As Card Not Present fraud continues to hurt the payment ecosystem including merchants, issuers, and acquirers, we wanted to offer some suggestions on what actions your business can take to reduce it today.
The core of the problem with card not present fraud (CNP) can be explained in one simple question: How do you prove that cardholders are who they say they are?
It’s not an easy task, and it’s what makes them so risky. Sadly, card not present fraud continues to be an expensive affair, set to cost issuers, merchants, and acquirers an estimated $34.66B by 2022.
Luckily, it’s a plague everyone is working together to fight. And there’s actually a lot you could do, as an online business, to reduce CNP (and card-present) fraud yourself today.
What Is Card Not Present (CNP) Fraud?
In short, CNP fraud is described as a fraudulent payment/scam without consent of the correct card owner. Most common forms and techniques with CNP fraud include:
- online sales
- mobile sales
- telephone transactions
- skimming and testing
Since the merchant is unable to physically confirm if the person is in fact who they say they are, as the purchase was made via an online transaction, it’s important to gather much information on your customers to mitigate risk.
CNP fraud prevention works by gathering user data, analyzing user behavior, and highlighting suspicious cards not present transaction information. This info should be enriched using IP address analysis, device fingerprinting, and social media lookup.
How Does Card Not Present Fraud Work?
CNP fraud takes place whenever a fraudster acquires some form of payment information, such as a credit card number, a person’s name, address details, or the 3 digit security number on the back, to then purchase products.
Nowadays fraudsters can easily purchase ‘fullz’ where complete stolen profiles are uncovered through data breaches or phishing attacks and can be purchased via the dark web.
In most instances, liability for fraudulent CNP transactions falls onto the merchant whereby chargebacks are a common sight as the victim often only reacts once it’s spotted.
Payment fraud prevention is the key to safer and healthier business growth. We take a look at what systems must be in place for it to work.
Read About It Here
10 Tips for Card Not Present Fraud Prevention
Since the majority of the time liability falls on the merchant, payment service provider, or the victim’s bank, it’s vital to understand the best ways to protect your business from CNP fraud. Modern solutions have been developed to help you spot the true customer or the fraudster.
Collect All the Customer Info You Can
Generally speaking, the more customer info you have, the better. This is true in the context of credit card fraud detection, but also marketing and sales, and card processing. Upselling, cross-selling and good segmentation can be improved thanks to the same info that allows you to validate user IDs, or to dispute a chargeback.
As to the kind of content you should gather, the bare minimum would be:
- Email address
- Credit card info including CVV code
- Billing address
- Information about the device used to log in
- IP address
- Phone number
Now you have three main touchpoints to gather that information: account registration, login or at the point where you take credit card payments.
And while it’s your duty to follow the best SCA practices, there’s a lot more info you can collect. User devices, phone numbers or email addresses can go a long way in filtering out bad agents – or at least prove they’re risky users, as we’ll see later.
- Why it works: The more knowledge you have about a user, the easier it can be to refuse suspicious payments that could be clear cases of card not present fraud.
- Main challenge: Collecting information without creating too much friction for the user, which can hurt conversions and sales.
Use Data Enrichment
If you read the first tip and wondered: How do I collect extra info without creating friction? The answer is data enrichment. It’s no wonder these tools are used by everyone from ecommerce to financial institutions these days.
Put simply, it is a process that takes single data points and uses them to aggregate info from external sources. For instance, an account email address is analyzed and found to be used for registration with social media profiles. Likewise, you take a phone number and see if it’s a landline or cell phone, and in which country.
All that info helps detect suspicious discrepancies. And best of all, it can be done pretty much instantly, and without asking the users for extra authentication steps if you use the right tools.
- Why it works: Data enrichment can be invisible to the cardholder, which helps you reduce danger without creating too many obstacles for the right customers.
- Main challenge: Enriching data from sources that make sense, and from fresh, open-source datasets. For instance, by linking an email address to the user’s connected social media accounts in use, which should be done by meeting GDPR requirements.
Follow the Best Data Protection Practices
Even though the customer isn’t standing in front of you, it’s still your job to protect their credit information. At least that’s what PCI Data Security Standard (PCI DSS) says, and it’s mostly to protect every merchant from potential CNP fraud attempts (and card-present too).
In practice, that means using online security tools like SSL, especially on pages that collect sensitive information such as credit cards, social security numbers, or addresses. You should also encrypt data as efficiently as possible, whether it’s shared between your customers and website, or between staff members.
- Why it works: Data that’s encrypted and safeguarded is less likely to fall into the wrong hands, which reduces fraud as a whole.
- Main challenge: Managing backup copies and configuring protection software and hardware can be costly due to rapid growth. It’s the #1 most cited challenge by industry experts.
