For online businesses, and especially fintechs, application fraud is a pain point that can cost dearly – way beyond just losing some customers.
Let’s look into how to better understand it and how to detect it with minimum friction.
What Is Application Fraud?
Application fraud happens when an individual uses deceptive methods when applying for a financial product. It is also sometimes known as form fraud. The product may be a mortgage, a loan, or even a new bank account.
As for the kinds of deceitful practices that count as application fraud, it may involve:
- using a stolen or synthetic ID
- lying about your income
- supplying doctored payslips
- inflating the value of something you wish to insure
The key issue with application fraud is that online companies tend to accept applications fast. The number of new users is often a KPI used to justify growth, which creates an incentive to be more lenient when it comes to risk management.
Unfortunately, this often proves to be a bad business strategy. Accepting more users may look good on paper, but if these are application fraudsters, you risk:
- losing valuable business
- offering loans to customers who will default
- paying compliance fines for KYC or AML
Insurance application fraud alone, for instance, is calculated to cost the UK economy more than £2/$2.60 billion per year, according to the country’s Insurance Fraud Taskforce.
The Nigeria-focused fintech FairMoney can make a decision about a loan in under 8 seconds, with much lower defaulting rates.
Learn how
3 Examples of Application Fraud
Application fraudsters are always a problem, but not all of them target the same kinds of companies. Let’s look at three examples to explore the range of attacks you may encounter.
Insurance Application Fraud
Insurance fraud isn’t anything new but the digitization of insurance companies has made them even more of a target for fraudsters, opening more loopholes and allowing schemes to scale more easily.
In this case, fraudsters might:
- Make false or exaggerated claims: For instance, inflate their salary to apply for a mortgage.
- Intentionally damage the item to make a claim: This is particularly common with high-end electronics and gadgets.
- Lie about who the policy is for: Consider car fronting, for instance: It’s when a policy is taken out by someone on behalf of another driver.
A point to note is that searching the application for inconsistencies is already part of the insurance due diligence process.
The major difference to keep in mind is that with online users, you can easily access interesting new data that wouldn’t otherwise show up on a credit scoring report – such as their digital footprint.
Digital Bank Account Application Fraud
We’ve got a full post on how fraudsters open bank accounts, but it all boils down to creating fake profiles using stolen ID documents.
Their end goal could be to use the account as a bank drop, to exploit a referral promotion, or to launder money.
Neobanks and digital banks are particularly careful not to add too much friction at the onboarding stage, in order to provide a pleasant customer journey – which is exactly why fraudsters can slip through the net.
This may cause problems such as:
- promo and bonus abuse
- KYC and AML fines
- legal issues
- loan defaults
And, of course, there are all the hidden costs of fighting fraud, such as lost customer service or reputational damage.
Loan Application Fraud
As far as financial products go, loans are probably some of the riskiest to offer. They also offer the highest reward for fraudsters who manage to fool the standard or alternative credit scoring process.
Fraudsters who target loan companies usually create synthetic IDs. These are identities made up of data from real people (who either willingly lend their IDs or have them stolen).
The reason these types of ID are so effective at fooling lenders is that they’re designed to target people with non-existent credit history, including the unbanked and underbanked. Fraudsters have been known to stoop as low as using children or deceased people’s IDs in order to fool the credit scoring stage.
How Does Application Fraud Impact Businesses?
Application fraud can impact businesses in a range of ways. Financial loss is the most obvious, with risks including falsified insurance claims, loan defaults, promo abuse, and more. There is also the risk of regulatory fines.
Dealing with instances of application fraud can also be a time drain for businesses, meaning it costs them in terms of staff time and loss of focus on core operational activities.
Businesses may also suffer reputational damage if they become associated with repeated instances of fraud. This can lead to further loss of revenue, as well as damage to trust previously built up with partner organizations.
5 Tips for Application Fraud Detection
With all the above in mind, it seems clear that application fraud stems from a key challenge: knowing exactly who you’re dealing with (especially online).
Here are our top tips.
Use Real-Time Data Enrichment
Online applications require users to fill out various fields. This is usually to answer questions relating to their identity – and will often contribute to your KYC onboarding process, whether they’re a legal requirement or not.
Such steps, however, create an amount of friction in the user journey. The more forms, to fill, the more friction there is. Worse still, they can even create churn, and send your potential customers looking elsewhere.
Moreover, how can you trust what users are writing in those fields? And how can you get a better sense of their identity without asking for hard proof via ID documentation or biometrics?
The answer may lie in data enrichment. Put simply, it’s about learning more about a user based on simple, easily shared data points, such as an email address, phone number, or IP address.
