Fraud rings tend to be more methodical with their attacks than a single fraudster looking to make a quick buck. Let’s see what this means for your business – and, of course, how to stop them.
What Is a Fraud Ring?
Fraud rings are organized groups of fraudsters. They tend to be more sophisticated than opportunistic fraudsters, having access to more resources, money, and technology.
While some fraud rings specialize in one type of attack, most fraud rings will straddle the lines between numerous fraudulent practices, even overlapping with cybercrime and general crime.
In fact, many fraud rings will work with specialists in numerous fields, such as for instance, social engineering, credit card fraud, and synthetic ID creation.
It should also be noted that it’s difficult to define precisely what makes a fraud ring. Just like other forms of organized crime (gangs, syndicates), it’s hard to agree on how many members you need to officially become a fraud ring.
Sometimes, the term “fraud ring” describes several accounts all belonging and/or controlled by one fraudster but, more commonly, they comprise multiple criminals working in tandem.
Want to learn more with concrete examples? Watch our webinar on fraud rings below:
Fraud Ring Examples
There are, plainly speaking, as many types of fraud rings as there are types of fraud. Here are examples of the most common ones you may encounter online:
Credit Card Fraud Rings
In February 2022, two Philadelphia men were convicted of running a credit card fraud ring that was made up of more than 200,000 stolen accounts. The scheme worked as follows:
- The fraudsters purchased large quantities of stolen credit card numbers available on the darknet.
- They encoded the stolen card numbers onto blank cards.
- Hired runners to go and purchase gift cards and other items with a high resale value, such as Apple products, jewelry, and high-end electronics.
This standard carding scheme is just one of the many examples of ways in which organized fraudsters target online stores and retailers, leading to high rates of chargebacks. The negative impact is felt both by legitimate cardholders and by online stores and retailers.
- Who’s affected? Online stores, brick-and-mortar stores, and generally any company that accepts payments in a CNP (card-not-present) scenario.
Identity Theft Fraud Rings
Manhattan District Attorney Alvin Bragg, Jr. announced on February 23, 2022, that six individuals had been prosecuted for identity theft.
In that particular case, the stolen identities were used to apply for unemployment assistance accounts with the New York State Department of Labor. It is claimed that more than $135,000 was collected in benefits.
This is how their scheme operated:
- The fraud ring created profiles using phishing techniques, stolen data from employers, and purchased IDs on the dark web.
- They applied for COVID relief loans
- They received the government help
- They defaulted on the loans
When the authorities tried to locate the creditors, they would be met with unsuspecting victims or non-existent profiles.
This kind of loan fraud scheme is prevalent in a number of industries. Banks and neobanks are particularly targeted due to their access to financial services. Loan providers, especially those operating online, often see their credit checks fooled by these kinds of synthetic identities.
- Who’s affected? Any kind of company with a KYC process such as banks, crypto exchanges,, BNPL companies, loan companies, insurance tech and iGaming companies.
Money-Laundering Fraud Rings
A whopping 1000 individuals were arrested by Interpol in December 2021, purely on the grounds of money laundering. The international effort saw cooperation between more than 20 countries, which resulted in nearly $27M being seized.
As is often the case with these sprawling fraud rings, the criminals committed a wide range of attacks, from romance scams to investment fraud.
However, it was the money laundering rules associated with illegal online gambling which appear to have tripped them up.
In fact, the operation saw Interpol pilot a new Anti-Money Laundering Rapid Response Protocol (ARRP), which proved critical in intercepting illicit funds.
- Who’s affected? The key targets of money laundering tend to be banks, ranging from financial institutions to neobanks. However, we’ve seen fraudsters launder funds through online stores, BNPL companies, and even crowdfunding platforms.
Interested in learning more about anti-money laundering? Read our full guide on the best AML software.
SIM Jacking Fraud Rings
The modern scourge of telecommunications fraud, SIM jacking has claimed victims as famous and tech-savvy as Jack Dorsey, Jeff Bezos, and Mark Zuckerberg.
