Have you ever wondered what kind of scams hide behind these “make money from home” adverts?
Well, after receiving a referral link, you’ll be prompted to sign up for their service. It’s an exclusive club, which requires you to submit a few documents. Once all your ID details have been submitted, you’ll receive your free $150.
It only takes one quick glance at the required fields to understand what’s going on: The service is essentially buying your personal ID documents.
How are they worth $150? Well, these documents are increasingly valuable to fraudsters and criminals. And in this post, we’ll look at the many ways they acquire them, use them, and why identity proofing is more important than ever in the online world.
What Is Identity Proofing?
Identity proofing is the act of authenticating a person’s identity when they are either making a purchase, submitting an application, or simply engaging with something that needs a level of verification.
Previously customers often had to send a physical form of identity documents for verification purposes however with biometrics, video identity verification, and other modern tech, the company can carry out KYC checks in a much more user-friendly manner.
It’s a legal requirement in certain industries (banking, fintech), and a must-have in fraud prevention but it’s a slow process, which can increase churn and turn your users away.
How Does Identity Proofing Work?
According to the US National Institute of Standards and Technology, remote identity proofing has three key factors to ensure full protection: resolution, validation, and verification.
- Identity resolution is the act of distinguishing a users identity amist a customer database, population or another similar user-based system.
- Identity validation: gathering unique evidence from the person ie password, security questions etc.
- Identity verification: before finally confirming the evidence submitted matches the data provided.
Why Is Identity Proofing Important?
For companies that look to streamline onboarding processes, identity proofing is important to protect businesses, and its users, against fraudsters as this extra layer looks to ensure only trusted individuals are able to access any data/products.
Scenarios include:
- KYC requirements: financial institutions, for instance, are under pressure to prove their users’ identities under Know Your Customer procedures.
- Digital credit scoring: Similarly, a loan provider would need to build a user profile based on user IDs.
- SCA/PSD2: Strong Customer Authentication, which is recommended under the PSD2 directive, aims to increase checks against stolen authentication elements
- AML: Anti money laundering checks, found, amongst others, in iGaming and forex exchanges, also require document verification
- Fraud prevention: confirming your user’s identity is one way to flag fraudsters. This helps reduce transaction fraud, and in turns chargebacks. You can also confirm a user’s identity if you flag a suspicious login attempt. Similarly, strange online behaviour (large cash deposits and withdrawals) could warrant an extra authentication step.
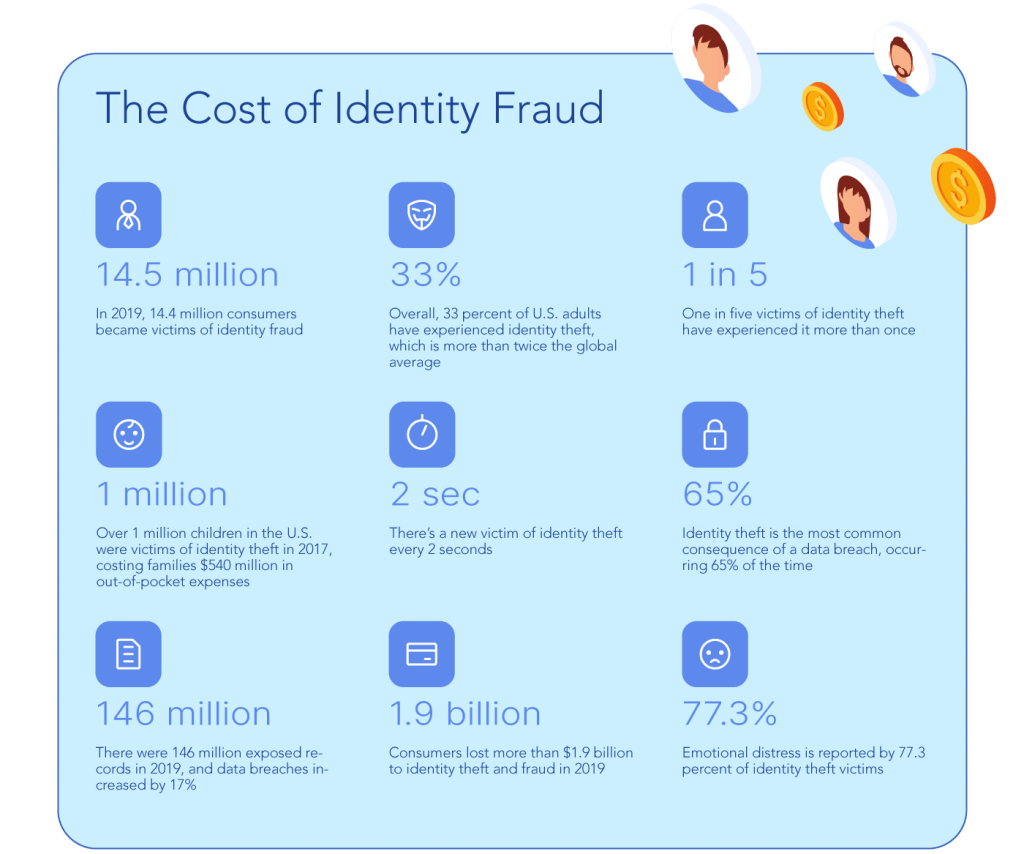
How Big of a Problem Is Identity Fraud?