The enrichment part lets you answer questions such as:
- Is this IP address pointing to a proxy or VPN?
- Is this person using a virtual SIM card?
- Does the user have an online presence and if so, how recent is it?
The last point, in particular, could be one of the strongest signals to check whether you’re dealing with a real user or not. Let’s look into it further.
Keep a Close Watch on Social Signals
As you can imagine, application fraudsters tend to work fast and keep several schemes going at any one time, which is why they won’t jump through hoops to create a believable online footprint.
This gives you a great chance to identify potentially fraudulent applicants in seconds.
In other words, a complete lack of social media profiles is highly suspicious.
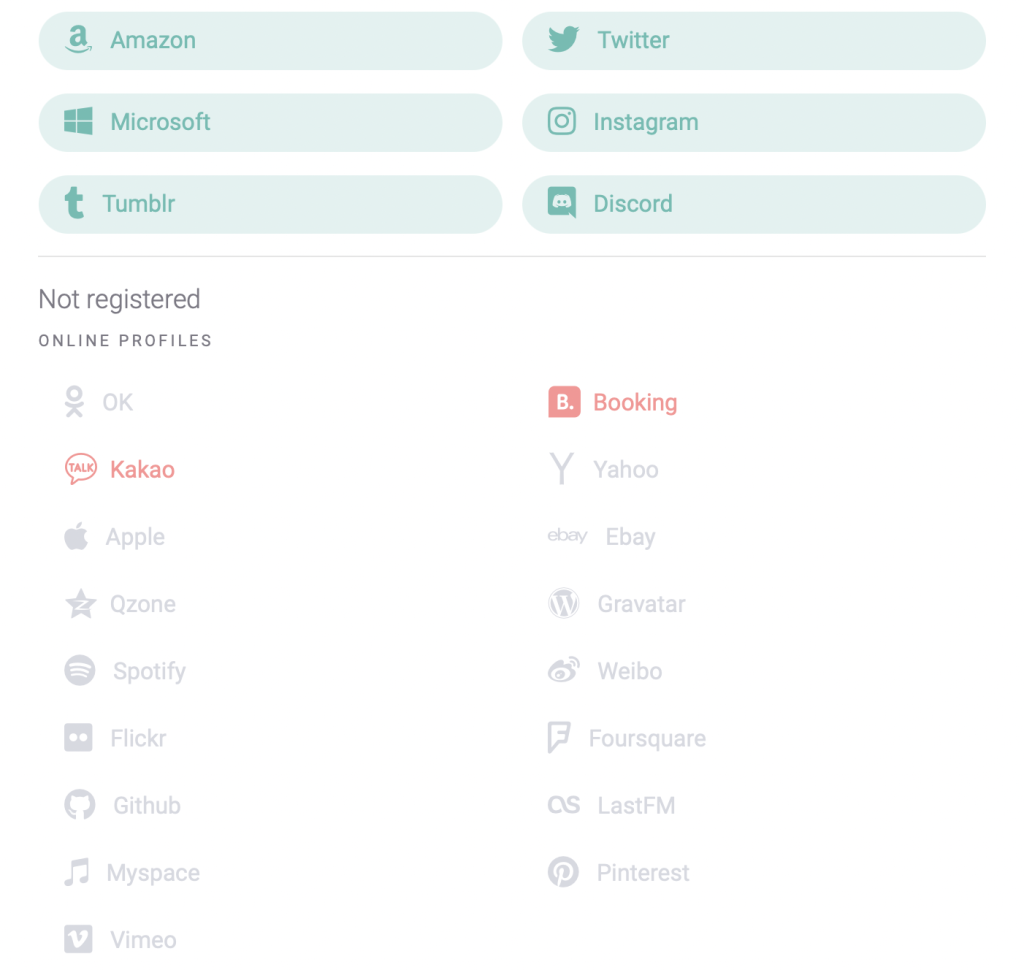
The image above is from the SEON platform, indicating which social media and other web platforms the email address we provided is registered on.
The applicant has, in this case, registered with this email address profiles on Amazon, Twitter, Instagram, Discord, Tumblr and Microsoft’s services. The greyed-out results are platforms that did not return a result (while the few red platforms timed out, as all this is gathered in real time).
We can thus conclude that this is a real individual, and not a fraudulent persona created by a fraudster to apply for a loan. The inverse – a user with apparently no social media presence – should make us scrutinize the application much more closely.
This type of digital footprint analysis social media search is unique to SEON, which checks 90+ platforms to gauge just how legitimate a customer is. The results are provided in real-time based on an email address or phone number alone, and with zero extra friction for the customer.