A 2021 case saw law enforcement officials arrest ten people in connection with a series of attacks designed to target high-profile individuals.
Fraudsters who commit these kinds of attacks tend to pool their resources to take over accounts, steal identities, resell valuable accounts, and perpetuate phishing and crypto scams. Here is how it works:
- Fraudsters find the phone number linked to a social media account.
- They contact the telecom operator responsible for that number.
- They pretend to be the rightful owner of the said phone number and ask to transfer it to a new SIM.
- A new SIM, which the fraudsters control, is thus linked with the original number.
- Fraudsters receive all SMS and 2FA notifications and use them to reset the social media account login details.
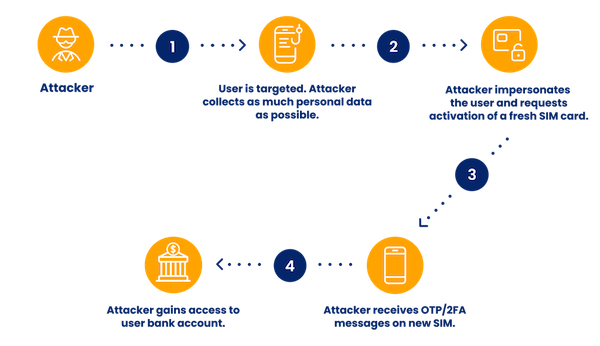
