The crypto landscape has often been seen as having trigger-happy, larger-than-life personalities. A place where the law only pokes its head in when it’s absolutely necessary. A wild west, in other words.
Most often, this is in reference to the high-profile exchange operators and the low-profile money launderers. Crypto exchanges may sometimes look to bend the definition of customer due diligence (CDD) and KYC in the name of onboarding more customers or providing a better experience.
But their finance-democratizing, control-decentralizing, owner-anonymizing approach can also invite unwanted criminal business.
While lawmakers develop scrutiny protocols to better monitor how these ecosystems operate, this space still offers opportunities to payment fraudsters who would take advantage. Here’s how to better protect your crypto business from payment fraud.
Do you accept card not present payments? Protect and streamline your business with SEON’s real-time data enrichment and advanced machine learning.
Ask an Expert
Why Is Payment Fraud a Problem for Cryptocurrency?
The inherently anonymized, low-scrutiny crypto exchange environment offers a more accessible playground for payment fraudsters. Naturally, every vertical of online business needs to have payment fraud on-radar, but crypto exchanges will always have trouble balancing security – and compliance – with the low friction experience that their customer base asks for.
This creates an alluring environment for instances of credential stuffing, targeted phishing attacks, payment with stolen cards, money laundering and account takeovers (ATO). The ability of cryptocurrencies to be fully “tumbled” to the point they are untraceable makes payment fraud in DeFi marketplaces an even more dangerous prospect.
Common Types of Cryptocurrency Payment Fraud
The following prevalent fraud tactics are not necessarily unique to crypto exchanges but offer unique challenges. They are not necessarily payment fraud in and of themselves but theft and payment fraud are their only possible outcomes when dealing with fraud and crypto assets. Types of crypto payment fraud include:
Credential stuffing in crypto exchanges, resulting from a data breach of paired usernames and passwords, poses a particular threat for crypto and other low-friction gateways. Where more hardened gateways might use tools that look up breached passwords with k-anonymity-powered haveibeenpwned, most crypto exchanges favor a minimal amount of friction at the login stage, and will likely not include such a check. In addition, credential-stuffing fraudsters often program into bots rudimentary spoofing techniques, such as rotating IP addresses for each attempted login. Where more risk-averse merchants may employ browser or device fingerprinting that can catch this, crypto exchanges are less likely to have these in place.
Phishing attacks ultimately lead to account takeovers and then payment fraud as well. They’re facilitated by the allure of much-hyped stacks of digital coins. Successful social engineering plots may result in the victim being tricked into simply handing over their login details, avoiding any of the possible security roadblocks that the exchange may (or may not) be exerting.
Account takeovers (ATOs) are the end result of the above attacks. When a fraudster gains access to a crypto account, not only will the account surely be drained and the coins tumbled, but if the account holder has also stored credit card information, payment fraud is inevitable. Unauthorized purchases made in the attacked account will result in pressure on the exchange to issue a refund. Worse yet, if the exchange either does not have a refund policy or that mechanism is poorly serviced, this might lead to the victim requesting a chargeback, leaving the exchange with both the loss and the fees.
Payments with stolen cards – such as credit card “fullz” found on the dark web – are easier to use on services that have lower security scrutiny. Mainstream online businesses who are wary of payment fraud will be running checks at payment to make sure there are no discrepancies between the card and the apparent buyer. Information like a card registration address and a disparate delivery address, for example, might raise red flags for a merchant with fraud protection software in place, but the distributed nature of the crypto vertical (and lack of delivery addresses) means that crypto exchanges won’t necessarily consider such instances risky.
Money laundering in crypto is another pain point linked to this type of fraud, as the laundering can take place through exchange-enabled payments.
All of these threats are equally as present for companies accepting card-not-present payments, but crypto exchanges in particular want to smoothen bumps in the customer journey wherever possible. While this ushers in a userbase that is in favor of decentralization, pro-anonymity, and an overall off-the-grid mentality, it also lets payment fraudsters bypass security protocols more easily than at a non-crypto marketplace.
