Do you think 2FA can protect you? SIM swap fraudsters think otherwise. Learn all about SIM swap fraud and how to prevent it in this article.
What Is SIM Swapping?
SIM swap fraud happens when a fraudster takes control of someone’s phone number. The fraudster contacts a telecom operator and convinces them to transfer a victim’s phone number to a new SIM. The fraudster then controls the new SIM and can receive SMS and phone calls.
This is particularly damaging when fraudsters receive 2FA and OTP messages. They can essentially log into the victim’s accounts and mine them for information or money. In 2020, 10 fraudsters were arrested by Interpol after stealing more than $100M in crypto following SIM swapping attacks.
SIM swap fraud is also known as SIM splitting or SIM jacking. It is a form of social engineering and telecommunications fraud as a telecom agent must be deceived and convinced to transfer the phone number to a new SIM.
How Does SIM Swap Fraud Work?
SIM Swapping tends to happen in one of two ways:
- Targeted SIM jacking: In this scenario, fraudsters have a specific phone number they want to control. This is particularly common when attempting to take over valuable social media handles. Prized Instagram or gaming accounts, for instance, have been known to fetch prices of up to $40,000.
- Brute force: Sometimes fraudsters will simply try their luck with numerous phone numbers until they hit the jackpot.
In both scenarios, the next steps are very similar:
- The fraudster will research information about the phone number’s holder.
- They will contact the relevant telecom company and impersonate the victim.
- They ask to transfer the old number to a new SIM, which they control.
- They can now start receiving 2FA or OTP SMS to log into accounts, steal information and steal personal data.
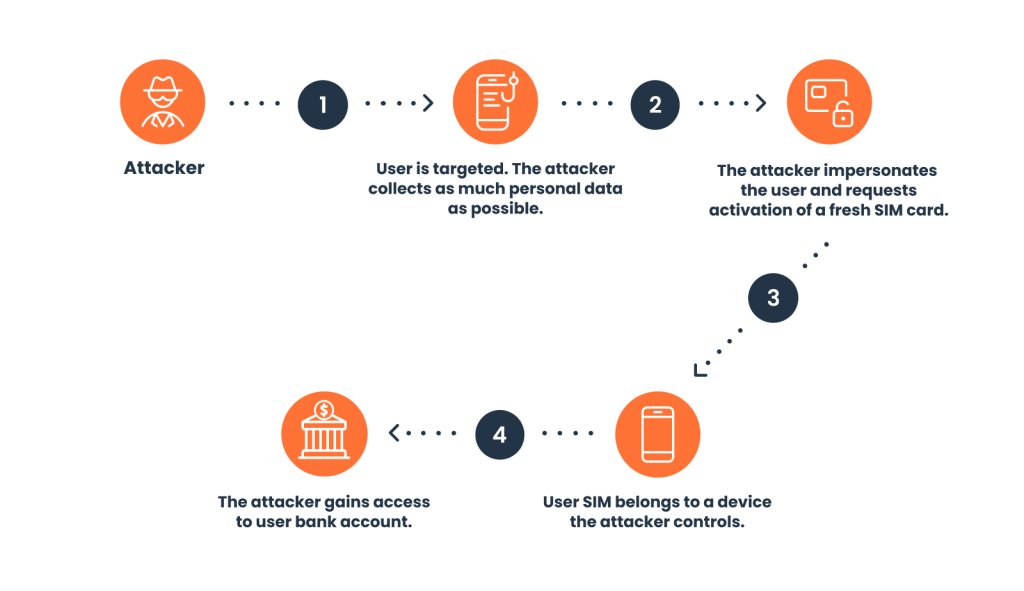
Fraud Attacks Following SIM Swapping
A SIM swap is only the first step for fraudsters. Once they are in control of your phone number, however, there is no limit to the number of damage they can do. This can take the form of:
- Account takeover: The most common form of attack, and indeed the reason why many fraudsters use SIM swaps in the first place. A fraudster who controls a phone number can receive 2FA or OTP SMS that allows them to log into your accounts. This includes mobile banking, social media, or online store accounts.
- Identity fraud: Stealing someone’s phone number isn’t considered ID fraud per se. But fraudsters often mine accounts for personal documents to steal the victim’s identity.
- Phishing: Once they are in control of a phone number, fraudsters can get in touch with your family, friends and colleagues to gather personal information.
- Transaction fraud: If your account acts as an e-wallet (for instance, for online store credit), fraudsters will use it to buy themselves gifts. Even worse, they could find a linked credit card number and use it on their shopping sprees.
- CEO fraud: There has been a rise in attacks where executives and managers are impersonated by fraudsters. Taking control of their phone number can certainly help these kinds of schemes.
How to Prevent SIM Swapping
Preventing SIM swapping is a three-pronged strategy. It takes collaboration between businesses, telecom operators, and users. Let’s break it down below in three different points.
1. Stricter Verification from Telecom Operators
The first step in preventing SIM swapping fraud is for telecom operators (telcos) to deploy more stringent verification procedures.
Luckily, regulations have been put in place in several countries to ensure user accounts benefit from increased protection.