- Who’s affected? Anyone, really. While high-profile users such as celebrities and CEOs have made the news after getting their accounts stolen, SIM jacking fraud rings will target individuals en masse. The real burden falls on companies whose accounts fall into the wrong hands, and telecom operators whose reputations are damaged by SIM jacking.
Learn more about SIM jacking and SIM swap fraud here.
How to Detect and Prevent Online Fraud Rings
Detecting fraud rings is all about spotting connections between users.
Let’s break down in detail below how we can do this using the SEON platform.
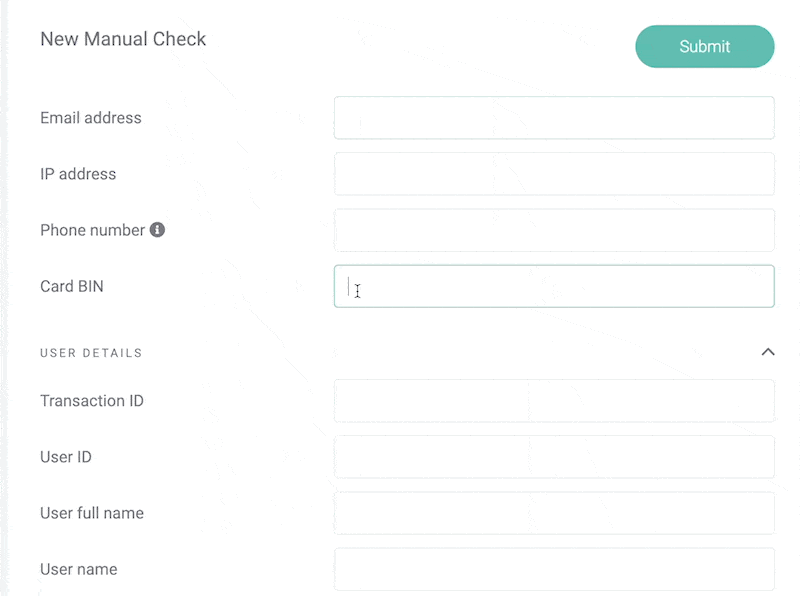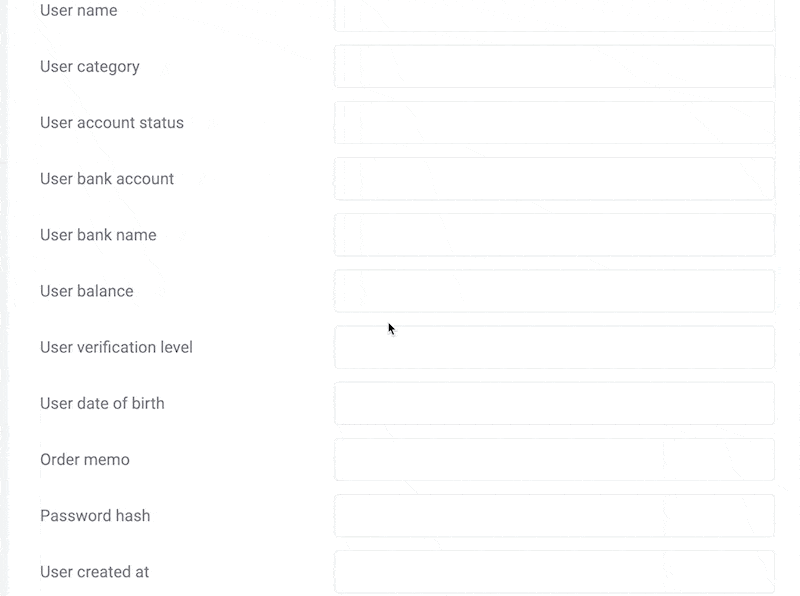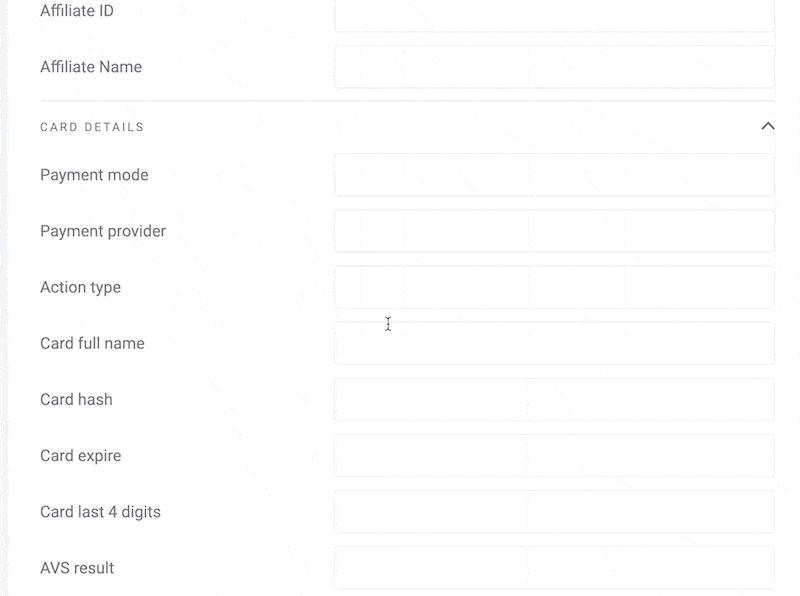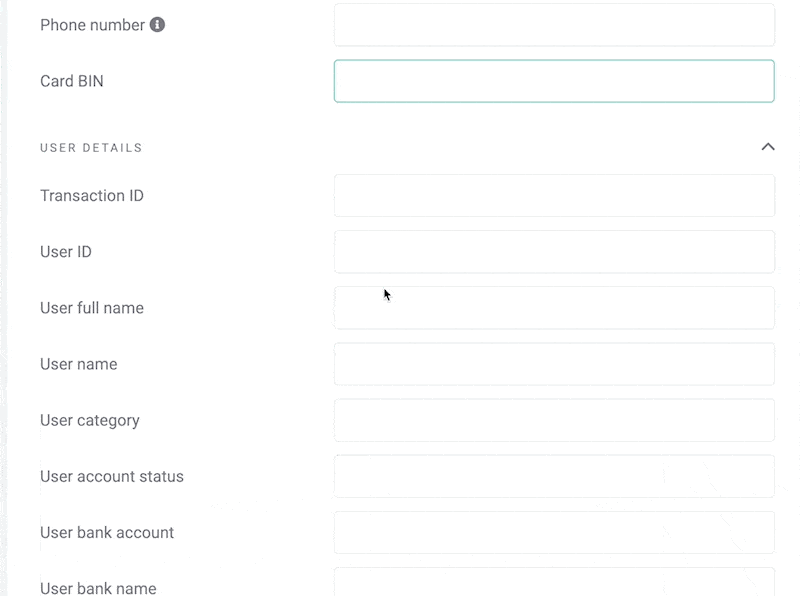
1. Start With as Much Data as Possible
As a fraud ring detective, your first task will be to gather as much information as possible.
