Account takeover (ATO) fraud continues to rise in 2024, with no signs of slowing down in 2025. Global losses have already reached nearly $13 billion, and forecasts suggest they could climb to $17 billion next year. These attacks are becoming more frequent and more advanced, putting both businesses and users at greater risk.
This guide breaks down why accounts are such a common target, how attackers gain access, and what you can do to stay ahead with practical prevention strategies.
What Is Account Takeover Fraud?
Account takeover fraud (ATO) is a type of identity theft where a fraudster gains unauthorized access to a user’s online account, typically by stealing login credentials. Once inside, the attacker exploits the account for personal or financial gain.
Many users refer to ATO simply as “account hacking,” especially when they discover that someone else has accessed their profiles without permission. This kind of fraud can affect banking accounts, eCommerce profiles, email inboxes, and more.
While financial gain is the most common motive, ATO attacks may also aim to steal sensitive data, impersonate the account holder, access stored payment methods, trick the victim’s contacts, or launch scams like phishing or business email compromise (BEC).
How Does Account Takeover Fraud Work?
There are many paths to successful ATO fraud. It works different depending on the attack vector:
- Opportunistic: A fraudster stumbles upon someone’s login details. This could be accidental, or more sophisticated, for example following a mass phishing email campaign. It could be because of an easy-to-guess password, brute force, or via malware such as a keylogger
- Bought credentials: Every huge data breach means a proliferation of ATO attempts is sure to follow due to the account details being sold in bulk for cheap on the darknet
- Credential stuffing: This is when fraudsters automate attacks (usually with bots) using login details they bought from a leaked database.
- Exploiting security vulnerabilities: This is where unpatched security holes are used to gain unauthorized access to a system. For example, Cross-Site Scripting (XSS) and Server Side Request Forgery (SSRF)
- Targeted attack: Fraudsters will often target specific accounts which they know to be valuable. In social media and gaming, for instance, there is a huge market for what is known as OG accounts or accounts with a rare, short handle. To target these accounts, fraudsters often rely on spear-phishing techniques (targeted phishing), or SIM-Swapping attacks.
SEON’s anti-fraud tools are designed to detect suspicious usage and uncover hidden fraudsters
ATO prevention solution
How Much Does ATO Cost Businesses?
According to research by Kaspersky, more than half of all fraudulent attacks are actually account takeovers.
While it’s often harder for businesses to quantify ATO losses compared to something like credit card fraud, the impact is far from invisible. The consequences can ripple across multiple departments. IT teams face increased pressure to resolve security issues, while support teams are flooded with customer complaints as users try to recover their accounts. Finance teams must deal with chargebacks, and the brand may suffer as frustrated users turn to competitors.
In some cases, the damage can extend even further — a publicized data breach can shake investor confidence. Research from Bitglass found that a company’s stock can drop by as much as 7.5% following a breach.
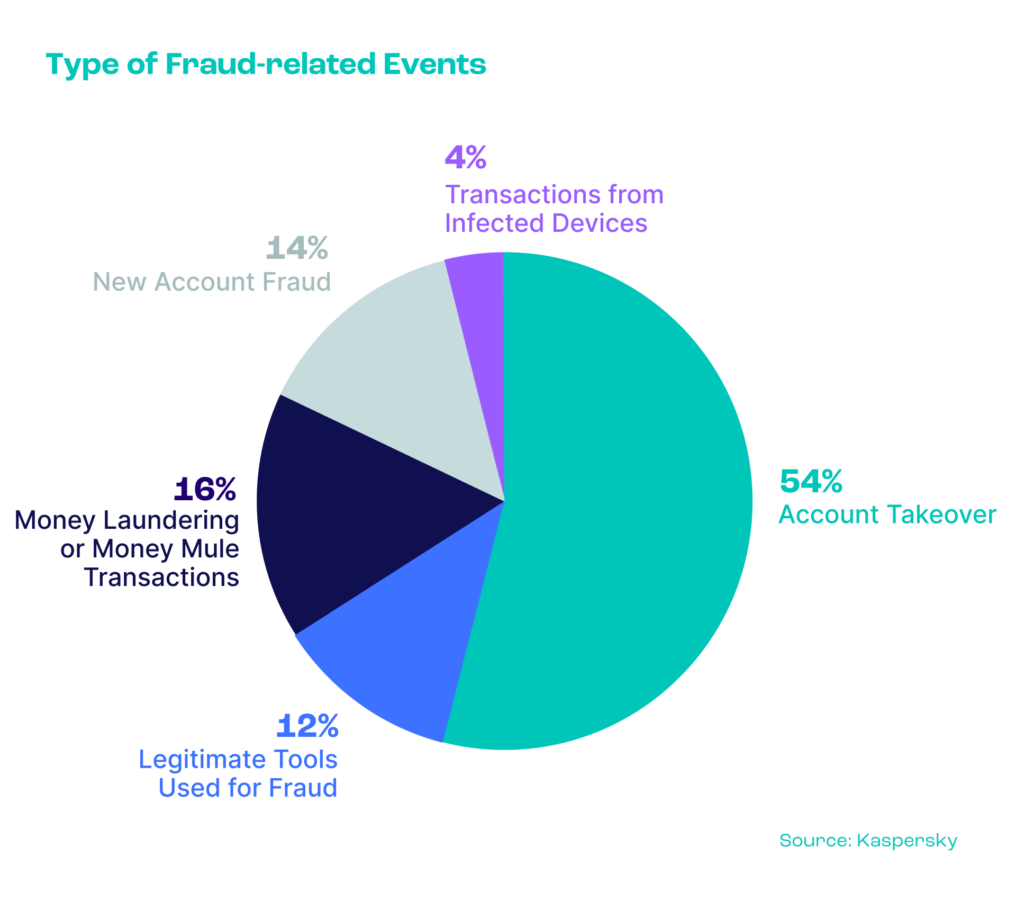
What Are the Signs of Account Takeover?
