As the world and its underlying systems move online, businesses find that the anonymous nature of the internet is at odds with safety and security.
They need to verify identities.
Regulators agree. Here’s why you need automated identity verification.
What Is Automated Identity Verification?
Automated identity verification is a process designed to let online businesses verify their users’ identities. The automation part is done via software. There are numerous methods to verify identities, such as biometrics, document verification, or digital footprint analysis.
The identity verification process is useful at several stages of the customer journey:
| Onboarding and signup | When new users register on your website, platform, or app. |
| Transactions | You might want to ensure the payment information is tied to the right person, whether it’s when paying for something, depositing money, or withdrawing it. |
| Logging in | It’s helpful to ensure the right person is accessing their account. At this stage, identification becomes synonymous with authentication, but the idea is the same: to confirm who is online and using your services. |
More importantly, automating the process allows companies to accept new signups, payments, and logins at scale – that is to say, without having to review each action manually.
This allows for creating growth and streamlining of operations.
Learn how Soft2Bet automated risk reviews to free up resources, accelerate manual checks, and improve its efficiency with SEON.
See Case Study
Why Is Identity Proofing Important?
For some businesses, identity verification is part of a risk management strategy. For others, it’s a regulatory requirement. Let’s look at the most common scenarios where it’s needed.
- Meet KYC regulations: While historically KYC compliance was only needed for financial institutions, these days, a growing number of verticals are legally required to know who they’re doing business with.
- Avoid fines and legal issues: A direct consequence of the point above is that if you were to fail to meet the requirements, you could be liable for hefty fines, or worse. For example, if found to be inadvertently assisting money launderers by not running adequate checks, staff could even be imprisoned.
- Reduce fraud: If you accept registrations or payments on your website, you’re likely to have to deal with fraudsters and criminals. Verifying user identities is a way to mitigate that risk, whether it’s to avoid chargeback fraud and bad loan applications, or even to ensure your marketing dollars aren’t wasted on junk users.
- Protect user accounts: Verifying identities at the login stage, which is an authentication technique, can be a great way to ensure none of your users’ accounts are stolen by fraudsters. This is called an account takeover though your users may refer to it as account hacking. Either way, it’s damaging to your business reputation and even your bottom line.
The Pros and Cons of Automated Identity Verification
If automated identity verification is so important, how come not every business deploys it willingly? Well, there are pros and cons, as we’ll see in detail here.
Automated IDV Pros
- Safer business: Automated identity proofing helps reduce risk. This secures your business, improves your risk management strategy, and makes you more competitive.
- No need for manual reviews: Automation is the keyword here, as it passes the burden of validating identities from your manual review team directly to the software. As a result, automated ID verification can work 24/7 and at scale.
- Log more data for compliance: Automated IDV often gathers extra data to work. Such data is helpful when you want to create logs and reports, which is handy when filing, say, a suspicious activity report or a chargeback recovery dispute.
- Easy integration: Connecting any kind of software to your business data used to be a complex affair. These days, you can deploy automated identity verification via API, which is a much more seamless process.
Automated IDV Cons
- False positives: One of the most frustrating experiences is when an identity verification system doesn’t recognize a legitimate customer. This is the surest way to create churn and send your customer toward your competitors.
- High friction: The amount of friction required to clear an automated verification system varies depending on the technique you use, but one thing is for certain: It’s never an obstacle-free affair. In fact, some IDV systems can be so time-consuming for your customers that they’re likely to cancel their actions.
- Can be expensive: Here again, the price varies from one technique to the other, but some of the more complex identity verification solutions can be pricey. You could be looking at up $3 per KYC check with a full-fledged video selfie identification tool, for instance.
- Still requires manual labor: You’ll have to consider the integration (developer time), the deployment (risk management team), and even support for customers whose identity verification failed.
5 Types of Automated Identity Verification Tools
Not all automated identity verification solutions are created equal. Let’s explore five of the most popular solutions you may want to investigate, including biometrics, digital footprints and even blockchain ledgers.
1. ID Selfie Video Verification
We’re all pretty familiar with document video verification by now. The automated software scans your ID and takes a photo or a video of you. It compares the data with that found on official government databases and returns positive or negative results.
This is no easy feat. This kind of automated verification software must scan through a global network of document verification services, which is why it can take a little while. This method is also very high friction. The customer must first find the right documents and wait for the verification process to be completed – not to mention any potential technical difficulties that may arise.
There’s also the issue of stolen ID documents and tech-savvy fraudsters. Selfies are fooled by deepfakes, and paper documents are easy to falsify (or buy from photoshopping services).
2. Biometrics Verification
Biometric verification is designed to be foolproof. A quick fingerprint scan or face ID check, and you’re good to go. But there’s a catch: Biometrics work great for authentication but not as well for identification.
That is to say, if you are going to ask your customers to submit biometric data, you still need to be able to check it against an official database. There is a push, however, to let people reuse their biometrics information to sign up for multiple services, which can save time, effort, and friction for legitimate customers while making life harder for identity thieves.