That includes identifying details such as an email address and phone number, but also credit card details, IP address, and whatever else you can gather about each user.
The idea is that the more data you can start with, the easier it will be to spot connections later.
2. Go the Extra Mile with Data Enrichment
Sometimes, the data comes from user fields, such as phone numbers or email addresses. Other times, you need to go look for it.
In fraud detection, this is a process called data enrichment. What it allows you to do is expose extra data points that are not immediately visible.
Examples of enriched data include:
- social media profiles linked to an email address or phone number
- whether the IP points to a VPN, Tor, or suspicious proxy
- if the card number indicates that it’s a prepaid card
The data enrichment process is a great way to uncover more about your users, without adding friction to their journey.
3. Find Patterns and Connections
Now that you’re armed with as much data as possible, it’s time to look for patterns. The best place to start is to filter the data.
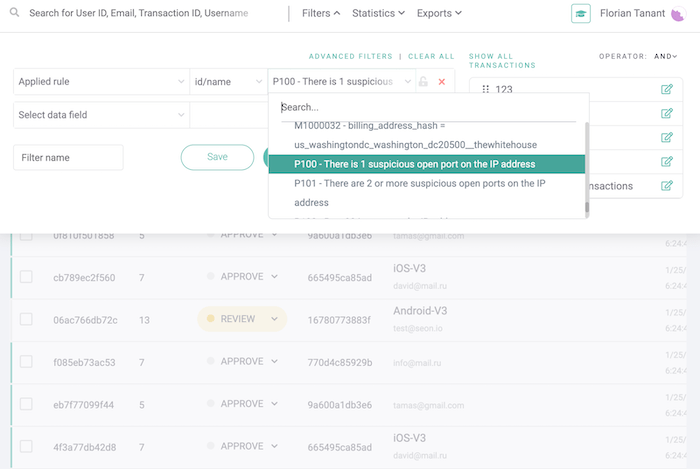
In the image above, we’re looking at all the transactions that came from a suspicious open port on the IP address.
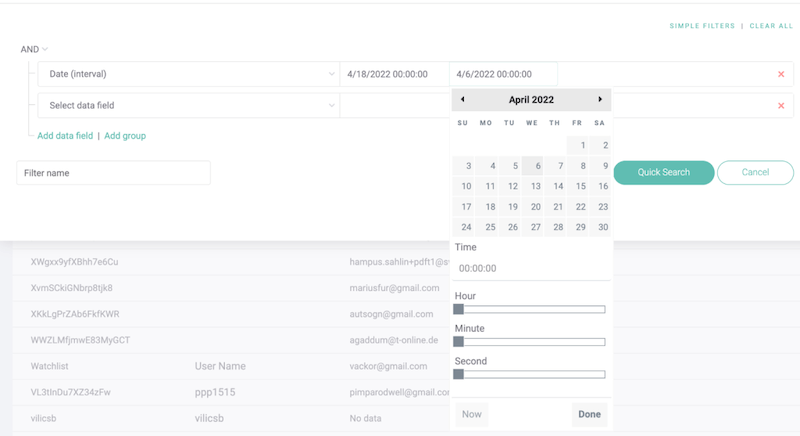
We can also be more selective with our data, for instance by adding a date range.
And, of course, some of the most important filters will look at device data.
