What Is SSL Inspection?
SSL inspection is the act of intercepting and inspecting encrypted traffic. Organizations will – or rather are advised to – monitor encrypted traffic in order to ensure there is nothing malicious entering or leaving their servers.
This is because almost all internet traffic is SSL encrypted these days – which comes with its own risks. According to recent figures, 95% of websites on Google use HTTPS and 90% of time spent browsing on Chrome is on HTTPS websites – as well as on Android at 95% and on Windows at 97%.
SSL interception can be always-on or sporadic. The term both applies to decrypting and inspecting data being sent to your servers through your website as well as decrypting and inspecting data sent from your organization.
There are several ways in which it is done, but the goal is the same: to keep data safe from bad actors.
What Are the Benefits of SSL Inspection?
Inspecting SSL allows businesses and organizations to keep their data, servers and operations safer. More specifically, by inspecting SSL, you can:
- block employee access to malicious content and dangerous websites
- identify and stop certain types of malicious attacks (e.g. DDoS)
- know when unusually large amounts of data are leaving your network
- more efficiently filter out specific users, IPs and/or locales
What Is Secure Sockets Layer (SSL)?
SSL, which stands for Secure Sockets Layer, is a key type of encryption between web surfers and web page servers.
More than 46 million websites use SSL by default in 2021, which provides a basic level of information integrity and confidentiality of interactions with the website – including transactions.
What Types of SSL Certificates Exist?
Types of SSL certificates for websites include DV, OV, IV and EV. SSL certificates are a sign that your browser can trust a website. They can be validated in a number of ways:
- DV: domain validation (the domain owner has been verified)
- OV: organization validation (the organization of the certificate applicant is verified)
- IV: individual validation (the individual requesting the certificate has been verified)
- EV: extended validation (premium option – organization is verified, known and trusted)
Each of these is an SSL certificate, but the assurances they provide differ.
For example, DVs mean that the owner of this URL has been validated. The highest standard available is the EV, which is much more rigorous than the others. But they are also more expensive to apply for, so only organizations that have a vested interest in proving how trustworthy and reliable their website is – for instance, those in the financial sector – will normally try to get an EV SSL certificate.
How Do I Know If a Website Uses SSL?
Simply put, if you want to check whether a website has SSL enabled, you look at its URL. Does it use secure HTTP?
- if it starts with https:// —> it does not use SSL
- if it starts with https:// —> it uses SSL
Moreover, most modern browsers will point this out near the URL bar with an open or closed padlock icon, which provides more information if you click on it – as you can see in the screenshot below.
From there, information on the type of SSL certificate can be gleaned with a few clicks on most browsers too, including the issuing body and dates valid.
What Is TLS?
TLS stands for Transport Layer Security but, for technical reasons, TLS and SSL are used interchangeably these days. Let us explain.
Anyone looking into SSL is bound to come across the acronym TLS. This is because TLS is an encryption protocol that was developed from SSL in 1999. Currently, the most advanced version of this protocol is TLS 1.3, which was published in 2018. Most people will say “SSL” but refer to either TLS or SSL – since legacy SSL protocols were deprecated more than 15 years ago.
What Is SSL by Default?
SSL by Default is an initiative that started in 2016, which looked to make SSL default for websites. It has been largely successful.
In fact, as of version 62, from October 2017, the Chrome browser has been marking HTTP pages as “Not Secure” when there are fields for the user to enter information, as well as on all Incognito Mode HTTP pages.
According to the Chromium blog, this was part of a wider plan to label HTTP sites as non-secure and raise awareness among even casual web users. In fact, an earlier change in the same direction had previously resulted in “a 23% reduction in the fraction of navigations to HTTP pages with password or credit card forms on desktop” within nine months (January to October 2017).
Reasons to use SSL in the first place include everything from keeping customers safer to securing prestigious verification and safeguarding your customer-facing brand image.
Namely:
- SSL keeps online shoppers safer
- SSL provides elementary protection from bad actors
- SSL stops several types of eavesdropping attacks
- SSL keeps personal information safe and boosts privacy
- SSL promotes the digital economy
- SSL builds trust between consumers and organizations
- SSL builds trust in online transactions
- SSL raises basic awareness of cybersecurity
What Is SSL Interception?
