What Is a Cookie Hash?
A cookie hash or hashed cookie is an identifying parameter generated for each browser session.
Cookies are small files produced by a website and stored locally to provide certain rudimentary bits of information about each user and their session to that website, when the user returns.
They contain different types of information to do with the user’s interaction with the website, of various levels of sensitivity – sometimes including passwords and personal data.
For this reason, cookies are not stored in plaintext format but hashed, obscuring the information within them.
Cookie hashes also find application in cybersecurity and fraud prevention, as they can inform websites and platforms about the user’s past conduct, setting off red flags where needed.
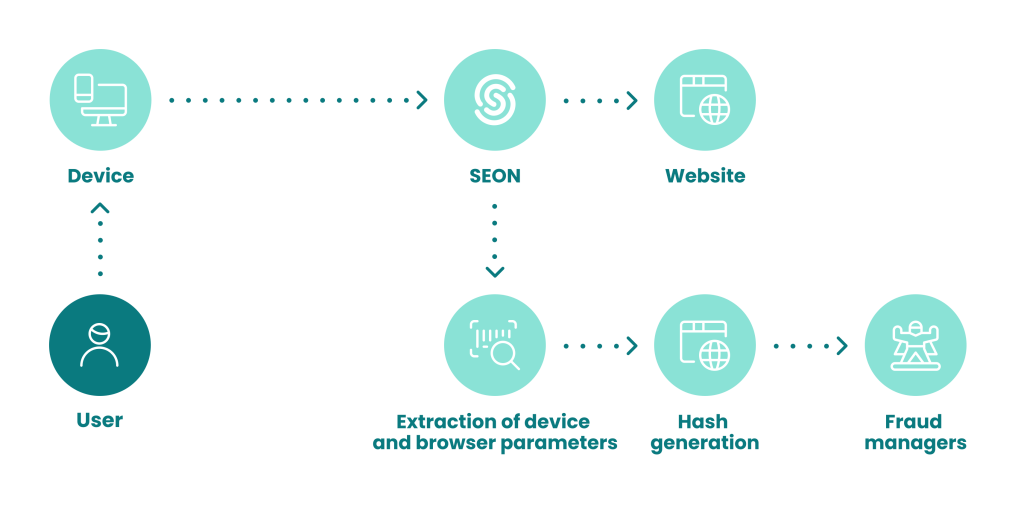
How Do Cookie Hashes Work?
On the website visitor’s side, cookie hashing goes unnoticed. Here’s what happens:
- You use your web browser to visit a website.
- As you interact with the website, a cookie is created containing information about your session.
- The cookie is hashed, for privacy and security.
- The cookie is stored by your browser on your local device.
- On your next visit to the same website, the website reads the cookie and remembers your settings, preferences and activity.
- Only the website that created a cookie hash can unhash it in order to read it.
Why Is Cookie Hashing Important?
Cookie hashing provides increased security and privacy over non-hashed cookies because a cookie hash can only be decoded and read by the website that created it.
Web browser cookies provide usability, personalization and convenience for everyday users without the need to create individual user accounts.
However, they also work behind the scenes to gauge user engagement and behavior, informing the website owner about what works and what doesn’t, as well as having more technical applications, including cybersecurity and fraud detection.
How Do Cookie Hashes Help Fight Fraud?
Cookie hashes help prevent fraud by telling us about a user’s previous actions on the same website, even if that user is pretending to be someone else. For instance, a fraudster who is trying dozens of username and password combinations hoping to break into someone’s account could be identified by a hashed cookie.
Because cookies contain information about previous visits of the same user and browser to a website, a cookie hash can flag unusual behavior that a legitimate user would never consider partaking in. For instance:
- The same browser and device logging into dozens of different accounts on an eshop
- An unusual number of US-based accounts being accessed from a faraway country, out of the blue
- The combined cookie hash, browser hash and device hash of several attempts at payments with different cards can reveal patterns that indicate manipulation, which is a red flag for potential illegal activity.
As with so many different facets of online crime, fraudsters have methods to evade cookie-hash-based fingerprinting. The simplest is clearing their browser’s cookies or using an incognito window. There are also extensions and software to enable browser spoofing, as well as emulators that spoof mobile devices.
However, advanced detection modules can still identify these fraudulent users, by combining dozens or even hundreds of different data points – which include cookie hashes – and flagging suspicious patterns and irregularities.
They typically return detailed fraud scores that can automatically block suspicious attempts, so that fraud analysts can respond to concerns and investigate further.
The web browser you’re accessing this page with is a treasure trove of data. See how finding and analyzing it can reveal their real intentions.
Learn More