What Is an Emulator?
An emulator is a piece of software designed to make it look like you’re using a different device, fully mimicking its hardware, down to its bugs.
The goal is to make your system look exactly like it was something else – be that a different type of PC, or a mobile device, or any piece of hardware.
Emulators have several legitimate uses, from running legacy programs to entertainment, but they are also employed by criminals to defraud companies, spoof the hardware of their victims, and/or hide their tracks.
In the world of cybercrime, the most popular type of emulator are mobile phone emulators, which go several steps beyond merely using a mobile proxy.

How Does an Emulator Work in Fraud?
Cybercriminals use emulators in their schemes both to hide their tracks and to give the resemblance of a commonplace device that will not arouse suspicion or, even worse, the appearance of a specific device whose legitimate owner is looking to make purchases or access their funds.
An emulator will pretend to have a different device ID than it does, and is also able to quickly switch from one device ID to another.
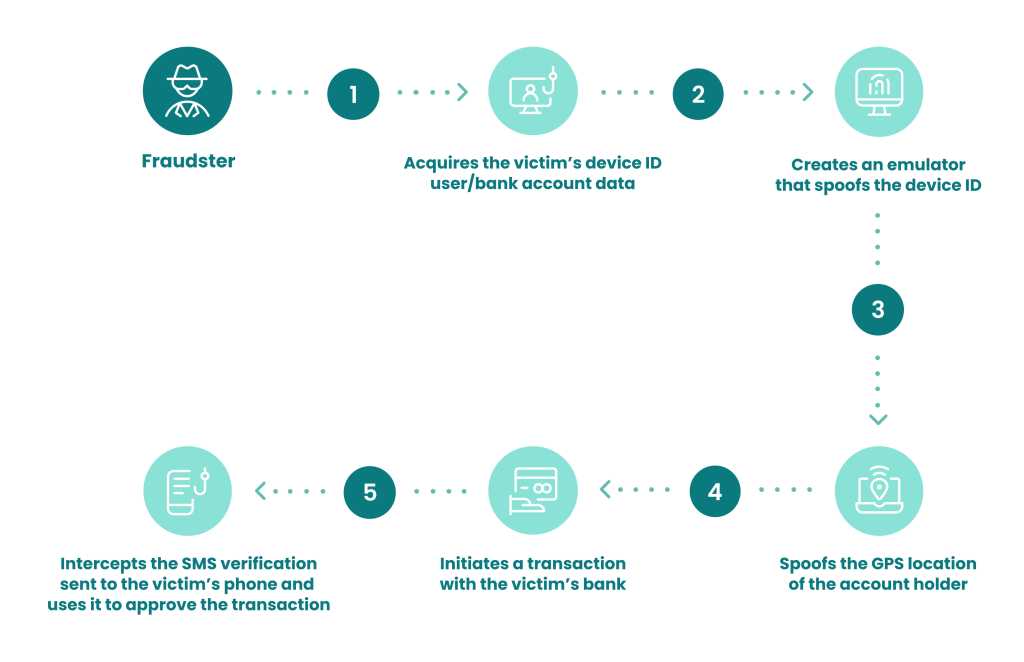
One example we can look at is using emulator technology to appear as a bank account’s legitimate owner accessing it via mobile banking. To do so, a fraudster will:
- acquire the victim’s device ID and user/bank account fullz
- via phishing, dark web purchase, or in a different way
- set up an emulator that spoofs the device ID of the account holder
- spoof the GPS location of the account holder
- initiate a transaction with the victim’s bank e.g. a money transfer to the criminal’s bank drop
- intercept the SMS verification sent to the victim’s phone and use it as a second MFA factor to approve the transaction.
If done correctly, this allows the fraudster to pass basic device fingerprinting checks, thus achieving their goal of stealing money, in this case, or conducting other types of crimes, in so many others.
In practice, a cybercriminal using an emulator will successively spoof the IDs and other characteristics of several devices in one session. Another usage would be to try to bypass the merchant’s app specifically, instead of trying to open a webpage.
Are Emulators and Virtual Machines the Same?
There are technical, under-the-hood differences between VMs and emulators, which help explain why fraudsters tend to prefer emulators and not virtual machines.
Specifically, emulation is all about giving the appearance of specific hardware, while virtualization is about software compatibility.
Virtualization creates a virtual environment within a different, physical environment. A common example is Wine, which creates a virtual Windows environment within Linux or macOS, which can be used to run Windows software on non-Windows machines. It merely creates a virtual interface, acting as a computer within a computer, so to speak.
A virtual machine creates an isolated environment. Its primary goal is to allow users to overcome software compatibility issues.
Emulation emulates the hardware of another device. For example, it can make a Windows PC appear to be an Android smartphone to a remote server it’s trying to connect to.
Other common examples of emulators are software that reproduces old arcade game machines (e.g. MAME), as well as virtual DVD-ROM drives that emulate the functionality of a physical DVD drive without the user installing such a drive.
An emulator mimics the hardware of another device. Its goal is to appear to be identical to that device.
What Are Emulator Farms?
Emulators can be sometimes organized into entire emulator farms as well as automated into bots to perform basic functions more quickly, causing irreparable harm to both businesses and consumers. Therefore it is important to invest in bot detection tools to prevent irreparable harm from occurring to businesses and customers.