Also, despite bold claims from the industry, depending on the type of biometric verification deployed, there can be some friction, both in practice and in principle. For example, not everyone feels comfortable showing their face or having their unique fingerprint shared with a private company.
3. Digital Footprint Analysis
A digital footprint is the closest thing we have to online profiling. This is about getting clues about who the person is based on the kind of digital life they live – starting with their email address or phone number. Information of this type may come from online records of past sightings of their email address, data breaches, or the kind of social media networks they have registered to.
It’s like playing data detective. You start with basic information such as an email address, phone number or IP address, and you cross-link the information to get more clues.
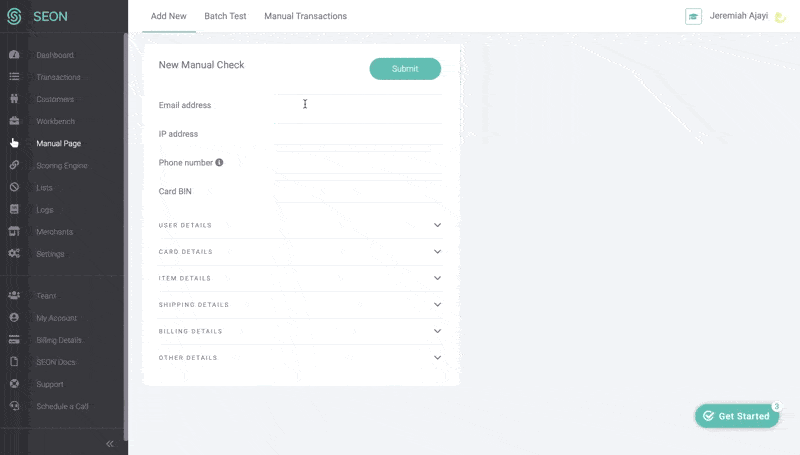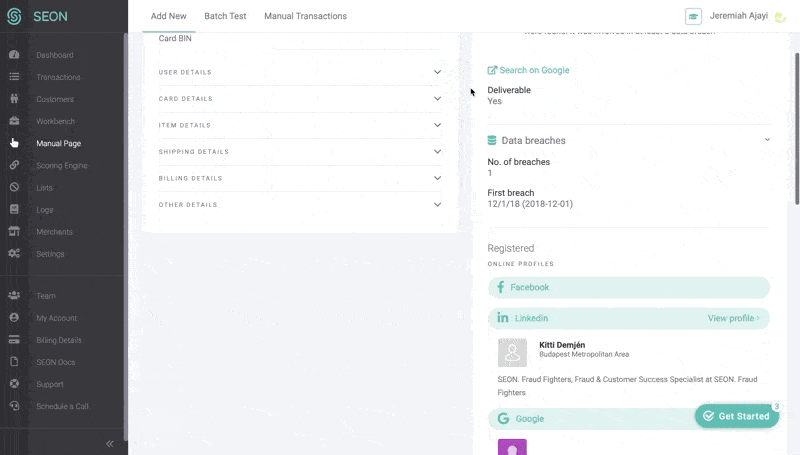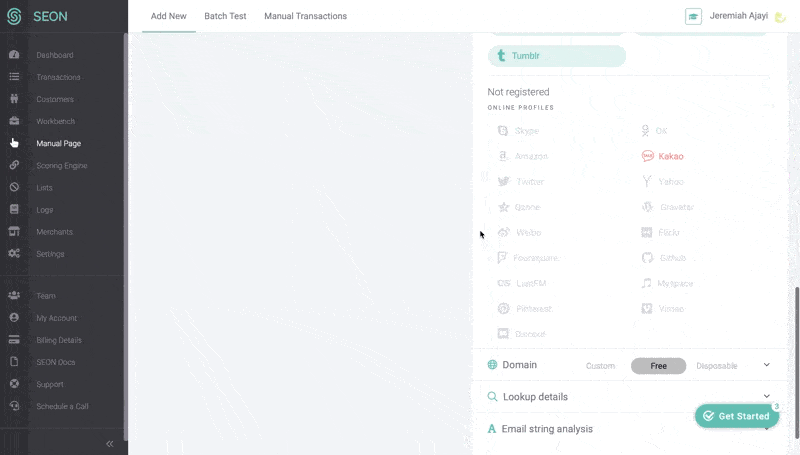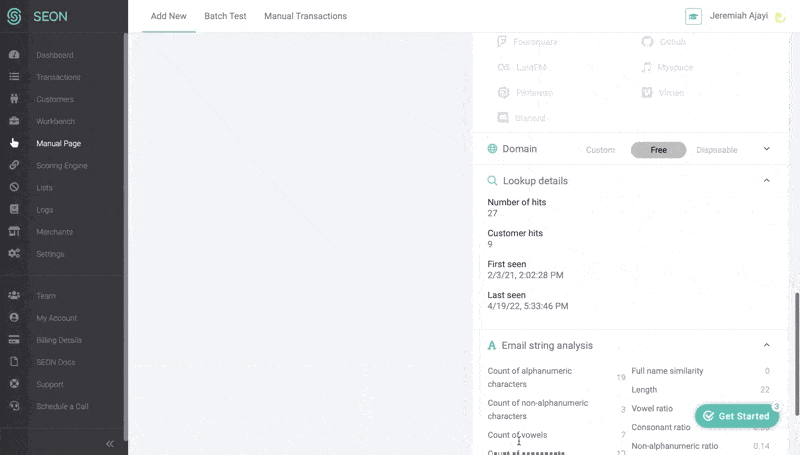
With SEON, that information can be checked against 90+ to get an idea of whether the person appears to have online history. An absence of online social and other profiles should be considered high-risk.
