What Is Phishing?
Phishing is an attempt to fraudulently obtain sensitive information. Criminals pose as legitimate individuals or organizations to try and obtain personal and other valuable information by email, SMS or other messaging.
Fraudsters who perpetrate phishing attacks have become increasingly sophisticated in their approach. Cisco’s 2021 Cybersecurity Threat Trends Report found that it was responsible for a staggering 90% of data breaches.
Phishing is the costliest type of data breach. IBM’s 2022 research into 550 incidents attached an average cost of $4.9 million to breaches from phishing. In fact, it took an average of 219 days for companies to even identify that phishing had taken place. It then took a further 76 days, on average, to contain a phishing attack. Such figures highlight the scale of the problem that phishing poses, as well as the lengthy disruption that it can cause.
Those who carry out phishing attacks may have a range of goals:
- Some are designed to steal information and/or money.
- Others are carried out to sabotage a company’s systems.
- Many carry out phishing attacks in order to install malware.
- Some seek to lure the target to a website as part of the ruse.
How Does Phishing Work?
Phishing works by tricking a target into thinking they are liaising with a legitimate contact at a company – someone who is authorized to access the information in question. Phishers use social engineering tactics, including guilt-tripping, creating a sense of urgency, etc, to convince their targets. Tools of the trade include fake or hijacked email addresses, phone numbers, logos, and other false business credentials, all helping trick the target into divulging sensitive data or clicking on a link.
While most people think instantly of email when it comes to phishing, attacks can also be carried out using social media, phone calls, voice messages, text messages and more. Phishing scams often put pressure on recipients to take action immediately, by sending a response, clicking a link, or both. Common methods of pushing recipients include stating that there has been a security breach or claiming that an urgent complaint has been received.
The cybercriminal reaches out in the hope that someone will “bite” and engage in conversation with them. When someone does, it allows the criminal to get a foot in the door and take further steps to try to fool the individual into taking additional actions. Those actions are made with the aim to get the victim to reveal information they shouldn’t (such as passwords or account numbers) or download something they shouldn’t.
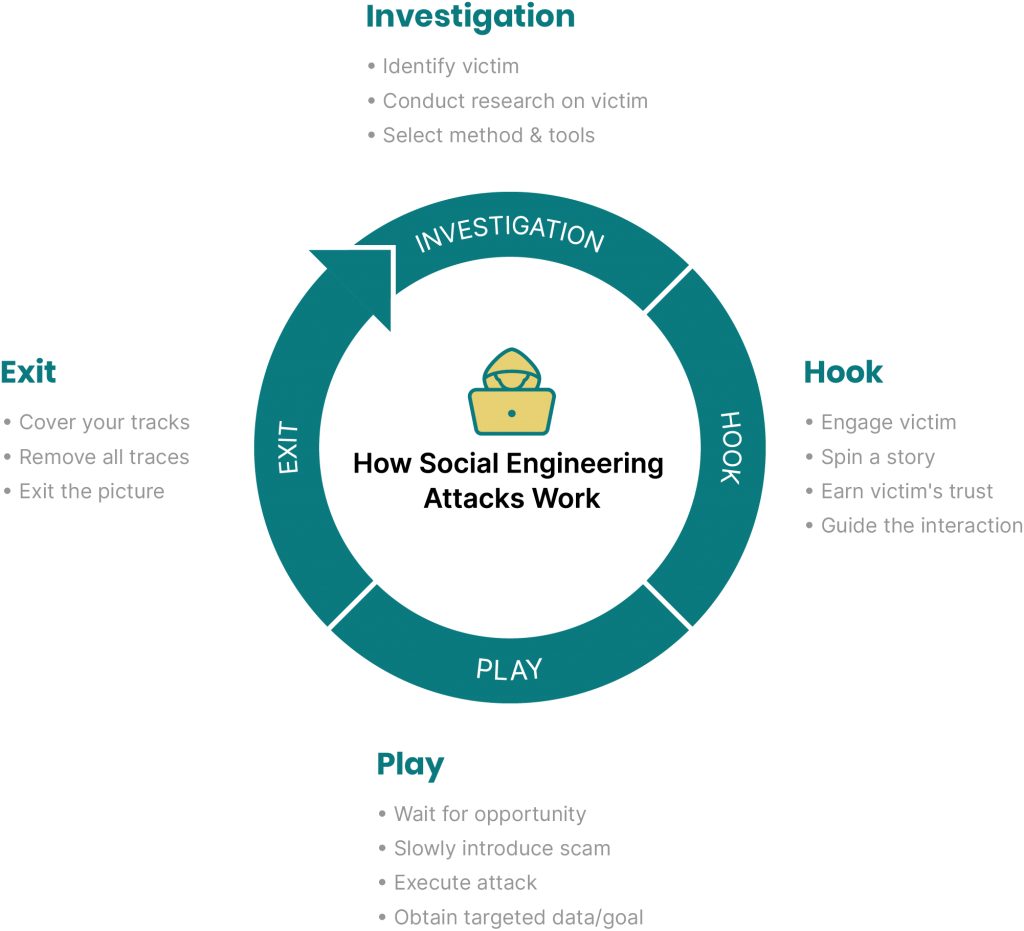
6 Types of Phishing
There are several different types of phishing attacks, from those that target a specific business to mass campaigns.