This also allows you to save on KYC costs, as you can filter out junk users before moving on to expensive identity verification checks.
Identify Connections Between Accounts
Another thing to remember about application fraudsters: It’s probably not their first attempt. Armed with this knowledge, you can start looking for connections between their multiple accounts.

You will want to look at similar IP addresses, email addresses, and previously blacklisted phone numbers, finding any similarities that indicate one person attempting to apply with multiple personas or accounts.
But the technology really kicks up a gear when you start looking at users’ configurations of software and hardware. In the fraud prevention world, this is done by logging and tracking:
- Cookie hash: Looking at your user’s browser session history as a strong indicator of who they might be.
- Browser hash: An ID based on the web browser’s unique features, such as version, installed plugins, etc.
- Device hash: A device fingerprinting process allows us to get a strong idea of who is connecting to a site based on their device and operating system.
While none of the above techniques are precise enough to confidently ID a user on its own, once you combine them, they can certainly help you spot suspicious connections between customers, or even just web visitors.
Understand Applicants’ Behavior With Velocity Checks
Velocity rules are the closest thing you can get to monitoring user behavior. This is done by looking at the kind of actions they perform on your application page during a certain timeframe.
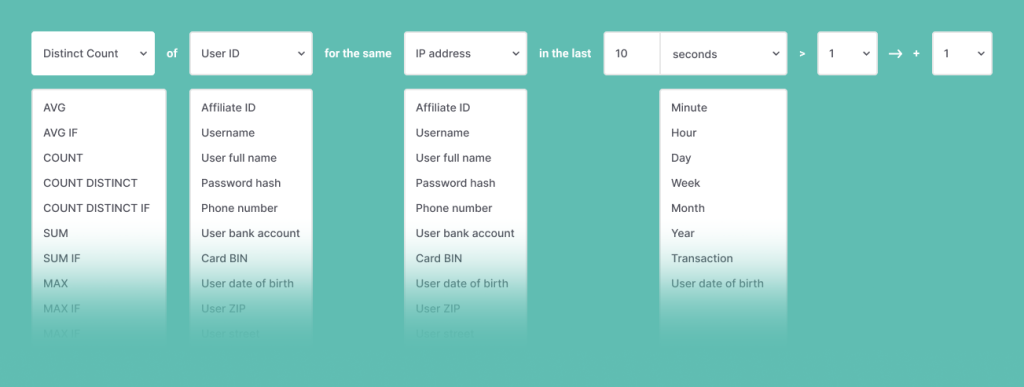
What would constitute suspicious behavior? Some examples:
- filling out a form in less than two seconds
- a rapidly changing IP address
- entering 10+ different full names in succession
The idea is to find the sweet spot between what a standard user would do at the application stage and what a fraudster’s behavior would look like.
To use one of the above examples, a legitimate user is likely to take a minute or two to fill in a series of short fields in a form. A fraudster, on the other hand, is likely to be using scripts or other automation to do so, as they help them scale – which means they will be filling in forms unusually fast.
Deploy Machine Learning Fraud Detection
Last but not least, you could leverage the power of AI to help you sport application fraud patterns.
A machine learning engine will learn from the applications you mark as fraudulent and help suggest risk rules based on their similarities.
You can even calculate false positives in advance and test the suggested rules on your existing data in a sandbox environment. The longer you let the ML system run, the more accurate its custom suggestions will become.
This is particularly helpful for companies with large volumes of applications, where a human analyst would struggle to spot non-obvious connections.
Partner with SEON to reduce fraud rates in your fintech with real time data enrichment and advanced APIs.
Ask an Expert
How SEON Can Help Curb Application Fraud
SEON provides a full end-to-end fraud prevention system based on real-time data enrichment, device fingerprinting, and machine learning suggestions. It’s ideal for application fraud but also multi-accounting, pre-KYC checks, and transaction fraud.
Uncover fraud patterns and discover revenue opportunities with the fraud prevention of choice for leaders such as Revolut and Afterpay, whether you’re a neobank, BNPL, fintech, or insurtech company.
Sources
- UK Insurance Fraud Traskforce: final report
FAQ
Application fraud covers any kind of lies or deceitful practices made by people when applying for a financial product. This can be a car loan, mortgage, neobank account, or BNPL account, among others.
Most companies can detect application fraud by focusing on strong identity-proofing tools. That may include KYC software, identity verification tools, or real-time data enrichment solutions.
The risks of application fraud to businesses include financial loss, trouble with regulators (potentially including fines), distraction from core activities, and reputational damage. This is why detecting and blocking attempted application fraud is so important.