Every year sets a new record for the number of exposed records in email data breaches. In 2022, 15M records were lost due to leaks and breaches. Of course, this sounds like bad news for everyone involved – both companies and users whose records will be made public. But we can also use that information judiciously to protect them. Let’s see how it works in practice.
What is an Email Data Breach?
An email data breach is an event where private email addresses are made public. It is also known as an email data leak, because the addresses and associated data are likely to be leaked on online forums, the darknet, or other public spaces.
Email data breaches can be the result of cybercrime, phishing, internal sabotage, or fraud attacks. Criminals usually target email addresses and their associated login details, such as passwords, to infiltrate existing user accounts. This is why email data breaches are often synonymous with account takeover fraud, where fraudsters access someone else’s account in order to withdraw money, mine it for information, or use it as a phishing tool to target other victims.
The type of companies more likely to be targeted for email data breaches includes social media companies, neobanks, financial institutions, BNPLs, e-wallets, online stores, and iGaming accounts – among others. However, in recent years, email addresses have been leaked from any kind of company, including travel operators, car companies, healthcare, nonprofits, education, etc.
Why Does an Email Data Breach Happen?
The reason email data breaches happen in the first place is that criminals can resell the information on the dark web. That’s the first thing that will happen. You’ll come across huge data dumps, as they’re called, which are sold in bulk on shady internet forums.
These account login details are used for account takeover (ATO attacks), or credential stuffing, where fraudsters attempt a combination of the email and password on numerous services.
As a side note, this is why using slightly customized passwords for different services can backfire. If your Gmail password is passw0rd4Gmail, it’s easy enough to infer what it will be for LinkedIn.
If fraudsters do succeed in getting in, they will mine the accounts for personal details or, ideally, currency (crypto fiat and even bonus points).
Now, if we switch over to the side of the company that lost the data, it will probably have to inform its users. This is especially true for European companies since the GDPR forces companies to publicly acknowledge when they’ve lost customer records.
Once the user is made aware of the leak, they tend to change their passwords – but not their email address. This is where it becomes interesting from a fraud management perspective.
How to Prevent an Email Data Breach
Preventing email data breaches takes effort from your security team, IT team, and every employee and executive. Training and education go a long way, and here are steps you can implement today:
- Educate employees about email security: That includes teaching everyone about how to securely open attachments, verify senders’ information, and scan for malware and viruses.
- Promote anti-phishing practices: Another example where prevention is better than the cure. If you can teach everyone how to detect phishing attempts and social engineering, you’re essentially blocking access to any potentially valuable data.
- Secure logins for everyone: A lot of data breaches happen after criminals log into your business using other people’s accounts. You can secure the login stage to prevent what is known as an account takeover attack.
- Boost your IT security: Last but not least, you should ensure you are ready to handle potential DDoS attacks, MitM attacks, Cross-Site Scripting attacks and other techniques that could leave your site at the mercy of cybercriminals.
As an online user, if your email address has been leaked in a data breach, you may want to consider the following steps:
- Find out what other info was compromised: you may need to check manually if your password or PII (personal identifying information), such as a social security number, was also leaked.
- Change your passwords: if your email address was leaked, chances are that an account password was leaked with it too. Whether you reused your passwords or not, it’s worth considering a quick update.
- Monitor your account for unusual activity: you may need to log into the account whose details were leaked. If the password has been changed, contact the company immediately.
- Be vigilant with your financial information: the worst-case scenario would be if your financial details were leaked. You may want to keep an eye on your credit card receipts, credit score reports, and even consider freezing your cards if needed.
Last but not least, remember that the company that lost your data is responsible for the leak. You may be contacted about a class-action lawsuit or compensated for your loss.
How to Monitor Email Data Breaches for ID Verification?
There are three key ways to monitor email data breaches for ID verification:
- Manual checks: you can find the leaked databases online, and search them for a specific email address. This is handy if you want to search the latest leaked database only, for instance, one that has been made public in the news.
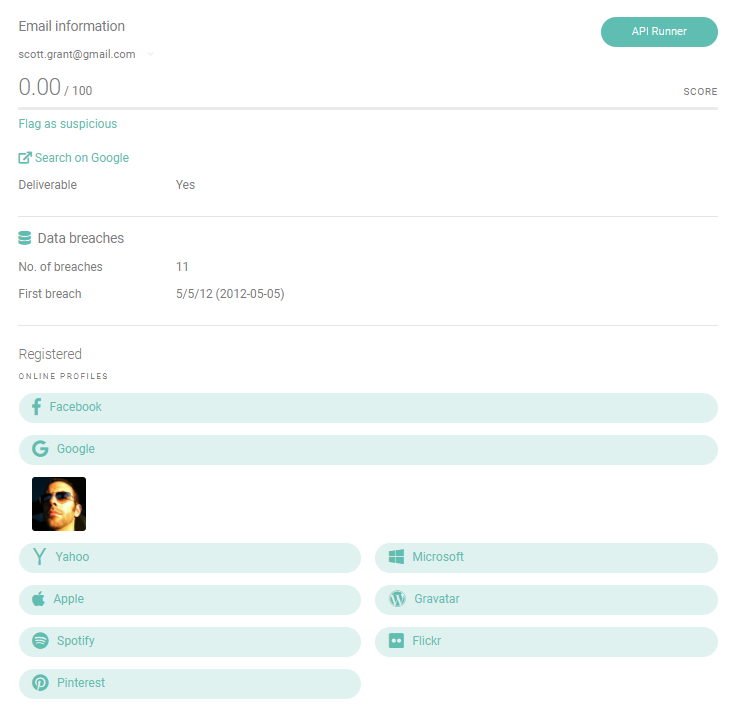
- Aggregate website: some websites let you manually check for specific data in all known leaked, or “pwned”, databases. By far the most popular of them all is haveibeenpwned.com, which, at the time of writing, has a database of 12M leaked accounts.
