Gabor Gulyas, data privacy and web tracking expert, shows us how fraudsters use browser spoofing to hide on your website.
In a previous article, I went over some of the basic techniques fraudsters use for browser and user agent spoofing.
Today, we’re going for another deep dive, inspired in part by the research paper Taming the Shape Shifter: Detecting Anti-fingerprinting Browsers. It’s going to be quite technical, but a fascinating look at how the bad guys operate!
What Is Device Spoofing?
Device spoofing is a practice where people use specific tools to make it look like they are using different devices (phones, tablets, PCs, etc.). The tools generate software and hardware information designed to fool monitoring systems.
Because websites monitor network traffic to improve security against fraud and attacks such as denial of service attacks, fraudsters and cybercriminals spoof the devices they use to hide their intentions.
What Is an Anti-Fingerprinting Browser?
[bctt tweet=”While these browsers are branded as protecting people’s privacy against tracking… their price and the technical skills needed to use them makes it clear: they focus on a different market.” username=”seon_tech”]
Fingerprinting has two purposes on the web: advertising parties use it to track people and collect information about them, and anti-fraud teams, like SEON, use it for security: e.g. detecting fraudulent activities, even when fraudsters try to hide their devices.
Alongside the development of fingerprinting techniques, device fingerprinting solutions also become increasingly sophisticated, pushing fraudsters and their suppliers to develop their own tools, purpose-built to evade detection.
This gives anti-fingerprinting browsers a euphemistic name: they are branded as a way to secure and protect people’s privacy against tracking. While this is true, their price and the technical skills needed to use them makes it clear: these products focus on a different market.
As you can imagine, those who use them not necessarily have the best intentions in mind.
In fact, these anti fingerprinting browsers are built for device spoofing that’s tailored to mimic the online configuration of a real user – useful if you want to have a stolen credit card number or bank account and want to pass off as the legitimate owner.
These tools also allow rapid configuration switching to change their online “appearance” every minute. This is used to avoid detection of repeated attempts, and to test the best configuration that can scale, for instance, to cover automated bot attacks and general bot detection.
Take complete control over your risk management with SEON software and the support of an expert team
Ask an Expert
Three Levels of Complexity
One way to discover the latest fraudster techniques is to crawl through dedicated underground forums. It’s something the SEON team is quite accustomed to, and this is where the authors of the aforementioned paper compiled a list of all the fraudsters’ tools of the trade.
We can split these into three categories.
Via JavaScript Injection