SSL interception is the act of intercepting encrypted SSL/TLS traffic for any purpose, which can also involve tampering with it. This can be done by both bad actors and by good actors in the fraud and cybersecurity equation.
In other words, intercepting SSL traffic means eavesdropping on this traffic, despite the fact that it’s encrypted – for any reason at all. By definition, SSL interception is a man in the middle (MitM) act because it places the intercepting party between the sender and recipient of information. However, it is not a MitM attack unless it is done for malicious purposes.
SSL may be the gold standard of web security, but it does not guarantee complete safety.
Bad actors will still attempt and occasionally succeed in intercepting a TSL/SSL-encrypted session and gaining access to or tampering with the encrypted data.
But companies who are trying to keep their traffic safe from prying eyes and from criminals will also intercept it in order to monitor it, to enhance their security, and to ensure everything is progressing smoothly and no cybercriminals have been tampering with it.
Why Inspect SSL Traffic?
SSL inspections allow an organization to ensure that there are no hackers, scammers or fraudsters attacking their servers via encrypted traffic.
As we have seen, SSL is a useful tool that provides a basic level of peace of mind to users and companies online. However, this encryption, which is now almost ever-present on the web, can be taken advantage of, helping criminals serve malicious content and carry out attacks.
In fact, the team at Zscaler has counted 1.7 billion threats in encrypted SSL traffic in the space of six months – and that is simply what’s been picked up by just one brand of software. Many more are estimated to occur.
For these reasons, inspecting SSL traffic is a good idea.
How Does SSL Inspection Work?
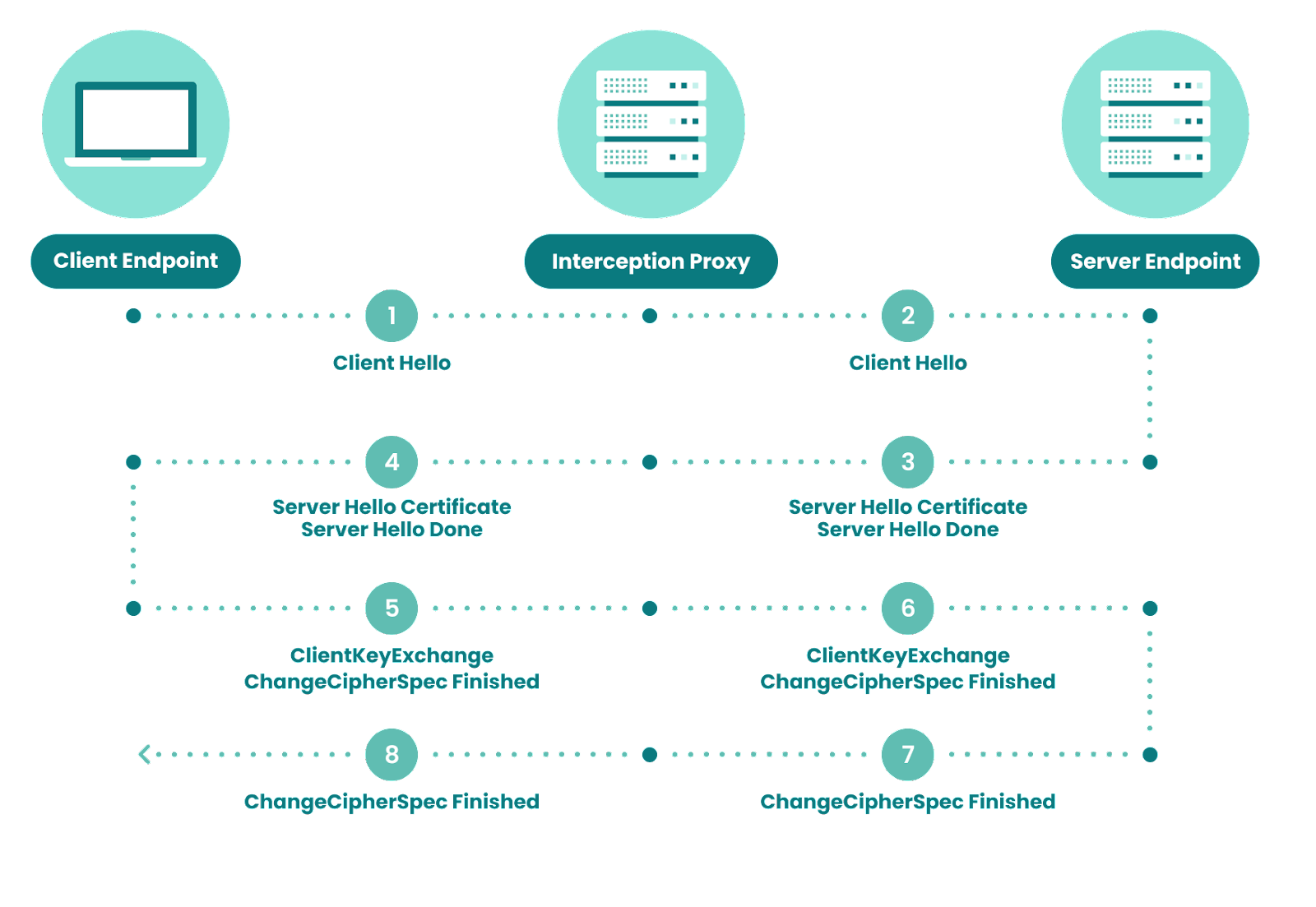
SSL inspection works by placing an interception proxy between the client endpoint and the server endpoint, which will decrypt and inspect the traffic.
