Every minute, approximately 1.5 million credit card transactions occur worldwide, totaling over 2 billion daily transactions in 2024 alone. With this scale, even a small percentage of fraudulent activity can lead to massive losses.
Velocity checks offer a crucial line of defense. By flagging unusual transaction patterns in real time, they help businesses catch fraud before the damage is done.
What Are Velocity Checks?
Velocity checks detect suspicious behavior by analyzing how often certain actions occur within a short timeframe. One or two failed transactions using frozen credit cards wouldn’t raise any eyebrows, but five failed attempts in rapid succession from the same IP address? A major red flag.
This behavior is a telltale sign of card testing, where fraudsters use stolen card details to identify which ones are still active. By tracking the speed and frequency of actions, velocity checks help spot fraud that static rules might miss.
What Are Velocity Rules?
A velocity rule (or velocity filter) is a logic-based condition that evaluates how frequently certain behaviors occur within a defined timeframe.
Essentially, they are conditional if-statements linked to timeframes:
If A happens within B time, then do C.
This is a simplified example — in practice, velocity rules are often far more complex. For example:
If more than A instances of B behavior occur while C is active and D present, all within E time and from F location, then add +5 to this user’s risk score.
These rules may seem complex because they’re highly contextual — custom-built for each organization, tailored to its risk appetite, industry and fraud exposure. But experienced fraud analysts know how to spot abuse patterns and where to look for signs of manipulation.
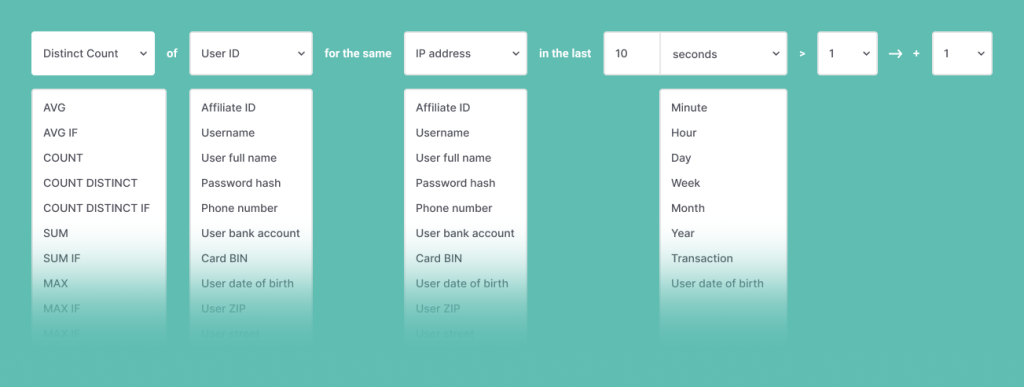
Velocity checks rely on data points captured through device intelligence and digital footprint analysis such as the email address, geolocation, IP address, browser type and version, card hash, device name, device language, installed plugins, etc.
Depending on the threat model, any of these data points can be tracked across timeframes ranging from seconds to years.
Here’s a practical example. We can set the following rule to ban devices that match the criteria for 24 hours.
More than 15 failed attempts to log in to more than 7 different accounts on a website, all from the same device ID, within less than 10 minutes.Velocity rules are essential when static, one-off checks aren’t enough. They detect subtle and time-sensitive patterns that reveal bots, credential stuffing and other high-velocity fraud attempts before they cause damage.
How Do Velocity Checks Work?
Setting up the process for velocity checks starts with identifying key data points: basically, looking back at past behavior to figure out what patterns tend to signal fraud. Sometimes this involves using machine learning to dig a little deeper and spot trends that aren’t obvious at first glance.
Next, the platform sets up what’s called a velocity rule. Think of it as a set of conditions: a mix of data points and timeframes that help flag unusual activity. Once the rules are in place, the system starts scanning for any behavior that matches those conditions.
If it catches something suspicious, the platform reacts right away. That could mean blocking a transaction, assigning a higher risk score to the user or triggering another security measure, such as asking them to re-enter their password.
And here’s the cool part: these rules aren’t set in stone. Data analysts can tweak them anytime, updating old rules, adding new ones or removing those that no longer apply, keeping the system flexible and ahead of the game.
IP Velocity Check
Velocity IP checks prevent fraud by tracking how many actions, transactions or attempts come from a single IP address within a short period of time. This helps analysts spot unusual spikes in activity that can signal fraud.
Setting up this kind of rule starts with gaining an understanding of what normal user behavior looks like. After that, this behavior is compared with patterns commonly seen in fraudulent activity. The goal is to catch and stop suspicious behavior before it can do any harm while also ensuring that legitimate customers can go through the process with minimal friction.
Why Are Velocity Checks Important?
Velocity checks are crucial in the fight against fraud because they enable a deeper understanding of both user and fraudster behavior. They enhance fingerprint analysis, making it easier to identify and track suspicious activity. These checks also improve the detection of fraud rings by spotting coordinated patterns across multiple accounts or devices.
With velocity checks, teams gain a clearer grasp of emerging threats and fraud trends. This leads to more precise, efficient detection and helps prevent more complex, hard-to-spot types of fraud. Crucially, they also act as a deterrent to fraudsters using advanced technology to bypass traditional defenses.
How to Use Velocity Checks and Velocity Rules for Fraud Detection
Velocity checks are a powerful tool in modern fraud detection. By incorporating the element of time, they help uncover hidden connections between users, actions and behaviors that might otherwise go unnoticed. Rather than looking at data points in isolation, velocity checks evaluate how those data points behave over time, providing a much deeper layer of insight.
These data points can come from a range of sources, such as device intelligence and digital footprint analysis, and when combined with velocity logic, they gain a new level of meaning. For example, a user making five account login attempts from the same IP address within two minutes may raise a red flag — something a static rule might miss.
What makes velocity checks especially effective is their flexibility. There’s virtually no limit to the combinations you can create when building rules and filters. That’s why it’s crucial to tailor these rules to each specific use case. What counts as suspicious for one business may be totally normal for another.
Many fraud detection platforms offer industry-specific templates to help. For instance, a flight booking site may focus on patterns of rapid searches and last-minute purchases, while a cryptocurrency exchange, where money laundering risks are higher, may monitor for multiple high-value transactions in a short timeframe. In the latter case, velocity rules are designed to trigger alerts for manual review whenever risky behavior is detected.
Ultimately, smart use of velocity checks means understanding your users, your risk landscape and how time can reveal what static data alone cannot.
How Velocity Rules Uncover Hidden Threats
With velocity rules, businesses can uncover signs of account takeover attempts, bot farm activity in gaming or gambling platforms and patterns linked to high-risk users. They’re also effective at flagging synthetic identities, identity fraud and card testing behavior, which often signal organized fraud operations.
In sectors like iGaming and eSports, velocity checks help detect bonus abuse and other exploitative behavior that can slip past standard rules. They’re equally valuable in identifying chargeback fraud and other forms of transactional abuse.
The real strength of velocity checks lies in their flexibility. When customized to an organization’s specific risk profile, they give fraud teams deeper insights into both genuine and malicious behavior and turn that insight into a strategic advantage. For businesses regularly targeted by sophisticated fraudsters, velocity checks are an essential layer in a broader, multi-layered fraud prevention strategy.