As the world continues to become more digital, so do the opportunities to steal personal/sensitive information and according to the Aite Group, losses due to identity theft are forecasted to increase to a staggering $721.3 billion in 2021.
Speak with one of our experts to see how SEON helps businesses catch high-risk users before document checks, and onboard trusted customers faster with risk-aware verification.
Ask an Expert
The Limitations of Document Verification
Document verification can be an incredibly useful tool to help validate a customer on your site, however it does bring both compliance and security issues as fraudsters become better at acquiring IDs.
As we’ve seen in our opening example, some people willingly sell their IDs online, probably unaware of the consequences. But unscrupulous individuals who want to acquire IDs have no shortage of options.
Data breaches
Criminal organizations are constantly targeting companies for their user data. In the first half of 2020 alone, Nintendo lost 160,000 accounts; Twitter lost 130,000; and EasyJet lost 9 million customer records.
These customer profiles are then sold in bulk on the darknet. Fraudsters trawl through the databases and use all the information they can exploit to create accounts based on real information – which is why it’s imperative to put measures in place designed to prevent identity theft.
Phishing
Essentially a scam or deceptive technique designed to get users to submit their ID documents by themselves. Users are targeted via SMS, email or even phone calls. The technique sometimes overlaps with what is known as “social engineering” whereby fraudsters steal information in real-life scenarios.
One interesting topical point: phishing techniques are constantly evolving and increasing in sophistication. In the COVID-19 era, when customers are increasingly online and confused, these attacks have multiplied.
Fraudsters will use communications related to travel refunds, Amazon Prime or banking, which redirect users to landing pages designed to farm personal data.
Fake ID Services/DIY Options
Not all IDs are stolen. Some of them are falsified for specific purposes. For instance, a fraudster who only needs a selfie with a driving license could easily log onto a clearnet ID photoshopping website and buy the appropriate document.
Darknet marketplace sellers also offer ID templates, so users can create their own documents with their preferred image editing software.
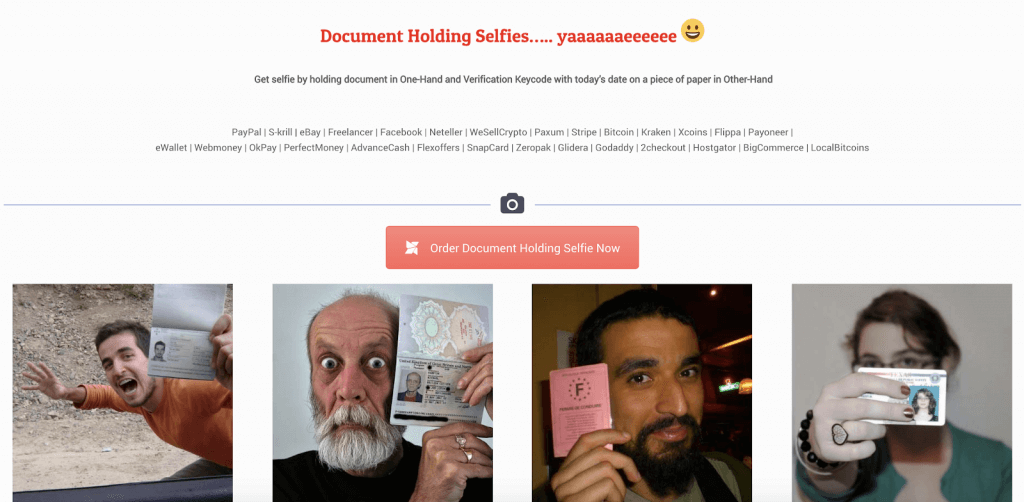
It takes very little know-how to get a fake selfie. And you can even find dozens of these services on the clearnet – no need for technical knowledge or crypto payments.