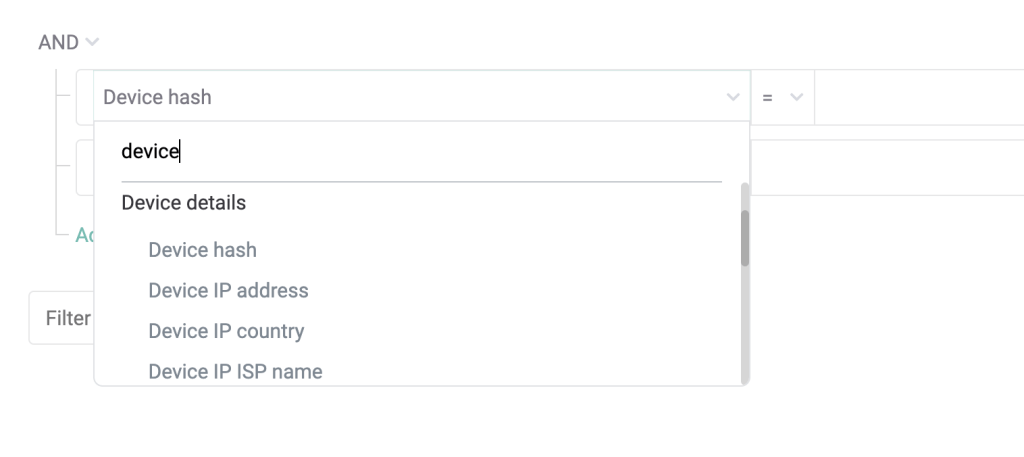
Because fraud rings don’t have access to an infinite number of devices, they tend to rely on emulators and spoofing tools to fake their connections.
However, if your anti-fraud solution can detect device spoofing methods, you have access to some of the most powerful data available to spot fraud rings. That may include:
- device operating system
- plugins installed
- attempts to hide behind software and hardware emulators
Each device type can also be logged as a hash, which is how you can establish that multiple users share the same configuration. This is key in spotting connections that could point to multi-accounting and fraud rings.
4. Visualize Connections With Graphs
If manual filtering doesn’t work for you, graph visualization is also a great way to establish links between users.

This specific “customer connection” feature of the SEON dashboard, shown above, helps you immediately visualize which data points are shared by similar users.
Of course, a little refining is still needed. Multiple customers sharing a similar OS and ISP doesn’t mean they are fraudsters. If they also appear to have the exact same HTML5 canvas size and plugins installed, you should probably start raising red flags.
5. Leverage the Power of Machine Learning
Digging through data manually can yield fantastic results, especially if you have eagle-eyed risk managers. But what if you have so much information that the noise-to-signal ratio is too high to spot significant patterns?
Then it’s worth looking at machine learning (ML) analysis.
Put simply, it’s about letting algorithms suggest potential patterns by running through your business data. If you often flag a specific type of transaction without realizing it, an ML system will be able to automatically create a rule, which you can enable, disable, or test on your existing data.
Below is an example of ML-suggested risk rule on the SEON platform. Here, the machine learning system is suggesting that we start flagging all transactions that share the same billing address hash.
