The damage that can come from a criminal taking over one of your online accounts is enormous. The process is known as an account takeover attack, sometimes shortened to ATO (account takeover fraud), and it is a favored method among online fraudsters.
On the plus side, organizations can equip themselves by carrying out ATO risk assessments and ensuring that security checks are robust and regularly implemented. This goes both for internal accounts, for example staff accounts, and customer-facing accounts that could be targeted.
We look at what an account takeover risk assessment is and cover the many ways in which it can be carried out effectively by management looking to protect their organization and its staff.
What Is an Account Takeover Risk Assessment?
An account takeover (ATO) risk assessment is a review process that is used to gauge the probability that an account – usually an online account – could be subjected to the type of cyberattack known as an account takeover. An ATO is when an individual accesses someone else’s online account without permission.
Such a risk assessment can be part of a wider fraud risk assessment for that organization or conducted separately when the need arises – for example, following an increase in data breaches or account takeover attempts at the organization or the sector as a whole.
There are many factors that are considered in an ATO risk assessment, such as the sensitivity level of the account’s information and resources, as well as the extent to which it is robust or vulnerable.
Note that some organizations may conduct ATO risk assessments for their internal employee accounts in particular, while others may choose to focus on their customer or user accounts – and yet others will look at all of these on a system-specific basis.
Partner with SEON to block fraudsters from taking over your customer accounts with minimal friction – to enable growth and reach new heights in customer satisfaction.
Ask an Expert
How to Assess Your Company’s Risk of ATO Fraud
The criteria to assess your company’s risk of corporate account takeover fraud varies from business to business and country to country, but there are corporate regulations in place that ensure some consistency in the best practices.
For example, business decision-makers can assess their organization’s fitness to prevent ATO fraud by determining the extent to which the business follows acceptable use policies (AUPs) and implementing security awareness training. It is also worth gauging which user accounts would be higher risk if breached, and what the attacker would be able to do if they succeeded, so you can strategically implement defenses at specific touchpoints.
Employees should be asked to sign up-to-date AUPs regularly because such policies set out the guidelines needed to ensure that an organization’s computers and its networks are used safely and securely by staff.
On top of this, risk management software & awareness training helps staff to be more vigilant in their use of company equipment by educating them on such ATO risks as leaving passwords on paper or remaining signed into unoccupied computers.
Computer System Security ATO Risk Scenarios
Computer system security risks in the context of ATO fraud are numerous but there are two key factors that allow them to persist: human error, which leads potential ATO victims to let their guard down to fraudsters; and cyber-attacks, wherein malicious actors use tricks online to exploit potential ATO fraud victims – even despite their best efforts to be safe online.
Human error usually means that the computer system security risk could lead to an opportunistic ATO fraud attack, and cyber-attacks are usually the means by which a premeditated ATO fraud attack may occur.
Human Error in Computer System Security Risks
There are countless ways that human error may lead to opportunistic corporate ATO attacks. In fact, some fraudsters may even target users who are prone to accidentally leaking their personal details – which is an example of the fact that human error can also play a big part in premeditated ATO attacks.
In either event, here are some of the key scenarios in which, through human error, users make themselves more vulnerable to computer system security risks:
- A user accidentally emails their login details to an unintended recipient.
- A user leaves their credentials written on paper and fails to hide them properly.
- A user accidentally downloads malware, meaning that a cyber-attacker could then use remote administration tools (RATs) to remotely witness their login details the next time they enter them into their computer. RAT attacks are examples of ATO fraud attempts that can stem from both premeditated and opportunistic means.
Cyber-Attacks in Computer System Security Risks
Next up, let’s look at some of the key scenarios in which premeditated cyber-attacks may exacerbate computer system security risks:
- An ATO fraudster tricks a user into disclosing their log-in details by posing as an IT manager. This is one of the many ways that cyber-attackers can use social engineering to achieve their goals.
- An ATO fraudster uses credential stuffing, which is when automated software is used to try out stolen login details on multiple online accounts.
- An ATO fraudster exploits users’ reliance on outdated – or outright malicious – software to gain account access through the given system vulnerabilities.