As we’ve established, SSL inspection is normally done by placing a piece of hardware or software between the client and the server. As the vast majority of internet traffic is SSL encrypted, so is fraudulent and malicious content and communications. And since it is encrypted, the only way to catch it is to decrypt and inspect this traffic.
Due to the extreme demands it would put on processing power and on its bandwidth, it is not feasible for a company to inspect all of its traffic, so most will only inspect some of the traffic to and from locations that they deem as untrusted.
What and how it is decided that a destination is worthy of the organization’s trust, and whether that destination is susceptible to attacks of its own, is up for discussion – so there is no fool-proof method, besides inspecting everything.
Common methods to inspect SSL traffic include the below, each with its benefits and shortcomings:
- next-gen firewalls (NGFW) through which traffic is streamed
- proxies that create separate connections between client and server
- TAP mode where traffic is copied as it flows, to be analyzed separately offline
Below, we can see how a proxy can be used to either just inspect or even intercept traffic.
Do You Have to Always Use SSL?
No, you do not have to. But it is a good idea to do so, not only because it’s safer, but because it helps your public image and marketing efforts.
Here is why: Today, Google Chrome and other leading browsers alert the user if any website that accepts any user information at all – even just an email address – does not have SSL enabled.
This is likely to put off even novice users since it is displayed as a warning to everyone.
Whether a website uses HTTPS or not is even a factor in search engine algorithms, which means that your site is likely to be penalized by Google, Bing and other search engines if it does not use SSL/TLS.
How Is SSL Traffic Intercepted?
There are several ways for bad actors to intercept traffic. These include:
- fake SSL certificates
- man-in-the-middle SSL attacks
- SSL interception proxy
What fraudsters will often try to do upon interception, in addition to stealing useful information, is to tamper with the data to allow themselves to ultimately gain access to your systems.
Moreover, because your employees and customers will receive the tampered information as ostensibly SSL encrypted, they are more likely to trust it. Therefore, this could more easily lead to successful attacks such as carding, account takeover and so on.
How Do You Stop Malicious SSL Inspection and Interception?
As we have seen, TLS/SSL encryption cannot provide complete peace of mind. On the contrary, it can give a false sense of security. In fact, such encrypted traffic can be intercepted and is no match for tech-savvy fraudsters in 2022 and beyond.
Instead, organizations across the spectrum of online activity are advised to be vigilant. Training employees in best practices can help ensure they will know to trust websites that use HTTPS or even consult with the IT team for important transactions they are uncertain about.
Organizations’ goal should be to deploy efficient inspection solutions that will allow them to protect against criminals who try to take advantage of SSL encryption.
The best method for this will depend on the individual company as well as the sector they are in and the types of attacks they are most often targeted by.
We explain the vulnerabilities that fraudsters exploit, so you know how to defend your business better.
Read More Here
Sources
Chrome Developers: New in Chrome 62
Chromium Blog: Next steps toward more connection security
SERP Watch: SSL Stats for Secure Browsing in 2022
ZDNet: How the NSA, and your boss, can intercept and break SSL
Zscaler: Analysis of SSL/TLS-based Threats | ThreatLabZ Infographic