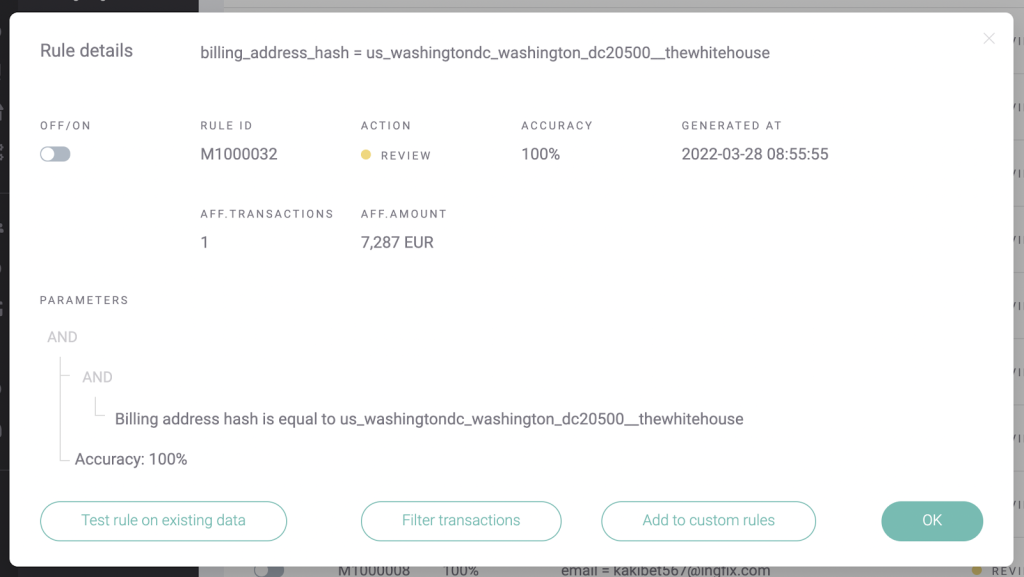
Of course, the longer you let your system run and accurately label suspicious cases, the more precise the algorithms can be. You can read more information on fraud detection using machine learning, or jump directly into SEON docs to see exactly how our platform does it.
Use Case: How a SEON Fraud Fighter Detected a Bonus Abuse Fraud Ring
Fraud managers rely on SEON every day to slash their fraud rates, improve compliance, and generally run operations as smoothly as possible.
Sometimes, however, it’s the SEON team that spots inconsistencies in the data.
This is precisely what happened when a leading iGaming company let our customer support agent, Conner Keele, pore over the data logs as part of the SEON team’s regular check-ins.
The company was aware that multi-accounting users were trying to abuse bonuses, but Conner noticed some interesting patterns on SEON’s customer connection tab:
- a lot of new users were signing up with an outlook.com email address
- they shared the same ISP
- all the email addresses followed the same structure, such as [email protected]
What’s more, data enrichment results showed none of the email addresses appeared on data breaches, and all the accounts chose the same security question (mother’s maiden name).
After confirming his findings by filtering each data point, Conner realized he had stumbled upon a fraud ring. He immediately notified the iGaming operator’s fraud analyst, who promptly implemented the right risk rules.
The result? More than 700 connected fraudulent accounts were taken down in seconds.
This simple yet effective maneuver saved the company huge amounts in wasted bonuses – not to mention the long-term headaches of having fraudulent accounts on the platform.
Want to see how SEON could help you catch more fraud rings? Book your demo below.
Partner with SEON to reduce fraud rates in your business with real time data enrichment and advanced APIs
Ask an Expert
Sources
- US Department of Justice: Two Philadelphia Men Convicted of Running Credit Card Fraud Ring Using 200,000+ Stolen Accounts
- Manhattan District Attorney: D.A. Bragg: Identity Theft Ring Indicted for Pandemic Unemployment Benefits Conspiracy
- Interpol: More than 1,000 arrests and USD 27 million intercepted in massive financial crime crackdown
- ArsTecnica: Authorities bust SIM-swap ring they say took millions from the rich and famous
Fraud Ring FAQ
A fraud ring is simply a group of fraudsters sharing resources to commit fraudulent acts. It is hard to distinguish between fraud rings and one fraudster targeting companies under multiple aliases. However, once apprehended, it often becomes more clear whether you were dealing with one person or multiple accomplices by looking at the methods they’re using.
There are as many types of fraud rings as there are types of fraud. Over the years, authorities have caught fraud rings specializing in romance scams, account takeover, and SIM jacking. What they all have in common is that they pool resources to coordinate and automate attacks at scale.
Like multi-accounting, you can detect fraud rings by identifying patterns in your fraudulent users. It may be that they often hide behind the same VPN or use a rotation of similar devices. In one of our use cases at SEON, we found that similar email addresses and ISPs could point to fraud rings, for example.







