What Is a Browser Hash?
A browser hash is a string of numbers and letters created to map data related to a user’s browser.
In a way, it serves as the browser’s ID, used to identify the browser and user by the party who created the hash to begin with. This also means that it can help tell whether two users are accessing a website from the same browser.
A browser hash can include information such as, among others:
- web browser type and architecture
- browser version
- installed plugins/extensions
- size of HTML5 canvas
- audio processor…
How Does a Browser Hash Work?
The process is fairly simple:
- When a user connects to your website, a fraud detection system can log browser data.
- That data is fed through a mathematical function called a hash, to standardize and store the information, encrypting it in the process.
- This essentially creates a browser ID, which is stored in the cache.
- Upon your next visit to that website, it will be able to pull, decode and read your browser hash, so it will know who you are.
Each unique configuration of the browser will have its own hash. However, similar configurations will share the same browser hash. It is possible for two browsers to have the exact same hash, even if they are on different systems.
This is part of why a browser hash on its own is not very useful. However, considered in tandem with device hashes, cookie hashes and other parameters, it enables fingerprinting protocols to gauge who a user is and, importantly, how likely they are to pose a risk.
Why Is a Browser Hash Important?
In fraud detection and cybersecurity, a browser hash helps to understand who you are dealing with based on the technology they use. Since a browser hash acts as an ID, we can therefore draw connections and make conclusions, such as:
- Has this browser configuration been seen before?
- Has the same user logged in with different browser setups?
- Could multiple connections come from the same person?
This helps detect connections between users and raises flags when the browser hashes are identical.
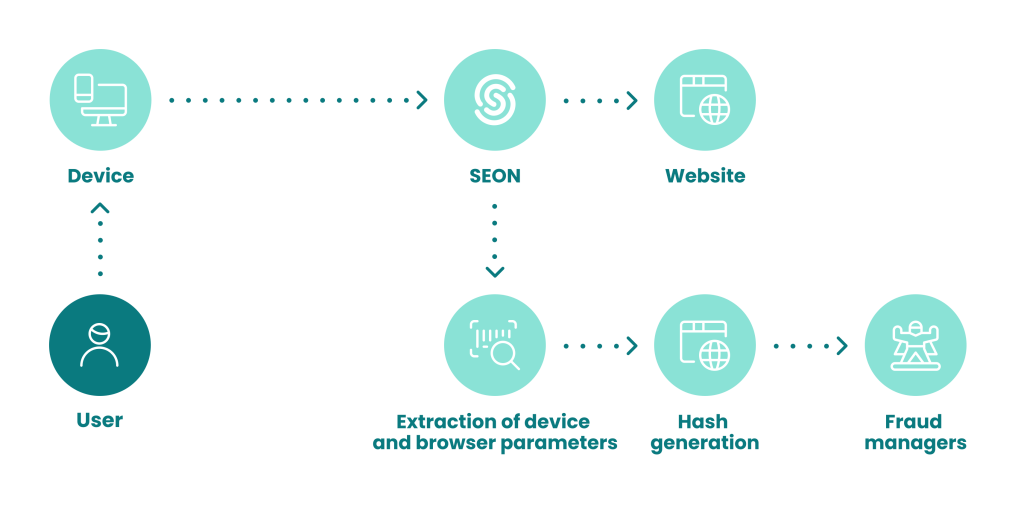
However, it’s worth noting that browser hashes are only part of the whole user profiling. You also need to look at other data points, such as the device, IP address, and personal information to complete the picture.
How to Implement a Browser Hash
A browser hash can be manually or automatically created for purposes of identification.
For example, at SEON, a browser hash is created automatically as part of our device fingerprinting module. This helps log information about the browser, but also the configuration of software and hardware of our fraud detection platform’s users.
By automatically answering some key questions about the user’s browser without any friction, browser hashes help protect organizations from fraud and cybercrime.
Browser spoofing is used by fraudsters to bypass basic security checks and pretend they are someone – or somewhere – they are not. But we know how to catch them.
Learn More Here