The simplest tools, such as the ones that we have seen in our previous post, inject JavaScript code snippets into visited websites so they can modify the behavior of the page.
Due to their nature, these tools are typically implemented as browser extensions. Some are shipped in modified browsers, while others are extensions that need to be installed manually.
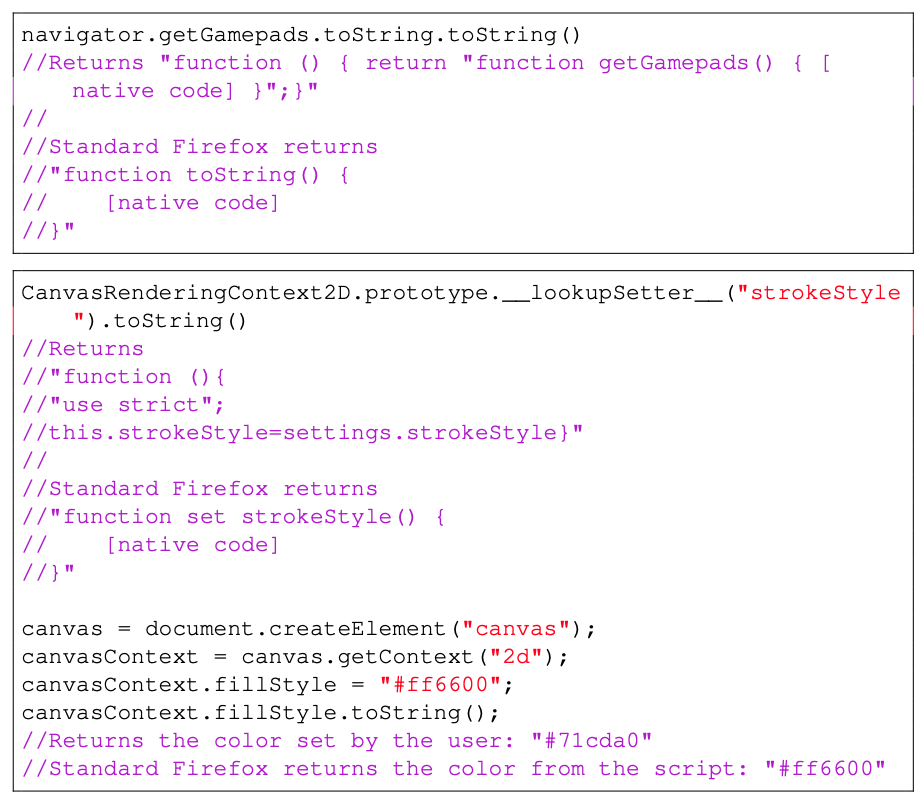
When a site tries to gather information, it’s met with manipulated data. For example, a site trying to access navigation.userAgent will get a different value than that of the default of the browser.
- Strengths and Weaknesses: These tools sacrifice features for ease of use. Fraudsters can easily buy, install and maintain them, but they’re also easier to detect with the right solution, for instance, a string comparison.
Native Tools
Native spoofing is somewhat more sophisticated and harder to detect. These tools are essentially browsers that are modified at the source code level, which lets fraudsters change fingerprinting attributes in a seamless way.
In that scenario, JavaScript functions can be modified at such a deep level that the detection methods mentioned above simply won’t work.
Another feature: the browser can add noise to certain values to confuse the tracking. The Mimic browser, for instance, has a feature called canvas poisoning, which is supposed to fool canvas fingerprinting.
- Examples of Native Tools: a great example is the Mimic browser. It is Chrome-based, and that lets users block fingerprinting features and add noise to certain values.
- Strengths and Weaknesses: While it’s harder to detect the Mimic browser, it’s not impossible because some errors and inconsistencies still appear when emulating other software and hardware stacks. For example, mimicking a Windows or Mac machine from Linux will still show browser plugins with .so extensions. Canvas noise can also be detected with the right setup.
Complete Recreation of the Software and Hardware Stack
For dedicated fraudsters, the most sophisticated solution involves completely recreating a fake user environment. That means emulating the hardware as well as the operating system for an attack.
Luckily, this is not only ambitious, but also very complex and expensive, which could be an obstacle to fraudsters who like to operate fast and at scale.
The bad news, however, is that while we know that solutions designed for that purpose exist, these are probably used on targeted hunts and are not advertised by fraudsters. Which means fraudsters using these kinds of methods could still be undetected by standard fraud and security solutions. However, they are currently only likely to be affecting a handful of people worldwide.
- Examples of what is used for complete software/hardware stack emulation: The closest tool we know of is probably a research tool called Blink. To avoid identification and tracking, Blink recreates a whole virtual machine stack every time it’s launched.
- Strengths and Weaknesses: Here again, small discrepancies can be detected between a real system and an emulated one. I mentioned Google’s Picasso in my previous post on browser fingerprinting, which runs graphical challenges. It could work here too.