- Automatic software solution: third-party software can query all the known leaked databases automatically for you. This is done via API request, and the advantage is that you get the results without having to do any manual work (besides the initial software integration).
Note that some software solutions will return extra information such as an educated guess about the email address creation date. Reverse email lookup tools can also find social media accounts, give risk scores, and detect suspicious email addresses from free domain providers or disposable email services.
How Does Monitoring Email Data Breaches Help ID Verification?
While email data breaches sound like bad news, they can be turned into a force for good. That is, in the context of fraud prevention and especially ID verification, where you can check if data has appeared in a breach before. Here are the key points to understand:
- An email address that appears on a data breach check is likely from a legitimate user. It means the address is mature, and you may even be able to infer its age.
- An email address that doesn’t appear on a data breach check should be considered riskier. It may be freshly created, or even a throwaway.
In other words, if you learn how to verify if an email was in a data breach, you have a tremendous advantage when it comes to creating a full user profile for ID verification.
Why Is It Important?
ID verification can create a lot of friction for users who want to sign up for your service. For instance, a full selfie ID video or uploading ID documents can be a frustrating experience. It’s also expensive, as you will need to deploy the appropriate resources (often a third-party solution).
However, checking emails is a fast, frictionless solution that can give you a great pointer about whether the user should be trusted or not. It’s lightweight, affordable, and the solution of choice for companies that want to flag fraudsters as soon as possible (for instance as part of a pre-KYC check).
How to Verify Users with Email Data Breach Checks
The good news is that data breaches can be turned into a force for good. That is, in the context of fraud prevention, where you can check if data has appeared in a breach before. Here is how it works:
Email Checks at the Signup Stage
When users sign up for your service, chances are they must provide an email address. We’ve previously covered the merits of an email analysis tool in another post, but in the context of data breaches, here’s the key takeaway:
- An email address that appears on a data breach check is likely from a legitimate user. It means the address is mature, and you may even be able to infer its age.
- An email address that doesn’t appear on a data breach check should be considered riskier. It may be freshly created, or even a throwaway.
This is a tremendous advantage in modern credit scoring, where you need to calculate how risky a user is based on as little data as possible.
You can read more about how to reduce fraud with reverse email lookup here.
Email Checks at the Login Stage
Things get even more interesting at the login stage. One way to ensure only legitimate users get into their accounts would be to keep an eye out for the latest data breach news, and manually check if their login details have been leaked.
But there’s a smarter way to automate checks: using a combination of email analysis and device fingerprinting.
Put simply, here are examples of rules you could set up:
- If the email has recently appeared on a data breach check and the user seems to connect from a new device, you should increase the risk. This is highly likely pointing to an account takeover.
- If the email has recently appeared on a data breach check and the user is connecting from a trusted device, you could suggest a password change. It’s never a bad idea to educate users about the value of their accounts to prevent later damages.
You could even go into more sophisticated setups using velocity rules, for instance. If a user email appears on a data breach, logs into their account, and makes a password reset request within a short timeframe: does it mean they are legitimate users worried about their accounts? Or an opportunistic fraudster?
Only a previously installed device fingerprinting solution will help complete the full picture to reduce customer insult rate and improve security.
Partner with SEON to reduce fraud rates in your business with real-time data enrichment, whitebox machine learning, and advanced APIs.
Ask an Expert
Key Takeaways
In conclusion, you can see how checking for a data breach can be a boon for fraud managers. It may seem counterintuitive, but sometimes, the work of cybercriminals can actually be employed against them.
Of course, this is just one weapon in your email profiling arsenal. You’ll also need to complete the picture using every tool at your disposal, such as IP analysis, device fingerprinting, and, ideally, custom rules specific to your industry.
FAQ
Yes. You can go to a website or a fraud prevention tool and type in your email address. The system will check all the latest data breaches to let you know if your information has been compromised.
Yes. You may receive an email alerting you that your information has been found in a data breach.
It means you are vulnerable to an account takeover attack, where someone logs into your account illegally. The best thing to do is to regularly change your passwords – especially if your data has been leaked online.
No. But a phishing email could lead to a data breach. Fraudsters use phishing emails to gather information about people, including company employees and those with access to business data. If they can impersonate them through social engineering, it is very likely that it will result in a data breach.
Sources:
• Statista: Number of data records exposed worldwide from 1st quarter 2020 to 3rd quarter 2022
Further Reading