Cash In Hand/Low Tech
A method increasingly found in developing markets, where organized criminals set up shops and purchase people’s IDs on-site. It’s also worth noting that fake IDs are almost considered a rite of passage in places like the U.S. where the market for fake driver licenses (to bypass underage drinking law) creates a constant supply.
Shortcomings of Current Identity Proofing Solutions & Software
So what is an online business to do if they want to verify someone’s identity? Well, they can of course get the data checked manually, either by an in-house team or an outsourced one.
They can also use a third-party tool, such as Onfido or Veriff. The problems? These checks slow down the customer journey of legitimate users, and they are expensive. With an external service, for instance, each document check will cost an average of $2.
And in terms of user friction, the costs of ID verification solutions are harder to measure, but no less significant. In the digital age, a seamless user experience is increasingly a competitive advantage.
SEON helps filter out potential fraudsters pre-KYC by acting as an extension to your pre-existing requirements that’s invisible to your customers, with all checks performed in real-time.
Companies that add more friction to their users at any stage (onboarding, login or money withdrawal) risk creating churn, and sending users towards their competitors.
Last but not least, even if you go through a lengthy identity proofing process, chances are that your system can still be fooled by fake documents, synthetic identity frauds (mixing real and made-up customer data), and stolen IDs.
More Security with Digital Footprint Analysis
A person’s digital footprint can provide you with the history of a user’s existence on social platforms; acting almost like an internet passport that can be used for verification purposes.
For many companies, the question is therefore to find a solution that is fast, effective, and affordable. This is precisely where digital footprint analysis, or digital footprint assessment, shines.
Put simply: a user’s digital footprint contains only traces that can be acquired by your company and via data enrichment. For instance, if you have an email address, you can gather extra data points such as a social media bio, avatar, and understand if the user really is who they say they are.
Digital Footprinting Examples
The beauty of digital footprint analysis is that you can learn a lot, starting with very little. This is particularly useful in industries where you are dealing with a paucity of data, or when you want user friction to remain as minimal as possible.
- Device fingerprinting: the phone, computer or tablet that borrowers use to connect to the lending website contains tons of info. Are they using private mode or an emulator? This could increase suspicion that they are not who they claim to be.
- Email profiling: does the address exist? Is it from a suspicious, disposable domain? does the email have any data breaches? Or one that doesn’t require any verification during sign up? Is it linked to a social media site? If so, when is the last time the user logged in?
- Phone analysis: are they signing up with a real phone number? From a fixed line or mobile? And did they use that number for messaging services like Viber, Telegram or Whatsapp?
- IP analysis: one of the oldest and easiest forms of security available: looking at the origin of the connection. Is it from the right location? Or likely to be masked via TOR or a VPN?
Whether you answer these questions yourself or let an automated id verification solution calculate a risk score for you, there is clearly a lot of useful data here that should help your identity proofing process.
Digital Identity Proofing Summary: Balance Friction with Security
Online businesses often need to balance security with friction. Too many authentication obstacles, and your users will look elsewhere. Too few, and fraudsters can easily fool your team to exploit your company.
The key is therefore to make better educated guesses about your visitors, by creating an invisible layer of protection on your site.
This is precisely what data enrichment can help with, allowing you to perform a complete digital footprint analysis. Best of all, you can do it in real-time, and without slowing legitimate customers who can help bring revenue to your business.
Frequently Asked Questions
Digital identity proofing is the process of verifying and authenticating the identity of individuals in an online context. This can come into play at both sign-up and withdrawal.
A person can verify their identity through a range of ways including biometrics and government document submissions; which method depends on what is required by the business and the corresponding regulatory body.
Requiring some form of physical or digital evidence is the best way to verify a person’s identity. A business will need proof of factors like name, date of birth or look to invest in digital identity proofing methods like asking them to take a selfie.
See how SEON combines document checks with real-time device, behavior and digital footprint signals all in one platform to stop synthetic IDs, deepfakes and bonus abuse.
Explore SEON Identity Verification
You might also be interested in reading about:
Sources used for this article:
- NIST Special Publication: Digital Identity Guidelines
- Giact– U.S. Identity Theft: The Stark Reality
- Keepnet Labs: The Biggest Data Breaches in the first half of 2020
- The Guardian: Scammers exploit Covid to steal from stressed bank customers
- BBC: Why fake ID is an American rite of passage