What Is a Datacenter Proxy?
Like any proxy, a datacenter proxy is a gateway that exists between a device accessing the internet and the website being visited.
Upon accessing the internet, the gateway software replaces the access point’s IP address with one that is temporarily leased from a physical data center. In doing so, the proxy user gets a high degree of anonymity, or can even edit how they appear on whatever page they land on.
Datacenter proxies differ from residential and mobile proxies in their physical presence.
All proxy services replace or obfuscate an original IP address with another IP but – rather than that of a physical residence or a number from a cloud of mobile IPs – a datacenter proxy’s IPs originate from a data center full of servers. In many cases, this means datacenter proxies operate faster, with lower latencies.
By taking on the IP address of a data center, this kind of proxy essentially provides a user with an entirely new location, and can be used for both constructive and malicious behavior behind that veil.
How Do Datacenter Proxies Work?
A datacenter proxy works much like any other proxy:
- A user purchases/installs the proxy’s gateway software on their device.
- Upon accessing the internet, the device first connects to the data center, where it is assigned an available IP from one of their servers.
- With the new IP, the user can then navigate to their site reasonably anonymously.
This process can be used on essentially any device that has the software installed. Some companies offer this service for free, but most operate on a paid subscription model, and they offer to lease addresses in bulk for users that require multiple IPs.
Fraudsters do their best to hide their identity with proxies. How do you catch them? Device fingerprinting detects Tor, emulators, VPNs, mobile & datacenter proxies, and more.
More Information
What Other Types of Proxies Exist?
In the digital sense, a proxy is a gateway that exists between a user accessing an online destination and the destination itself. The gateway exists to create distance between the server and the user’s personal information – a valuable function in a world increasingly concerned with digital privacy.
As the need for privacy and the threats to it have diversified, so, too, have the proxies to fit those needs. Datacenter proxies are still the most common proxy servers, due to their ready availability and generally low price point, but the anonymous browsing market is evermore populated with other, more specific proxies for specific issues.
Though new products with new technology seemingly appear overnight, and some of these terms will overlap with one another, here are some other kinds of proxies to be aware of:
- Residential proxies: Very similar to a datacenter proxy in structure, but replacing the original IP with an IP from a genuine physical address through an ISP. Residential proxies provide a user with an essentially genuine digital presence and generally have a higher price point to match.
- Mobile proxies: When a user accesses the internet via a mobile proxy, their device is first assigned the next available IP at their local connection point (e.g. a cell tower). The IP address will be essentially random, or at the very least a random selection from a pre-existing bank of addresses which may rotate or change over time. Mobile proxies are very similar to residential proxies in their functionality, but provide an additional layer of anonymity because of their relationship to both the network and other devices on the network, which may be sharing the same IP at a given time.
- Forward proxies: A forward proxy is any proxy where the user gains a secondary IP to access a destination with, moving forward from the user to the website. Both residential and datacenter proxies are examples of forward proxies.
- Reverse proxies: Where a forward proxy is designed to protect the user from the data-harvesting of the website, a reverse proxy sets up a layer of protection in front of the website itself. Visitors to a domain will first be directed to a proxy server, where their ID can be looked at and assessed before they are admitted.
- Public, shared, and private proxies: Proxies can be stratified into different sizes based on how many users can access a single gateway. Public proxies will generally have the most users, and thus the most security flaws. Shared proxies, for example a proxy shared by an entire company, will have fewer users and be more secure than a public one, while a private proxy will offer the most security. Notably, public proxies will have the lowest cost, while the security of a private proxy will certainly be the most expensive.
- Anonymous, high anonymity, and elite proxies: For users who want to scale the depth of their anonymity, there are generally three levels of security. Anonymous proxies hide the user’s identifying data upon accessing the web, while high anonymity proxies take the extra step of deleting that data first. Elite proxies offer the most obfuscation, and either provide a genuine but faked set of data, or remove all indications that a proxy is in use at all.
- Transparent proxy: A transparent proxy is usually deployed by a company wishing to control their employees’ online activity (such as which websites they access from work) and so is in no way designed to protect anonymity. Rather, it identifies users specifically, then prevents them from access to anywhere the company deems blacklisted.
- Rotating proxy: A category that most security-minded proxies will fall under, rotating proxies refer to the practice of regularly changing the IP that is assigned to a user upon their request to access the internet. Thus, the user behind the proxy appears slightly different to the server on each visit, making them harder to identify.
Where Do Datacenter Proxies Come From? Who Owns Them?
The market for datacenter proxies is well established and diverse. Part of their usefulness includes the ability to secure an IP in almost any part of the world.
Making a new datacenter proxy is as simple as:
- acquiring the space to hold the servers
- acquiring enough servers to provide a diversity of IPs
- setting up the servers to be proxy servers
- connecting to the internet and getting customers
The simplicity of this model means that market options run the gamut in terms of scale and price. Many ISPs offer all kinds of proxies, including data centers, with legit credentials from their service.
A simple web search will yield many more results, with pricing models based on data bandwidth or number of proxies, going well up into the tens of thousands per month for a bulk lease.
What Are Datacenter Proxies Used For?
Datacenter proxies generally offer online anonymity with high speeds and affordable price points, and there are a great many applications for such services.
While any fraudster appreciates this kind of anonymity, these proxies are by no means illegal, nor are they inherently malicious. That said, almost all the practical applications involve concealing identifying data to work around the existing security protocols of a given domain.