In the US, for instance, the FCC amended its Customer Proprietary Network Information (CPNI) and Local Number Portability rules. The new rules state that mobile carriers must notify actual customers before reassigning the number to a new SIM card or a porting.
As a bonus, the rules are also designed to block robocalls by forcing mobile carriers to maintain a Robocall Mitigation Database. If a phone number is tagged as spam, it should be displayed as such on people’s caller IDs when the phone is ringing.
The rules are strict, as the FCC has indicated that any mobile carrier not following them would be banned and essentially stopped from operating.
2. Account Verification Using Digital Footprint Analysis
If you can’t trust 2FA to guarantee that the right person is logging into their account, you need to authenticate using alternative methods.
One of these methods is to look at digital footprints…
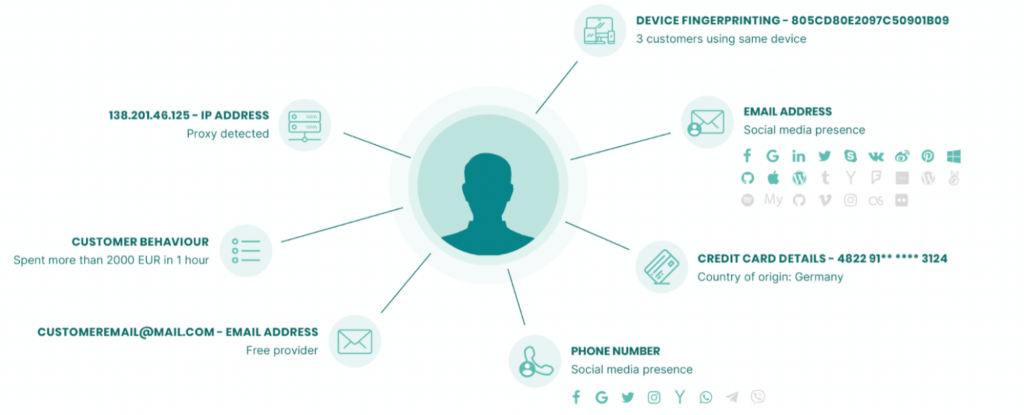
In simple terms, it’s about checking that the data for the user logging in is consistent with data you’ve collected in the past. Most companies already look at IP addresses, but you could also look at the device’s configuration of software and hardware.
We’ll go into more detail on this later – though you can skip to the tools section to find out more if you prefer.
3. Better User Education
Last but not least, phone number holders should keep a close watch on their personal accounts. Common sense goes a long way, but more and more companies are taking matters into their own hands to educate users about the importance of their account details.
2FA or MFA verification is a good starting point, but more and more businesses now incentivize users to rely on biometrics authentication and email verification to log into their accounts – or at least to be notified when a suspicious login happens.
Best Tools for SIM Swap Fraud Detection
While telecom operators should have their own SIM swapping detection methods in place, most businesses can also leverage anti-fraud tools.
These tools are designed to authenticate users, which may come in handy if they have just been victims of SIM-jacking attacks.
Tools with a proven track record of helping authentication include:
- IP lookup: By learning everything possible about an IP address, you can compare the data with your standard user logins. More importantly, you can instantly detect suspicious connections from far-off geolocations or from spoofing tools such as VPNs, Tor, proxies, and emulators.
- Device fingerprinting: Similar to IP lookups, you can also gather hundreds of data points relating to the device software and hardware. This is also helpful when identifying spoofing configurations that hide behind emulators. More to the point, a new device that uses the same data but a new phone number would be a clear indicator that you are dealing with SIM swapping.
- Virtual SIM card detection: Obtaining new phone numbers for their scams costs fraudsters a lot of time and effort. To speed things up, they rely on virtual SIM cards or eSIMs. You can perform a quick HLR/CNAM check to learn if the new phone number points to suspicious data or not.
Want to try it yourself? Give our phone lookup tool a go:
Takeaways
SIM swap fraud has targeted some of the most famous people on Earth. Jack Dorsey, Jeff Bezos, and Kim Kardashian have all been victims of SIM jacking.
And while targeting your phone may not be as glamorous, fraudsters still do their best to take over accounts in any way they can.
The good news is that regulations are forcing telco operators to be more stringent when it comes to verifying users. And thanks to tools like SEON, you can also perform your due diligence whenever a user logs in with new data.
Frequently Asked Questions
A fraudster who SIM swaps your SIM card will take control of your phone number (but not your device), so they can receive SMS on your behalf. It is particularly dangerous as they can receive 2FA and OTP codes to log into your social media, banking, or even ecommerce accounts.
SIM swap fraud happens when a bad agent convinces a telco operator to switch a phone number to a new SIM. The victim isn’t aware of it, and the fraudster takes control of the new number.
Yes. If you perform a SIM swap, you may be prosecuted and imprisoned.
Sources
- Europol: Ten hackers arrested for string of SIM-swapping attacks against celebrities
- FCC: The FCC’s Push to Combat Robocalls & Spoofing
- The New York Times: Instagram Bans Hundreds of Accounts With Stolen User Names