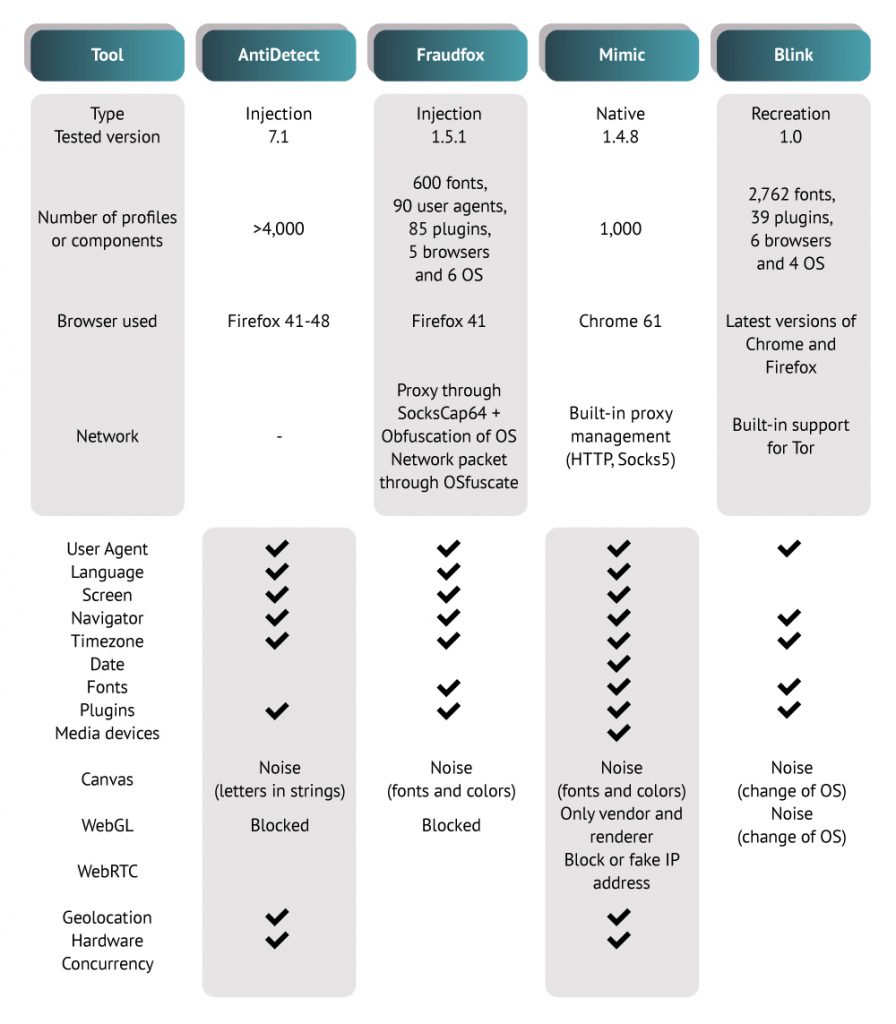
The features of four different anti-fingerprinting solutions, as found here.
The takeaway of this analysis is the following. While emulating very specific configurations is possible in theory, these attacks are difficult to carry out and quite expensive; they just don’t scale. These barriers push most (or maybe all) fraudsters into using native spoofing tools that should be detectable.
What is Canvas Fingerprinting?
There are a few ways to track users across the web. Most people will be familiar with web cookies, but you can also use a technique called canvas fingerprinting. Essentially, it looks at how the canvas element (part of HTML5) is rendered on the page.
Each combination of browser, operating system and installed graphics hardware will have their own signature, which is how you can identify certain users over time. It’s the same kind of technology you will find on a website like AmIUnique.org , which shows you your fingerprinting and the proportion of users sharing the same features.
Setting Up an Anti-Fingerprinting Detection Test
So how do you detect anti-detection tools? Let’s look at an example of how the SEON fraud prevention platform does it.
In this scenario, we’ll try to detect a browser that uses noise to hide its real values. More specifically, one that generates a random font set, so that the software “looks” like another one.
Font masking options
To detect these non-native fonts, we set up a simple website that runs a font-probing JavaScript code. This performs a series of security tests, hidden from the user. It renders two identical text elements, one with the system default font, and one with the currently used font, to look for differences.
If there are any differences between the two font sets, we can assume that one of them has been installed later, which points to a spoofing attempt.