Employees, individuals, and IT teams must look out for numerous signs of account takeover. These range from unfamiliar transactions and unusual activity on an account to changes to personal details. Let’s look at some of the signs that should cause your Spidey-Senses to tingle:
- Unfamiliar transactions: If you see something you don’t recognize, such as an email in your Sent Items that you didn’t send, an item on your bank statement you don’t remember buying, or a log-in alert for an account you’ve not tried to log in to, it’s a major red flag. This could be account takeover fraud, so don’t ignore it. Notify your IT department, bank, the company the account is with, and/or whoever else is relevant to the account.
- Unusual activity: Higher-than-usual purchase values or changes in purchase frequency could indicate a bank, credit card, or ecommerce account has been taken over. Different log-in patterns (in terms of log-in location, time, or device, for example) could indicate a user account has been taken over. Whatever the type of account, unusual activity is something to watch for.
- Personal information changes: There are plenty of genuine reasons why an account holder might change their registered email address, phone number, or shipping address. That said, when two or three of these all change at once, it is a cause for suspicion.
Businesses should be on the lookout for all the above signs of ATO. It’s also possible to spot attempted account takeover: Repeatedly failed log-in attempts are often a sign of a fraudster trying to get into an account by brute force, so it’s crucial to be alert to this, too.
Account Takeover Fraud Detection
While it can be challenging to catch ATO attempts, these attacks can be detected by monitoring for out-of-the-ordinary account behavior. Deploying fraud prevention and detection software helps you keep track of user activity and helps you spot suspicious patterns.
- Flag suspicious behavior: Look for suspicious account changes in real time, recognize suspicious IP addresses and identify unknown devices or multiple accounts being used from the same device.
- Spot connections between users: Identify fraud rings and sophisticated multi-accounting users who jump from one account to the next by recognizing recurring patterns and connecting seemingly unrelated users.
- Harness the power of Machine Learning: An AI-powered machine learning tool (ideally consisting of both a whitebox and blackbox model) gets increasingly accurate with your feedback and helps you identify the patterns and typical behavior the human eye wouldn’t be able to notice.
Implementing the right fraud prevention and detection solution equips you with the essential tools to proactively monitor user activity and swiftly identify suspicious behavior, effectively blocking account takeover attempts.
3 Account Takeover Fraud Detection Features
Detecting account takeover attempts requires more than just login credentials. Modern fraudsters use tools like emulators, spoofed devices and masked IP addresses, so businesses need deeper insight into who’s really behind a login attempt. That’s where intelligent fraud detection software and tools come in. Here are the core methods that help reveal suspicious logins before damage is done:
Device intelligence
Device intelligence involves gathering and analyzing data about the device used to access an online service, like browser type, OS, screen resolution, and signs of automation or spoofing. By creating a unique device fingerprint, it helps spot unusual logins and risky behavior. Over time, it builds a baseline of normal activity to better detect threats and prevent account takeovers.
IP analysis
IP analysis looks beyond the user’s location as it also identifies patterns like logins from high-risk geographies, sudden changes in geolocation, and usage of anonymizing tools such as VPNs, proxies or the Tor network. With dynamic risk scoring and the ability to whitelist known travel or location changes, IP analysis helps reduce friction for trusted users while catching bad actors.
Behavior analysis with velocity rules
Even if credentials are compromised, fraudsters rarely mimic legitimate user behavior perfectly. Velocity rules allow you to monitor activity in real time, such as the number of login attempts, password resets or changes to account settings, to flag unusual patterns. This form of behavioral analytics is key to identifying account takeover attempts in progress and responding before harm is done.
How ATO Detection Works with SEON
SEON makes it easy to uncover signs of account takeover without adding friction for genuine users. Our platform combines deep device intelligence, advanced machine learning and customizable risk rules to give your team full visibility into risky login behavior.
- Advanced device intelligence: Detect risky device setups instantly, including spoofed environments, emulators or repeated use of new devices. Our solution builds a device history that helps spot new or suspicious connections with confidence.
- IP intelligence: Understand more than just where a user is connecting from. SEON’s IP analysis detects the use of proxies, VPNs, Tor nodes, and high-risk geographies. It also identifies patterns in connection behavior to surface anomalies that could indicate account takeover or fraud attempts.
- Transparent machine learning: SEON’s whitebox machine learning engine analyzes your historical ATO patterns and constantly retrains itself. Results come in the form of clear, human-readable rules, so your team stays in control and can validate findings.
- Behavioral insights with velocity rules: Track and analyze how users interact with your site, from login frequency to changes in behavior over time. These insights power highly tailored risk assessments and real-time decisioning.
With SEON, detecting ATO isn’t just about stopping fraud — it’s about doing it smarter. Our API-first platform adapts to your risk appetite, integrates seamlessly and gives you both proactive protection and a smoother experience for your genuine users.
Frequently Asked Questions
Account takeover involves someone accessing an account owned by another individual without authorization, whereas identity theft involves the fraudulent creation of a new account using stolen identity information. Account takeovers can affect both businesses and individuals, whereas identity theft exclusively impacts individuals.
Monitoring account activity in real time, in addition to user behavior analysis and automated alerts for suspicious behavior is the best method to detect ATO. Additionally, regularly screening user credentials against known breaches and educating users about risks are essential components of an effective detection strategy.
Industries most at risk of ATO attacks include but are not limited to financial services, ecommerce, healthcare, iGaming and government and education sectors due to their access to valuable data and financial assets.