Emulator farms can also very quickly switch from account to account, especially so in the case of randomized accounts used to spam reviews, mass create new accounts, commit app install, mobile ad fraud, and so on.
As a recent example, Ars Technica reported in December of 2020 that cybersecurity researchers uncovered a massive operation where 20 emulators were used to mimic over 16,000 mobile phones.
The capacity of each emulator was massive, with a single emulator spoofing over 8,100 mobile devices in order to steal from compromised mobile banking accounts. The losses are valued in the millions.
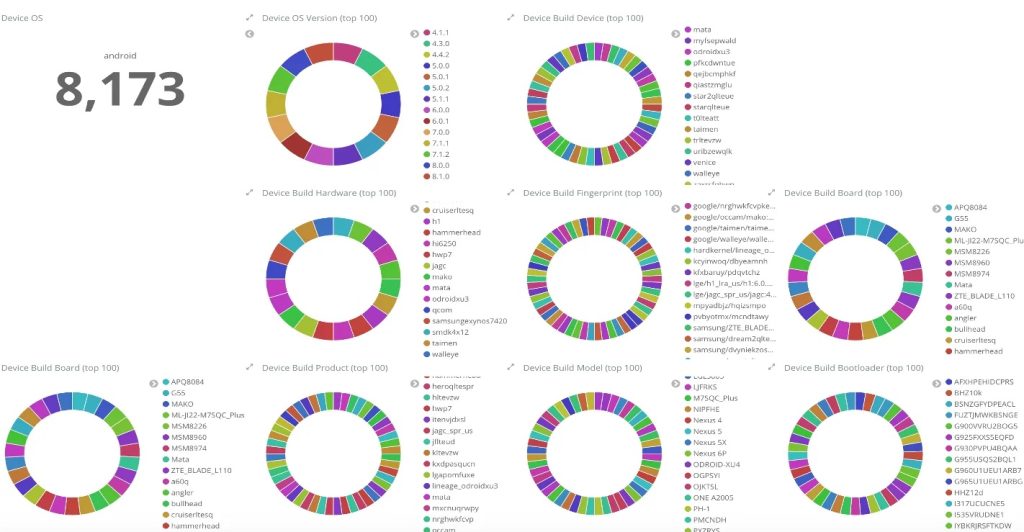
IBM image via Ars Tecnica
Examples of Emulator Fraud
Since emulators are a fraudster tool rather than a specific type of fraud, they are used in several different ways by cybercriminals:
- to enable multi-accounting, making multiple different attempts at logins or payments from the same device appear to come from different devices
- to emulate specific devices belonging to specific victims whose accounts the fraudster is trying to access
- to give the appearance of a legitimate new user or buyer trying to create a new account or complete a transaction, through randomization
- to conduct affiliate fraud in sectors such as iGaming
- as SecOps to further hide the criminal’s tracks, similar to proxies and Tor
- to conduct cyber-espionage or cyber-warfare
- to evade previous bans and flags by appearing to be a new user.
Some of the more commonly used emulator and virtual machine software includes: FraudFox, Linken Sphere, Bluestacks, Nox, Incogniton, MultiLogin, Kameleo, Selenium, and AntiDetect.
How Does Emulator Fraud Impact Businesses?
Emulator fraud can impact businesses in a multitude of ways. Traditionally, basic anti-fraud measures would look into the device ID to gauge how trustworthy a user was.
Emulator fraud is designed to evade this, finding fertile ground in largely obsolete methods deployed by unsuspecting companies.
The implications are diverse and far-reaching:
- lost revenue from stolen merchandise
- lost funds for banks, fintech firms, and ecommerce
- chargeback requests and higher chargeback ratios
- a barrage of fake reviews causing reputational damage
- mass harm to customers and clients, such as by mass account takeover
These are, of course, mere examples. The nub of the issue is that emulators make fraud easier to commit, and criminals more likely to get away with it. To protect against emulator fraud, organizations are called to adopt up-to-date anti-fraud strategies.
How to Detect Emulator Fraud
Detecting, stopping and mitigating emulator-enabled fraud involves combining advanced device fingerprinting protocols with other methods to collect several data points that allow us to reach more confident and well-rounded conclusions about the intentions and identity of each user.
For example, a device ID might seem legitimate but once combined with a velocity check, it can reveal that the same device was supposed to be in a remote country a few minutes prior.
It is impossible for both of these to be genuine, as not enough time has passed for the consumer to have traveled from one place to the other. This raises red flags.
Taking this basic idea further, sophisticated anti-fraud protocols combine the above with machine learning, data enrichment, and human intelligence to reach conclusions on a case-by-case basis.
With the help of robust rulesets and fine-tuning, each organization can utilize the best suited fraud detection software to implement efficient protection against emulator fraud, despite the rise observed in its use in recent years
Combining device fingerprinting with other complex checks means fraudsters will not be able to hide so easily, no matter how they try to spoof their device and connection.
Read More Here
Sources
Ars Technica: “Evil mobile emulator farms” used to steal millions from US and EU banks
Stack Overflow: What are the specific differences between an “emulator” and a “virtual machine”?