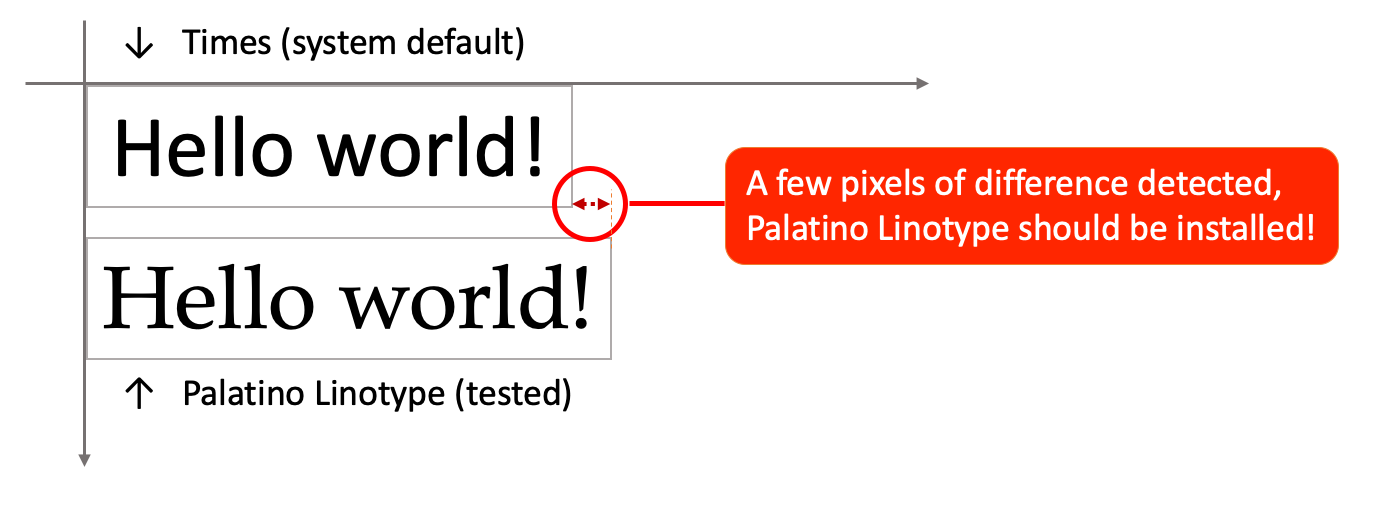
As for our own font detection website, it used a set of optimized cloud fonts. (We could have used FingerprintJS, but our own solution got results 66.1% faster.)
After running a few tests, we managed to establish values representing real browsers versus fake ones.
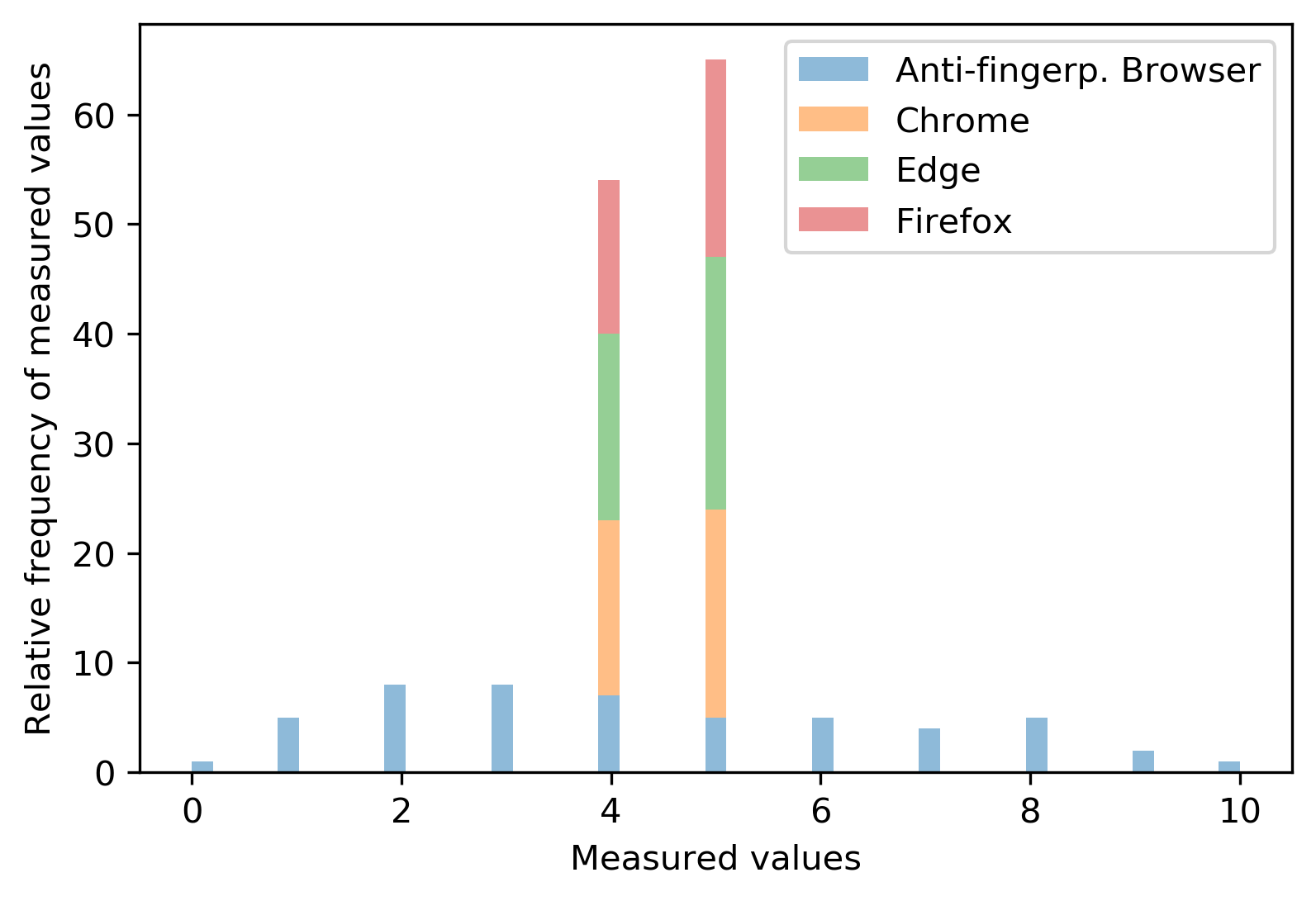
That means we can now create a strong custom rule with simple thresholds. If the value is between 3 and 6, we can decrease the risk factor. Anything above or below that should make the risk score go up and can point towards an attack attempt.
A Technological Arms Race
There is a strange dynamic between fraudsters and anti fraudsters. It’s a bit like an arms race. Whoever has the most advanced technology at the time can win, but only until the other side catches up.
The good news is that even the latest anti-fingerprinting browsers aren’t fully undetectable yet. Thanks to advanced techniques like font probing and canvas fingerprinting, which are included in the SEON platform to detect device spoofing, you can still take the upper hand against bad agents trying to exploit your business.
SEON offers the most advanced device fingerprinting tech to uncover fraudulent activity from customer devices
Ask an Expert
Device Spoofing FAQs
A common example of spoofing is IP spoofing using a VPN. You can also spoof your device’s MAC address, and use more sophisticated tools to spoof your entire hardware and software configuration. User-Agent spoofing also helps developers preview web pages as if they were in different browsers.
IP address spoofing is the most common type of spoofing. A VPN, proxy or Tor connection will essentially replace your real IP address with another – which is considered spoofing.
Spoofing your phone means using a device to display a different caller ID. This is often used by scammers and fraudsters to hide their identities when calling victims.