No matter how big or small your business is, chances are there’s something there to exploit. And it’s not always money. For fraudsters and cybercriminals, any amount of data and information is good enough.
While we’ve already covered a wide range of attacks in the context of account takeover fraud, today, we’ll be looking at a very specific way in which fraudsters put their foot through the door: social engineering attacks.
Now, let’s go over some of the basics.
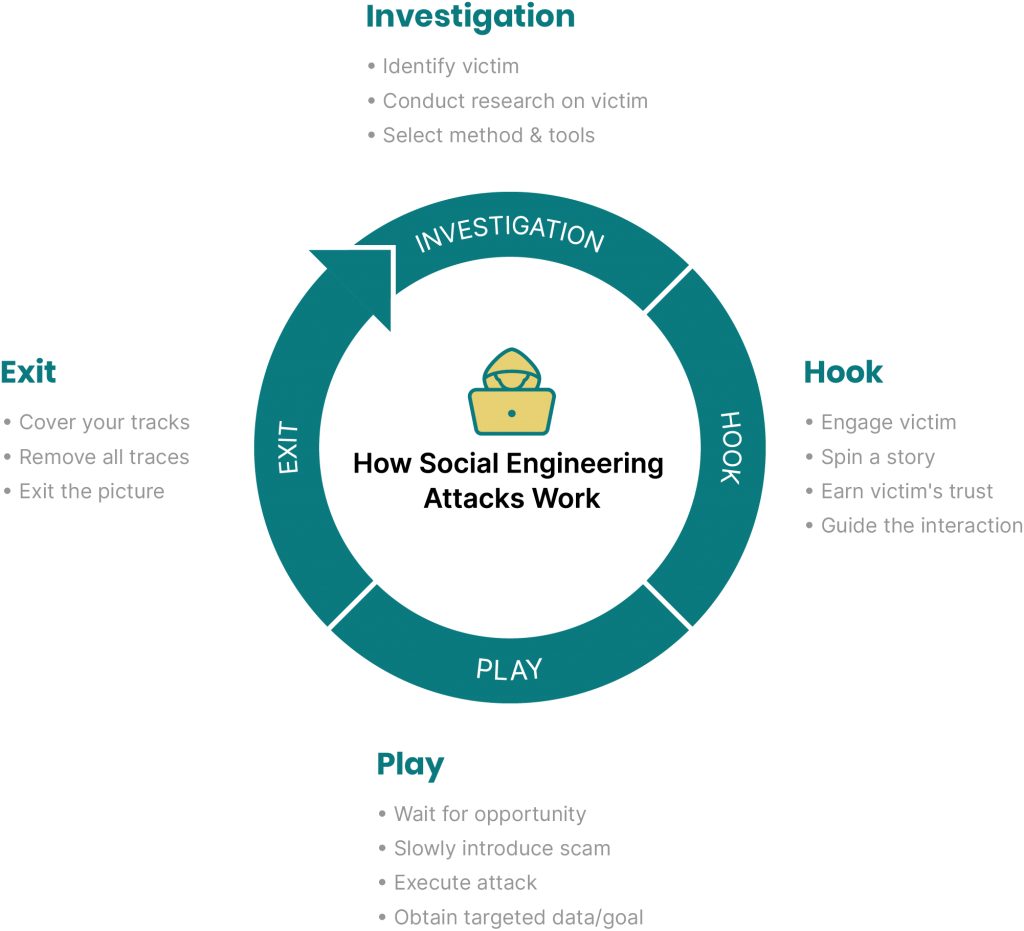
What Is a Social Engineering Attack?
A social engineering attack takes place in three steps. First, the attacker targets a victim. Second, they earn their trust. Third, they gain what they were after, usually breaking security practices or stealing information.
These attacks tend to work based on six principles:
- Authority and trust: where the attacker poses as an authority figure.
- Consensus and social proof: where peer pressure forces someone to commit an action.
- Scarcity: the idea that a victim will miss out if they don’t act.
- Urgency: the idea that the victim will miss out if they don’t act fast.
- Familiarity and liking: convincing victims to perform certain actions by earning their trust / faking attraction.
Practically speaking, the angle of these attacks is increasingly shifting from email communication to phone calls. Email security is quite good these days, but a pressuring phone call can still trick both customers and employees, especially with how easy it is to spoof the caller number, making it seem like they are from a trusted entity.
(Pro tip: if you get a phone call from someone who is claiming to be from your bank, offer to call them back.)
An excellent example of a sophisticated social engineering scam is the one perpetrated against Google and Facebook. A Lithuanian group set up a fake company pretending to be a manufacturer working with the two tech giants.
They then sent phishing emails to Google and Facebook employees, invoicing them for services that were genuinely purchased, but directing them to send money into the wrong accounts. Between 2013 and 2015, this social engineering attack is estimated to have help steal more than $100M.
