Online lending has gained significant popularity recently due to its accessibility, speed, convenience and competitive rates. However, it has also attracted the attention of fraudsters who exploit the digital nature of transactions.
The online lending environment provides ample opportunities for criminals to acquire cash quickly by blending in with legitimate customers, taking out loans with no intent to repay or impersonating others using stolen identities. In the UK, according to the Department for Business and Trade – approximately 11% of loans, equivalent to £5 billion ($6.4 billion US), were obtained through fraudulent means.
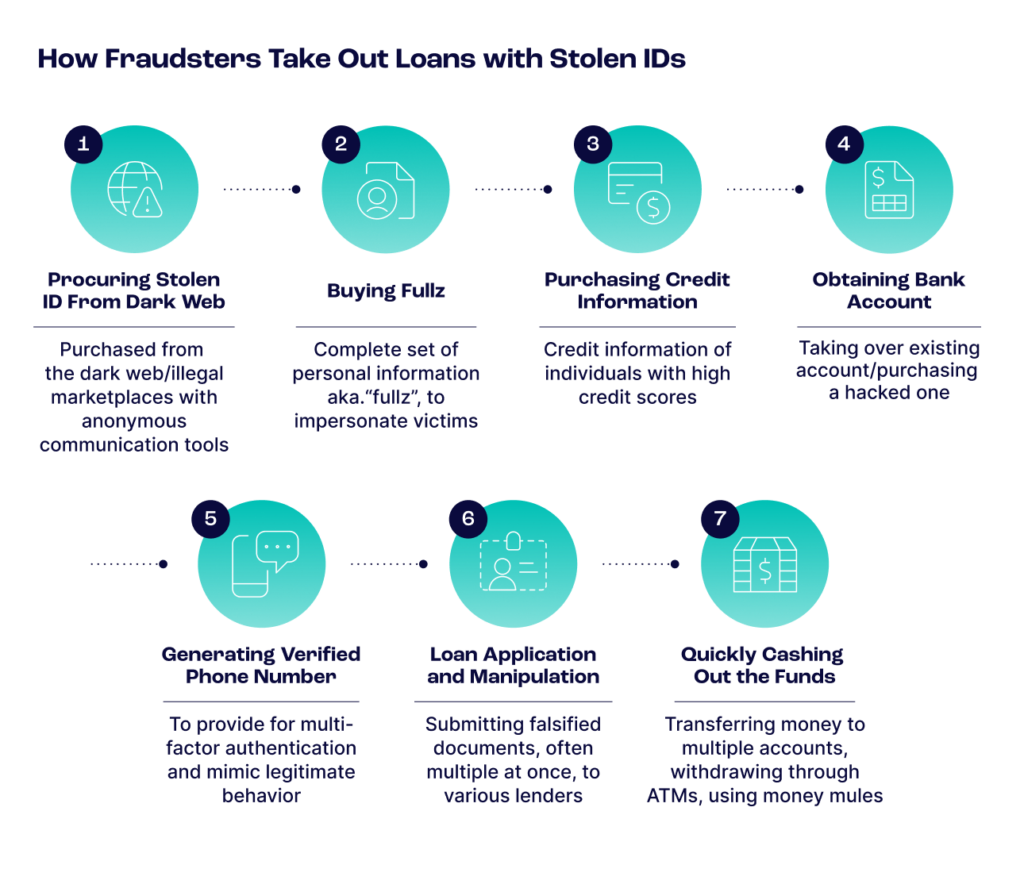
To combat fraud, online lenders must gather more customer information and examine alternative signals to better identify defaults and fraudulent intent. Understanding how fraudsters use stolen IDs to secure loans is crucial.
This guide explains their techniques to evade detection and exploit system vulnerabilities. By learning these steps, lenders can implement strategies to identify and prevent loan fraud, safeguarding their operations and protecting legitimate customers.
Step 1: The Dark Web for Stolen IDs
Like many other illicit online activities, most loan fraud starts with stolen IDs procured on the dark web or illegal marketplaces. In these areas, anonymity is prized. To maintain privacy, fraudsters employ the Tor Browser, a free, open-source web browser designed to enable anonymous communication and protect users’ privacy and freedom online, or fraudsters will use I2P, which stands for the Invisible Internet Project.
This overlay network uses peer-to-peer-like routing structures designed to protect the privacy and identity of users while they communicate over the internet. Once veiled with privacy, fraudsters will head to darknet marketplaces to purchase stolen IDs. If fraudsters are not familiar with these steps, they will often find detailed instructions on private forums, including plenty of beginner guides to fraud.
How to Stop These Actions: Fraud prevention software uses device intelligence – including cookies, browsers and device hashes – and digital footprint analysis to identify whether applicants use Tor or another privacy tactic to hide their actions. By recognizing these signals, lenders can flag suspicious activity and require additional verification steps.