- Email phishing: Currently the most common type. Fraudsters send out phishing emails to a mass list of email addresses. It is a numbers game, based on the premise that if enough emails go out, someone will bite sooner or later. These generic phishing emails are some of the easiest to spot as they are usually poorly designed, badly worded, and full of spelling and grammatical errors.
- Spear phishing: Spear-phishing is a type of phishing attack that takes aim at a particular target, with the message tailored to that person. It could, for instance, address them by name, or include specific information about them. Often, it is a company administrator or a member of the finance department who is the target.
- Whaling: Named after its high-value targets, whaling is a type of spear phishing that targets CEOs and other C-suite executives. Closely associated with CEO fraud, whaling uses social engineering to try to trick top executives into sharing bank details or other sensitive company information.
- Smishing: Another non-email type of phishing, smishing is a text message-based scam that attempts to trick the recipient into clicking a link or calling a phone number. Texts purporting to be from banks or from delivery companies are two common methods of smishing attack. They seek to trick the user into revealing account details or perhaps to call a number that then costs them money while lining the criminal’s pockets.
- Vishing: Vishing is the voice equivalent of phishing. The caller may, for instance, pretend to be from your bank, a credit card company, a delivery service, and so on. If you’ve ever received a call from someone claiming to be from Microsoft and telling you your computer has a virus, it’s likely you have encountered a vishing attempt first-hand.
- Search engine phishing: The cybercriminal’s goal is to appear at the top of search engine results. If they can achieve this, they can trick searchers into clicking the suspicious link, which will then direct the user to the criminal’s own website. The aim is for the user to enter their log-in details into the spoof site, thus handing them over to the criminal. Businesses looking to avoid their own sites being spoofed as well as having their user details stolen through search engine phishing, should put robust multi-factor or biometric authentication processes in place.
Businesses are increasingly opening themselves up to customers and external users. This increases their risk of phishing. Learn how SEON’s API can help prevent and reduce fraud.
Learn More
Consequences of Phishing
Phishing can have serious consequences for both businesses and individuals, including identity theft, theft of funds and more.
For businesses, phishing can cause significant disruption to operations and potentially huge financial losses. It can also cause reputational damage if a company has to report a data breach caused by its staff being fooled into handing over information – which some legislation, such as the GDPR, mandates.
But it gets worse: It was reported by IBM that in 2022, 60% of company data breaches led to increases in prices being passed on to customers. This means phishing is costing both the business and its customers money.
For individual victims of phishing, such as those tricked into handing over card or bank account details, the consequences of phishing can include financial loss and a huge range of associated problems, such as a trashed credit rating. Stolen personal information (PII) often enables identity theft, among other crimes.
Another common use of phishing details involves account takeover attacks, where a fraudster hijacks a person’s account. This may allow the criminal to gain sensitive information, steal funds, or defraud the account owner’s contacts.
Finally, the phenomenon of phishing can be said to affect consumer trust in online transactions and services, potentially causing some individuals to not trust anyone online, including legitimate businesses, as they choose to err on the side of caution. This stalls the growth of online commerce, especially in certain demographics and locales.
How Can Businesses Prevent Phishing?
Some businesses are more appealing to fraudsters than others when it comes to the target of phishing attacks. Financial service providers such as banks and credit card companies spring to mind.
Thankfully, there are steps that such businesses can take to help protect their customers. Implementing multi-factor authentication, biometric authentication or other types of sophisticated authentication is one such step, as it is harder for criminals to bypass these processes – though not impossible: Deepfake technology is now being used to impersonate people’s voices and videos of them.
It is also important to remember that an organization’s defenses are as strong as its “weakest” employee: A staff member who falls for phishing scams is enough to unwittingly bring down a business, as has happened with frontpage news in recent years, including the DNC email leak and the 2014 Sony Pictures leak.
Here are some more ways to protect your customers from social engineering attacks like phishing:
- Educate both customers and employees about what phishing is and what they should look out for.
- Ensure your customers know which bits of information you will never ask them for.
- Always check email and message sources and IDs, from email headers to URLs.
- Leverage authentication and verification proofing technology.
- Ensure lines of communication are open between different business departments.
- Make phishing prevention part of your risk management strategy.
- Secure your devices and premises against fraud and malware.
How Can Individuals Defend Against Phishing?
As an individual, you can defend against phishing by educating yourself about what it is and how it works. Knowing which warning signs to look out for could make a huge difference.
It’s also important to trust your instincts. If something doesn’t feel right, stop and check. Phishing scams can be very sophisticated but sometimes all it needs to avoid falling victim is for you to step back from the situation and think twice before clicking a link or sharing a piece of information.
Remember: If something is too good to be true, or if an urgent request is unusual in that context, it is probably linked to fraud. If unsure, contact the purported sender yourself using a number or email address from their official website, which you ought to get to from a search engine, not an email link.