Check Unusual Behaviour
Hopefully by now, you have enough information to start gathering insights about user behavior. While what is considered fishy can differ from one merchant or payment processor to the next, there are a few general red flags to keep an eye for, perfectly exemplified in the graphic below:
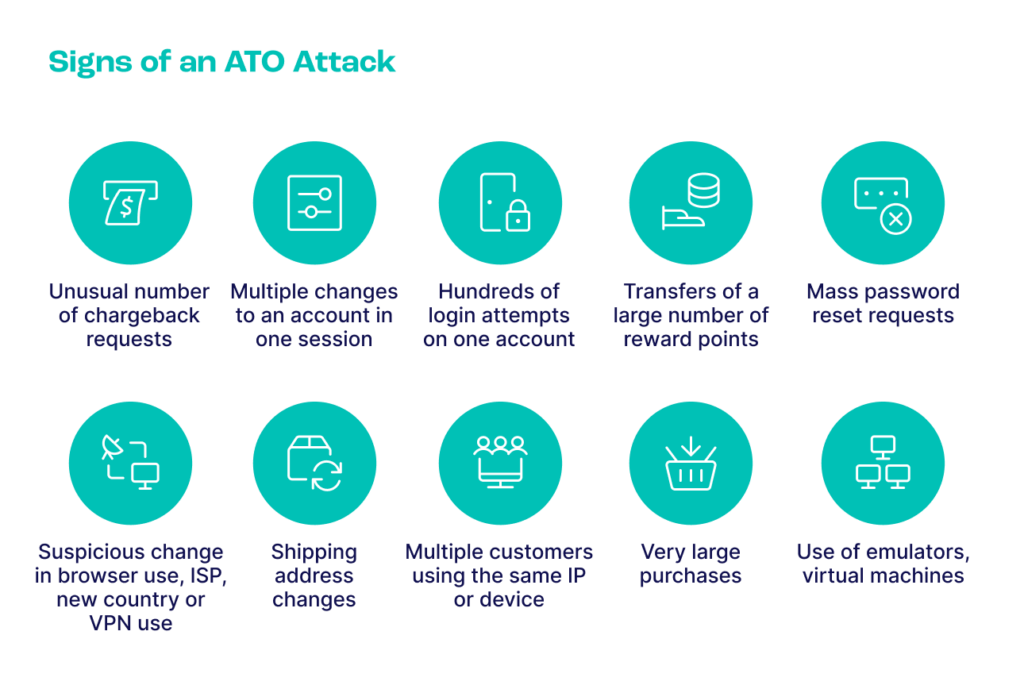
- Why it works: Fraudsters often try to work fast, and use multiple stolen card details in a row to maximize how much they can extract. This means their behaviour follows certain patterns that point to digital fraud.
- Main challenge: Analyzing behaviour is very difficult to do without a proper risk management solution in place as the merchant needs it to be done in real time.
Look Out for Very Small Transactions
Not all the fraudulent payments made to your business will impact you directly. Sometimes, fraudsters will use you to “test a card”, usually by purchasing inexpensive items or services.
Of course, if the transaction goes through, fraudsters could very well use the same stolen card to purchase more expensive items, which will damage your business eventually.
- Why it works: Identifying card testing as soon as possible can help prevent fraudsters from using stolen card details for larger transactions.
- Main challenge: Keeping an eye on small transactions that would otherwise go under the radar.
Analyze Gift Cards
Gift card fraud is often a problem that goes hand in hand with CNP fraud. Individuals looking to quickly turn stolen products into cash will often activate gift cards using stolen payment details, then sell these digitally delivered funds on an open marketplace within minutes.
If your company has a loyalty program or offers gift cards as a product (or payment method) it helps to be extra vigilant there.
- Why it works: Adding an extra hurdle for fraudsters who want to perform gift card fraud can help reduce card not present fraud too.
- Main challenge: Offering enough payment channels and loyalty programmes without suffering from bonus abuse.
Ask for Extra Authentication
At this stage, you should have all the insights you need to segment users based on how risky they are. So it’s time to reduce the risk by asking for extra authentication details.
At SEON, we like to call it light and heavy KYC. And our management system is adept at only triggering the heavy authentication methods based on your own thresholds. That means that legitimate users will be able to purchase with as little friction as possible, while potential CNP and card present fraudsters will have a harder time going through the hoops.
In practice, you’ll be looking at first enabling light KYC tools like email analysis, IP analysis, or device fingerprinting, amongst others.
If you find enough red flags to be worried, you can then trigger additional authentication measures such as ID verification, 2FA or credit card preauthorization.
