same cookie hash.
- Cons: Clearing the browser cookies and cache generates a new cache.
Device Hash
The ID is created based on hardware data such as the device type, HTML5 canvas, whether it allows touch support, and more.
- Pros: Unique ID based on the sum of the data points that relate to the device. Fraudster tools such as AntiDetect or FraudFox will generate the same hash, which can prove the use of a virtual machine, emulator or remote desktop connection. Plugins used to spoof a device will also generate a unique ID, which increases suspicion.
- Cons: There are far fewer unique IDs, as anyone with the same phone or laptop and browser version will generate the same hashes.
As you can see, it’s always better to combine all three hashes in order to get a better picture of who your users are. Legacy fraud detection methods only looked at the cookie hash or user agent, but fraudsters are now too savvy to be caught that way.
SEON is a powerful end-to-end solution that gives you complete control over the rules that affect your users’ fraud scores.
Ask an Expert
What Is Cross-Browser Fingerprinting?
While the standard browser fingerprinting is dependent on which browser the person uses, a method called cross-browser fingerprinting has allowed researchers to ID people based on hardware alone.
This development could have drastic consequences both for privacy-focused users and fraud prevention companies. Bear in mind, however, that several of the methods and innovations introduced by researchers in cross-browser fingerprinting have already been integrated into fingerprinting solutions. This includes some of SEON’s fingerprinting data points, which we continue to update.
Anti-Fraud Benefits of Browser Fingerprinting for Businesses
As a technology, browser fingerprinting can offer numerous benefits to businesses.

Identifying Users
Every user’s configuration of software and hardware is likely to be unique. This means you can essentially turn that configuration into a user ID.
Once you have identified the user, you can track their movements across your site. It’s also helpful to know when they are returning visitors.
Delivering Tailored Content
One of the key benefits of having a de facto user ID is that you can offer your users specific content. This could be geolocalized web pages, or redirecting them towards appropriate resources.
The same applies to targeted marketing. Once you know you are dealing with a loyal customer, you can send them unique offers such as bonuses, loyalty points, or special discounts.
Blocking Account Takeover (ATO) Attempts
ATO attacks happen when someone logs into an account that isn’t theirs. But if you’ve managed to create an ID for the original account holder, it becomes much easier to spot suspicious logins.
For instance, a new login from a previously unseen device and IP geolocation could increase your suspicions.
It’s worth noting that an efficient anti-fraud tool will not block all new device logins because sometimes, it will simply be someone logging from a new mobile device or computer. The key is that you should know when to ask for extra authentication, based on a combination of data points and what each means.
Spotting Connections Between Users
When the configurations for multiple users are similar, you can make an educated guess that you are dealing with the same person attempting a multi-accounting attack.
In the context of fraud prevention, this will allow you to prevent problems such as bonus abuse. iGaming companies and online casinos have an extra incentive to block collusive play between groups of players (or one person pretending to be multiple players).
Flag Suspicious Connections
Finally, a key use of this fingerprinting is to help reveal suspicious user configurations. That includes any kind of setup that points to:
- Emulators and spoofing tools: software designed to mask the real data and to replicate configurations from another setup.
- VPN, proxy, and Tor usage: software designed to hide the real IP address and to route the user’s traffic through another network.
Once again, these kinds of data points won’t always point to fraud. But you should be extra vigilant with these users.
The Shortcomings of Online Fingerprinting
While browser fingerprinting is a fantastic way to get an idea of who your web visitors are, it’s no magic bullet. Here are some reasons why:
Data Has a Short Shelf Life
This is an area we recommend fraud managers pay specific attention to. A lot of fraud companies pride themselves on their ability to track hundreds or thousands of online data points for browser fingerprinting.
But the ability to track more personal data isn’t always better, if it is stale. What is a much better and smarter approach is to find and enrich the fresh points with other fraud prevention modules in order to create a multi-layered fraud prevention solution to protect your business and users.
Fraudsters Are Savvy Enough
The very fact that specific software is designed to spoof devices, browsers and operating systems clearly shows that fraudsters have experience with online fingerprinting. They will try their best to manipulate the data to hide their real-world identity.