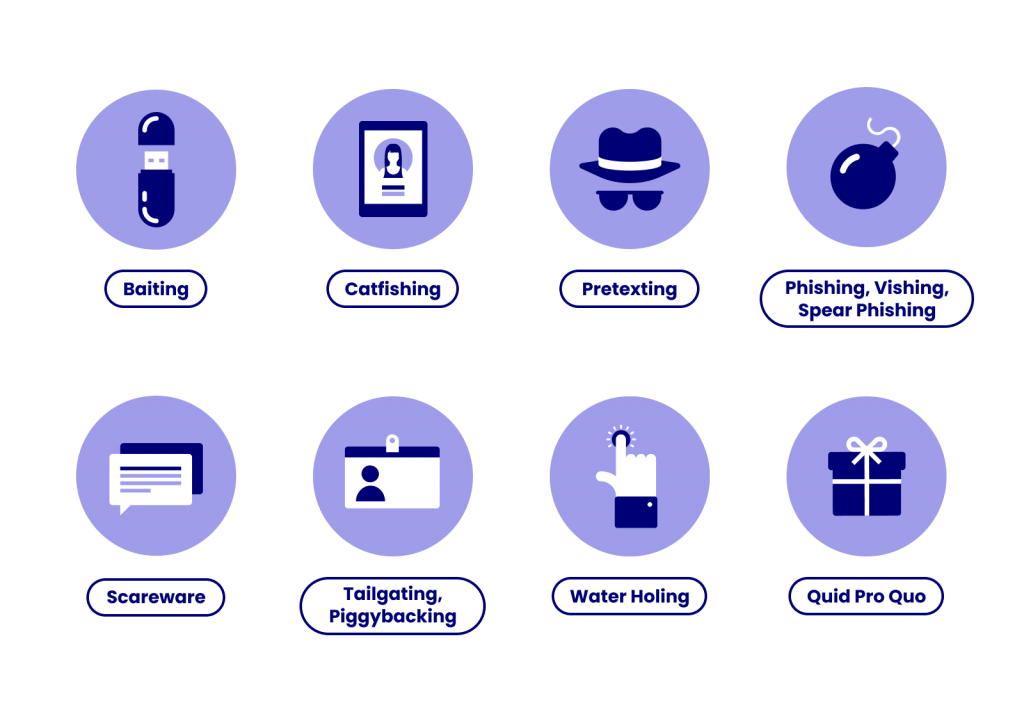
8 Types of Social Engineering Attacks
Below are 8 examples of the most common scenarios you might encounter at your company.
Because social engineering is such a broad term, it helps to break it down into different attack techniques.
1. Baiting
Baiting, as the name suggests, takes advantage of a victim’s curiosity or greed. A trap is set up by the attacker and designed to push someone to commit a specific action.
An example of a physical bait would be a USB drive left unattended on someone’s desk. Would you plug it in to check out its contents? Unbeknownst to you, it could be deploying malicious software on your computer, such as ransomware.
But baiting can also work digitally. An online form or an enticing advertisement can accomplish the same goal.
2. Catfishing
A well-known form of social engineering is catfishing. It is a deceptive activity based on creating a fictional persona that earns a victim’s trust. A close relative is romance fraud, whose rates have skyrocketed in recent years.
The real-life equivalent is called a honey trap, where an attacker pretends to be romantically interested in the victim to extract what they want.
3. Pretexting
By stringing a series of lies together, attackers can convince victims that they are a co-worker, bank official or government agency. They establish trust with the person and convince them to answer security questions to confirm their own identity.
The psychological trick puts victims on the defensive, who feel they need to clear their good name, revealing important personal information in the process (social security number, bank account details, etc…).
4. Phishing (Vishing & Spear-Phishing Attacks)
By far the most common type of social engineering has to be phishing and relatives such as vishing and spear-phishing attacks. All three are designed to extract user or employee information. The differences in the terms are purely technical:
- Phishing: any kind of messaging campaign designed to redirect the victim towards a specific form, site or checkout. Common examples include sending an SMS that tells the victim to log into their bank account to redirect them towards a copy of the bank’s website.
- Vishing: phishing done using voice technology such as a Skype call or fraudulent voice message.
- Spear phishing: this is targeted phishing focusing on an individual. Company executives or customer service representatives are increasingly targeted due to their access to important company information.
Other forms of this kind of social engineering include smishing (SMS phishing) or angler phishing (carried out via fake customer service accounts on social media).
It’s worth noting that recent years have seen an increase in phishing using deepfake technology, both for voice and video. The technology allows fraudsters to impersonate someone by feeding clips of a real person to software and reprogramming it to make it say what they want.
In the context of social engineering, it’s often used to gain trust, for instance by telling an employee to wire money to a specific account by posing as an executive.
5. Scareware
Scams work at their best when the victim is under stress, which is why attackers have created an entire genre of malware called scareware. It involves frightening the victim into performing an action, such as downloading a malicious antivirus under the pretence of fixing a computer error.
Scareware is often distributed via spam email or pop up advertisements and tends to target older, less tech-savvy generations.
6. Tailgating & Piggybacking
The heist movie classic, which sees bad agents impersonate a delivery driver or janitor to access restricted areas. While most corporate settings have security systems in place to avoid this kind of infiltration, it can be surprisingly easy to get past a front desk if you’re confident enough.