How Do You Detect Payment Fraud in Cryptocurrency?
For crypto exchanges to balance both low friction and high (or legally acceptable) security, risk management software systems like SEON’s dynamic friction present a convenient tool to effectively curb payment fraud.
A protocol of dynamic friction is where obviously good users, as determined by techniques such as IP lookup, browser and device fingerprinting, and email lookups, are presented with the smooth experience that crypto exchanges want. Meanwhile, users whose data returns red flags or question marks can be asked to complete hardened security checks, possibly submitting more data or completing MFA-type security measures. Obvious fraudsters will be flat-out blocked, if that is what the exchange’s risk appetite calls for.
The software scrutinizing data points throughout the customer journey, from onboarding to transaction, to look for anomalies like:
- passwords that have been associated with data breaches, risking credential stuffing
- multiple, apparently disparate users who have the same device fingerprint – also indicating credential stuffing
- accounts submitting payment data that appears very removed from the actual location as shown by device fingerprint or IP check – stolen credentials
- unexpected behavior like a large account suddenly changing payment details or draining the account – ATO
- new account registrations with new email addresses that are not associated with any other social media or online accounts – another potential indicator of an ATO attempt
SEON can be customized to monitor for these interactions, setting thresholds for what constitutes suspicion based on your company’s risk appetite. Notably, as regulations for both AML and customer safety coalesce into existence, these risk appetites may get reassessed. Thankfully, fraud management solutions like SEON can be endlessly retuned to fit into tighter security mandates, and ultimately help crypto exchanges steer clear of debilitating fines, or even sanctions.
Top 3 Custom Rules for Payment Fraud in Cryptocurrency
Crypto exchanges can deploy rules from the SEON platform that address the risks associated with payment fraud. Here are three such rules that help keep any merchant safe, yet be deployed dynamically to suit an optimized crypto exchange experience.
#1: Multiple Accounts With Identical Cookie Hash
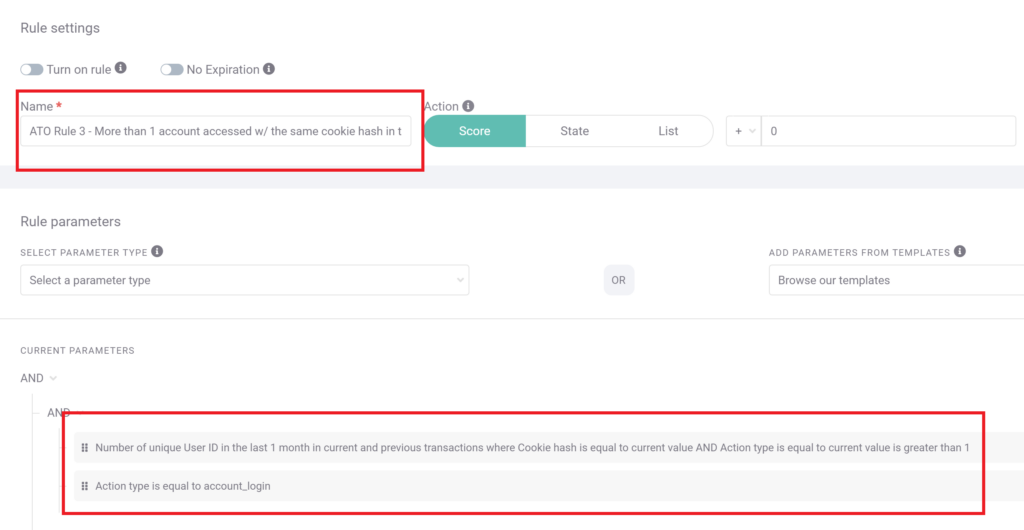
Cookie hashes are a part of browser fingerprinting. This rule is deployed to detect fraudsters who are attempting to test leaked batches of username and password combinations, hoping to find one that gets a successful login.
