The rise of online transactions and evolving cybercrime tactics highlight the urgent need for strong identity risk management and monitoring. Identity theft presents significant challenges to businesses, making proactive risk mitigation essential for regulatory compliance, trust, asset protection, and operational integrity.
Identity risk management encompasses a spectrum of measures to fortify defenses against activities that exploit personal identity information (PII). It prevents issues such as payment fraud, account fraud (and misuse), loan fraud, and conducting business with high-risk individuals, as well as a stipulated practice for anti-money laundering (AML) compliance. With the stakes high, understanding the complexities of identity fraud and adopting industry best practices is necessary to protect customers in an increasingly digitized world.
Understanding Identity Risk Management Fundamentals
Principles for identity risk management vary depending on the context and industry. Still, the pursuit can be defined as endeavors that ensure secure and reliable digital identity management, including preventing unauthorized access to sensitive information, such as login credentials, PII and financial information. A critical aspect of cybersecurity, the fundamentals within this realm center on three main components: identifying, assessing and mitigating risks associated with digital identities and access controls across an organization.
Why Cybersecurity Teams Need to Implement a Risk Management System
A rise in identity theft incidents, with a 257% increase in the past decade yielding 1.10 million reported cases in 20231 alone, showcases the urgent need for risk management systems within cybersecurity protocols. Credit card fraud accounted for 34% of these statistics, indicating fraud’s pervasive and industry-agnostic nature.
Cybercriminals often employ sophisticated tactics, such as synthetic identities, account takeovers (ATOs) and exploiting unsuspecting individuals through socially engineered schemes. These tactics pose a significant threat, potentially leading to infiltration into financial systems or other mission-critical data, compromising sensitive information and causing economic losses. By adopting proactive measures such as continuous monitoring, real-time analytics, and comprehensive risk assessment protocols, organizations can layer their defenses against identity-related threats.
How to Conduct a Thorough Identity Risk Assessment
Each organization’s journey demands a meticulous understanding of its vulnerabilities and risks. The following details a five-step process.
Risk Identification
The initial phase in managing identity risk is identifying potential threats associated with identity verification, access privileges and entitlements. This step entails collecting thorough data on user accounts, roles and access rights throughout the IT infrastructure to pinpoint vulnerabilities—such as excessive permissions, inadequate authentication controls and deficient separation of duties that may result in compromised accounts or unauthorized access.
Risk Assessment
The next step is to assess and prioritize identified risks based on their potential impact and probability of occurrence. This process includes evaluating the criticality of assets and data vulnerable to identity-related risks and scoring and ranking risks through methodologies such as risk matrices or quantitative risk analysis models. Factors like regulatory compliance obligations and the potential financial or reputational repercussions are also considered during this assessment.
Risk Mitigation
Once risks have been prioritized, the subsequent step involves implementing effective mitigation strategies that span a range of actions to strengthen security measures. Firstly, organizations can bolster their defenses by implementing preventive controls, like enforcing robust authentication protocols, limiting access privileges through ‘least privilege’ principles, and conducting regular entitlement reviews to curtail attack surfaces. Additionally, deploying detective controls – including implementing user activity monitoring systems, real-time policy violation alerts and anomaly detection mechanisms – becomes imperative to proactively identify and thwart potential threats.
Incident Response & Remediation Processes
Establishing robust incident response and remediation processes is essential to swiftly address identified risks or security incidents. Organizations can effectively mitigate the impact of security breaches and safeguard their assets by defining clear procedures for incident detection, containment, eradication and recovery.
Continuous Monitoring & Adaptation
Identity risk management constitutes a dynamic and continuous process necessitating vigilance and adaptability to counter emerging threats and accommodate environmental shifts. This involves periodic reassessment of risks to incorporate new vulnerabilities, technologies or changing business needs.
Real-time monitoring and analytics swiftly detect changes in user behavior or risk profiles, enabling prompt control adjustments. Employee training on identity risk management best practices strengthens organizational defenses. Integrating people, processes, and technology ensures effective identity risk management, fortifying cybersecurity, protecting assets, and maintaining regulatory compliance.
3 Technological Innovations to Mitigating Identity Risks
In today’s digital-heavy era, addressing identity-related risks requires better technology. As organizations strive to protect sensitive information and maintain trust, three technological innovations – digital footprinting, device intelligence and AI-powered insights – are revolutionizing identity risk management, providing robust tools to detect, prevent and respond to fraudulent activities with unprecedented precision and agility.
Digital Footprinting
Digital footprinting offers organizations profound insights into verifying the veracity and validity of an account by looking at an individual’s online behavior and activities through available public information. It aggregates and analyzes a wealth of data, including social media profiles, browsing history, online purchases, communication patterns and other signals, to provide a comprehensive view of digital presence. Through related account information, such as past data breaches and IP address data, the narrative of legitimacy shines through connected and related accounts, while fake accounts, created quickly and at scale, stand out. Integrating digital footprint analysis into identity risk management allows organizations to identify potential threats and vulnerabilities.