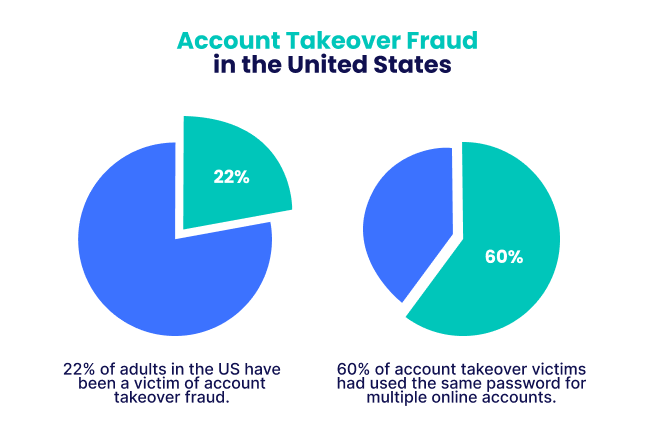
How to Assess Computer System Security Risks
To assess computer system security risks in the context of account takeovers, make sure to check the preparedness of users and user accounts, and check how secure the software is – including users’ software and the digital infrastructure.
For example, if you are a CEO concerned about your staff being vulnerable to ATOs, these are some of the ways that you can ensure both your users and their computers are as safe as possible:
- Ensure, through training and other resources, that all staff is educated about computer system security risks, particularly in the context of ATOs.
- Ensure that all users are using up-to-date operating systems and the best possible protection software.
- Ensure that all users know exactly who they’re talking to whenever conversations about remote access, login credentials, and other sensitive information take place. If in doubt, they ought to try to contact that party in a different way, to verify – for example, by picking up the phone.
- Ensure that your staff members understand the value of going paperless: With the right password protection in place, no one can leave digital log-in details lying around – but they can certainly do so if they’re careless with their printed or handwritten notes.
How to Assess Physical Security Risks
Physical security risks of account takeover fraud are the presence of any physical objects – or otherwise the lack of physical objects – that can be exploited by fraudsters. For example, the presence of paperwork with passwords written on it is a physical security risk, just as the absence of security cameras is a physical security risk.
One can assess the level of physical security risks by taking stock of what tangible resources they do and do not have in their given premises. For example, if you were in charge of an organization’s anti-fraud security efforts, these are the things that you would need to ensure that the premises don’t have:
- loose papers or mail containing sensitive information
- doors with weak or nonexistent locks
- unlocked computers, phones, and other communications equipment
Also in the context of physical security risks is the need to ensure that the premises do have:
- vigilant security staff
- high-definition, always-on security cameras
- fully-functioning door locks and alarm systems
By ensuring that your premises don’t have physical items that are high-risk do have physical items that boost your protection, you can make an assessment that your organization is well-equipped to counteract the risk of account takeovers.
How to Assess Personnel Security Risks
When conducting an account takeover risk assessment, it is crucial to also consider security risks stemming from, or linked to, employees and contractors. Anyone in charge of their organization’s security measures against account takeovers must ensure that both the general staff and the security staff are vigilant and well-trained – and that there is little potential for any insider threat to do harm, be it deliberately or not.
Bearing in mind that the presence of trusted personnel and the absence of untrusted personnel is key, these are some of the factors that should be considered in assessing personnel security risks.
- the level of knowledge and accountability that both the general staff and the security staff have in securing sensitive information
- the level of tolerance that all members of staff have in allowing non-personnel inside the premises
- the level of scrutiny that hiring managers take in ensuring that their new starters should be considered trusted personnel within the premises
By assessing factors such as the above, as well as carrying out regular checks to verify that the right measures are taking place, you can ensure that you have a viable risk assessment when observing the level of personnel security risks in your organization.

Assessing the Risk of Customer Account Takeovers
Depending on its demands, risk appetite and regulatory needs, an organization may also choose to conduct an account takeover risk assessment focused on the possibility of user or customer accounts being taken over. For example, this can be an online shop where consumers can create shopper accounts and store their card details, or an online platform that provides access to services, such as video streaming.