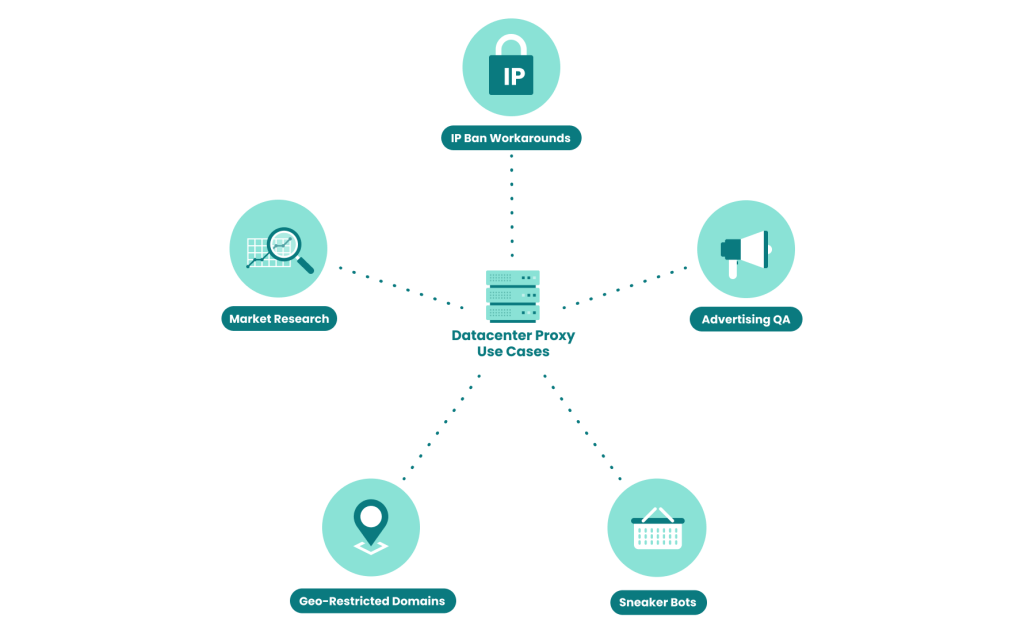
Above-board applications of datacenter proxiees include:
- Market research: Many companies will use a datacenter proxy to operate market research tools – very often, a web scraper. These programs go to specific domains then scan and copy specific information so it can be analyzed. Common data to scrape includes things like comparing the different prices of a single product on different marketplaces, identifying emerging news stories, or monitoring developments on rival websites.
- Accessing geo-restricted domains. Some websites and services only allow visitors from certain regions to access their content. A simple workaround to this is leasing an IP from a datacenter proxy within the permitted region.
- Marketing quality assurance: By employing one, or a number of datacenter proxies, companies can digitally masquerade as their target advertising market, then make sure their promotions are appearing correctly and achieving what they want.
- IP ban workarounds: As datacenter proxies should successfully obfuscate a user’s IP address, a user who has been banned from a website can potentially use one to access that site again. This is a technique that can be used for legitimate reasons, like managing social media accounts that would otherwise be banned for multiple accounts on a single IP.
- Sneaker drops/sneaker bots. The release of some brands of shoes often come with a massive, instant demand as they hit the digital market, and many manufacturers restrict the number of pairs that can be bought by a single shopper. Sneaker bots are increasingly popular programs that usually use datacenter proxies to appear like different people instantaneously. Users are thus able to buy more pairs than normally allowed. Legally, this is a grey area and its legitimacy depends on the T&Cs of the merchant.
Can Datacenter Proxies Be Used for Fraud?
The use of some sort of proxy is par for the course when it comes to digital fraud. As datacenter proxies are plentiful and easily accessible at a relatively low cost, they are a favorite of fraudsters who need a large number of IPs constantly.
Credit card fraudsters will use stolen credit information in conjunction with a proxy to make themselves appear like the genuine cardholder – say, by placing themselves digitally in the correct vicinity. For an unprotected storefront, this might be enough to successfully masquerade as a legitimate customer.
Fraudsters who are controlling a botnet of infected machines will lease bulk IPs from a data center, then make sure their bots are cycling through them regularly to avoid being fingerprinted and recognized. These botnets can then be used to perpetrate criminal, fraudulent activity that requires potentially thousands of zombified machines.
One common use case is in all sorts of advertising and affiliate fraud. For example, click fraud where a botnet is used to generate ad revenue. This is achieved by taking advantage of cost-per-click and cost-per-impression schemes, where companies pay advertisers based on the amount of traffic directed to their storefronts through ad links. After using other methods to direct traffic through the paying gateways, fraudsters could also reroute traffic through proxies to make them appear as higher-value impressions upon arrival at the affiliated website.
Though datacenter proxies are offered by legitimate businesses, including ISPs themselves, they are also a convenient tool for fraudsters. Proxies will be a part of online fraudulent activity in many cases, with datacenter proxies being the most common type among them.
How Can You Fight Fraud Enabled by a Datacenter Proxy?
In the fight against digital fraud, there is always a thin line to walk between security and friction. When it comes to datacenter proxies, many fraud-fighting tools will flag IPs from datacenter proxies as suspicious, but no company wants to turn away good customers just because they’ve been identified as proxy users.
Plus, there is much more that sophisticated software can gather from someone’s IP than whether they are using a proxy. Enter an IP address in the form below to see an example of SEON’s data enrichment:
Beyond this, very valid user has a footprint much larger than just an IP, and anti-fraud software builds a profile based on dozens, if not hundreds, of data points, which can’t necessarily be hidden with a proxy.
Advanced anti-fraud tools that go well beyond simple IP reputation scores are required for a company to be confident about datacenter customers.
These data points include their device fingerprint – screen resolution, installed browser plugins, languages – and often have nothing to do with the IP origination. There are also velocity checks and, indeed, proxy detection.
With the right fraud prevention software in place that is adjusted to an individual business, the costs will always be outweighed by the number of fraudsters deterred – and all that would have been lost had they been successful.