Step 2: Buying Fullz
Fraudsters have coined the term “fullz” to refer to a complete set of an individual’s personal information, often used for harmful purposes. Typically, a fullz package includes a full name, address, date of birth, social security number (SSN), bank account information, credit card information, email address, phone number and driver’s license number. With this comprehensive information, fraudsters can convincingly impersonate victims to obtain loans.
How to Stop These Actions: Fraudsters operating with fullz typically cannot access a victim’s email account and will sign up for a new account through a free provider. SEON’s digital footprint solution looks at email accounts associated with an address to check for involvement in data breaches, establish the duration of existence and verify social signals associated with an email address to confirm its validity. A new email address with no known history is a common indicator of fraud. Monitoring for unusual account creation patterns and cross-referencing with known data breach information can also help identify fraudulent attempts.
Step 3: Purchasing Credit Information
Traditionally, online lenders protect themselves by deploying credit scoring systems. However, fraudsters have found ways to circumvent these protections by purchasing credit information on individuals with high credit scores and using those stolen identities for their loan applications. They often pay for this information using stolen credit cards to avoid detection.
Some of the more sophisticated cybercriminals use social security numbers stolen from children, as these records are typically clean and unmonitored. Then, they create synthetic identities, which combine stolen and fabricated information to present a convincing front.
How to Stop These Actions: SEON combats the use of stolen credit information by creating a digital footprint of loan applicants using their email address. A legitimate email is typically linked to many social media accounts and apps, unlike a fraudster’s email. Additionally, velocity checks can detect and flag multiple applications from the same identity within a short time. By combining digital footprint analysis with velocity checks, lenders can more effectively prevent fraudulent loan applications.
Step 4: Obtaining a Bank Account
Fraudsters need a bank account that is not linked to their real identity to receive their loan. Instead of setting up a new account, they may conduct an account takeover on a lending platform or purchase a hacked account from a dark marketplace.
How to Stop These Actions: SEON supports the banking industry by helping digital banks and traditional institutions shut down fraud throughout the entire customer journey. By protecting against from the moment of sign-in, through onboarding, and during transactions, we ensure a trusted environment for all banking activities.
Step 5: Generating a Verified Phone Number
Multi-factor authentication is ubiquitous in fintech, and it often uses a one-time password to authenticate the account owner. This presents another challenge for fraudsters, who need to provide an actual phone number to link to their application to mimic the behavior of a legitimate applicant.
How to Stop These Actions: By mapping an applicant’s digital footprint using their phone number, SEON can help lending companies identify potentially fraudulent applications. Our customizable data rules allow lenders to set a default risk score that matches their risk appetite, helping to determine the likelihood of default. This process ensures that even if fraudsters generate a verified phone number, their overall digital footprint and risk indicators will reveal inconsistencies, effectively identifying fraudulent attempts.
Step 6: Loan Application and Manipulation
Once equipped with stolen IDs and fullz, fraudsters will apply for loans by manipulating or falsifying additional documents, such as pay stubs or bank statements, to substantiate their false identities. They often submit multiple applications across different lenders to maximize their chances of success. Fraudsters may target loan companies with less rigorous aff affordability checks or due diligence procedures, but no lender is entirely safe from these schemes.
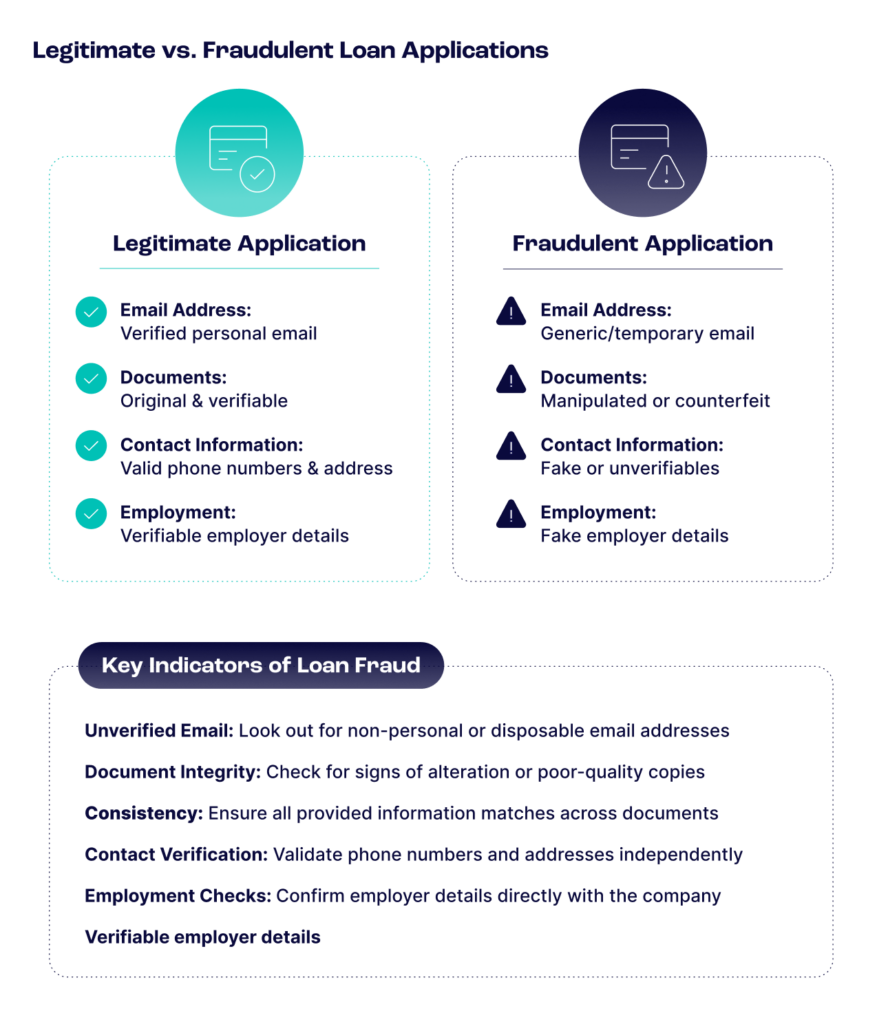