Of course, for the good guys, the fight is all about identifying these spoofing methods and setting up good tracking techniques. One example of this from recent years was when it was understood that a browser fingerprint of the size of the canvas can help to indicate fraud – because bad agents tend to resize their browsers to work on multiple platforms at once.
General Users Are More Concerned About Privacy
The rise of privacy-centered browsers such as Brave or Firefox shows that users don’t enjoy being tracked. These browsers and others, such as the latest version of Microsoft Edge, build privacy features into their code – for example, by disabling JavaScript, blocking tracking pixels and tracking cookies by default, or only allowing HTTPS.
There is also no shortage of anti-tracking options for general users, such as the Tor browser, NoScript (which blocks JavaScript everywhere), Ghostery (which lets you block and audit your browser fingerprint), or the dozens of ad-blocking tools that regularly top the list of the most downloaded extensions on any app store.
And while the general public isn’t necessarily tech-savvy enough to deploy the right tools, there is a general sense that data privacy is important and that tracking poses a threat. As reported by the Pew Research Center, 81% of US citizens believe they do not have enough power over how their data is tracked by companies. The same amount believes that the risks outweigh the benefits, which could see a rise in consumer tech designed to address these concerns.
Data Collection Must Be Acknowledged
There are data collection and privacy issues that should be raised with browser fingerprint and canvas fingerprinting tools.
This is why you have to make sure that your browser fingerprint solution is compliant with local laws and regulations. While it is a legal practice, you may need to acknowledge every digital fingerprint in your terms and conditions, as some visitors may wish to opt out (like with a cookie policy).
What is an Anti-Fingerprinting Browser?
It’s worth noting that every time risk managers deploy new browser fingerprinting features, organized fraudsters create tools designed to confuse them.
This is particularly evident with the rise of anti-fingerprinting browsers, or browser spoofing tools, which are deployed to emulate other configurations. Privacy advocates also recommend them to those who want to avoid targeted marketing or simply to reduce personal data collection.
8 Browser Fingerprinting Techniques for Fraud Prevention
Browser fingerprinting is a process, which means that several different tools can offer similar results. Let’s take a look at the standard features and see how they work.
Hashing
All the data returned from online fingerprinting is processed through a hash function. This is a long string of letters and numbers which processes data of arbitrary sizes into fixed-sized values. This makes it easier to log the information, encrypt, analyze and compare it.
For instance, SEON works with hundreds of parameters, but only three kinds of hashes: cookie hash, browser hash, and device hash.
Canvas Fingerprinting
Websites written in HTML5 contain a code element called the canvas. This element is used to draw graphics on a web page. It also generates data such as the font size or active background color setting, which come into play when creating a unique user ID for tracking. It is the most powerful feature of browser fingerprinting.
- HTML5 canvas fingerprinting detects: installed client fonts, browser font size, active background color, graphics card, operating system, and more…
The HTML5 fingerprint is used as a fraud prevention technique based on the fact that the same canvas image may be rendered differently on different computers.
WebGL Fingerprinting
Like the canvas element, WebGL is a JavaScript API that renders on-screen images and graphics. An image is rendered with a fixed size and, because different GPUs use different algorithms to display it, you can estimate the kind of graphics card your user has installed.
- A WebGL fingerprint detects: graphics card model, screen resolution…
User Agent Detection
A user agent, or UA, is part of the software designed to identify a browser with the website. It is a string which, when detected by a site, can display tailored content for specific browsers.
There are a few caveats to user agent detection, all related to how this data point is used in the real world. Firstly, web developers often rely on user-agent switching tools to visualize how a site will look on a variety of devices. Fraudsters use the same type of tool to spoof a browser. Default Android web browsers use the same user agents as Safari to make compatibility easier. Google is also depreciating user agents in its Chrome browser.
Still, user agent detection is an integral part of browser fingerprinting and remains useful when considered in tandem with other elements.