7. Water Holing
Regular users of a website have already established trust with the company. While a victim may not click a link from an unrecognised email address, they’ll have no problem clicking it if it’s on a website they frequent often.
A water hole attack involves injecting malicious code directly into a targeted website that the victim is known to frequent.
8. Quid Pro Quo Attacks
Quid Pro Quo attacks are named after the Latin term for a favour granted in return for something. These attacks simply involve promising services or goods in exchange for what the fraudsters are after.
Funnily enough, the bar doesn’t have to be set particularly high. Attacks have been successfully launched on employees simply by offering them a bar of chocolate in exchange for their login credentials.
How to Protect from Social Engineering Attacks
You can’t teach common sense, but you can still put all the odds in your favour when it comes to anticipating how to prevent and protect your company against a social engineering attack, here are 11 examples:
Educate Employees and Users
First of all, make sure social engineering is covered as part of your employee security awareness training and that everyone has understanding of the current attack trends
Check Sources and IDs
Whether it’s an email header, phone call or URL or contractor invoice. It’s worth doubling down on security measures by asking for ID or ID proofing online.
Have Clear Security Protocols and Use Passwords
Clarify the exact steps for your agents on how to handle password or email changes or unblock requests. User accounts are valuable for fraudsters, and they will be persistent in keeping them, as explained by Anonymous G, an active fraudster, on our Cat & Mouse podcast.
Communication Between Departments
For many companies, the weakest link is the customer support team, who might not have sufficient knowhow on fraud. For user verification purposes, there should be some sort of hotline between the departments for added security.
Raising User Awareness
The most common form of social engineering attack against your customer will be a phone call where the scammer will claim to be a representative of your company. Educate and warn your customers, clarifying not just where you might contact them, but what is the type of data you would never request – such as card numbers, who they transact with, personal details, etc.

Leverage ID Proofing Technology
Social engineering happens when you can’t confirm who you’re dealing with. In the digital world, this is exactly what ID proofing attempts to solve.
A reverse email lookup search, for instance, can reveal the risks associated with a certain email address. An attacker might register an email that looks like it matches the details of the actual account holder (firstname.lastname), but it will not have the corresponding social media profiles you would expect.
Similarly, checking an IP address for people getting in touch via a contact page can immediately help you decide if you’re dealing with a legitimate user or someone using either a proxy or is attempting an attack from a country where the original user never was before.
The same can be said for phone numbers: a legitimate user will likely call you from a number that’s associated with their messenger profiles, while a fraudster will use a virtual number or a burner phone.
For more advanced verification methods, see our post on OSINT – Open Source Intelligence. You can also consult our list of the best reverse email lookup tools.
Secure your Devices and Premises
Anti-malware and anti-virus software should be deployed and kept up to date. Company software and firmware should also be patched against the latest vulnerabilities. Make sure employees are aware of the potential risks when using company equipment, especially things like public Wi-Fi or rooted phones.
Similar security measures apply to company premises. You need to control every aspect of your offices, from desk security to waste management.
Hire Social Engineering Services
Finally, you may want to look at hiring social engineering services, performed by white hat security experts and consultants. They will test your employees, website and offices for vulnerabilities and deliver in-depth reports about where your weak spots are.
Social Engineering Scams vs Phishing
If social engineering sounds a lot like phishing, it is because both practices are related. Social engineering, however, is a broader term. Bad agents who use social engineering may do it to access secure areas or to find web vulnerabilities. Phishing, on the other hand, is specifically designed to gain personal information such as login credentials or credit card numbers.
In that sense, every phishing attack is a form of social engineering. But not all social engineering is necessarily phishing.
What Are Social Engineering Services?
There are companies that act as security consultants for your business. They will perform certain tests to attempt to obtain information from your website, users or employees. By highlighting vulnerabilities, they can help you protect against cybersecurity and fraud attacks, such as social engineering.
When it comes to social engineering attack prevention, education is the best tool in your arsenal. Simply being aware of the scope, resources and sophistication of social engineering attacks can be enough to spot something suspicious before it’s too late.
At SEON, we help companies deploy tools that protect employees and users – especially in the context of authentication at login and signup.
SEON is more than just a software solution, it is your business partner in fraud fighting
Ask an Expert
Frequently Asked Questions
The most common type of social engineering attack is by far phishing. It exploits human error in combination with technology, such as malicious links or SMS sent under a fraudulent identity.
Yes. It social engineering is a crime that may lead to legal penalties.
Technically, social engineering is not hacking as it only deals with people, not IT equipment. However, social engineering is often performed in combination with other cybercrime, one of which is account hacking.
According to a 2018 study, two out of ten company employees will be targeted – and fall for social engineering techniques.
You might also be interested in reading about:
Learn more about:
Digital Footprinting | Browser Fingerprinting | Device Fingerprinting | Fraud Detection API
External Sources:
- Justice.gov: Lithuanian Man Pleads Guilty To Wire Fraud
- BBC: Romance fraud on rise in coronavirus lockdown
- Forbes: A Voice Deepfake Was Used To Scam A CEO Out Of $243,000
- Science Daily: Social engineering: Password in exchange for chocolate