How to Stop These Actions: Lenders can combat this by implementing multi-layered verification processes, including document verification, biometric checks and cross-referencing information with external databases. Leveraging alternative data points such as utility and rent payments, employment and income data, and digital footprint analysis can enhance fraud detection. Advanced machine learning models can detect anomalies and inconsistencies in application data, while real-time monitoring can flag suspicious activities, such as multiple applications from the same identity. These measures help identify and prevent fraudulent loan applications effectively.
Step 7: Cashing Out
Once a loan is approved, fraudsters quickly cash out the funds. They might transfer the money to multiple accounts or withdraw it through ATMs to minimize traceability. Another common tactic is using money mules, individuals hired to move money through various accounts. This makes it challenging for law enforcement and financial institutions to trace the funds to the original fraudulent activity.
How to Stop These Actions: Implementing advanced transaction monitoring systems is crucial for detecting unusual withdrawal or transfer patterns. Real-time analytics can identify and flag suspicious activities, such as large withdrawals immediately after a loan disbursement or multiple transfers to unlinked accounts. Collaboration with other financial institutions to share intelligence on known fraud tactics and suspicious activities can enhance detection and prevention efforts.
Additionally, using machine learning models to analyze transaction behaviors and flag high-risk activities can help prevent fraudsters from successfully cashing out.
Learn how loan fraud goes beyond stolen IDs, from synthetic identities to loan stacking, and how lenders can reduce risk early.
Read loan fraud guide
How to Protect Your Business from Loan Fraud
At every step of our research, we were amazed by how easy it would be even for a newbie to start defrauding online lenders. No wonder it is one of the most targeted verticals by fraudsters.
But the good news is, there are plenty of ways to stop them. Using a combination of tools and processes, you should already have enough data to create a tight net to catch criminals.
While some points are falsifiable, it’s almost impossible to cheat all of them all of the time. By checking the connections between data points, a good integrated system can find red flags that would otherwise go unnoticed.
Staying on top of fraud trends will also go a long way in understanding attack patterns and preventing them. SEON’s machine learning looks for patterns and proposes rules that apply to your business. Fine-tuned with your feedback, it adapts to your risk tolerance, giving you more accuracy and speed. Offering all of the above in tandem with modular APIs, unique insights, and a customer success team made up entirely of fraud analysts and managers, means SEON is a valuable partner for lenders looking to stop fraudsters.
We believed social media presence could help validate user identity,” says Kaspars Magaznieks, Head of Fraud at SunFinance. “SEON established that correlation for us. We now use the data to confirm identities and contact non-paying customers for debt collection.
Sources
- Baines Wilson LLP: Bounce Back Loan Fraud
- The Conversation: AI threatens to add to the growing wave of fraud but is also helping tackle it
Frequently Asked Questions
Lenders use various techniques to detect and prevent fraudulent loan applications, including digital footprint analysis, device intelligence and multi-layered verification processes. They monitor for unusual patterns, such as multiple applications from the same identity or suspicious device usage, and employ machine learning models to detect anomalies and inconsistencies in application data.
Digital footprint analysis involves collecting and analyzing data from an individual’s online presence and activities, including social media profiles, email usage, and other digital behaviors. By examining these data points, lenders can verify the authenticity of an applicant’s identity and detect potential fraud. A robust digital footprint often correlates with a legitimate applicant, while a sparse or inconsistent digital presence may indicate fraudulent activity.
Alternative data points, such as utility and rent payments, employment history, and digital transaction patterns, provide a more comprehensive view of a borrower’s financial behavior. These data points help lenders assess creditworthiness for individuals with limited traditional credit histories, improving the accuracy of credit assessments and expanding access to credit for underbanked populations.