- User agent detection reveals: browser name, version or version number
Audio Fingerprinting
Producing sound from a mobile browser and device audio stack is surprisingly complex. In audio fingerprinting, a website uses the AudioContext API to send a low-frequency sound through the browser to the device, and measures how the device processes that data. This helps inform how to process audio – but no audio is recorded, collected, or played, so you don’t need microphone and speaker access. And yet, this technique can inform fingerprinting with multiple parameters and values.
- Audio fingerprinting detects: AudioBuffer value, DynamicsCompressor value…
Device Fingerprinting
Companies who create mobile apps specifically for smartphone OS can use a specific SDK (software development kit) to get extra information about devices, whether they are built by Apple, Samsung or other vendors.
- Such mobile device fingerprinting products detect: MAC address, serial number (Android only), device time zone, battery health, CPU details…
Tor Detection
By default, Tor makes each user have the exact same fingerprint. This ensures companies lack Tor fingerprinting information, ultimately providing fraudsters anonymity from basic anti-fraud solutions.
However, Tor detection works by running a test to see if the user’s IP matches a known Tor exit node, thus determining whether a user is running Tor. While a Tor user might not have any malicious intent, Tor users should be flagged as high risk by default due to the statistically higher likelihood of fraudulent activity.
Selenium Detection
Selenium is an open-source tool that automates browsers, which was originally intended to help with web application testing. Selenium is very easy to set up and allows users to run scripted actions in a distributed manner.
Though it is a useful tool for developers, it’s also the tool of choice for malicious actors who would want to scrape your website – e.g. ticket scalpers. Unfortunately, these people are incentivized to hide what they’re doing, and you need to be proactive in catching them.
While Selenium itself is difficult to detect, you can use JavaScript to check for evidence of WebDriver, the technology behind it. In fact, our upcoming rule update will automatically flag browsers that are automated as risky, allowing you to block bot traffic and service abuse.
How SEON Does Browser Fingerprinting
At SEON, we were very lucky to develop our browser fingerprint module with Gábor Gulyás, a pioneer of device fingerprinting. His expertise helped us create browser fingerprinting based on hundreds of parameters. However, we also recommend combining our module with other fraud detection features, such as:
- Social media lookup, which gathers data from social networks to enrich your understanding of the people on your site
- Reverse phone/email lookup to enrich data and create a better online digital footprint analysis
- IP analysis and proxy detection to ensure you understand more about connections between visitors
- Machine learning, the only engine powerful enough to look at all the data at scale and suggest risk rules tailored to your business model
All the browser fingerprinting modules are accessible as part of the SEON platform, designed by anti-fraud experts for businesses in any vertical. To see how we help reduce the costs and resources lost to fraud by 70–80% without sacrificing user experience, try a free demo with SEON.
Explore the benefits of using SEON’s advanced browser fingerprinting technology to spot fraudsters easily, helping you focus on what matters while staying safe.
Learn more
Frequently Asked Questions
A range of industries across ad tech, fintech, and fraud prevention rely on browser fingerprinting to understand more about their customers.
Browser fingerprinting analyzes any given user’s software and hardware configuration, which in turn creates unique IDs that can be used to highlight suspicious behavior. It can help spot a range of potentially fraudulent activities including synthetic IDs, identity theft, CNP fraud, phishing, spoofing, account takeover, and affiliate fraud.
Yes, browser fingerprinting is legal as all the information collected is considered public and does not include any personal data. However, one should note that the fraud solution that collects the data should be compliant with all applicable legislation. For instance, SEON is fully GDPR compliant and ISO-27001 certified.
You might also be interested in reading about…
- SEON: Best Fraud Prevention Software and Tools: Reviews in 2024
- SEON: Reverse Email Lookup: How It Works & How to Perform It
Learn more about:
Device Fingerprinting | Device Intelligence | Digital Footprinting | Fraud Scoring
External Sources
- Cover Your Tracks: About Us
- Pew Research Center: Americans and Privacy: Concerned, Confused and Feeling Lack of Control Over Their Personal Information
- Tom’s Guide: The best ad blockers in 2021
- Tor Project: Changes to the Tor Exit List Service