- Why it works: You keep your customers happy, and discourage card not present fraudsters by letting them know they are suspicious.
- Main challenge: Once again, it can be hard to automate adaptable KYC at scale without the right system.
Dispute Chargebacks
One aspect of card not present fraud we haven’t really covered yet is the problem of friendly fraud. As you may already know, there’s nothing friendly about it. Card not present transactions that could damage your business occur when:
- Customers change their mind about a purchase and claim it was fraudulent
- Use their real card to try and scam the system by claiming a chargeback
- Family members are processing payments on the card without authorization
The takeaway here is that the chargeback is clearly the customer’s fault. And believe it or not, issuers and banks are actually quite good at siding with businesses, if you have all the right data to back up your claim (which goes back to my tip #1 and #2).
So what can you do armed with enriched data? Well, for instance, one of our clients uses our social media analysis tool. They found that some customers claimed they’d never received the product, and discovered social media posts of them showing the very same product off online. Talk about getting caught red-handed.
- Why it works: If you have the right info at hand, it can be easier than you think to win a chargeback dispute, which can be considered friendly fraud.
- Main challenge: Collecting the right data at the right time.
Look into Velocity Rules
The last two tips are more technically advanced, and I don’t imagine you’d be able to do it without a complete end-to-end solution.
So if your system allows it, I would highly recommend looking at velocity rules. These are rules for calculating risks such as transaction fraud that look at connections and combinations of points happening during a set timeframe, such as:
- Shipping address connected to multiple different cards in a short period of time
- High number of transactions on the same card
- High order value and fastest shipping method
- High priced items orders during the day…
So it is a kind of behaviour profiling, and a highly efficient one at that.
- Why it works: Another way of profiling CNP fraudsters behaviour, without creating friction for legitimate users.
- Main challenge: The number of combinations of velocity rules is virtually infinite, so you need to refine your search (or let an AI system help) to extract good parameters.
Build Risk Scoreboards
Reducing card present and card not present fraud is all about calculating risk and setting your thresholds. So sometimes you need to have enough data on fraudsters to be able to predict who will be a bad customer.
One convenient way to do it is through risk scoreboards, which allow you to cluster users based on similar data, behavior and risk score.
These scoreboards, which use statistical models, can vary greatly in complexity, so I won’t go into too many technical details here. But whether you do it manually or use an automated solution, scoreboards are a fantastic way to detect fraud, and therefore reduce potential damage.
- Why it works: Creating risk models helps extract insights about bad users and detect fraud before it can happen.
- Main challenge: Risk scoreboards are complex statistical models that can be hard to create manually.
Solutions for Card Not Present Fraud
For businesses, there are a range of fraud prevention products available to integrate into your business, whether you require a full end-to-end system or individual modules.
Ideally, you want to cover the 10 points above but it’s also worth considering if you need to further protective measures such as biometrics, captcha or one time passwords.
A device fingerprinting module will enable your fraud manager to analyze the hardware and software of a person visiting/transacting on your website.
Device fingerprinting pulls thousands of usable data points to spot potentially malicious actors, some of those parameters include:
- IP address
- HTTP request headers
- Plugins or fonts
- Operating system
- VPN and browser information
- Time zone and language
- User agents
- And much more..
Understanding as much as you can about any user and not taking advantage of all available data / overlooking siloed data will be a sure way to miss CNP fraud.
Card Not Present (CNP) Transaction: Do It Right
Like with many other types of fraud, the best way to improve your CNP transactions is to be prepared, well-equipped, and knowledgeable. This is true whether you use a full end-to-end fraud prevention system or multiple layers of protection via different tools.
Simplifying data enrichment for small businesses is also something we’ve been thinking about a lot at SEON. This is why we even created a tool that gives you complete flexibility by working as a one-click data enrichment solution: our Extension for Google Chrome.
It’s designed to speed up data enrichment based on email addresses, phone numbers or IP addresses, so you can start reducing CNP fraud in one click today.
Partner with SEON to reduce fraud rates in your business with real time data enrichment and advanced APIs
Ask an Expert
Frequently Asked Questions
In most cases it will fall on the merchant however depending on the security setup it can also cost the payment service provider or bank.
Very common. In the US alone it’s predicted that CNP fraud costs consumers and businesses upwards of $10bn.
The best way of ensuring protection would be using some form of multi-factor authentication.
You might also be interested in reading about:
Learn more about:
Device Fingerprinting | Browser Fingerprinting | Fraud Detection API
Sources used for this article
- Payments Journal: A Smart Solution to Manage Card Fraud
- PCI Security Council: Protect your business. Secure your payment data
- Tech Republic: Data protection: Top 3 business challenges