Note, however, that digital footprint analysis is a pre-KYC filter and cannot fully cover KYC compliance. You can filter out users who are definitely not who they say they are. It’s not possible to authenticate people based on their digital footprint alone, but you can certainly flag high-risk customers with it.
4. Behavior Analysis
Analyzing a user’s behavior on your domain is not an exact science, and you’re not likely to guess who someone is by monitoring how they use your service. Behavioral analysis is, however, increasingly helpful in filtering out fraudulent users – especially bots and other automated software.
By checking how a user interacts with your online website or app, you get to see if they appear legitimate or not. For instance, someone who goes through a 5-minute onboarding process in 10 seconds could raise red flags.
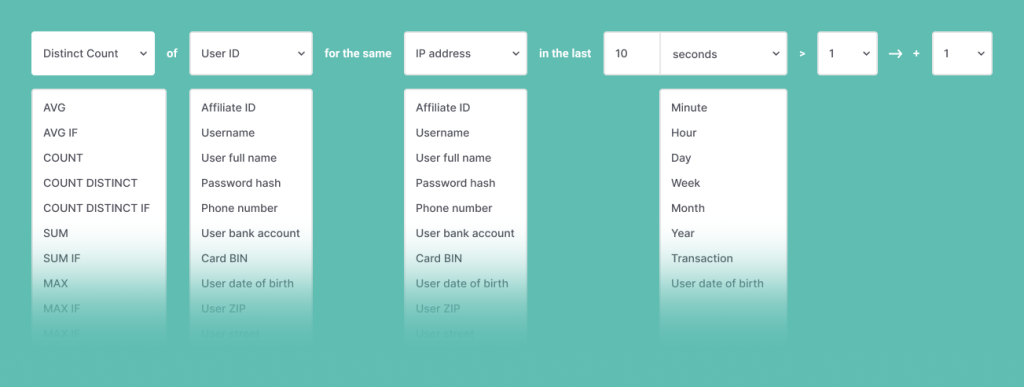
In fraud prevention, most behavior analysis is done via velocity checks, which look at user actions over a specific time frame.
5. Blockchain KYC
Turning your identity into an anonymized token on a specific blockchain isn’t as far-fetched as it sounds. In fact, even the banking giant HSBC pioneered a trial of the method in the UAE with great success.
The idea is simple but technically complex. An individual goes through an initial identity verification process. If successful, they get a KYC certificate, which is tokenized and accessible on a specific blockchain. This is unique to the person but not the company, so the individual can choose to share it with organizations, or not.
Companies can then integrate the KYC service, and it will ensure that every new signup is associated with the correct KYC data.
While this method has plenty of potential benefits, it’s also a work in progress, and not scaleable enough to be a fully reliable identity verification method yet.
Partner with SEON to reduce fraud in your business with real-time data enrichment, whitebox machine learning, and advanced APIs.
Ask an Expert
How SEON Helps With Automated Identity Verification
As a fraud prevention solution, SEON isn’t a full identity verification software. It cannot check official documentation, for example. However, SEON is a perfect way to:
- augment your existing identity verification strategy
- perform pre-KYC checks to save on costs and resources
- score customers as low, medium or high-risk
- authenticate users at login
- analyze user behavior to flag suspicious actions
All of this is based on fast, frictionless data enrichment and risk scoring, designed to give you all the information you need to run an online business with complete peace of mind.
SEON is flexible and granular. It can be used as a set-and-forget solution to supercharge automated ID verification or fully customized to suit a company’s risk appetite and fraud environment.
FAQ
When it comes to online users, you can verify identities by running ID verification checks with third-party providers. You can also manually check official government databases. Some companies prefer to confirm if someone is a real user or not by looking at their digital data.
To perform faster identity checks and at scale, you need to automate them with specific software. There is a plethora of automated identity verification tools designed to integrate with your business data to confirm IDs at the signup stage.
An electronic identity check, or eIDV, is a computerized system designed to verify identities. It uses both private and public sources to confirm online users’ identities.