It is quite obvious that both of the above have a lot to lose to consumer account takeovers. Beyond the reputational damages that follow breaches – which in some locales organizations are required by law to disclose publicly – there can also potentially be financial damage to the company itself through chargebacks, and even the risk of the fraudsters finding their way deeper into your systems or sensitive information depending on the type of account that has been hijacked.
With customer accounts, assessing takeover risk basically boils down to considering the following:
- How well protected are the accounts? This concerns both sides of the equation:
- Do you require multi-factor authentication to grant access? How about passwords? Biometric authentication?
- What systems do you have in place for fraud prevention and cybersecurity?
- Is your user authentication workflow airtight?
- Have you invested in risk monitoring software?
- How lucrative are these customer accounts as targets? This relates both to the type of organization and the information within accounts:
- Do you provide a way for customers to store payment information and personal information on their accounts?
- Are there any digital wallets involved, in fiat currency or otherwise?
- What can they do on the account itself? Can they, for example, apply for a loan or make a payment?
- What level of control are these users granted over systems? Could there be any backdoors and gaps in your higher-level accounts?
Once you have a complete account takeover risk assessment, you can better plan your strategy to both prevent and mitigate against attacks on your users’ or customers’ accounts.
Best Practices for ATO Risk Assessment and Prevention
The best practices of ATO risk assessment and prevention involve identifying that the correct items, personnel, and systems are in place as well as ensuring that those resources are equipped to counteract account takeover attempts.
In other words, to assess the risk of account takeovers as well as to prevent them, you must ensure that the best security resources are not only present but also well-implemented.
Here are some key best practices for ATO risk assessment and prevention:
- Identify the extent to which the organization’s occupants/staff are ensuring that they are securing sensitive information.
- Identify the extent to which both the security staff and security systems are present and operative.
- Identify which, if any, members of staff have multi-factor authentication in use – and ensure that those who do not have it start using it.
- Identify the extent to which your organization is prepared to freeze accounts that are subjected to takeovers. It is vital to note that the first priority when an account has been taken over is freezing it, to prevent further harm.
- Research authoritative advice to further guide your risk assessment and prevention strategies. For example, LexisNexis provides the warning that business owners will be held accountable in the event that their customers experience an account takeover. This is crucial advice to consider when deciding how to implement your own best practices.
By acting on the above, as well as implementing further measures when required, you can prepare your digital infrastructure and your staff to counteract account takeovers, as well as mitigate most harm from successful attempts.
Our fraud detection tool helps improve the customer experience, minimize the need for manual review, and boost your growth and revenue.
Read the Case Study
Fighting Account Takeovers with SEON
SEON’s industry-agnostic fraud prevention solutions are equipped to counteract account takeover fraud at various touchpoints – and can be further augmented through custom rules as well as machine learning rules.
The way that SEON does this is by offering its users the ability to customize their API calls to home in on what they deem to be suspicious activity.
User activity is considered within the dimension of time – for example, any failed login attempts are monitored, with each consecutive one adding to the risk scoring. The process is further informed by SEON’s algorithms, which gather hundreds of data points to gauge every user’s intentions and true identity.
This is not done just at the login stage: The system will monitor all accounts for signs of suspicious or malicious activity and flag them in real time, so it’s not just fake credentials that sign off the alarm but also employees who suddenly attempt to access sensitive documents, for example, or customers whose payment attempts fail too many times to be considered accidental.
SEON’s APIs can also flag when an email has been linked to password breaches in the past, by pulling data that has been anonymized with k-anonymity. The sandbox environment allows users to test and determine the right rules for their infrastructure and risk appetite, determining exactly what behavior constitutes a potential account takeover in the making, helping conduct better ATO risk assessments.
To fight the risk of account takeovers, you need to assess the risk of account takeovers. From there, by understanding and implementing account takeover fraud detection, you can ensure that their organization is prepared to prevent ATO fraud at best – and remedy it at worst.
You might also be interested in:
Sources
- Texas Department of Banking: Account Takeover Risks
- LexisNexis Risk Solutions: Preventing Account Takeover Fraud