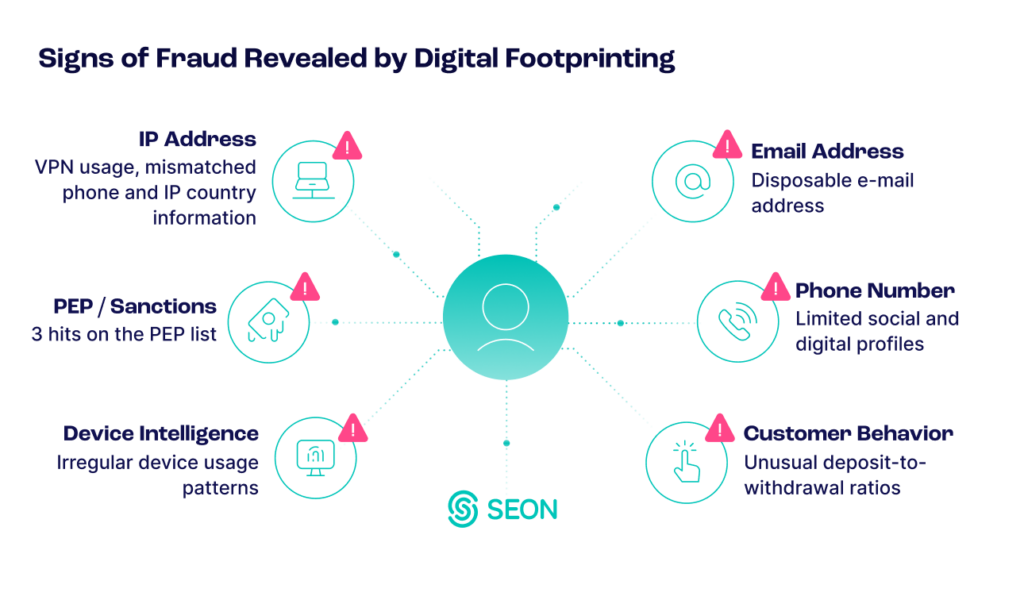
For instance, by refining authentication processes, organizations can enhance accuracy in verifying users’ identities through cross-referencing information with user-provided data. Additionally, vigilant monitoring of changes or deviations, such as the sudden shift in online activity or unauthorized account appearances, enables organizations to promptly detect signals of identity theft or account compromise. Organizations can proactively address specific identity-related risks by facilitating tailored risk profiles for individuals or entities.
Digital footprint data serves as valuable forensic evidence in security incidents or breaches. It aids investigations and incident response efforts by facilitating the tracing of breach origin and enhancing mitigation effectiveness.
Device Intelligence
Device intelligence improves identity risk management by analyzing device characteristics, behaviors and attributes, such as type, operating system, IP address and geolocation. This analysis strengthens authentication processes, identifies suspicious access attempts and maintains robust security measures.
Detecting anomalies and enabling adaptive access controls are crucial for leveraging device intelligence. Monitoring device attribute changes can help identify identity-related risks, like unusual login attempts. At the same time, adaptive access controls allow organizations to adjust authentication requirements based on perceived risk, thus enhancing overall security.
Discover how to secure every transaction and protect your business.
Read More
Powerful AI-Insight
The power of artificial intelligence (AI) lies in its ability to analyze vast datasets and detect intricate patterns indicative of potential risks with unprecedented speed and accuracy. AI sifts through diverse sources of information, including user behaviors, transactional data and historical patterns, to identify anomalous activities or deviations from established norms. This enables organizations to anticipate and address emerging threats before they escalate into full-blown security breaches or other harmful activities, securing information and maintaining operational continuity.
AI-powered solutions also enable dynamic adaptation to evolving cyber threats in real time. Through continuous learning and refinement, AI systems can autonomously adjust risk assessment parameters and detection algorithms based on the latest threat intelligence and environmental changes. This adaptability ensures that identity risk management strategies remain agile and responsive in the face of rapidly evolving attack vectors and tactics employed by cybercriminals.
Preparing for New Challenges in Identity Risk Management
The ease with which identities can be falsified and placed at risk today underscores the need for more nuanced solutions. Rather than solely focusing on verifying IDs, organizations must adopt strategies that examine who is connecting and how they are connecting. This approach acknowledges that identity is just one piece of the puzzle and that actual security lies in understanding behavioral signals and analyzing real-time data points.
By integrating digital footprinting, device intelligence and AI algorithms, SEON provides a sophisticated approach that sifts through real-time data points to stitch together a comprehensive identity picture. This enables organizations to make informed decisions and effectively safeguard against fraudulent activities.