As the bots that are automated to carry this out are often operated from a single browser, and most will not be clearing their cookies in-between attempts, a user triggering this rule is a strong indicator of credential stuffing.
Note that this rule is set up to trigger at the login stage, and the associated risk score (0 in the screenshot) can, and should, be set to at least pause the user journey – or you risk more stuffing attempts.
#2: User Has Never Connected from IP Country Before
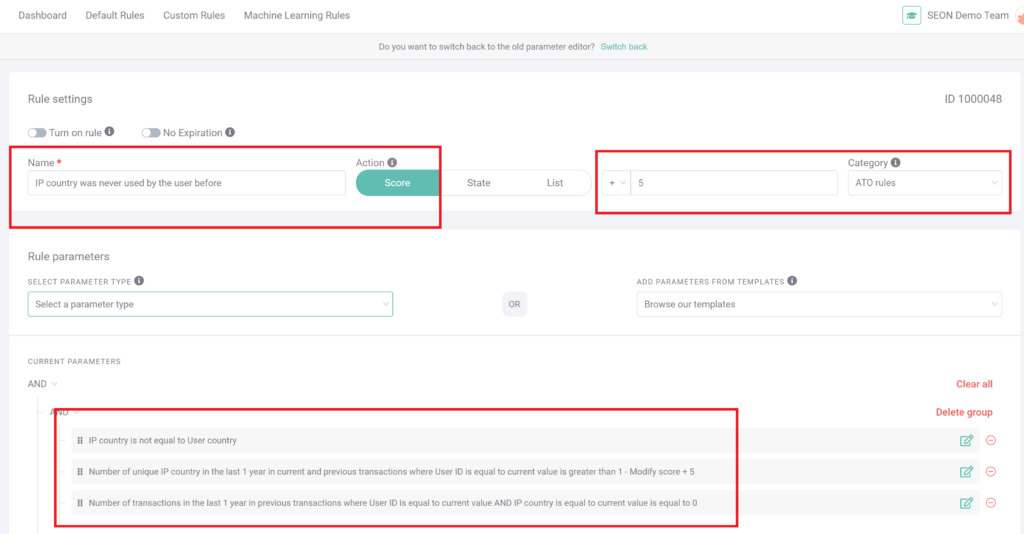
In this screenshot, SEON has been customized to be careful when an account could have been compromised by an ATO.
When a registered user logs in from a new IP location, this rule will trigger. Above, the sensitivity is currently set to a relatively low +5 points to the user’s risk score, but this can be adjusted from the field in the top right, to add more, less or even trigger manual review as soon as it happens.
It is perfectly possible for a legitimate user to be accessing the crypto exchange from a country while traveling, but with other risk indicators, this rule may add up to a risk score that warrants a manual review by a fraud analyst.
#3: Suspicious Spike in User’s Spending
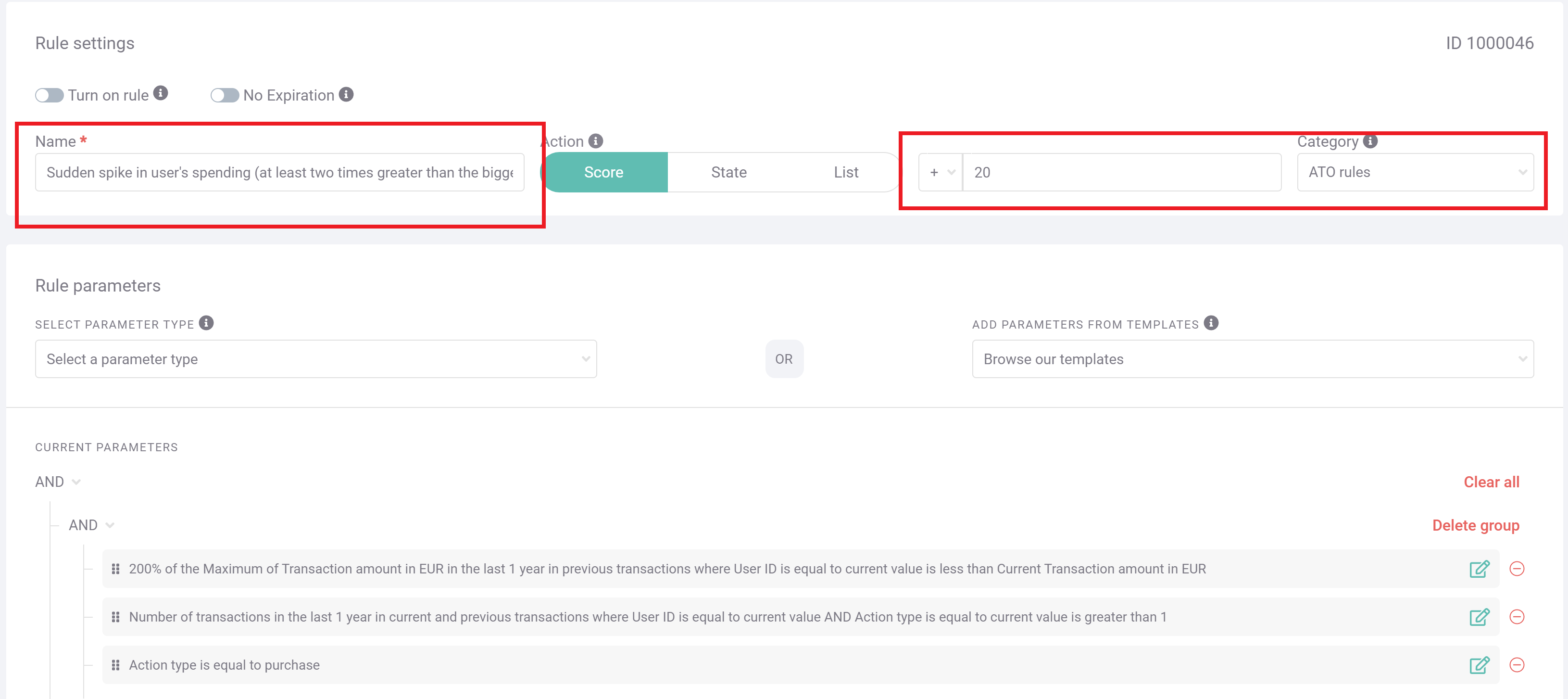
In the event of a successful ATO, crypto exchanges should be monitoring the behavior of users if the fraudsters are to be caught.
Here, SEON has been tuned to monitor purchasing behavior for unusual transactions – in this case for attempted transactions that are historically at least 200% of any previous historical transactions. In the screenshot, the rule is set to add +20 points to the user’s risk score, which will trigger a rejection or review in many cases.
Individual exchanges would be wise to tweak this rule based on risk appetites and any historical patterns of fraud within their own infrastructure.
SEON’s real-time protection, transaction checks, and login monitoring can be customized to stop account takeovers before they cause much damage.
Ask an Expert
How SEON Helps Crypto with Payment Fraud
SEON’s dynamic friction-utilizing technology help cryptocurrency exchanges both fight fraud and maintain a smooth pathway from login to cryptocurrency transaction monitoring.
The methods that payment fraudsters employ to meet their nefarious goals are what SEON is engineered to prevent. The software suite shines when addressing the challenges that the crypto vertical faces: anonymity and necessarily low friction. Even users who connect anonymously, e.g. via a VPN, can be scrutinized for signs of malicious intent from the moment they log in, or attempt to.
By deploying SEON together with enforcing best practices such as spreading awareness of account takeover fraud prevention among your users, you can fight back against payment fraud as well as keep friction to a minimum, ensuring legitimate users appreciate their experience on your platform.
Related Case Studies for Cryptocurrency
- Crypto Platform Deploys SEON Custom Velocity Rules to Block Money Launderers and Cut Down Fraud by 60%
- FIAT <> Crypto API Reduces Weekly Chargebacks From $40K to $0 Thanks to SEON